
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Keeping up with workload vulnerabilities and cyber threats is huge challenge every day for security teams – especially those deploying cloud-native technologies. Cyber attacks are an unfortunate reality in our interconnected world. Security is constantly evolving. Developers, DevOps, and cloud teams must adopt new best practices that balance shift-left and shield-right security approaches to reduce risk. This is where the partnership of Sysdig and Snyk is aimed. Read on to consider if it is time for you to revisit your cybersecurity strategy for the cloud.
Shift left: Developer-driven security
An exploitable vulnerability in your code or container can compromise your whole cloud infrastructure. To get ahead of this risk, the practice of "shift-left" security has emerged to focus on addressing known security issues during the development pipeline with the specific intent of preventing runtime exploits.
In most organizations, developers aren't security experts. They care about security, but it's not necessarily where they want to spend their time. Security test automation is challenging. To successfully "shift left" requires new processes and tools to simplify the task. Equally important is training and education to gain cloud-native security expertise.
A number of technologies come into play in delivering application security during development. This includes:
- Software composition analysis (SCA): Discover and analyze open source software (OSS) for vulnerabilities and potential exploits.
- Static application security testing (SAST): Analyze source code, bytecode, or assembly code for security vulnerabilities.
- Infrastructure-as-code (IaC) auditing: Check IaC templates for misconfigurations and security flaws.
With each of these tools, you can help your organization avoid fire drills later in production by proactively identifying and addressing security issues, such as vulnerabilities and misconfigurations, before shipping your application.
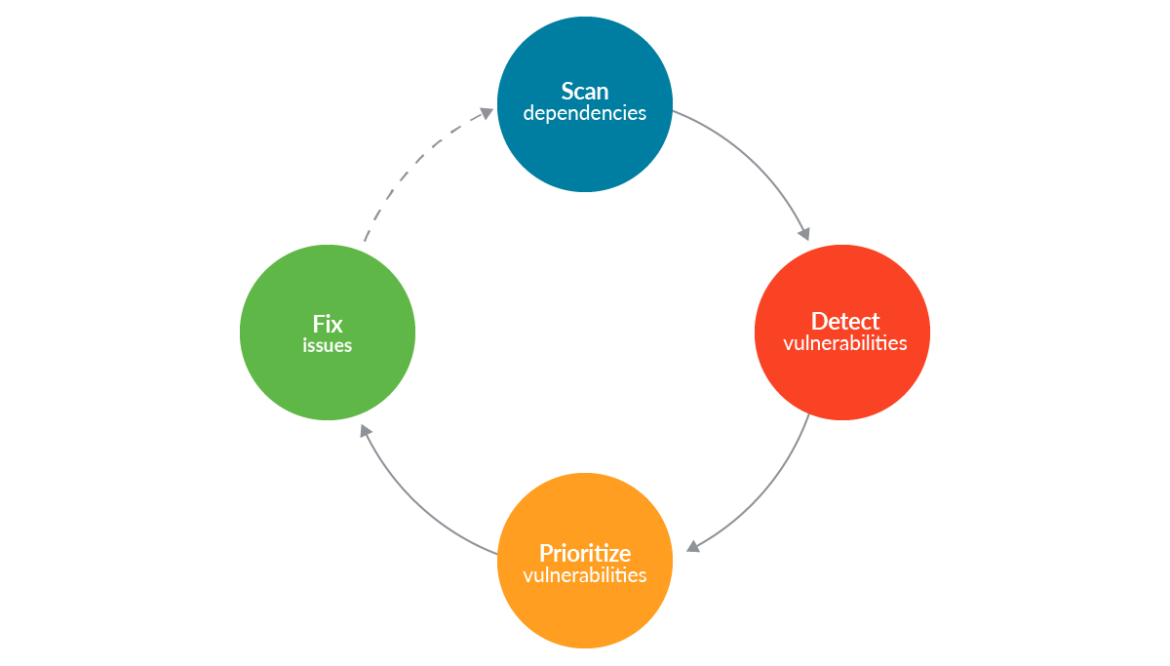
Shield right: Runtime security
Even with the perfect "shift-left" security practice, threats can arise in production. Many different attack vectors exist, and issues like ransomware, crypto mining, or other compromises aren't prevented by scanning code or images. Plus, because container vulnerabilities are discovered daily, your container, which seems safe today, can become a potential victim of newly disclosed exploits tomorrow.
