Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

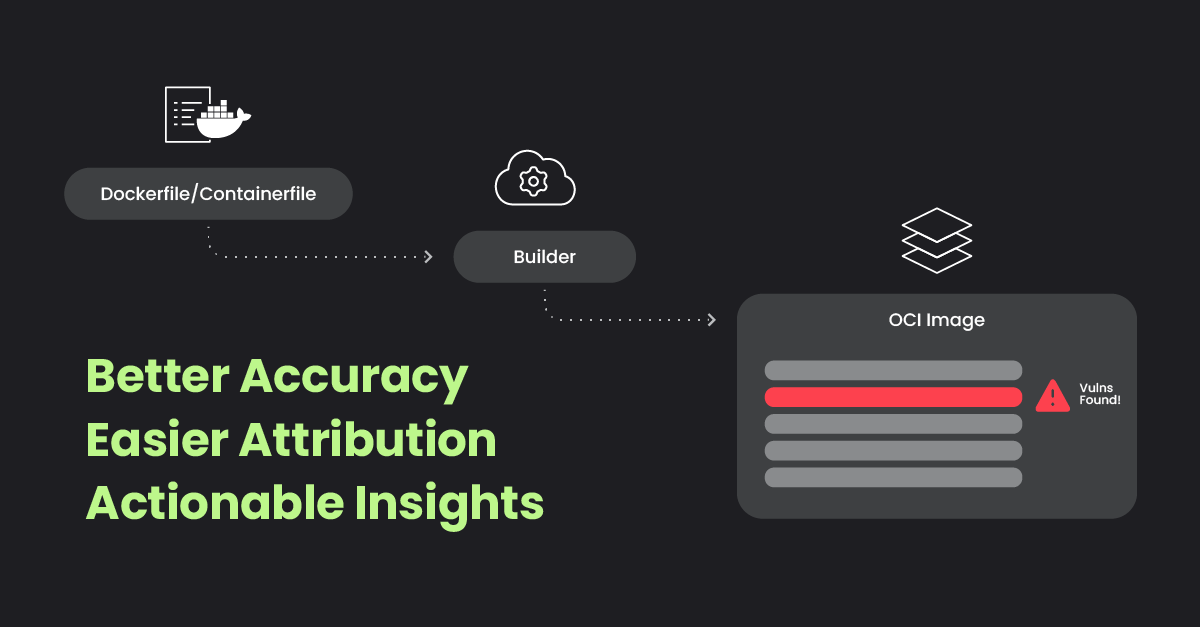
Containerized applications deliver exceptional speed and flexibility, but they also bring complex security challenges, particularly in managing and mitigating vulnerabilities within container images. To tackle these issues, we are excited to introduce Layered Analysis — an important enhancement that provides precise and actionable security insights.
What's new: Layered Analysis capabilities
Layered Analysis enhances our container security toolkit by offering a granular view of container images, breaking them down into their composing layers. This capability enables more accurate identification of vulnerabilities and optimized remediation workflows by clearly discerning whether vulnerabilities belong to the base image or the application layers, aiding in proper team assignment and resolution.
Key benefits
- Enhanced accuracy and reduced time to fix: Identify vulnerabilities at each container image layer, pinpointing the specific package and instruction responsible, thereby reducing fix time.
- Facilitate attribution and ownership: Discern whether vulnerabilities belong to the base image or the application layers, aiding in proper team assignment and resolution.
- Actionable insights: Receive practical, contextual recommendations to expedite and prioritize vulnerability resolution.
Detailed insights with Layered Analysis
Container images are constructed in layers, with each change or instruction during the build process creating a new layer. Layered Analysis helps detect and display vulnerabilities and packages associated with each image layer, identifying different remediation actions and ownership depending on the layer introducing the vulnerabilities.
