Content
If you use Amazon’s Elastic Compute Cloud (EC2) service, you’re also using Amazon Elastic Block Store (EBS) to provide persistent storage capacity for those instances. EBS functions similarly to a hard drive, allowing the instance to create a file system and have persistent storage. This article will dive deeply into EBS and discuss the importance of encryption to secure its contents. We’ll discuss how to encrypt your EBS volumes and the impact of encryption on performance; we’ll also explore its impact on activities like snapshots, snapshot sharing, and the long-term security implications for encrypted volumes.
Elastic Block Storage and Encryption
AWS has made encryption of EBS volumes as easy as possible. When a volume is encrypted, all data stored on it is encrypted, including the boot and data volumes. When you attach an encrypted EBS to an EC2 instance, encryption extends beyond the stored data to all data transfers to and from the volume.
AWS supports a default encryption process that you can configure by region within your account. You can also choose between using AWS-created keys or a customer-managed key (CMK) to encrypt your volumes. In both cases, Amazon encrypts the data with industry-standard AES-256 encryption and stores the encryption key in the AWS Key Management Service (KMS). We’ll discuss the different encryption key options in a quick step-by-step guide to enabling encryption later in this article.
Some Questions You Might Have About Encryption:
Do I Need to Encrypt My EBS Volumes?
Ensuring that you encrypt all of your stored data is a best practice. Even if you think there is no value to a potential hacker, encryption by default reduces the chances that someone in your organization may make a mistake. AWS makes the encryption process incredibly seamless, which means there isn’t any reason not to encrypt your data.
Will Encryption Impact Performance?
AWS handles the encryption process transparently, and you should experience the same IOPS performance between EC2 and your EBS volumes with encryption as without. Even if there was a minor impact due to enabling encryption, it’s not worth leaving your data unencrypted in the cloud.
Quick Step-by-Step Guides to Enabling EBS Encryption
Let’s go through a few AWS console scenarios related to EBS encryption. We’ll discuss configuring the default encryption key for a region, creating a new encrypted volume, encrypting an existing volume, and what to do when sharing an encrypted snapshot with another account.
Configuring a KMS Key for a Region and Enabling Encryption by Default
Setting up an encryption key and enabling encryption for a region within your account forces the encryption of any new volumes created. This action is a good best practice for all regions you use. Begin by logging in to your AWS account and navigating to the EC2 home page in the region where you want to enable encryption. You’ll see a section for your account attributes at the top right corner of the EC2 dashboard. Click on the link under settings for EBS encryption.
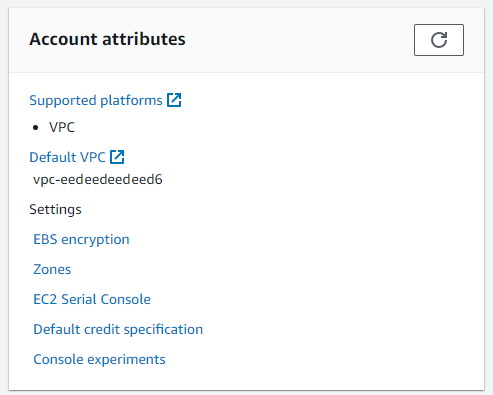
This link takes you to the management panel for EBS encryption. You’ll see the default setting that EBS encryption is disabled, similar to the screenshot below.
