Disruptive technologies have a learning curve in the pace of adoption and implementation. Training and education tend to follow a slower schedule and can have a hard time keeping up with discoveries happening on the bleeding edge. This is part of what led to the current cloud security skill gap.
The cloud transformed software development, accelerating innovation and the pace of human creativity. But, we now know that it also formed new security challenges. The cloud is complex and provides malicious actors with many opportunities. However, one out of every four IT and security specialists struggle to get the training necessary to defend properly.
Security professionals need to move fast to stay on top of evolving threats. With cloud adoption still ongoing, smaller teams can struggle to keep track of what’s happening in their environments. Not everyone has a fully stocked SOC in house!
This is why Sysdig Sage™, our AI-driven cloud security analyst, was built to help security professionals of all levels accelerate analysis and investigation, allowing them to prioritize what matters. But, is it truly beginner-friendly?
In this article, we explore Sysdig Sage from a non-technical perspective. Most cybersecurity professionals will have better training than two marketers on a product walkthrough, but can it help two relative newbies navigate a complex cloud security environment?
250 events in a single instance – the first thing one notices when looking at a security events log is the sheer amount of data. We hear a lot about alert fatigue working in the cloud security industry, but nothing can prepare you for that long doom scroll. Everything on the screen documents things happening in your environment, which is incredibly helpful, but not knowing what’s innocuous and what’s a threat – and how much of a threat – makes a big difference.
— KZ
The thought that immediately comes to mind is “Where do I even start”?
What is Sysdig Sage?
Sysdig Sage uses an autonomous agents approach, leveraging multiple specialized AI agents that work collaboratively with a common goal: to simplify and accelerate security and enable a faster, better-informed human response.
With the help of multi-step reasoning and contextual awareness, Sysdig Sage understands exactly where the user is in the UI and provides direct, easy-to-understand explanations of all runtime events. It also suggests remediation strategies and prevention best practices and improvements.