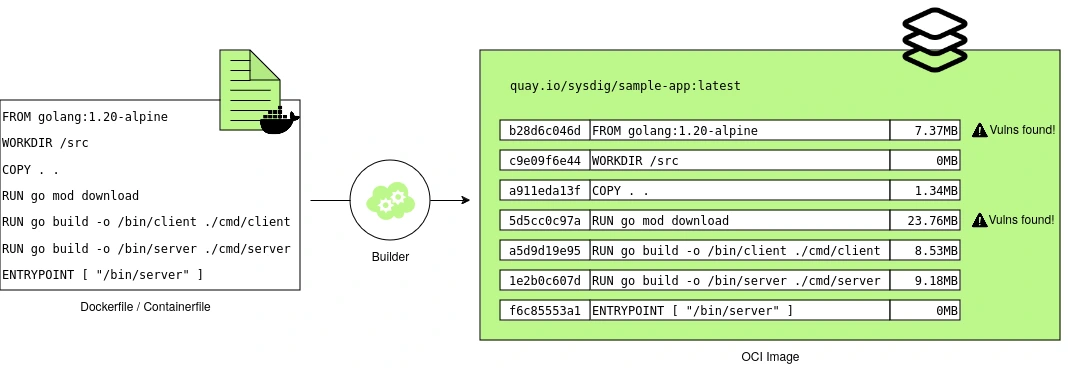
For example, vulnerabilities in the base OS layer, such as an end-of-life (EOL) Alpine version, can be remediated by updating the base image version, a task typically performed by the security team. In contrast, vulnerabilities in the application or non-OS layers, such as outdated Go libraries like Gin or Echo, can be addressed by updating the versions of libraries and dependencies, tasks that fall to the development teams.
How to enable and use Layered Analysis
Layered Analysis is now generally available and requires the following components for full functionality:
- Cluster and Registry Scanners: Automatically supported with platform scanning.
- CLI Version 1.12.0 or Higher: Ensure you are using the latest CLI version.
- CLI Enhancements: Utilize new flags (–separate-by-layer and –separate-by-image) to modify output and view image hierarchy or layer information.
- JSON Outputs: Updated to include new fields for detailed layer information.
Exploring the image hierarchy
Understanding the image hierarchy is key to Layered Analysis, as shown in the screenshot below.
This view shows the difference between base images and application layers, helping you quickly identify where vulnerabilities come from:
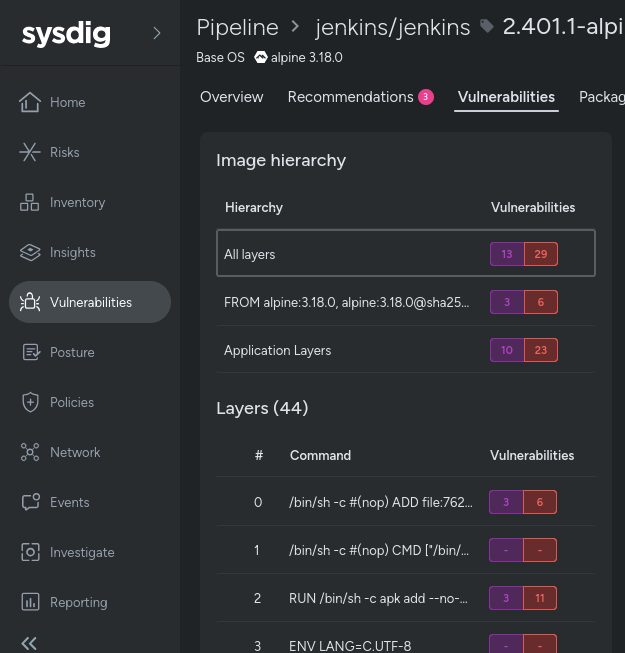
- All layers: Shows the total number of vulnerabilities in the final image, including both application and OS layers. If a vulnerability is fixed in an intermediate layer, it won't be included in the total count.
- Base Images (prefixed with FROM): Display vulnerabilities present in the base image, including those inherited from parent images.
- Application layers: Only show vulnerabilities introduced in the application layers, excluding those from base images.
