Sysdig 2024
Cloud-Native Security
and Usage Report
The cloud accelerates innovation. But what are the risks of moving too fast?
After analyzing millions of containers and thousands of cloud services, users, and roles, the results are in! The biggest trends we’re seeing include:
- Shift-left still isn’t a reality yet
- Identity management is the most overlooked cloud risk
- Short-lived containers will always present risk
- Enterprise GenAI adoption is growing slower than expected
Dig into the report to uncover the latest insights and best practices for cloud-native security and usage today.

Download the Report
This site is protected by reCAPTCHA and the Google Privacy Policy, Microsoft Privacy Policy and Terms of Service apply.
Secure practices or convenience: What are organizations choosing?
Convenience and user experience often trump security so that organizations can ensure availability and high productivity.
Runtime security still rules while shift left isn’t a reality yet
Runtime prioritization can help reduce critical and high vulnerabilities by 50%. Organizations should be scanning for, identifying, and remediating vulns in the pre-delivery pipeline before runtime.


Identity management is the most overlooked cloud risk
Enforcing least privilege will reduce misconfiguration and privilege escalation attack opportunities.
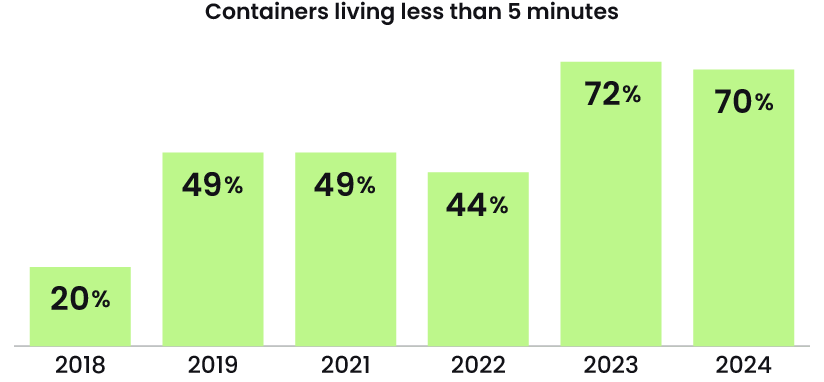
Short-lived containers will always present risk
With automation, attackers can enter and move laterally before the end of a container’s lifespan, reinforcing the need for continuous threat detection, and a record for investigations.

Enterprise GenAI adoption is growing slower than expected
Most AI packages are used for data correlation and analysis–not for managing security practices or improving detections.