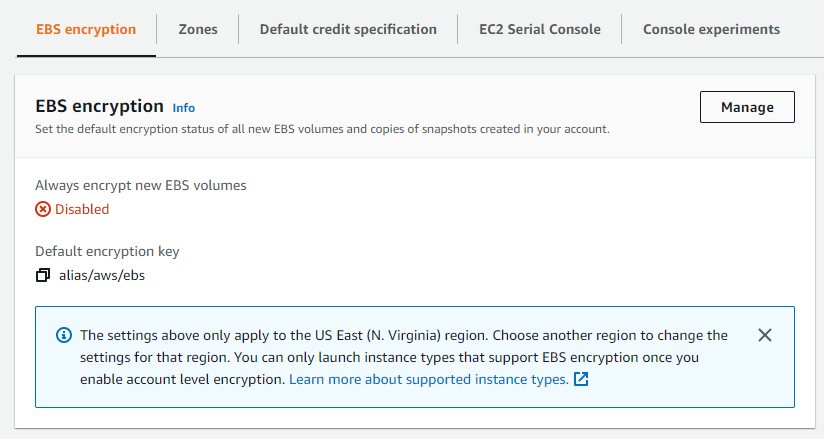
Click the Manage button to enable encryption for new EBS volumes and to set the Default encryption key.
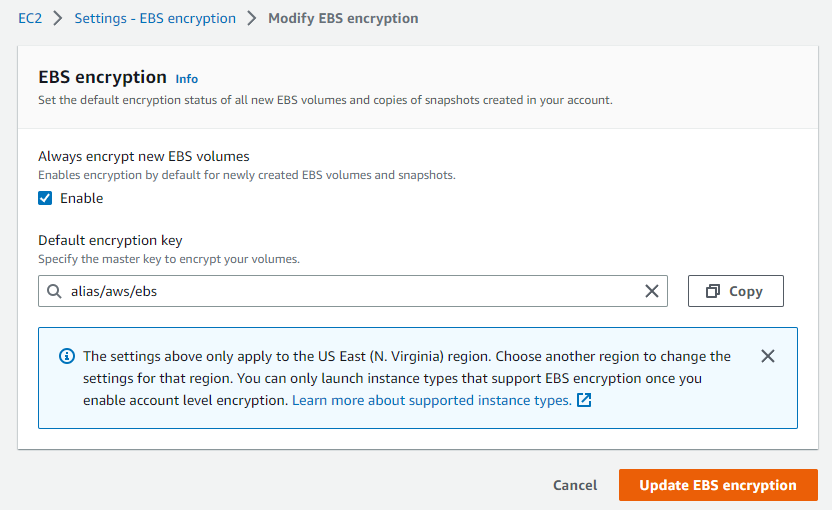
You can use the provided key or click in the text box to select an available CMK (Customer Managed Key). After you click the Update EBS encryption button, all new EBS volumes created in this region will be encrypted using the specified key. If you elect to use a CMK, you may see a charge if the number of keys exceeds the free tier threshold, but the amount charged is negligible.
Creating a New Encrypted Volume
AWS supports encryption for the current generation of EC2 instances, and many of the previous generation. If you are using an older or obscure instance type, check the EBS encryption requirements to ensure it is supported. You can create a volume while instantiating a new EC2 instance or a standalone volume. We’ll use the second method to limit the scope of this example.
From the EC2 home page, select Volumes from the navigation panel on the left-hand side, under the Elastic Block Store section. Initiate the creation process by clicking the orange Create volume button.
After selecting the volume type, size, and availability zone (AZ), you’ll see the Encryption section, as shown below. If you follow the steps above, you’ll see a message that “Encryption is set by default.” If this is the case, you can continue using the default key for the region or select a different key if desired. If your account does not have encryption enabled, you’ll need to check the Encrypt this volume box to display this section and select the encryption key.
