Cloud Security Posture vs Kubernetes Security Posture
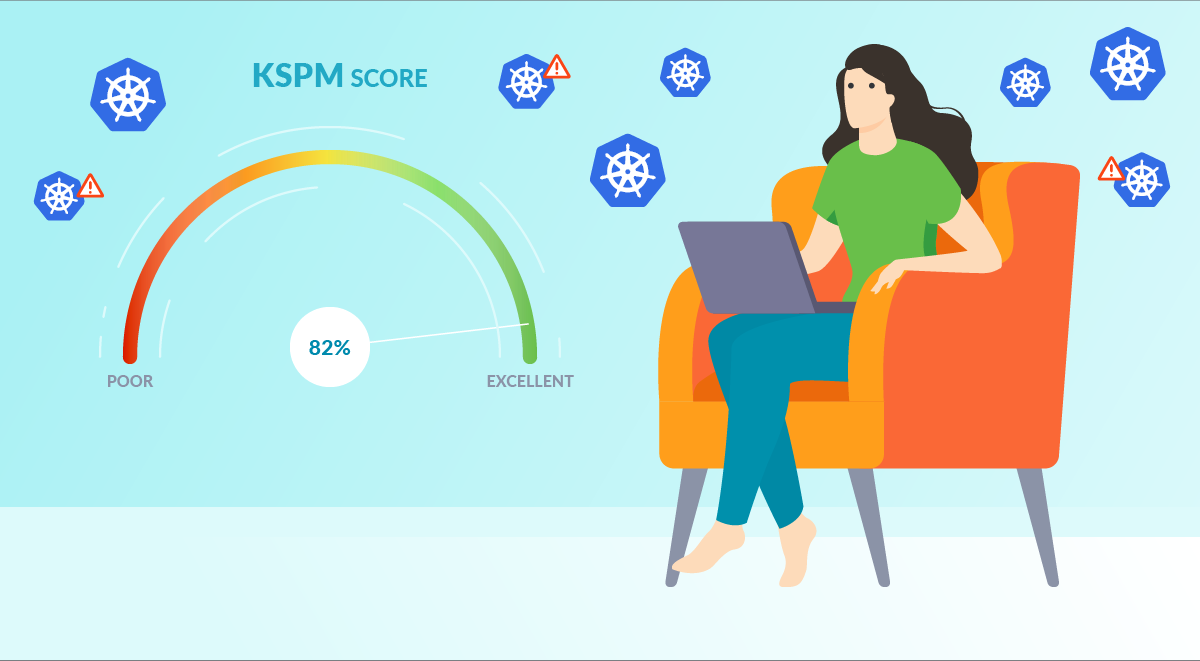
Cloud Security Posture Management or CSPM refers to the security tools designed to evaluate and prioritize policy violations for cloud resources (such identify misconfiguration issues and compliance breaches). CSPM help organizations to be as secure as possible against the various threats that could impact cloud environments. So we can see KSPM like one of the sub-cases under CSPM.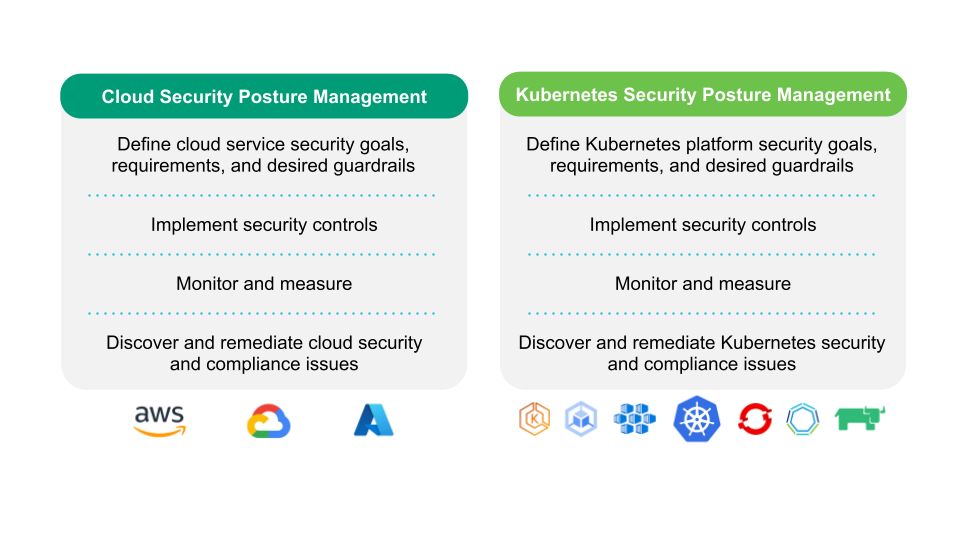 For a cloud security engineer, the Kubernetes Security Posture can just be a percentage number or score. The higher the score, the better Infra/Ops teams are doing following security best practices. The lower the KSPM score…means the fateful number is going to chase you until you fix all those configuration issues that do not meet the security guidelines.