This makes it ideal for security teams with diverse skill levels – everyone on the team can get the help they need to manage more and escalate less.
Dive deeper into Sysdig Sage here.
As soon as I jump into a security platform, it’s information overload. There’s clearly tons of valuable data here, all telling a story about what’s happening in my environment, but not in any language I speak. Which information actually matters? Which events represent real threats I need to focus on? Even when I bring up a specific event, it’s not clear what I should actually be doing. If I’m going to make any sense of all the rich information at my fingertips, I’m definitely going to need some help.
— MR
A beginner’s guide to Sysdig Sage
Where do I start – prioritization and strategy
At a glance, it becomes clear that Sysdig Sage is instrumental for anyone looking to gain a more in-depth understanding of the terms and concepts of cloud security. This is one of the benefits of multi-step reasoning. Sysdig Sage understands the question, provides simple answers, and – like any good conversationalist – remembers what we talked about earlier and lets it inform future queries.
As a complete beginner, I might need some truly foundational elements explained. Being new to runtime security, my understanding of what exactly constitutes a runtime event might be a little hazy.
So, I asked Sysdig Sage to explain.
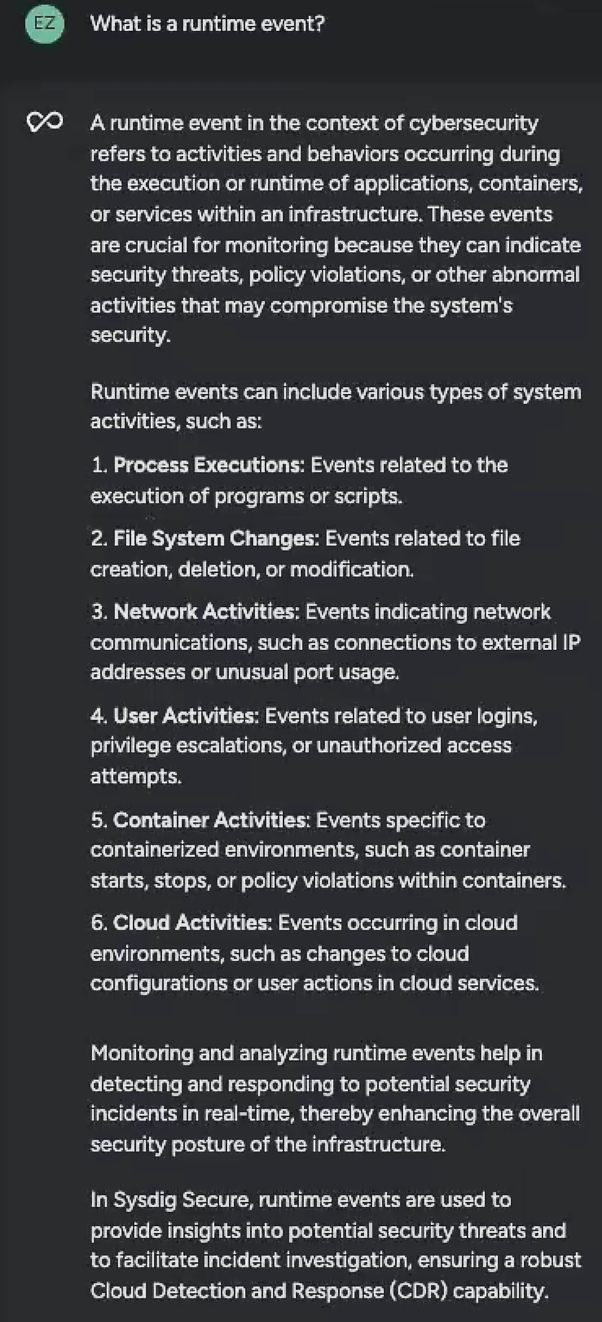
What is great about the response is that it does what it’s supposed to: define the term I asked about as well as craftily suggest tips on the areas I need to pay regular attention to. It’s already helping me prioritize, even at this early stage.
Because it is context-aware, Sysdig Sage knows where I am within the UI and works as my partner as I try to understand the runtime events in front of me. Clicking into any event shows the Sysdig Secure detailed overview:
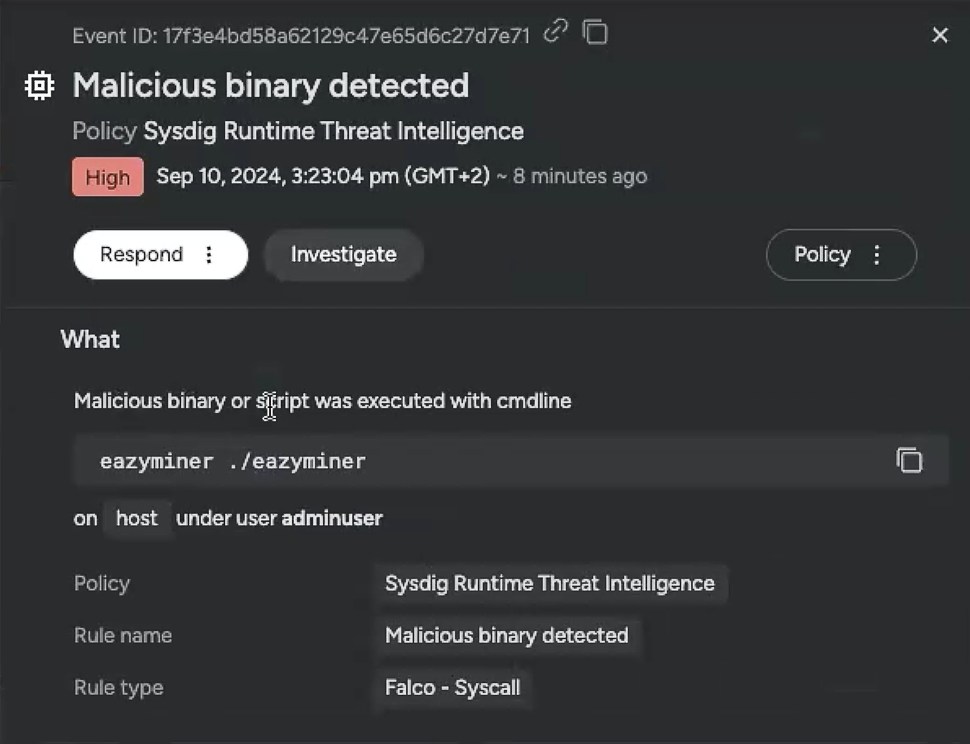
This overview is useful for quick response – right away, I can see the event was high-severity and it happened recently, which means I should prioritize it. I also had the Respond and Investigate toggles ready to use. But, as a less experienced user, I immediately had many questions:
- How big of a threat is this?
- That eazyminer line does not inspire confidence. How can I understand it better?