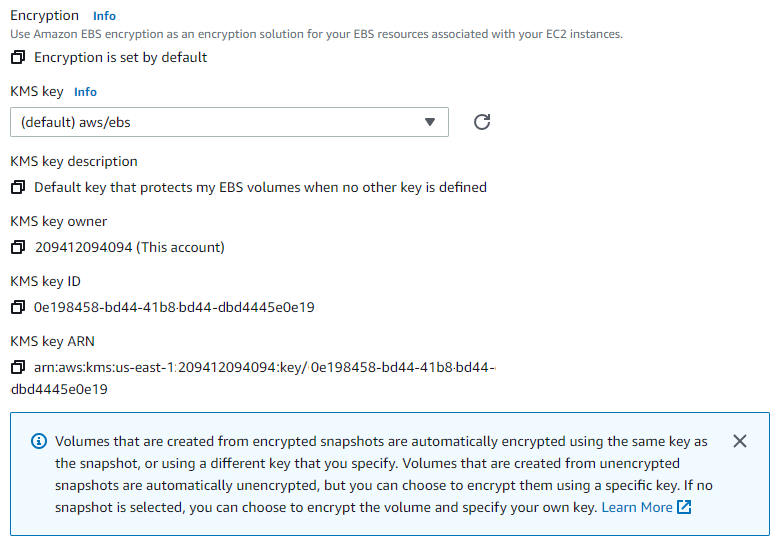
That’s all there is to it. After you click the Create volume button, you’ll have an encrypted volume ready to attach to an EC2 instance.
Creating an Encrypted Volume from an Existing Unencrypted Volume
The directions above are perfect if you’re starting with a brand-new account. But there’s a good chance that if you’re reading this, you already have some unencrypted volumes, and now you’re trying to figure out how to encrypt them. This section is for you. Unfortunately, there isn’t a single step to encrypting an unencrypted volume. You can, however, accomplish this with a couple of steps.
You can make your life easier if you enable encryption by default for your region, but you can create an encrypted copy of your volume without that step.
From the Volumes dashboard inside AWS EC2, identify the volume you need to encrypt. Check the box in the leftmost column of the volume you want to work with and click Create snapshot from the Actions dropdown. It’s helpful to add a description to the snapshot, but not required.
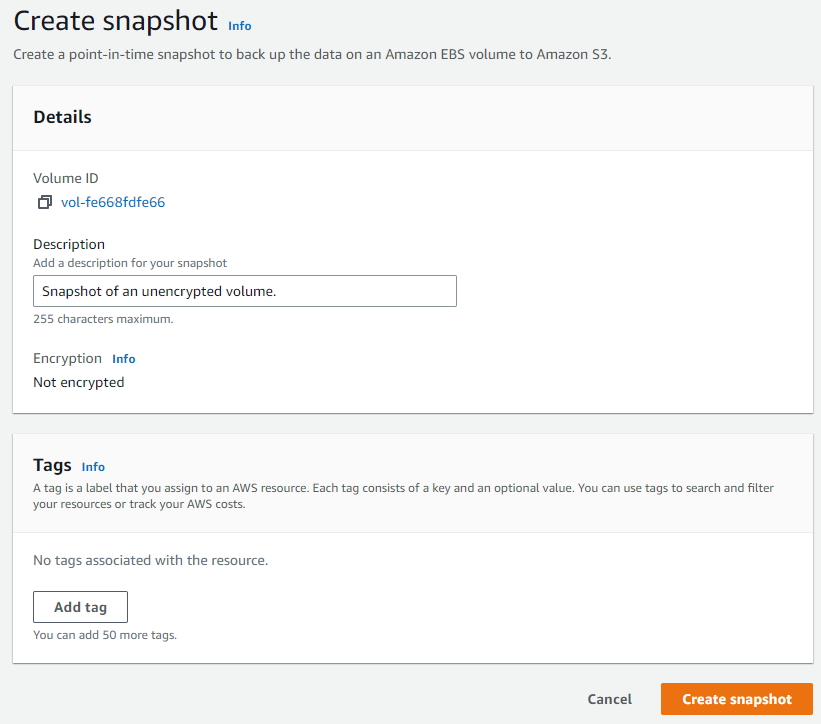
Once you have a snapshot of the unencrypted volume, navigate to the Snapshots dashboard (located directly below the link to the Volumes dashboard). Find and check the box next to the unencrypted snapshot and select Copy snapshot from the Actions dropdown.