When a compliance audit approaches, security teams and auditors will need all the relevant documentation on the company’s current security posture, KSPM score included.
For a cloud security engineer, the Kubernetes Security Posture can just be a percentage number or score. The higher the score, the better Infra/Ops teams are doing following security best practices. The lower the KSPM score…means the fateful number is going to chase you until you fix all those configuration issues that do not meet the security guidelines.
When a compliance audit approaches, security teams and auditors will need all the relevant documentation on the company’s current security posture, KSPM score included.
Security audits vs Security Posture
Because security audits will come. They have become common procedures in today’s companies. Maybe the first thought that comes to mind when thinking about security audits can be negative, security audits are not something to fear. Actually, they help organizations protect sensitive data, identify security risks, and ensure employees stick to security practices. Regular audits force us to continually re-evaluate our security policies or create new ones to keep up with the latest threats and also track the effectiveness of our security strategies. A security audit can be driven by a company, to comply with best practices or internal security guidelines. Companies that belong to a particular field that operates with sensitive data, may be forced to carry out these security audits based on industry regulatory standards, such as HIPAA, NIST, etc. In the vast majority of cases, companies will have at least to comply with the national regulations of their countries.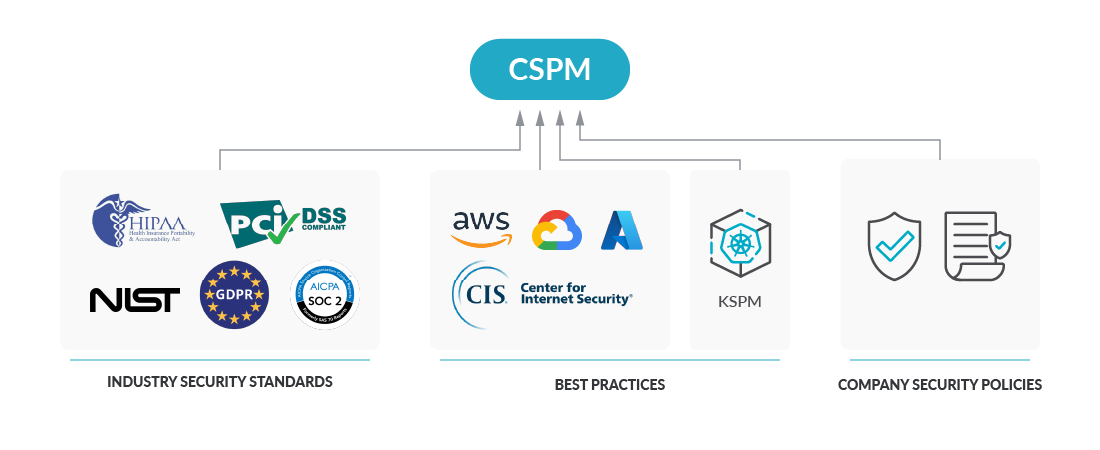 The Center for Internet Security (CIS) is an independent organization that provides configuration baselines and best practices for securely configuring a system. CIS guidence is one of the most used references among security teams. There are CIS Benchmarks for all kinds of IT environments, and Kubernetes has its own CIS benchmarking as well. No need to say that you can use the CIS Kubernetes Benchmarks to enhance your Kubernetes Security Posture :)
The Center for Internet Security (CIS) is an independent organization that provides configuration baselines and best practices for securely configuring a system. CIS guidence is one of the most used references among security teams. There are CIS Benchmarks for all kinds of IT environments, and Kubernetes has its own CIS benchmarking as well. No need to say that you can use the CIS Kubernetes Benchmarks to enhance your Kubernetes Security Posture :)
Don’t get caught off guard
If you are using Kubernetes to orchestrate your workloads, in the cloud or on-prem, there is a good chance that you hear that fearsome sentence one day: “We need to improve our Kubernetes Security Posture“. For the Infra/Ops teams that are already overwhelmed in their daily duties, all the extra work to fix Kubernetes’ bad practices can be a big headache. Depending on the tools and processes you have put in place to provide Kubernetes Security Posture insights, you will be more or less successful when trying to improve the KSPM score. Start tracking your Kubernetes Security Posture from the beginning. Some of the questions you should be asking to check if you have the proper tooling or processes could be:- What is my KSPM score?