- Should I suspend the identity access that adminuser user is clearly exploiting?
- Is this all a part of a broader security incident?
Before I could panic further, I asked Sysdig Sage for details:
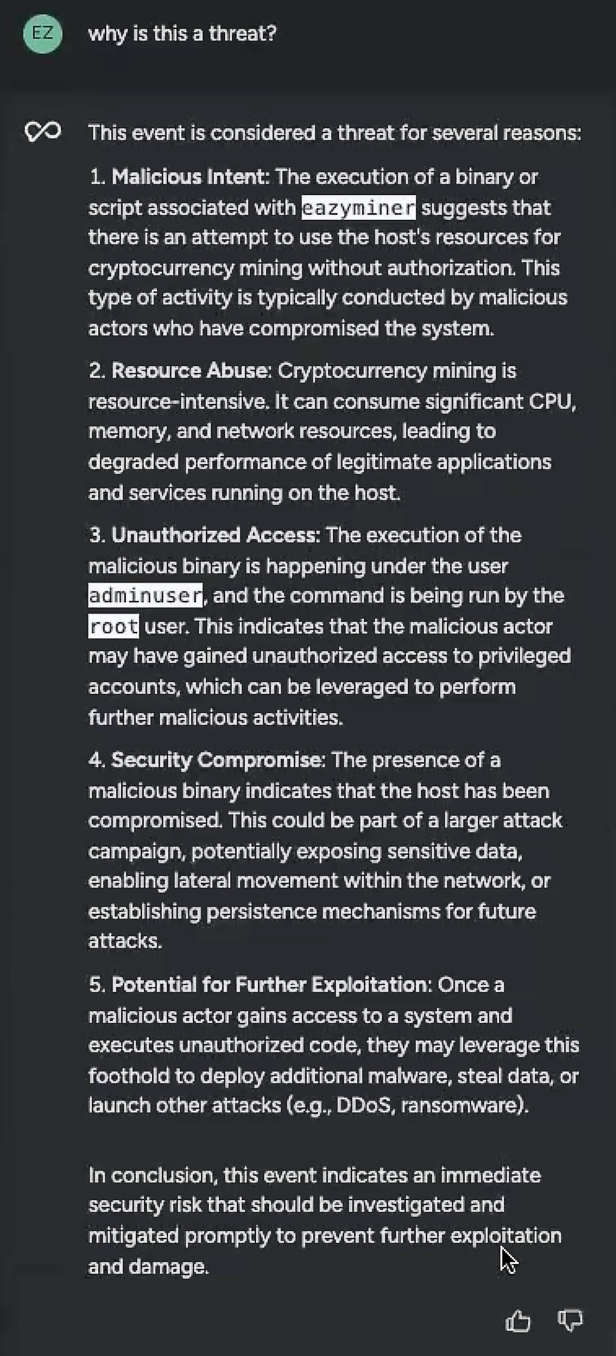
According to Sysdig Sage, this was definitely a cryptoming event. My environment’s resources were being abused, and whoever it was had admin access and was running the command as root user. It was also likely to be a part of a much broader security event. I knew right away I needed to act. Using Sysdig Sage’s remediation options, I proceeded with next steps.
After playing around with the tool for a few minutes, it was clear that Sysdig Sage could help me understand runtime events. But, that was only one event.
My Events log showed I had a lot of events.
Many of them recent, many of them high severity.
