Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

We’re excited to announce that Falco, the CNCF graduated runtime security project, is now officially available as an AWS-validated Amazon EKS add-on. This marks a significant milestone in making runtime security more accessible and easier for Amazon Elastic Kubernetes Service (EKS) users to deploy.
Why this matters
Runtime security has become a critical requirement for cloud-native environments. While traditional security tools focus on known vulnerabilities and signatures, modern threats require behavioral monitoring that can detect zero-day exploits and insider threats in real-time.
Falco addresses this need by monitoring system calls at the kernel level, providing deep visibility into what’s actually happening inside your containers and hosts. Here’s why having Falco as an EKS add-on is game-changing:
1. Simplified deployment and management
Most users currently deploy Falco using the Helm chart, which requires managing Helm releases, updating values files, and handling upgrades manually. With the EKS add-on, you get:
- Single-command installation without needing Helm
- Automatic integration with EKS cluster lifecycle
- No need to manage separate Helm repositories or releases
- Simplified updates through the EKS add-on update mechanism
2. Seamless integration with AWS services
As an official add-on, Falco integrates naturally with the AWS ecosystem:
- Direct streaming of security events to Amazon CloudWatch
- Native support for AWS CloudTrail events alongside syscall monitoring
- Automatic tagging and correlation with EKS cluster metadata
- IAM Roles for Service Accounts (IRSA) pre-configured for secure AWS service access
3. Automated lifecycle management
When new versions of Falco are released with critical security updates or new detection capabilities, you can update with confidence knowing AWS has tested the compatibility with your EKS version.
Prior to upgrading, it is essential to review the release notes for any breaking changes in newer versions.
4. Consistent deployment across clusters
For organizations managing multiple EKS clusters, the add-on ensures consistent Falco deployments across all environments without the configuration drift that can occur with Helm-based deployments.
Getting started
Installing Falco on your EKS cluster is now as simple as running a single command. Here’s how to get started:
Prerequisites
- An EKS cluster running Kubernetes 1.25 or later
- The Falco EKS add-on requires network connectivity to download rules and plugins from the Falcoctl artifact registry. Ensure your EKS nodes can access:
- https://falcosecurity.github.io/falcoctl/index.yaml (Falcoctl registry index)
- ghcr.io (GitHub Container Registry for downloading artifacts)
Installation
Note: At the time of writing, the latest add-on version is v0.41.0-eksbuild.1
Option 1: Using AWS CLI
export ADD_ON_VERSION=v0.41.0-eksbuild.1
aws eks create-addon \
--cluster-name <cluster-name> \
--addon-name sysdig_falco \
--addon-version ${ADD_ON_VERSION} \
--region <cluster-region>Option 2: Using eksctl
export ADD_ON_VERSION=v0.41.0-eksbuild.1
eksctl create addon \
--cluster <your-cluster-name> \
--name falco \
--version ${ADD_ON_VERSION} \
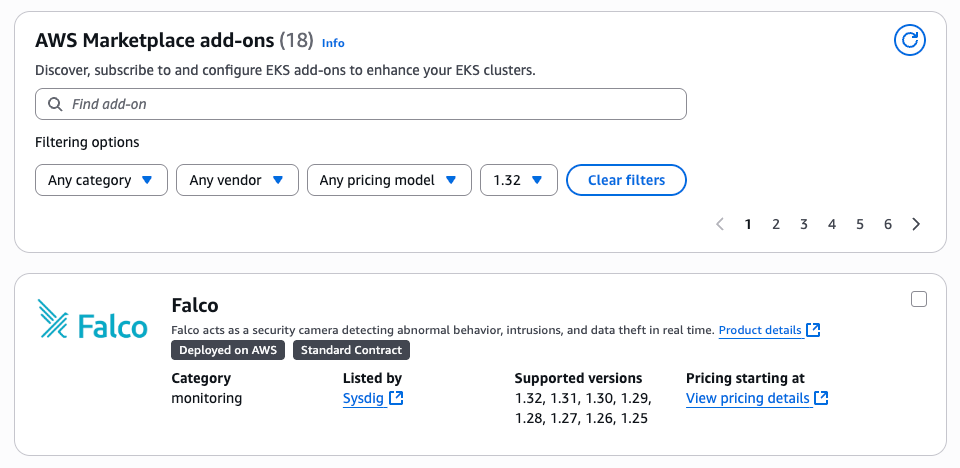
--region <cluster-region>Option 3: Through the AWS console
- Navigate to your EKS cluster in the AWS Console
- Click on the “Add-ons” tab
- Click “Get more add-ons” and search for “Falco” within the section at the bottom
- Mark the checkbox from the right and proceed to the next step
- Configure the IAM role and version
- Click “Add”
About Falco rules
Falco rules are the heart of its detection engine. Each rule defines a security policy that describes suspicious or malicious behavior to detect. Rules are written in YAML and use a powerful condition language that can analyze system calls, file access, network connections, and process behavior in real-time.