- Which controls are we failing?
- How can we decide which violations to fix first?
- What’s the quickest way to remediate specific issues?
KSPM to Improve Kubernetes Security Posture
You only need to follow these three septs to set up a strategy to improve your Kubernetes Security Posture:Step 1: Visibility – Set the basis
This might seem obvious but before you start you need to make sure everyone stays on the same page. We want the teams involved in the Kubernetes management process to be aware of the actual state of your KSPM score, right? Having visibility is going to be crucial to do a good job.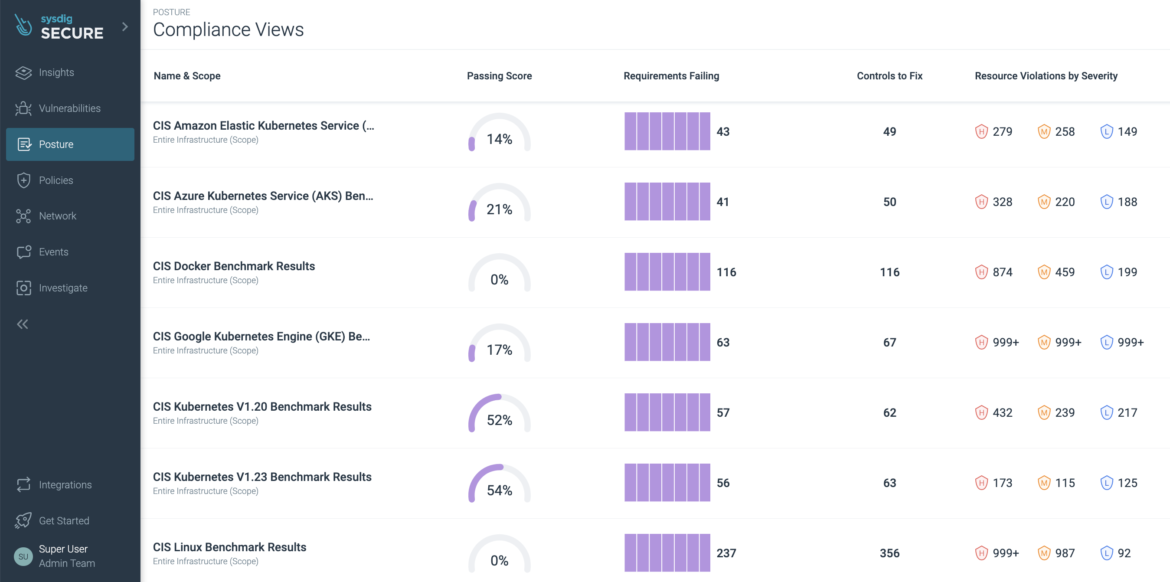
Step 2: Prioritize – Define your working strategy
Not all bad practices are rated the same. Some pose more risks than others. It is not the same to haveOver permissive access to a resource type than having ServiceAccounts with the Ability to create pods in a cluster (which can ultimately open up possibilities for privilege escalation).