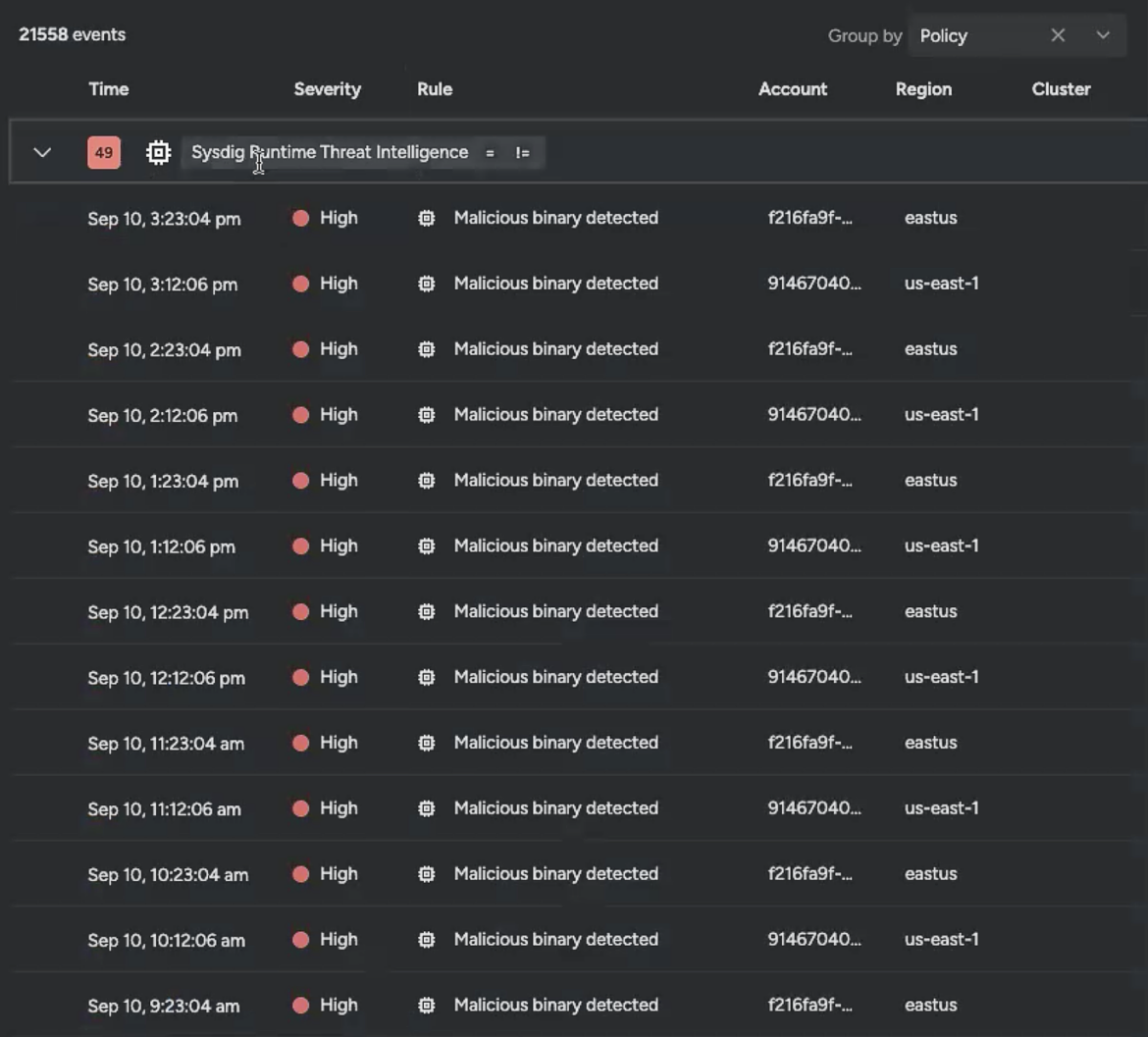
Attempting to address all of them would be impossible. I might miss something important if I tried going through all of them at once.A more experienced security professional might have been able to tell what matters at a glance and plan her day accordingly, but that wasn’t me. I knew I needed help.
So, I asked Sysdig Sage about the events I needed to address first.

Sysdig Sage displayed an itemized list of the highest severity events. I could have gotten this list in other ways – Sysdig offers robust risk prioritization – but here I had them all in one place, broken down by priority, number of individual events, and direct links to more details.
However, looking after further inspecting the list, I noticed that the first instance still had 263 events. It was much better than 21558, but it was still a large number. If I only had eight hours in a day, I needed to understand how to get everything done in the time I had.
I asked Sysdig Sage to help organize my calendar.