A typical Falco rule consists of:
- Condition: The specific behavior pattern to detect (e.g., “a shell is spawned inside a container”)
- Output: The alert message with contextual information about the event
- Priority: The severity level (INFO, WARNING, ERROR, CRITICAL)
Out of the box, Falco comes with a comprehensive set of rules including:
- Terminal shell in container
- Netcat Remote Code Execution in Container
- Drop and execute new binary in container
- Linux Kernel Module Injection Detected
- And many more…
For a deeper look into the rules configured, you can check them within the Falco rules file hosted in Github.
Tuning Falco rules
While the EKS add-on uses default rules, you can still customize them using ConfigMaps by loading your rules.
How it works
Falco loads rules files in order, allowing you to:
- Override existing rules (change priority, disable, modify conditions)
- Add new custom rules
- Keep all default rules intact
Steps to customize rules
- Create a ConfigMap with your rule overrides (in this case the manifest file is called “my-falco-rules.yaml”):
apiVersion: v1
kind: ConfigMap
metadata:
name: my-falco-custom-rules
namespace: falco
data:
my-falco-rules.yaml: |
- rule: Terminal shell in container
override:
enabled: replace
enabled: false2. Apply the ConfigMap:
kubectl apply -f my-falco-rules.yaml3. Patch the DaemonSet to mount your custom rules:
kubectl patch daemonset falco -n falco --type=json -p='[
{bas
"op": "add",
"path": "/spec/template/spec/volumes/-",
"value": {
"name": "custom-rules-volume",
"configMap": {
"name": "my-falco-custom-rules",
"items": [{
"key": "my-falco-rules.yaml",
"path": "my-falco-rules.yaml"
}]
}
}
},
{
"op": "add",
"path": "/spec/template/spec/containers/0/volumeMounts/-",
"value": {
"name": "custom-rules-volume",
"mountPath": "/etc/falco/rules.d/my-falco-rules.yaml",
"subPath": "my-falco-rules.yaml",
"readOnly": true
}
}
]'4. Verify that your custom rules (my-falco-rules.yaml) are loaded correctly with the default ones in the pods:
kubectl logs -n falco -l app.kubernetes.io/name=falco -c falco | grep -i "rules"
Tue Jun 17 11:27:30 2025: /etc/falco/falco_rules.yaml | schema validation: ok
Tue Jun 17 11:27:30 2025: /etc/falco/rules.d/my-falco-rules.yaml | schema validation: ok-
Important notes
- Persistence: After EKS add-on updates, you’ll need to apply again the DaemonSet patch
- Testing: Always test rule changes in non-production environments first
Viewing security events
If any Falco rule is triggered, events will appear in pods’ output. You can view them using:
kubectl logs -n falco -l app.kubernetes.io/name=falcoRemember that Falco output may be buffered.
Next steps
- Tune your rules: Start with the default ruleset and gradually customize based on your workload patterns
- Set up alerting: Configure CloudWatch alarms for critical Falco events
- Review best practices: Check out the Amazon EKS Best Practices Guide for runtime security
Troubleshooting
If you encounter issues, check the Falco pods status:
kubectl get pods -n falco
kubectl logs -n falco -l app.kubernetes.io/name=falco
kubectl describe daemonset falco -n falco
Staying updated
Currently, AWS doesn’t provide automatic notifications for EKS add-on updates. We recommend periodically checking for new versions using:
aws eks describe-addon-versions --addon-name sysdig_falco --kubernetes-version <your-k8s-version> --region <your-region>Get involved
Falco is an open-source project with a vibrant community. Here’s how you can contribute:
- Join the Falco Slack community
- Contribute rules to the falco-rules repository
- Report issues or feature requests on GitHub
Conclusion
With Falco now available as an EKS add-on, AWS users can deploy enterprise-grade runtime threat detection with the same ease as any other AWS service. Whether you’re protecting against container escapes, detecting cryptocurrency miners, or ensuring compliance, Falco provides the deep visibility you need.
Start securing your Amazon EKS workloads today by installing the Falco add-on!