Being able to filter and prioritize is key when designing your strategy. To optimize your time as much as possible, start remediating the highest risks first.
This can be the foundation to start your Kubernetes Security Posture improvement strategy, and how you would tackle it.
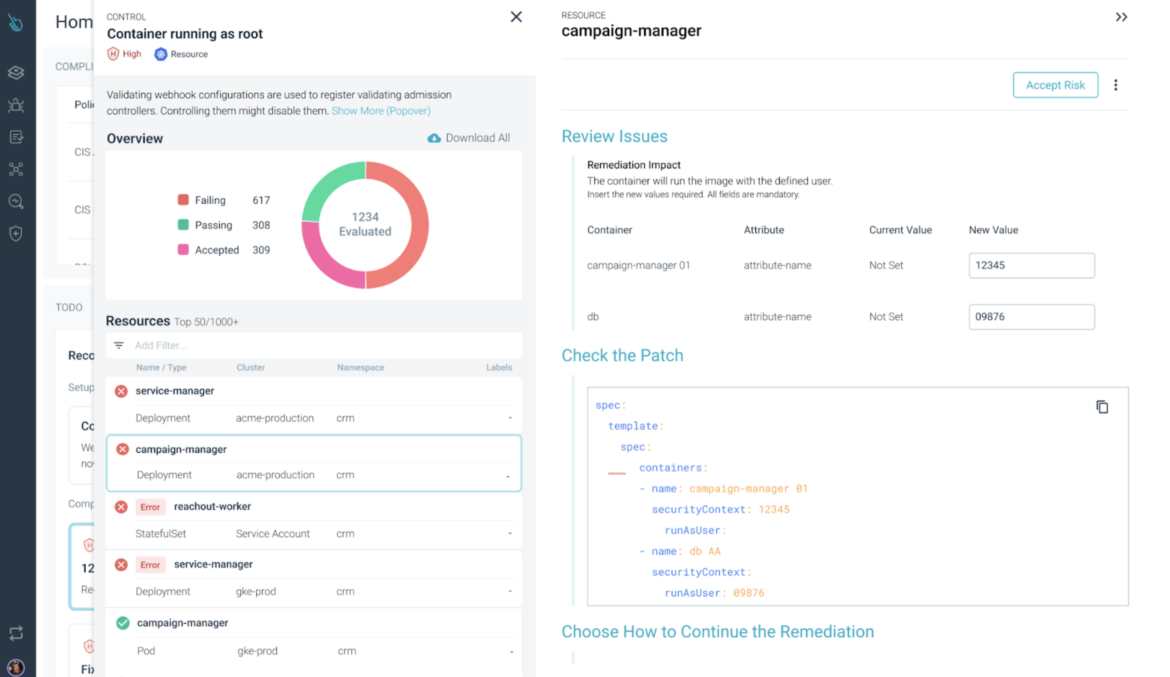
Controls are either failed or passed. There is no magic on it. But the reason behind why this happens can be slightly different.
Let’s take the Container permitting root control for instance. In this failing control, we can see that the actual attribute value hasn’t been set. Is not that it has a risky/non-permitted value.
- Not having enough time to plan ahead a deployment
- Insufficient knowledge of security risks of the underlying technology
- Lack of resource optimization.