If encryption is enabled by default, you only need to select the appropriate KMS key and click Create snapshot. If you don’t have encryption enabled, you can still choose the Encrypt this snapshot option, and AWS will prompt you to select a KMS key and display the key details. The image below shows the process in an account which does not have encryption enabled by default.
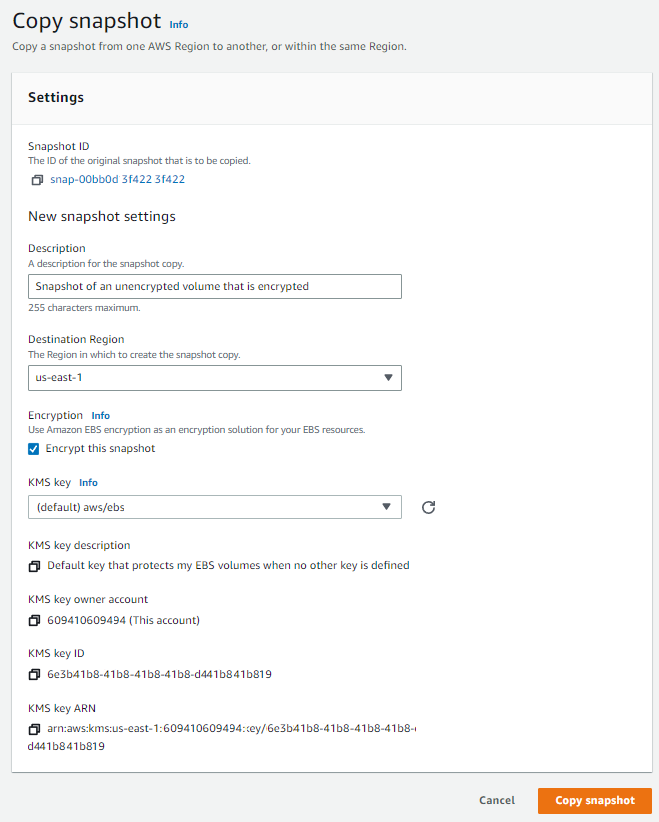
It takes AWS a minute or two to create the encrypted snapshot copy, but once it has been completed, you can create a new encrypted volume from the snapshot and use it to replace the unencrypted volume.
Sharing an Encrypted Snapshot with Another Account
The challenge with sharing an encrypted snapshot with another account is that it needs to be encrypted using a Customer Managed Key (CMK) that you can share with the other account. If the encrypted snapshot uses a KMS-generated key, you’ll need to create a copy of it and encrypt it with a CMK. You can do this by following the above steps to encrypt an unencrypted snapshot.
Other Challenging Encrypted/Unencrypted Situations
The examples above should cover most of the initial challenges you may encounter when using EBS encryption in your AWS account. You may face additional challenges if you support an environment with a mix of encrypted and unencrypted EBS volumes. The AWS EBS documentation covers several of these encryption scenarios, including re-encryption of snapshots and volumes and migration of data between encrypted and unencrypted volumes.
EBS Key Rotation and Long-Term Security
We’ve already discussed that enabling encryption by default is a best practice for your AWS accounts. Another best practice from a security perspective is to ensure you regularly rotate your cryptographic keys. AWS has also made this process as simple and transparent as possible.
You can enable automatic key rotation on your account, and KMS will create new keys annually. When this occurs, existing volumes still have access to the previous key and can continue using it as long as you don’t delete the previous key. Any new volumes will use the new key, and your EC2 instances can efficiently and effectively communicate with all volumes, old and new.
Next Steps
Encrypting your EBS volumes ensures that your persisted data is protected, and AWS has made the process as seamless and transparent as possible. Enabling encryption by default ensures all new volumes and snapshots will be encrypted and eliminates the chance of someone inadvertently creating an unencrypted resource. If you have additional questions or challenges not addressed above, the AWS EBS documentation is an excellent and well-maintained resource for all things EBS-related.