"Shield-right" security emphasizes mechanisms to protect and monitor your running services. Traditional security practices with tools like firewalls and intrusion prevention systems (IPS) aren't enough. They leave gaps because they typically don't provide insight into containerized workloads and the surrounding cloud-native context.
Organizations deploying containers must account for container abstractions and ephemeral computing to avoid blind spots that can lead to security control failures. Threats can be detected by monitoring a reliable source of truth. For containers and cloud, this includes:
- Linux system calls
- Kubernetes audit logs
- Cloud activity logs
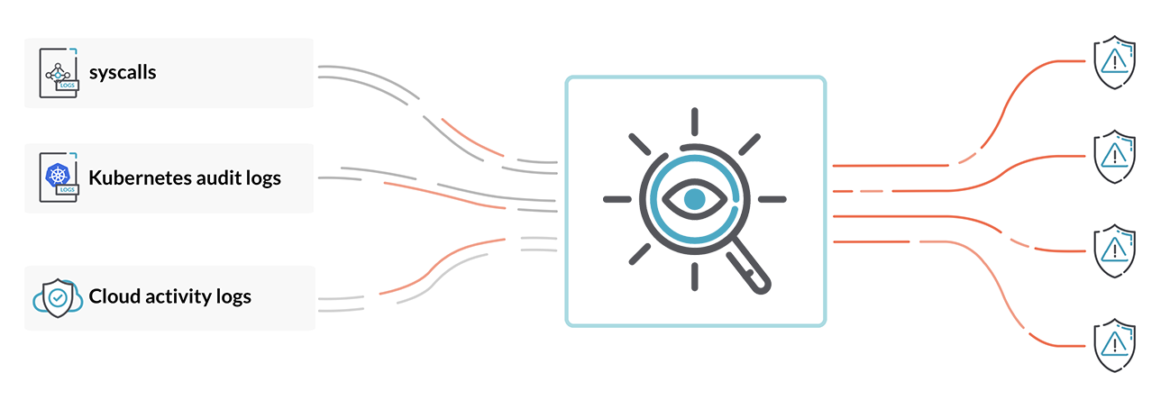
Digging through this data manually is, of course, untenable. By incorporating a policy engine, you can define what behaviors to flag in order to automate runtime security detection and response across your clusters, hosts, orchestration engine, and cloud.
Why you need both shift-left security and shield-right security
The goal of every cybersecurity program should be full lifecycle security – from the software supply chain to production. The practice of DevSecOps was born out of this need. It is also the catalyst for the partnership between Sysdig and Snyk to enable complete container security from source to run. Balancing development-stage security and runtime security is crucial. Developers need SAST and SCA tools that provide insight and actionable remediation advice on how to fix problems. SecOps teams need a runtime security net to catch issues that bypass defenses or exploit yet-to-be-addressed vulnerabilities.
Additionally, runtime visibility can help you to improve your shift-left practice. Once your containers are in production, a feedback loop to correlate issues discovered in runtime back to the underlying code helps developers know where to focus. Static security testing can also be informed by runtime intelligence to pinpoint what packages are actually executed inside the containers that run your application. This enables developers to deprioritize vulnerabilities for unused packages and focus instead on fixing exploitable, running vulnerabilities.
Conclusion
Rapid application deployment cycles and dynamic container environments have changed security requirements. Application development, infrastructure operations, and security teams must now more closely cooperate and work together to incorporate shift-left and shield-right practices into their security toolchains. With these two approaches, organizations can be more effective in detecting and responding to security vulnerabilities and incidents in modern application architectures.
To dive deeper and learn more about the challenges and practices of securing containers, Kubernetes, and cloud, download the whitepaper, Cybersecurity Strategy Must Include Both Shift-Left and Shield-Right Approaches.