Step 3: Remediate – at the source
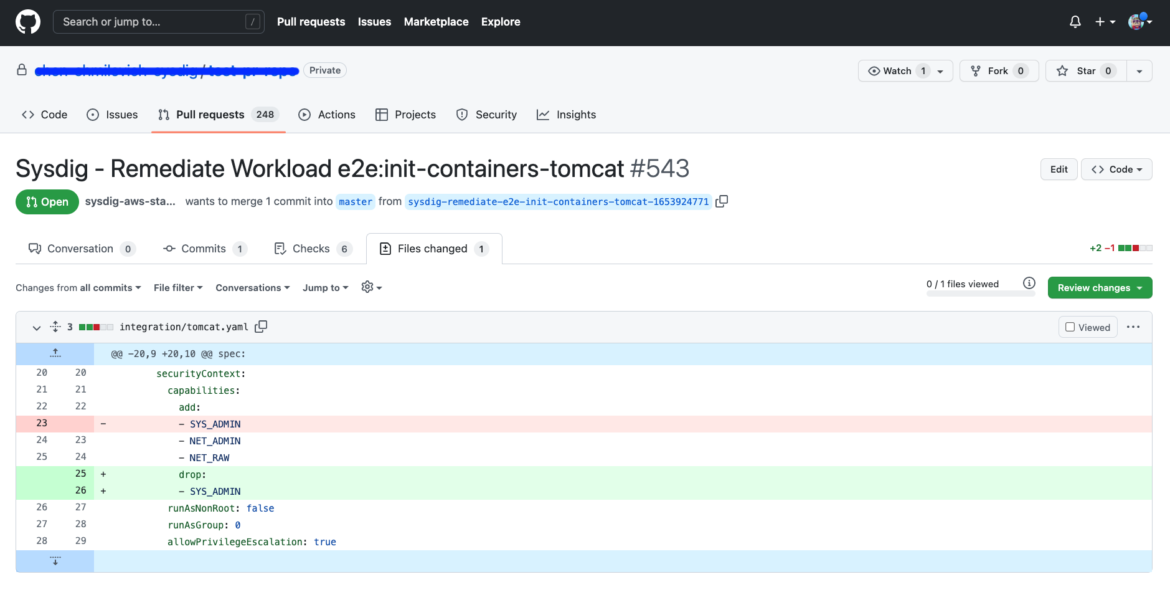
When having to remediate failed controls from security policies, teams that use automation, prefer to keep using this methodology, integrating the remediation workflow with their tools. At Sysdig you can tie Kubernetes security violations with the Infrastructure-as-Code (IaC) manifest that defines your Kubernetes resources, in your git repository, identifying the two ends of the pipeline. Using this approach will narrow your attack surface at runtime but also, you can be sure those changes are reflected in your IaC manifest and won’t happen again.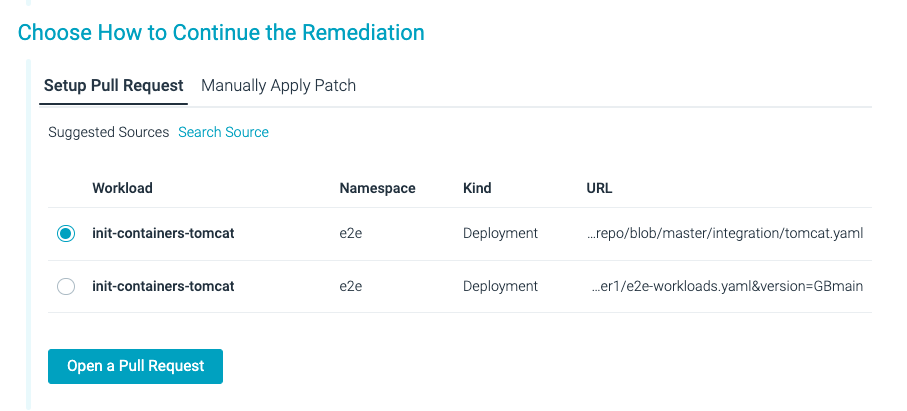
- Manually – You can copy the patch code and apply it in production.
- Automated – You can remediate at the source simply creating a pull request integrating the patch (as well as checking for code formatting cleanup).
Conclusion
Kubernetes requires a thoughtful design to ensure that governance, compliance, and security controls are included. You can use automation to remediate and maintain a well-managed and secure cloud while increasing your Kubernetes Security Posture.
With a tool like Sysdig, that provides KSPM and actionable compliance, including automated remediation at the source code manifest, fixing security violations of the Kubernetes environment should not be something that is done all at once, in a rush, when an audit approaches, but rather a continuous improvement process that aims at obtaining a basically compliant/secure infrastructure that only requires minor adjustments every now and then.
Register for our Free 30-day trial and see for yourself!