
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Over the past 12 months, the cloud-native application protection platform (CNAPP) market has seen an enormous amount of change with no signs of slowing down — and customers are taking notice.
We believe the latest Gartner Market Guide for Cloud-Native Application Protection Platforms is an incredibly helpful resource in understanding the value CNAPP solutions provide, their key capabilities, and future planning assumptions. Read on to find out what our most important takeaways are from this year’s report.
Read the 2025 Gartner Market Guide for Cloud-Native Application Protection Platforms now.
Benefits of a CNAPP platform
Gartner’s definition of CNAPP has remained largely unchanged:
“Cloud-native application protection platforms (CNAPPs) are a unified and tightly integrated set of security and compliance capabilities, designed to protect cloud-native infrastructure and applications. CNAPPs incorporate an integrated set of proactive and reactive security capabilities, including artifact scanning, security guardrails, configuration and compliance management, risk detection and prioritization, and behavioral analytics, providing visibility, governance and control from code creation to production runtime.”
We believe CNAPP platforms help teams by providing:
- Increased efficiency
CNAPPs simplify security operations by replacing multiple point products and providing a unified view of risk. This streamlines processes, freeing teams from the burden of mastering various tools and managing alerts from different sources. - Comprehensive visibility
CNAPPs provide a unified view for teams to swiftly pinpoint issues, events, and potential attack paths. Through user-friendly visual layouts, alerts, suggestions, and guidance for remedial actions, you can make informed decisions and proactively safeguard against threats. - Enhanced detection of cloud threats
CNAPPs offer an end-to-end solution, ensuring consistent threat detection and visibility across any workload, cloud, or service. By leveraging techniques such as machine learning and threat feeds, CNAPPs enable organizations to effectively identify and respond to threats, reducing the attack surface in cloud-native environments.
As the category continues to expand rapidly, the sheer number of capabilities that can be considered under the CNAPP umbrella has made it difficult for customers to understand what they need to have versus what is nice to have. Gartner has brought some clarity to this question:
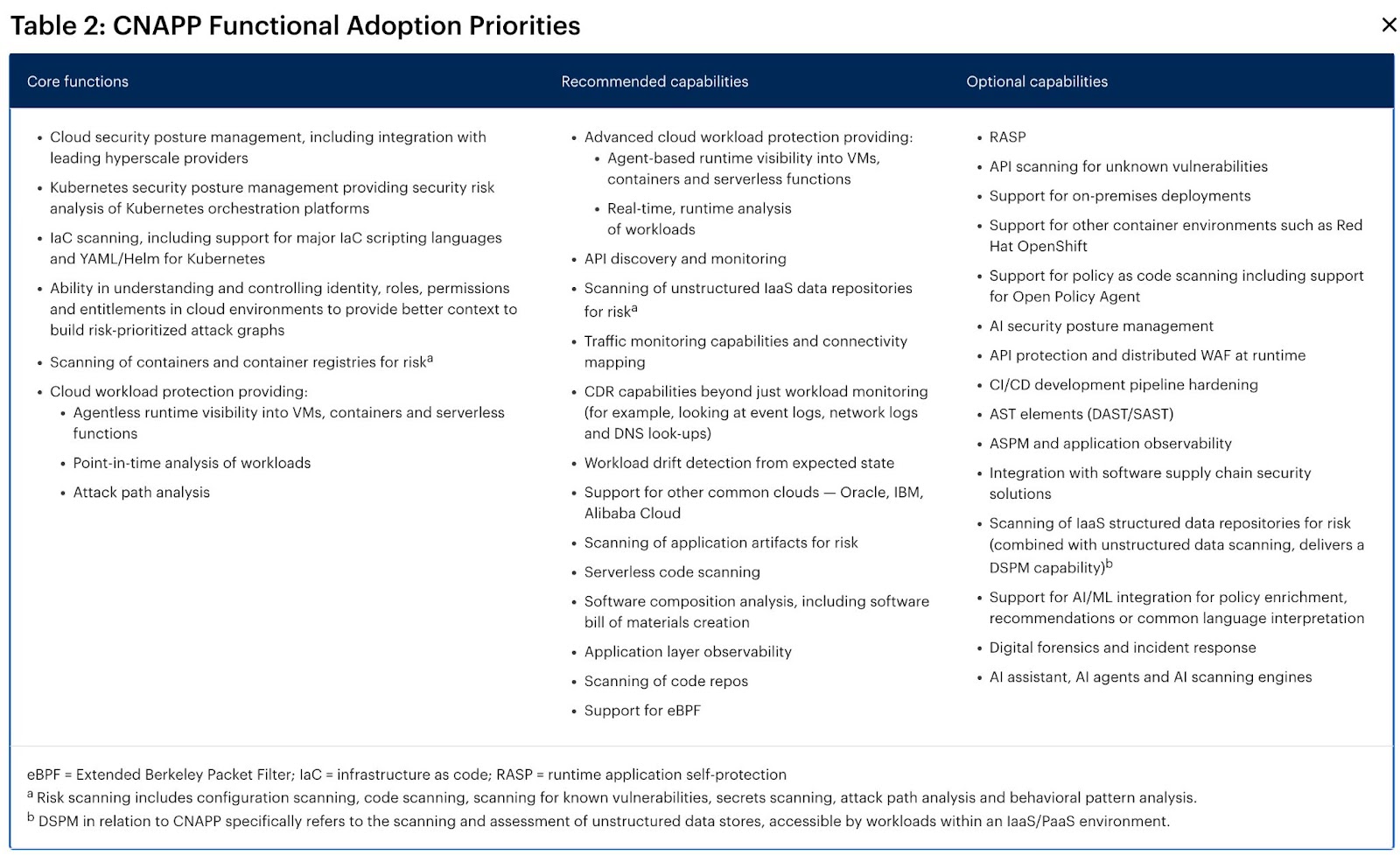
Notable additions to Optional Capabilities include “AI assistant, AI agents, and AI scanning engines.” As Gartner notes, “CNAPP solutions are increasingly incorporating generative AI (GenAI), common language interpreters, machine learning (ML) and large language models (LLMs) to reduce management overhead, offer policy recommendations, and enhance pattern analysis for threat detection and response.” In our view, it’s clear that Gartner recognizes the key role AI will play in moving the CNAPP market forward.