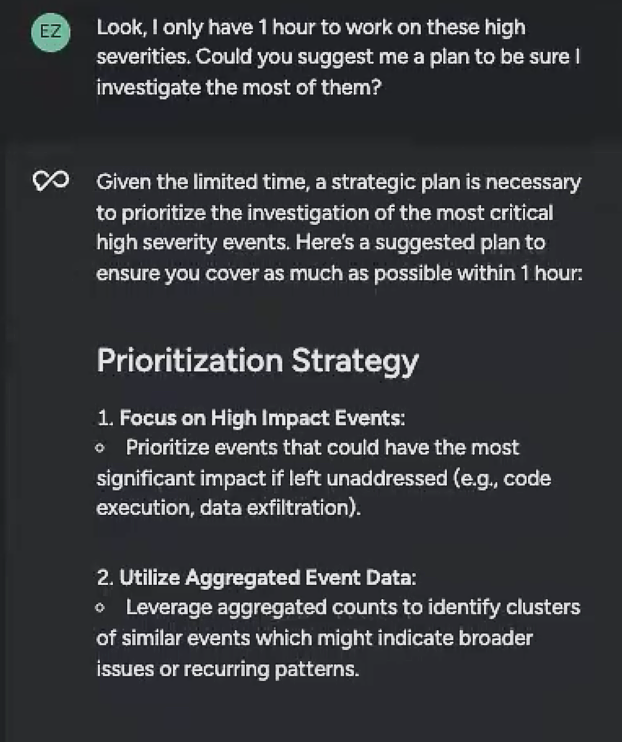
In the output, I got a prioritization strategy that outlined my tasks broken down by time estimates. Looking at the time estimates, I might need to narrow down my focus, but having a plan in place makes me feel more confident as I start my investigation.
Alert fatigue is one of the most challenging aspects of a security professional’s day-to-day life. For smaller organizations with fewer resources, this can easily go from challenging to grueling. Having a tool that helps the human defenders prioritize and accelerate investigation and response is a groundbreaking next step closing the cloud security knowledge gap.
Guided Remediation
Jumping into Sysdig Secure, my goals were to find a potential threat, and learn how to remediate it. But I wasn’t sure if I could achieve them, given my lack of hands-on experience and limited knowledge.
I decided to start with the same event we discussed above:

This was clearly a high-severity event, and with the help of Sysdig Sage, I was able to better understand why. But that knowledge alone wasn’t going to make my environment any safer. What I really needed to know was what to do about this threat. So I turned to Sysdig Sage:
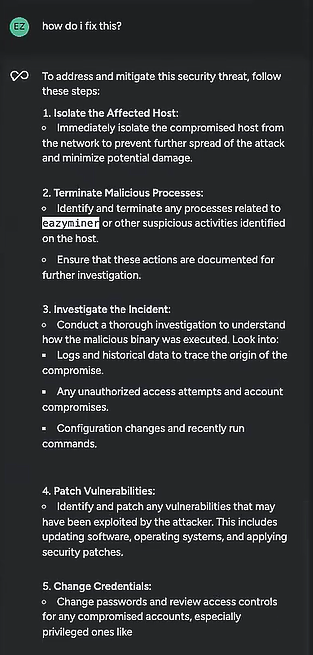
Even when I didn’t have the words to describe what I was looking at, Sysdig Sage knew exactly where in the UI I was and what I wanted to fix.
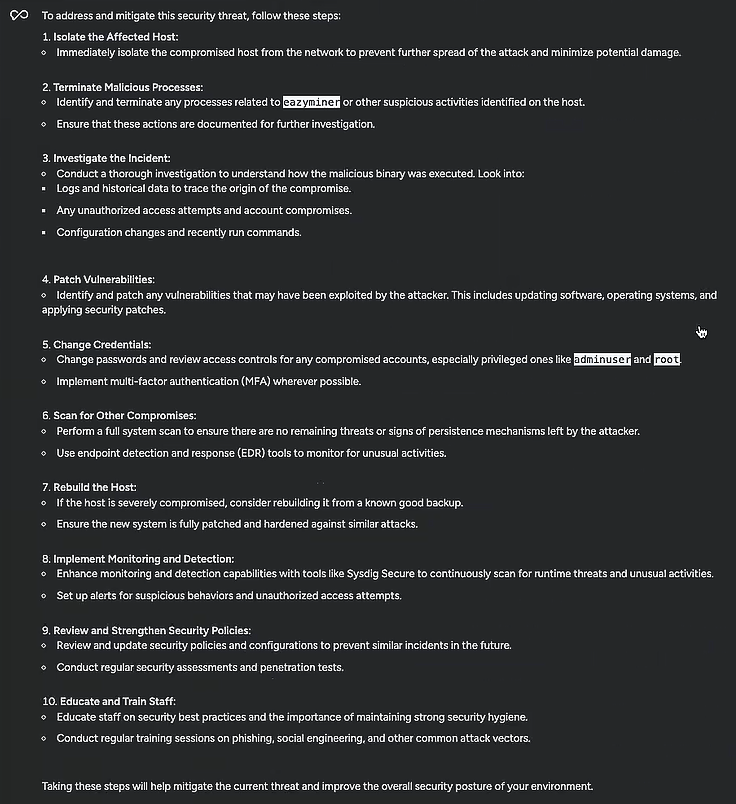
Sysdig Sage had a whole list of recommended remediation strategies to try, including isolating the host in question, terminating any processes or activities related to the suspicious eazyminer, changing passwords, and performing a full scan for other signs of compromise. Sysdig Sage even had some long-term suggestions to prevent similar threats from popping up in the future, like conducting regular security training with staff. For each of these suggestions, it broke things down further into clear steps I could take.
