
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Containers revolutionized how we build, deploy, and run applications with increased speed, agility, and scalability. But, as often happens with transformative technologies, they require an evolution to security strategy. Centralized deployments inside a protected perimeter gave way to continuous and distributed deployment of containers, creating a growing, dynamic, and distributed attack surface. IT and security teams were left blind and exposed in the cloud.
Adding to the pressure, reports such as Verizon's 2022 Data Breach Investigation Report (BIRD) show that threat activity is increasing and targeting everyone. The growth of supply chain and third-party relationships used as attack vectors, a thriving market of stolen credentials, the rise of RaaS (Ransomware as a Service), and increase in the number of critical vulnerabilities uncovered, including Log4j and Spring4Shell, are a reminder that threat detection is critical. It is wise to consider a breach and protect your runtime environment from common and emerging threats, such as malware, C&C, backboor, and cryptominers, among others.
The challenges faced when securing container environments start with complexity and the lack of real-time visibility into what is going on inside containers. But cloud-native's immutability principle can be a great asset to security teams. Immutability means that a container won't be modified during its life: no updates, no patches, no configuration changes. If a change happens, it is considered a drift, and possibly a sign of an attack. Unfortunately, container drift can also be caused by legacy practices when IT administrators provide maintenance on running containers, blending their actions with the ones of adversaries. Threat actors and malware, as well as the signs of their attack, can then hide in the activity noise and stay undetected while executing their malicious codes.
However, with Sysdig's Drift Control, teams have an easy way to detect, prevent, and speed incident response for containers that were modified in production to run new executables, also known as container drift. By blocking the drift, you prevent the attack.
Preventing attacks and legacy practices that increase risk
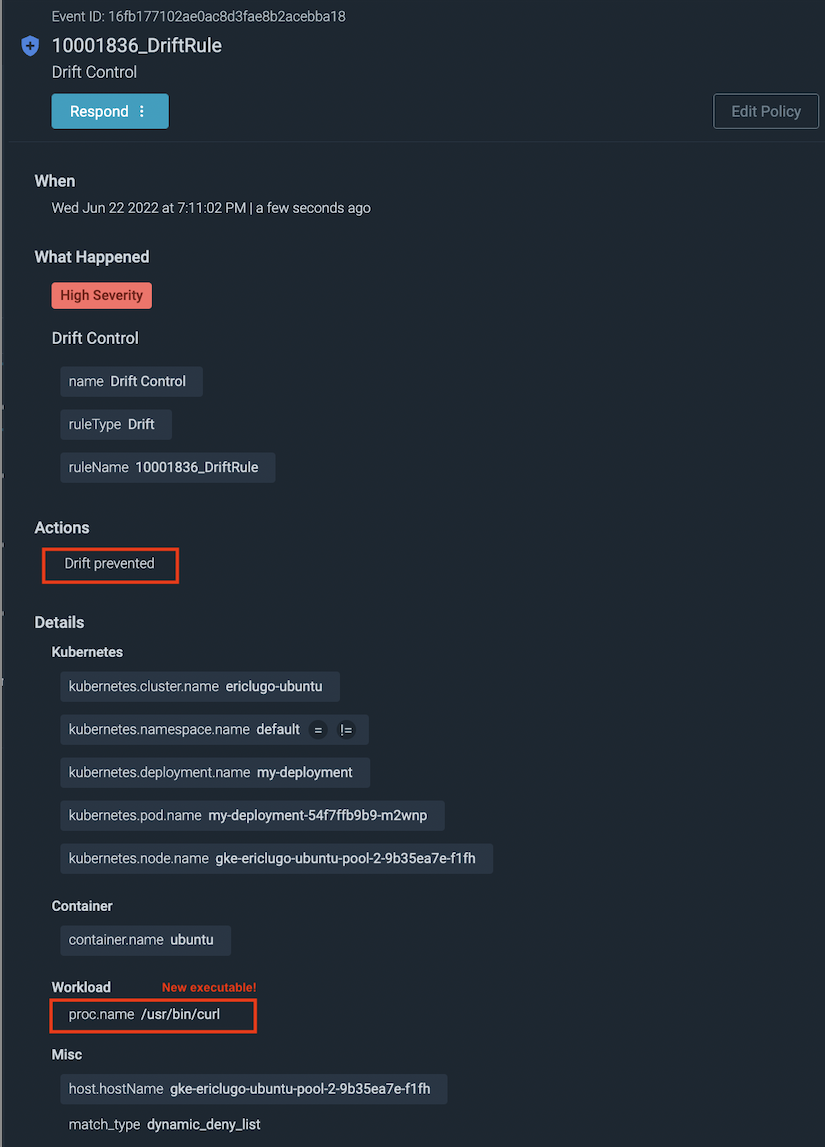
Attacks often include running adversary code on the victim's machines. Following the initial access, actors try to run scripts or malware with embedded executables to continue the attack, which could include enabling remote command and control (C2), making data unavailable for ransom, launching other attacks, among other malicious actions. Being able to identify which code doesn't belong is fundamental to thwart attacks before they can cause damage, and that is the job of Drift Control. It detects what is new or modified and blocks from execution.
Drift Control provides an easy way to prevent attacks at runtime by simply following security best practices of immutability and ensuring containers aren't modified after deployment in production. It also helps organizations move away from legacy practices that don't work in cloud-native environments, such as changing an application in production, downloading new packages, and installing IT tools for local maintenance. These practices increase risk by augmenting the attack surface that could be exploited and add to the noise by hiding similar actions, although malicious.
