Today, we are excited to announce the launch of Sysdig Secure 3.0! Sysdig Secure is the industry’s first security tool to bring both prevention and incident response to Kubernetes.
This release has three main features:
- Kubernetes Policy Advisor prevents threats at runtime using Kubernetes Pod Security Policies.
- Falco Tuning optimizes Falco rules to reduce false positives and alert fatigue.
- Activity Audit speeds incident response and enables audit by correlating container and Kubernetes activity.
As DevOps teams ramp Kubernetes in production, their responsibilities expand beyond monitoring, capacity management and troubleshooting to include security and compliance. Teams are looking to merge these two functions into a single secure DevOps workflow. So let’s dive deeper into how the new features of Secure 3.0 streamline security responsibilities for DevOps teams, so they can focus on maximizing availability of their Kubernetes platform.
Kubernetes Policy Advisor provides native threat prevention
Pod Security Policies (PSPs) are a powerful security control
Kubernetes Pod Security Policies provide a framework to ensure that Pods run with appropriate privileges and can only access the required resources.
Pod Security Policy can limit Pod behavior to improve security. For example:
- Prevent privileged pods from starting and control privilege escalation
- Restrict Pod’s access to specific filesystems, host and network namespaces
- Restrict the users/groups a Pod can run as
- Limiting the volumes a pod can access
- Restrict other parameters like runtime profiles (AppArmor, SELinux, etc) or read-only root filesystems
Pod Security Policies are actually a threat prevention mechanism. The security constraints allow you to enforce a least privilege model that prevent attacks from spreading across the cluster and block the typical container breakout approaches.
Pod Security Policies are part of the Kubernetes platform, so when they validate Pod configuration and enforce runtime permissions, they don’t impact performance of the application workload. Other tools that tamper with the container infrastructure, or modify the host binaries and container images, can introduce security risks and potentially impact performance.
Challenges of implementing PSPs
Although PSPs are a powerful tool, there are some barriers to implementing them broadly:
- PSPs are easy to misconfigure: DevOps teams spend a lot of time manually configuring PSPs. It is challenging to find the right balance, so you don’t have a policy that is too restrictive and breaks the application or a policy that is too permissive and leaves pods exposed. Creating appropriate policies is often complicated and time consuming.
- Validating PSPs pre-production is hard: Since PSP configuration is complex, there is a risk of making mistakes. There is also no standard way to test PSPs prior to enforcement, which makes it hard to confidently adopt PSP’s at scale.
Kubernetes Policy Advisor allows you to deploy PSP’s confidently in production
Sysdig’s Kubernetes Policy Advisor provides a simple and scalable mechanism to safely implement Kubernetes Pod Security Policies (PSP) in production.
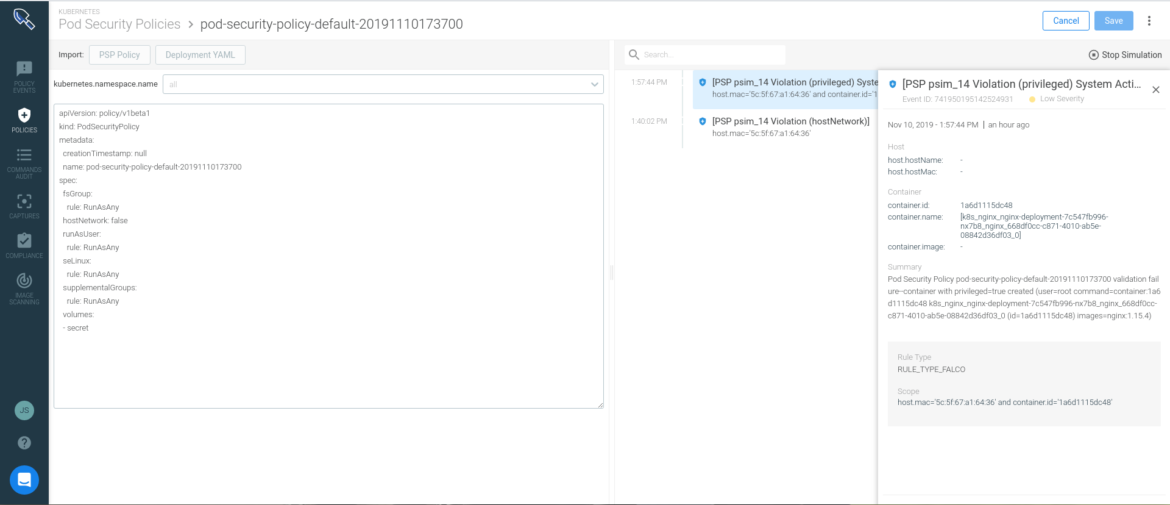
Kubernetes Policy Advisor creates a three step workflow to easily implement PSPs:
- Generate: Sysdig Secure auto-generates a restrictive PSP from the pod specs inthe deployment definition of a yaml file. This process allows you to significantly decrease the time spent configuring security policies.
- Validate: Policy Advisor validates the policies prior to enforcement to ensure they do not break application functionality. Comparing the PSP against the application runtime behavior, teams can tweak the policy to be more or less permissive. This iterative process gives confidence in the expected pod behavior in production.
- Prevent: Sysdig leverages Kubernetes-native controls to handle enforcement. This streamlined approach doesn’t tamper with the container infrastructure and has no performance impact.
For a deep dive into how Sysdig Secure prevents threats using native Kubernetes controls read: Pod Security Policies in production with Sysdig’s Kubernetes Policy Advisor.