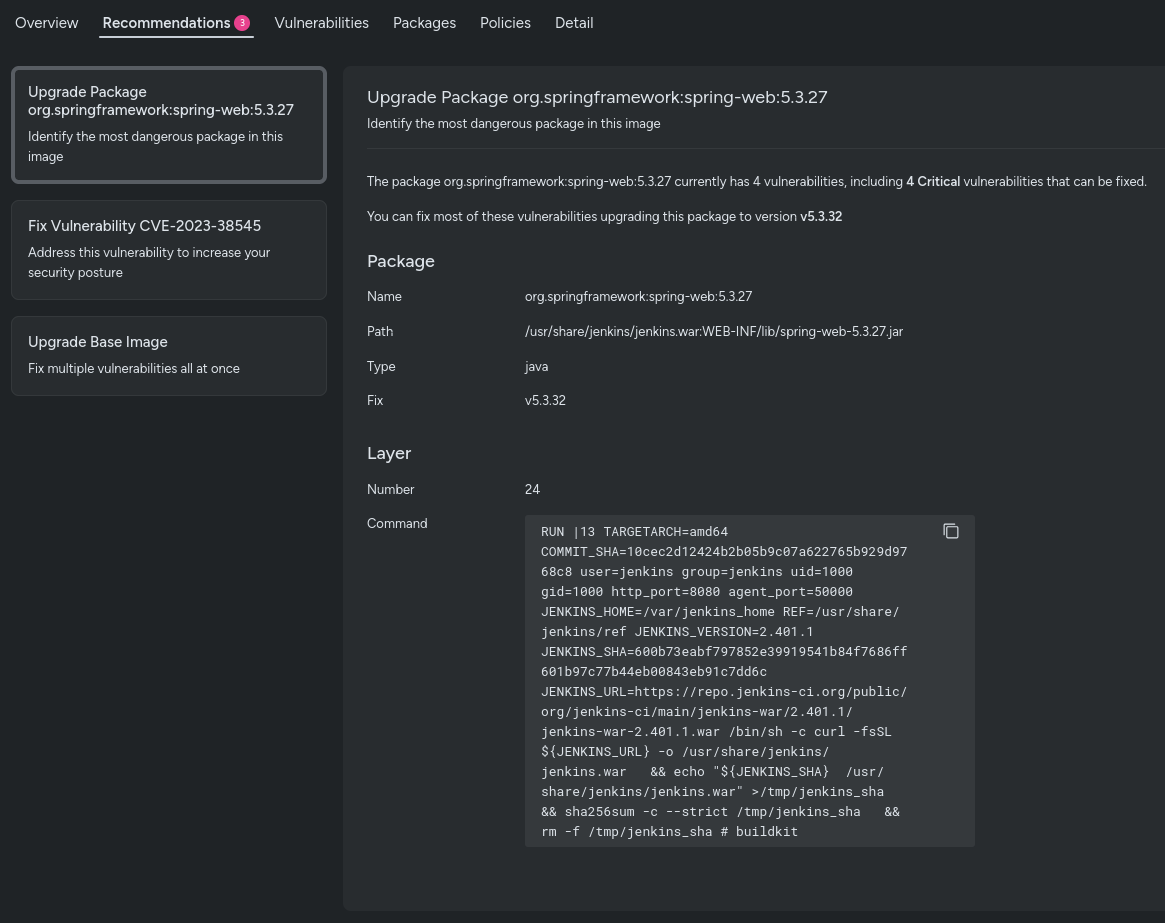
Actionable recommendations
Layered Analysis doesn't just identify vulnerabilities; it also provides recommendations to fix them. You'll receive suggestions to upgrade base images, address the worst vulnerabilities in application layers, and fix problematic packages.
These actionable insights help streamline the remediation process, ensuring that vulnerabilities are addressed efficiently and effectively.
Full visibility of image history
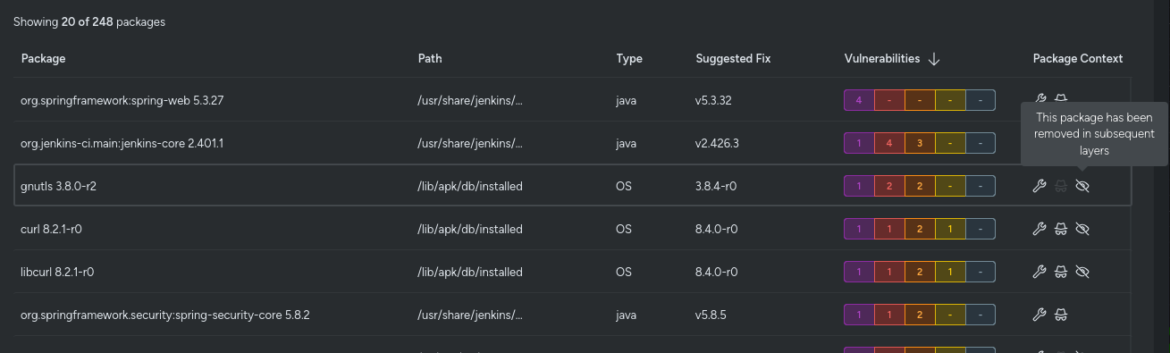
Layered Analysis also offers full visibility into the history of your container image. You can see packages that existed in previous layers but were removed in subsequent layers.