By detecting attempts to modify container executables in production and ensuring that those attempts are not successful, it forces operations to follow best practices and stops risky legacy practices from being carried over to cloud environments. Best practice calls for respecting the immutability principle, which means that you only fix at the source. This requires building a new container for deployment. Drift Control helps organizations put an end to ad hoc modifications, driving consistency from source to run and preventing actions that could be part of an attack.
How Drift Control works
Drift Control detects and prevents execution of executable files that were added or modified after a container is deployed into production. It uses real-time deep visibility into running containers to automatically identify those spurious executables.
Drift Control is a simple runtime security policy that can be quickly applied to the entire environment:
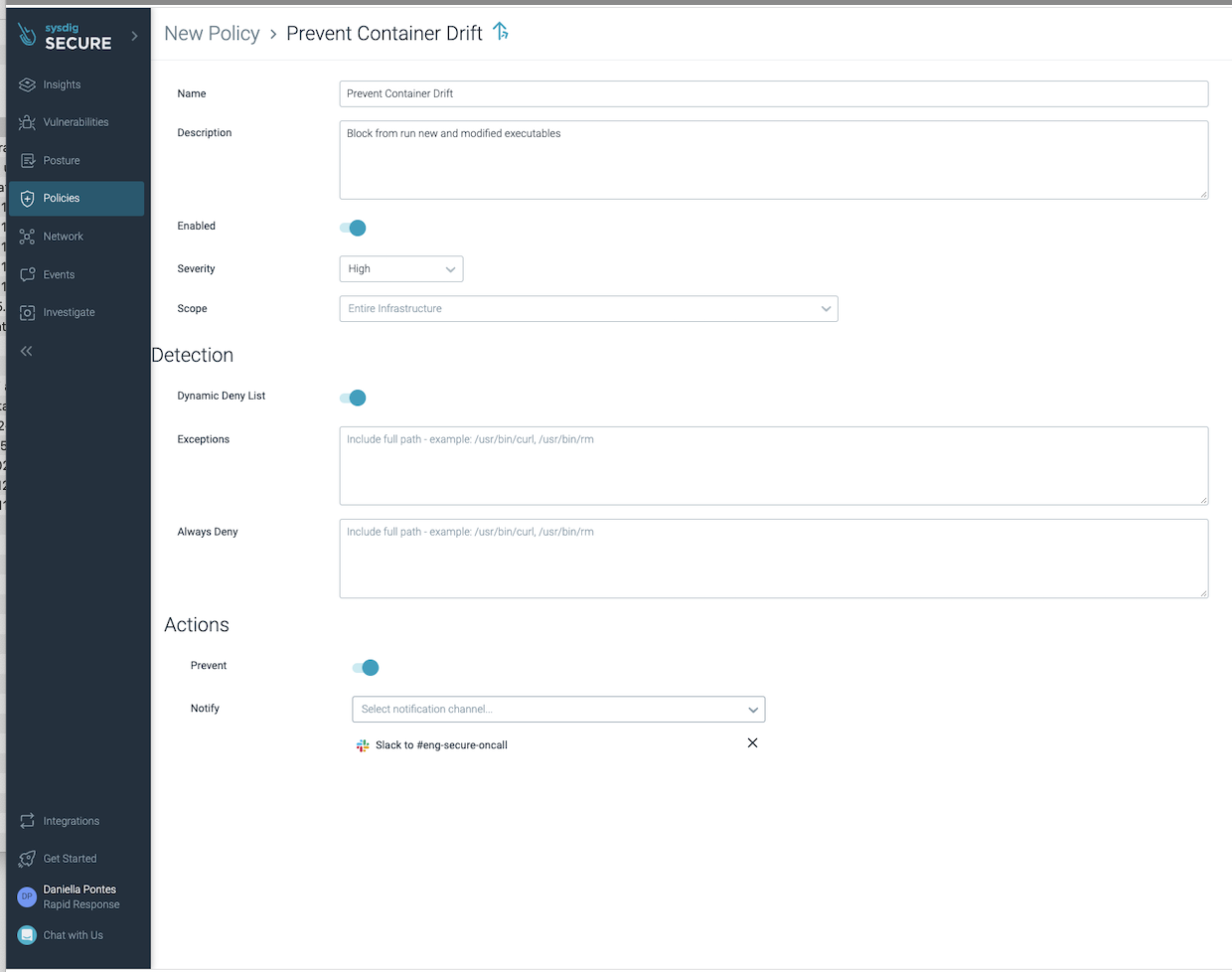
It can be enabled in detection mode to alert on attempts to run packages or binary files that were added or modified at runtime, such as:
- Execute a package that was downloaded or updated with package manager
- Execute a file whose permission/attribute has been changed to executable
And if in prevention mode, Drift Control blocks those detected new executables from running.
Key benefits delivered by Drift Control
- Prevent attacks by blocking container drift in production: Drift Control automatically flags and denies deviations from the original container, blocking malicious executables before damage is done.
- Enforce immutability best practice: Drift Control ensures that container software is not modified during its lifetime, driving good practices, consistency from source to run, and preventing actions that could be part of an attack.
- Enable easy and effective security: Teams are often overwhelmed by cloud-native complexity and blind to container drift, especially at scale. With Drift Control, security teams and IT can just enable it on the entire container environments and immediately start protecting runtime.