Falco Tuning generates fewer false positives by tuning runtime policies
Falco is the open source Kubernetes runtime security project originally started by Sysdig. Since October 2018 it has been a CNCF® Sandbox Project.
Using Falco, DevOps teams can create custom runtime rules based on container behavior or Kubernetes audit-based events. Managing security policies at scale, across clusters and clouds, can be challenging. Sysdig Secure extends Falco by easing the burden of creating and updating runtime Falco policies with centralized management, a flexible policy editor and automated profiling.
DevOps teams can reduce false positives generated by security policies when they leverage Sysdig Secure’s Falco Tuning capabilities. Falco Tuning analyzes recurring events and suggests changes to policies that minimize redundant alerts.
For example, a web service in Kubernetes write logs to a specific path. If the application is upgraded, and in the new version logs are written to a different path, the policy could generate a high volume of false alerts. Falco Tuning observes the runtime events and automatically suggests that a new path is included as a condition filter in the rule. This helps reduce false positives and noisy alerts.
Activity Audit is the first Kubernetes-native tool for incident response
Security teams don’t have an audit trail for Kubernetes
Understanding all the changes in your cluster generated by a Kubernetes user or service is nearly impossible. Without the ability to map system activity to users or services, security teams have no way to uncover malicious behavior and misconfigurations within Kubernetes.
Existing tools provide this information as disparate data points that are not correlated. SOC teams need to be able to analyze an endless list of different scenarios:
- Show all outbound connections from my billing namespace to an unknown IP address
- Trace a
kubectl execuser interaction and list all the command and network activity that happened inside the pod - Show every tcpdump command execution that has happened in a host or Kubernetes deployment
Activity Audit speeds incident response and enables audit in Kubernetes
Sysdig’s Activity Audit speeds incident response and enables audit for Kubernetes. Sysdig captures relevant information like:
- executed commands inside the container
- network connections
- Kubernetes API events like users executing
kubectl exec
By correlating this information with Kubernetes application context, the SOC team can spot abnormal activity. For example, they can review a kubectl exec into a pod in Kubernetes andtrace the chain of activity.
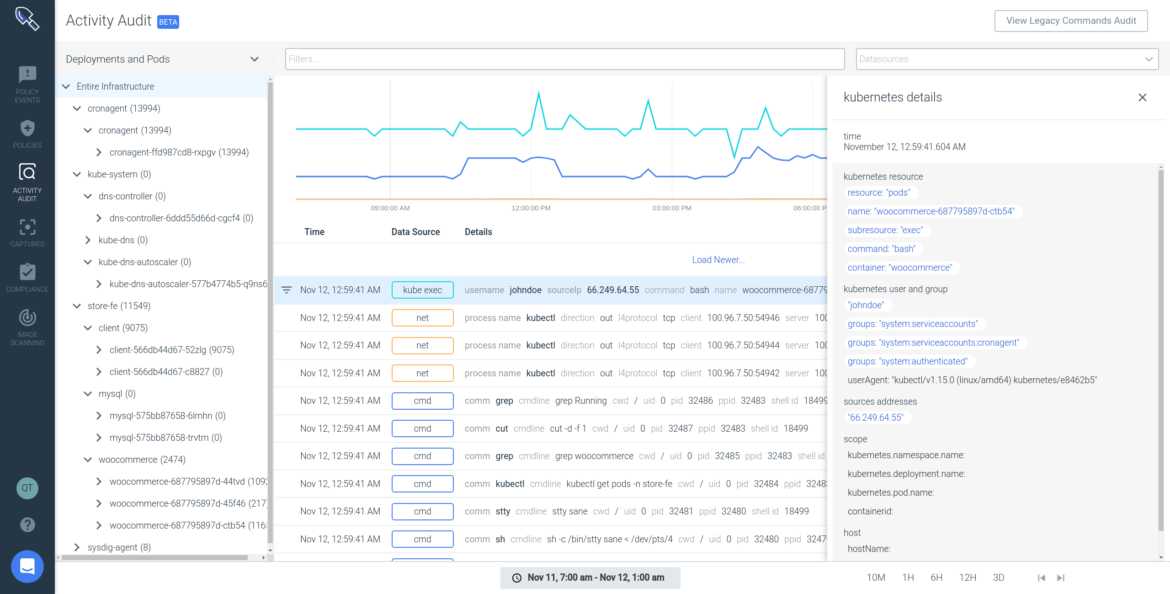
Activity Audit provides teams with an audit trail, a common requirement for compliance standards like SOC 2, PCI, ISO, HIPAA and allows them to investigate Kubernetes user activity even if the container no longer exists.
Activity Audit complements the existing Sysdig Secure forensics capabilities (Captures), by recording all the pre and post attack container activity. This allows teams to analyze everything that happened – not only after an incident, but also before, so you can understand the full sequence of activity. Sysdig Secure is the only Kubernetes audit and incident response solution available today.
For a deep dive into incident response and audit for Kubernetes read: Incident response in Kubernetes with Sysdig Activity Audit.
Conclusion
Sysdig Secure 3.0 is the industry’s first tool to provide enterprises with threat prevention at runtime using Kubernetes-native Pod Security Policies (PSP). This launch also includes the first incident response and audit tool specific to Kubernetes environments.
Sysdig Secure embeds security and compliance into the build, run and respond stages of the Kubernetes lifecycle. With Sysdig, enterprises can embed security, maximize availability, and validate compliance. Sysdig Secure integrates into your secure DevOps workflow, giving you the confidence to run Kubernetes in production.