Sysdig announced our own AI cloud security analyst, Sysdig Sage, in 2023, and recently completed the full integration into Sysdig Secure. Sysdig Sage uses multi-step reasoning to analyze complex attack patterns and understand how seemingly unrelated events are connected. It correlates signals across multiple domains to identify hidden or emerging threats that traditional tools may miss.
Runtime visibility lets you fix what matters faster
At Sysdig, we believe true cloud security starts at runtime. Runtime is the highest fidelity signal in cloud security. Most tools miss what’s running right now, creating blind spots during both prevention and response. By rooting all decisions in what’s actually in use at runtime — along with real context — security teams can make better risk decisions and prioritize their day. This extends to security operations teams, who use runtime context as a key input in identifying and prioritizing threats:
“They need the capabilities to pull contextual runtime data on behavior and threats while feeding this context into SIEM and SOC services for event correlation. Without this context, security operations (SecOps) finds it challenging to manage runtime vulnerabilities discovered within published workloads and identify abnormal workload co-pilots resulting from exploiting vulnerabilities or excessive privileges.”
With help from runtime insights, SecOps teams are able to stop drawing in false positives and enable faster, more accurate responses to cloud threats.
Enhanced prioritization helps connect dev and security
Prioritizing risk is one of the key use cases for a CNAPP. This is especially important during development to ensure that risks are not introduced into production. Assigning ownership, notifying the right teams, and tracking remediation progress can be surprisingly difficult, especially when there’s a disconnect between security and development teams. Security teams might flag a critical vulnerability, but that doesn’t mean it will get addressed anytime soon. Developers are under pressure to deliver features fast, and security tasks often land as unexpected, low-context interruptions. Without a shared view of risk and clear accountability, even critical vulnerabilities can linger unresolved for weeks or months.
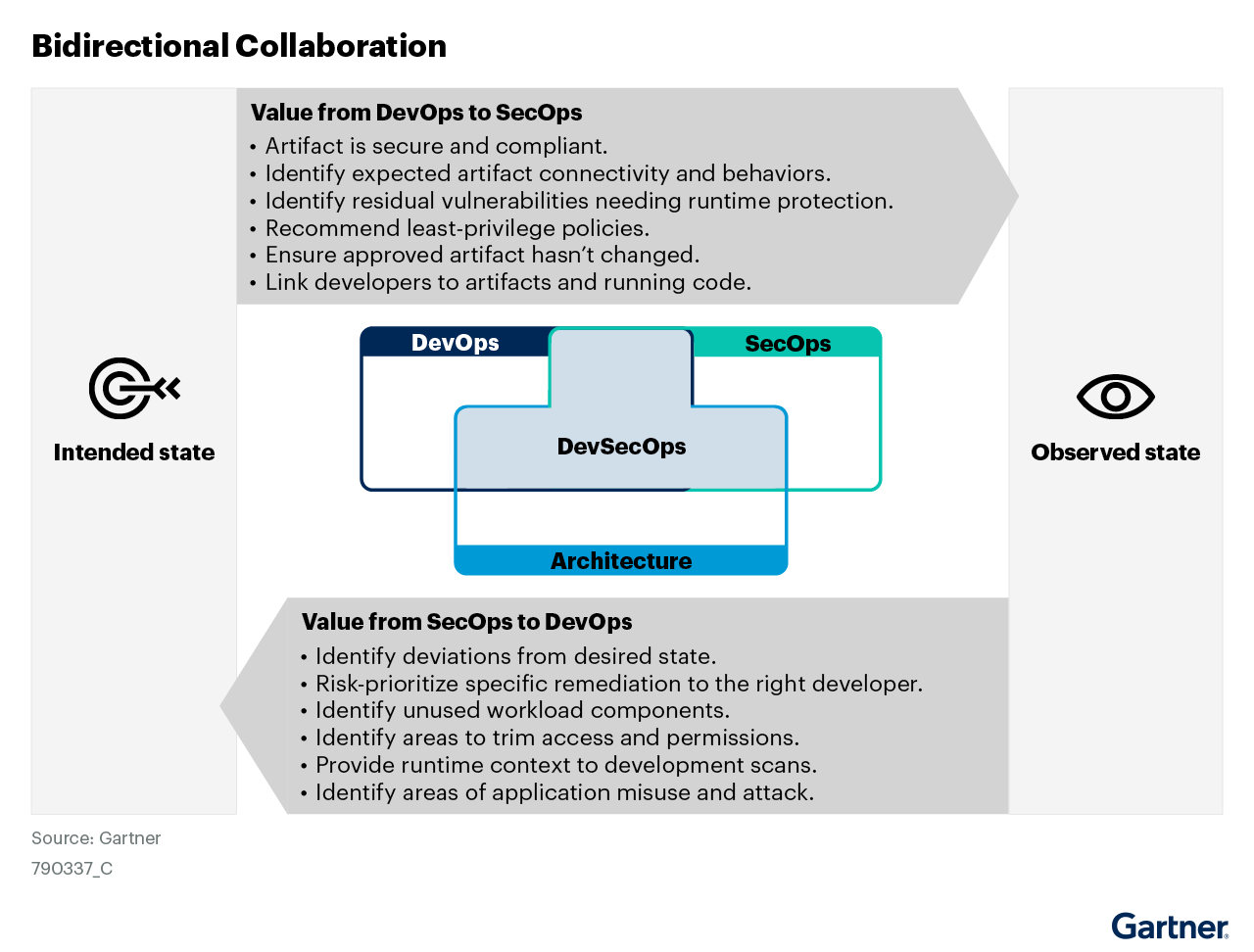
According to Gartner, one of the characteristics a single vendor CNAPP needs to have is:
“An understanding of the relationship between development artifacts (custom code, libraries, container images, VMs and IaC scripts), who created them and when they were created, who deployed them and when they were deployed, and who changed them and when they were changed. Mapping of accountability and responsibility to code and artifacts is critical.”