While these packages no longer pose a security issue, having this historical view is invaluable for understanding the evolution of your image and ensuring comprehensive security management.
This helps teams trace back through changes, making it easier to collaborate and maintain a secure container environment.
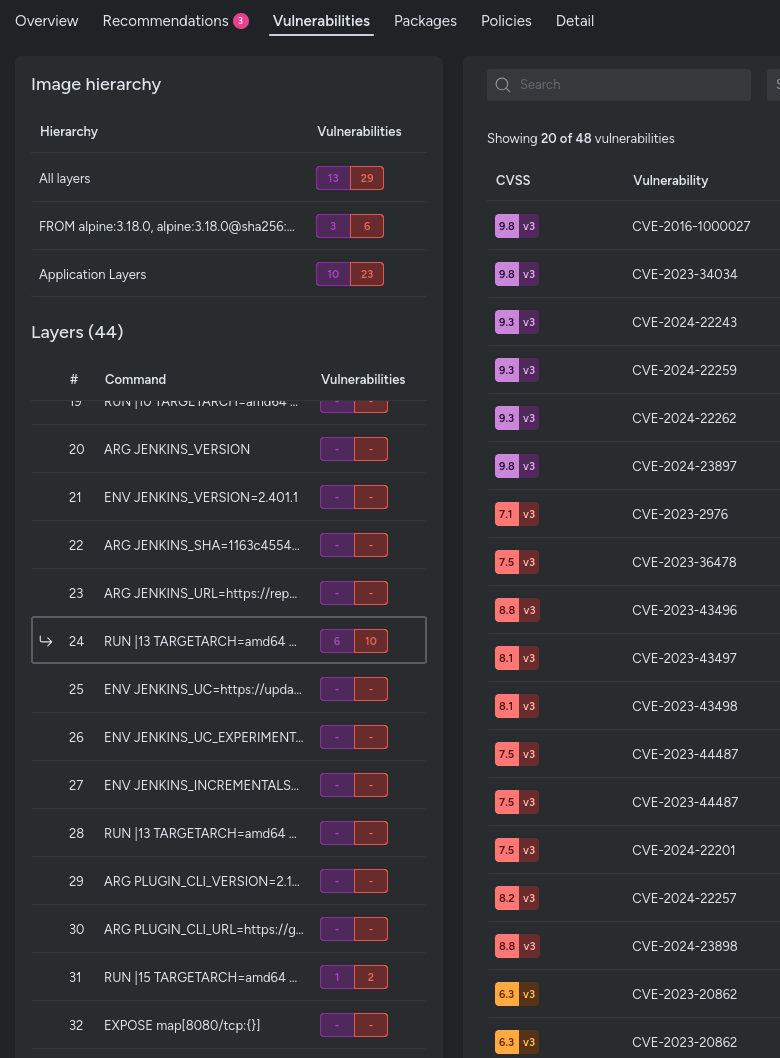
Investigate single layers
Another powerful feature of Layered Analysis is the ability to investigate single layers of your container image. You can see exactly what packages exist in each layer and identify any vulnerabilities introduced at that specific stage.
This granular investigation capability allows teams to pinpoint the source of security issues and understand the impact of each layer's changes. By isolating and analyzing single layers, you can more effectively manage and remediate vulnerabilities.
Leveraging Layered Analysis for better security
Layered Analysis empowers security and development teams by providing a clear and actionable view of container image vulnerabilities. By enhancing the precision of vulnerability identification and optimizing remediation workflows, teams can effectively reduce risks and improve overall security.
With Layered Analysis, teams can pinpoint exactly where a vulnerability was introduced, identifying the specific layer responsible. This capability is particularly useful in large organizations where multiple teams are involved in containerized applications lifecycle, from building images to deploying and monitoring their health — such as infrastructure engineers creating/curating base images, developers packaging applications, and all of them working together to make sure workloads are as secure and vulnerability free as possible and security patches are promptly applied. By tracing vulnerabilities back to their source, teams can determine responsibility and ensure accountability.
By clearly distinguishing between base image and application layer vulnerabilities, Layered Analysis enables more efficient routing of remediation tasks. Security teams can focus on updating base images to mitigate inherited vulnerabilities, while development teams handle issues within the application layers. This structured approach not only streamlines the remediation process but also enhances the overall security posture of containerized environments.
Want to learn more? Reach out to your Sysdig representative, or book a demo here!