I wanted to see if Sysdig Sage could give me more guidance on how to isolate a host.
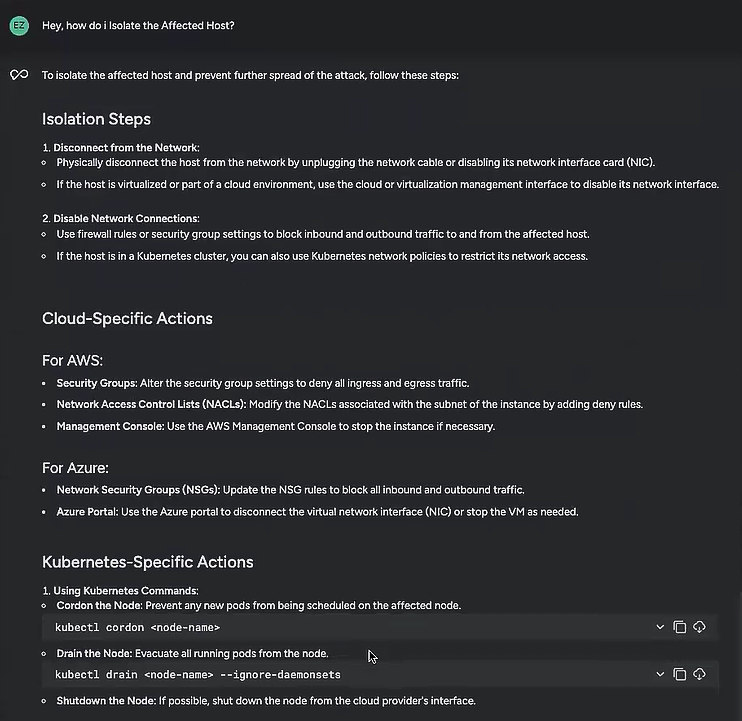
With its multi-step reasoning capabilities, Sysdig Sage remembered what we’d been talking about and simply continued the conversation, as naturally as a human guide would.
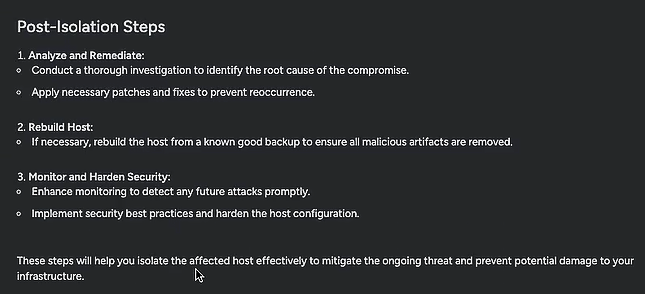
Just like that, I had a more detailed breakdown, with clear directions to follow. Sysdig Sage started with broad directions, like disconnecting from the network and disabling network connections, plus more specific steps depending on the specific environment. It also told me what do to next after isolating the host:
But what if it wasn’t that simple? What if this wasn’t just an isolated incident of, say, someone setting their password as 12345, but a sign of a bigger threat to my environment? How would I even know?