To address this, we’ve recently announced our partnership with Semgrep, which helps enterprises reduce risk surface area through improved prioritization and streamlined find/fix cycles. One of the benefits of this partnership is improved identification of ownership - customers are able to map vulnerabilities discovered at runtime back to the originating application teams or service owners (derived from source control/SCA data), which enables clearer, more direct ticket assignment and accountability.
The role of AI within CNAPP
One of the biggest issues for cloud security and developer teams is that they spend thousands of hours each year triaging alerts, often taking more time deciding what to fix than actually addressing and resolving their issues. Risk prioritization in current tools often falls short due to a lack of business context. This causes delays in response, which prolong exposure to business-critical threats that could disrupt key functions and compromise sensitive data.
We believe AI can help by redefining risk prioritization and remediation strategies, allowing teams to enhance productivity, shorten time to resolution, and significantly reduce business risk. According to Gartner:
“The expectation is that these new AI capabilities will significantly improve risk management and reduce mean time to resolution (MTTR), resulting in quicker detection and response to cloud infrastructure and application risks both proactively and reactively.”
Summary
It’s clear that the need for CNAPP solutions is only increasing. In fact, Gartner believes that “By 2029, 50% of all enterprise applications are expected to operate in containers, necessitating enhanced and unified security controls for cloud and applications.”
Security strategies that rely on disconnected point solutions — even if those solutions are considered “best of breed” — will increasingly struggle to meet the demands of the current threat landscape.
The time has come for a unified approach. And for truly comprehensive, end-to-end security, organizations should look for a CNAPP that:
- Prioritizes active risk through the use of runtime insights to help zero in on the most urgent security issues.
- Provides real-time detection so teams can investigate and respond to threats within minutes.
- Enables a unified view of all cloud risks and threats, no matter what kind of environment you have.
Ready to start consolidating your cloud security? Check out Sysdig’s runtime-powered CNAPP solution, or read the full report from Gartner today!
Gartner® Market Guide for Cloud-Native Application Protection Platforms
Gartner, Market Guide for Cloud-Native Application Protection Platforms, Dale Koeppen, Esraa ElTahawy, Neil MacDonald, 6 August 2025.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.