I took my worries to Sysdig Sage:
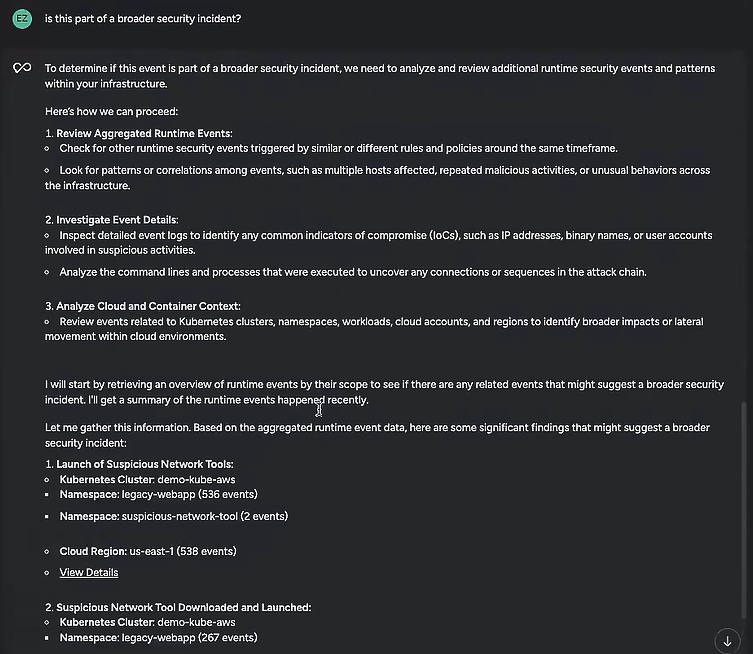
Sysdig Sage suggested reviewing other events occurring around the same time frame and trying to find patterns or similarities. It also recommended looking at events happening in other parts of my infrastructure to check for lateral movement.
Now, I knew the steps I could take to see if a broader security incident was happening. Combing through all the other recent events and trying to figure out what might constitute a pattern would still have been a daunting prospect, but Sysdig Sage immediately started looking into that data for me.
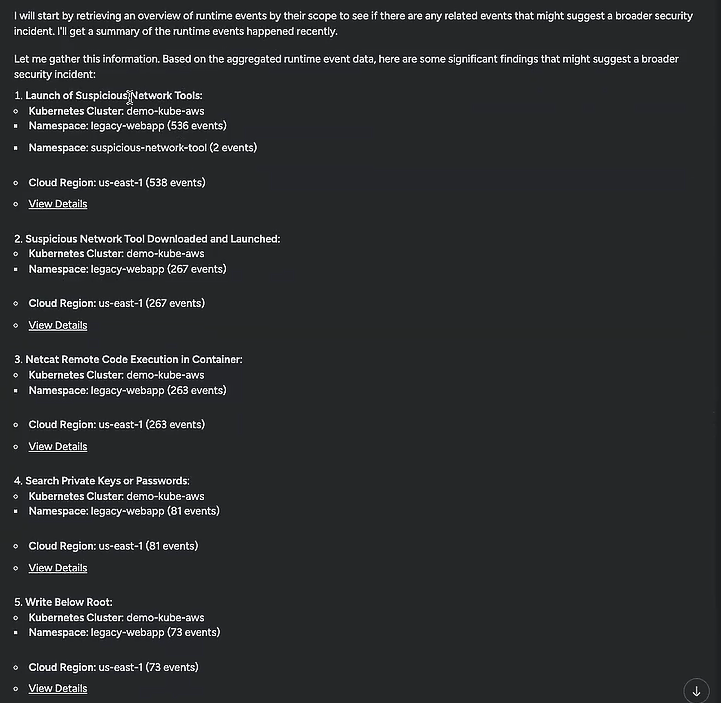
Sysdig Sage found several groups of events that looked similar to the malicious binary one, cataloged their basic details for me, and included links to review the full lists of events. After the last group of events, it came to a conclusion:
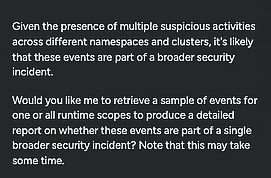
I started this exercise staring at a critical runtime event, with no idea how to proceed. But within minutes, I had been able to learn exactly what I needed to do to address the individual threat in terms I understood or I could ask more questions if I needed more information. I’d confirmed the likelihood of a broader incident and was now ready to kickstart a full investigation.
Sysdig Sage is for everyone
The cloud moves fast. Experienced security professionals as well as beginners need to keep up. Sysdig Sage bridges the cloud security skill gap, so that teams of all skill levels can quickly understand what’s happening in their environment and respond to threats. It serves as the ideal cloud security analyst – allowing them to move faster and focus on what truly matters.
Sysdig Sage provides context, helps to prioritize events, and recommends actionable steps. By guiding users through complex investigations and providing real-time remediation suggestions, Sysdig Sage vastly improves decision-making and empowers everyone to take control of their environment, regardless of their expertise.
To learn more about how Sysdig Sage can enhance your security operations, check out this blog post. See it in action and experience the power of AI-driven investigation firsthand here.