Secure AI workloads and accelerate innovation
Complete visibility and end-to-end security for AI workloads and training data
Protect AI without putting on the brakes
Elevate AI workload security with a platform built for AI environments
AI threat visibility
Automatically detects suspicious activities and threats within AI workloads in your environment across key solutions such as OpenAI, Amazon Bedrock, Anthropic, Google Vertex AI, IBM watsonx, and TensorFlow.
Risk prioritization
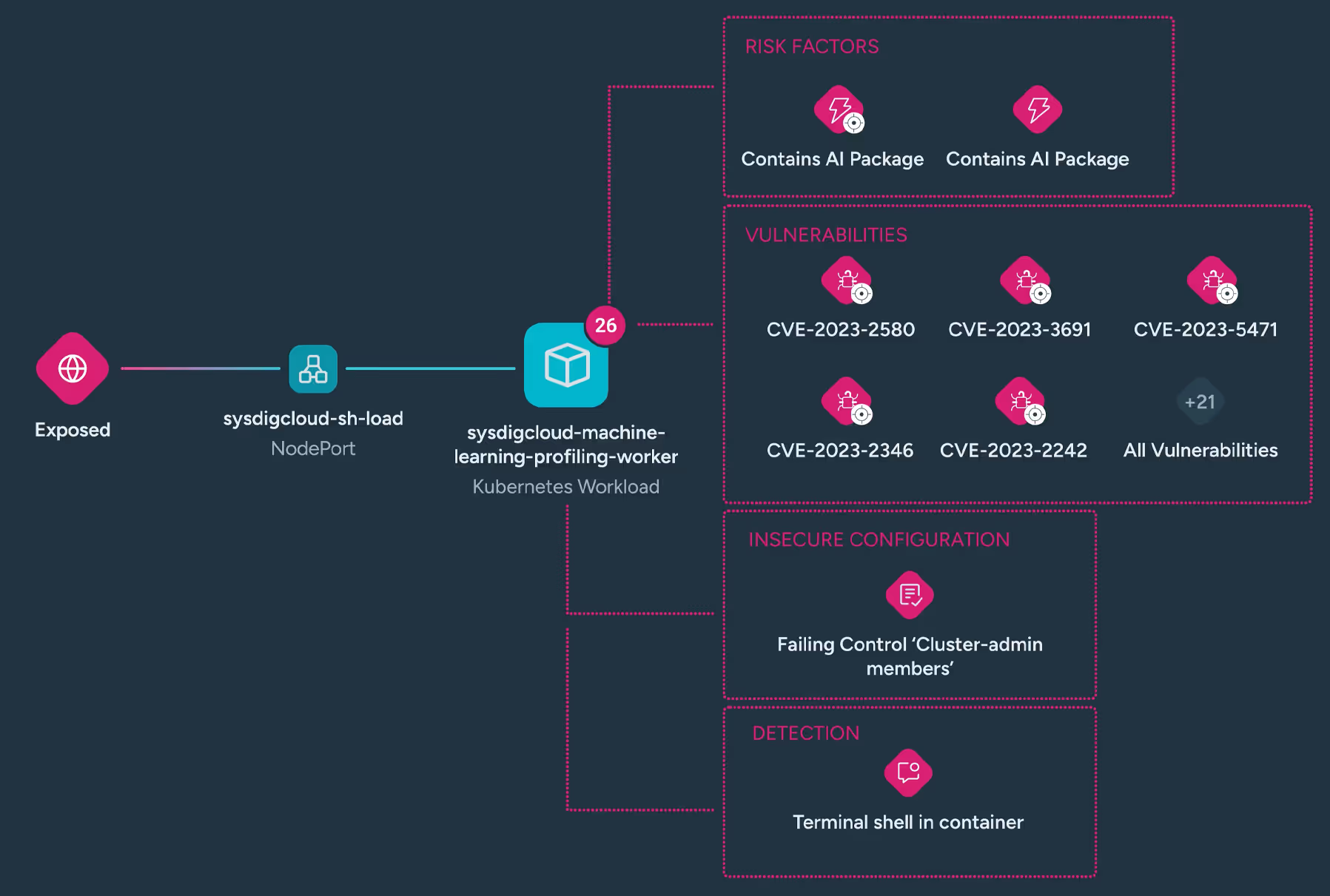
Enriches static risks, such as public exposure and misconfigurations, by incorporating real-time threats and suspicious activities — like shell access or remote file copying — allowing you to prioritize the most urgent risks to your AI workloads and data.
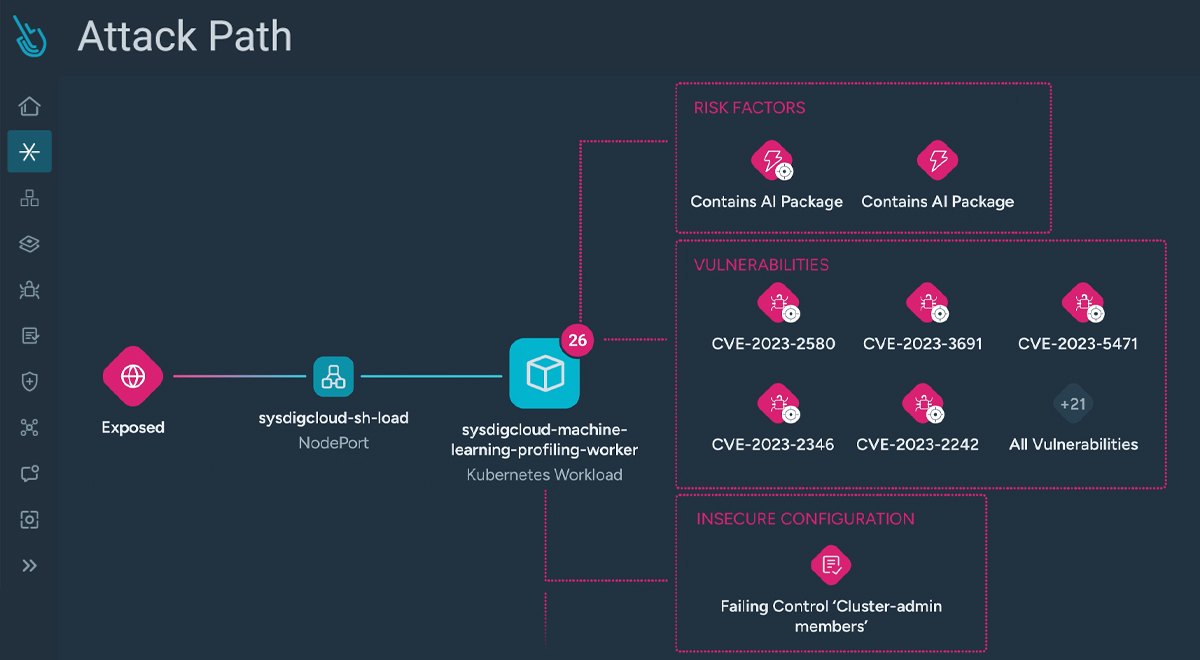
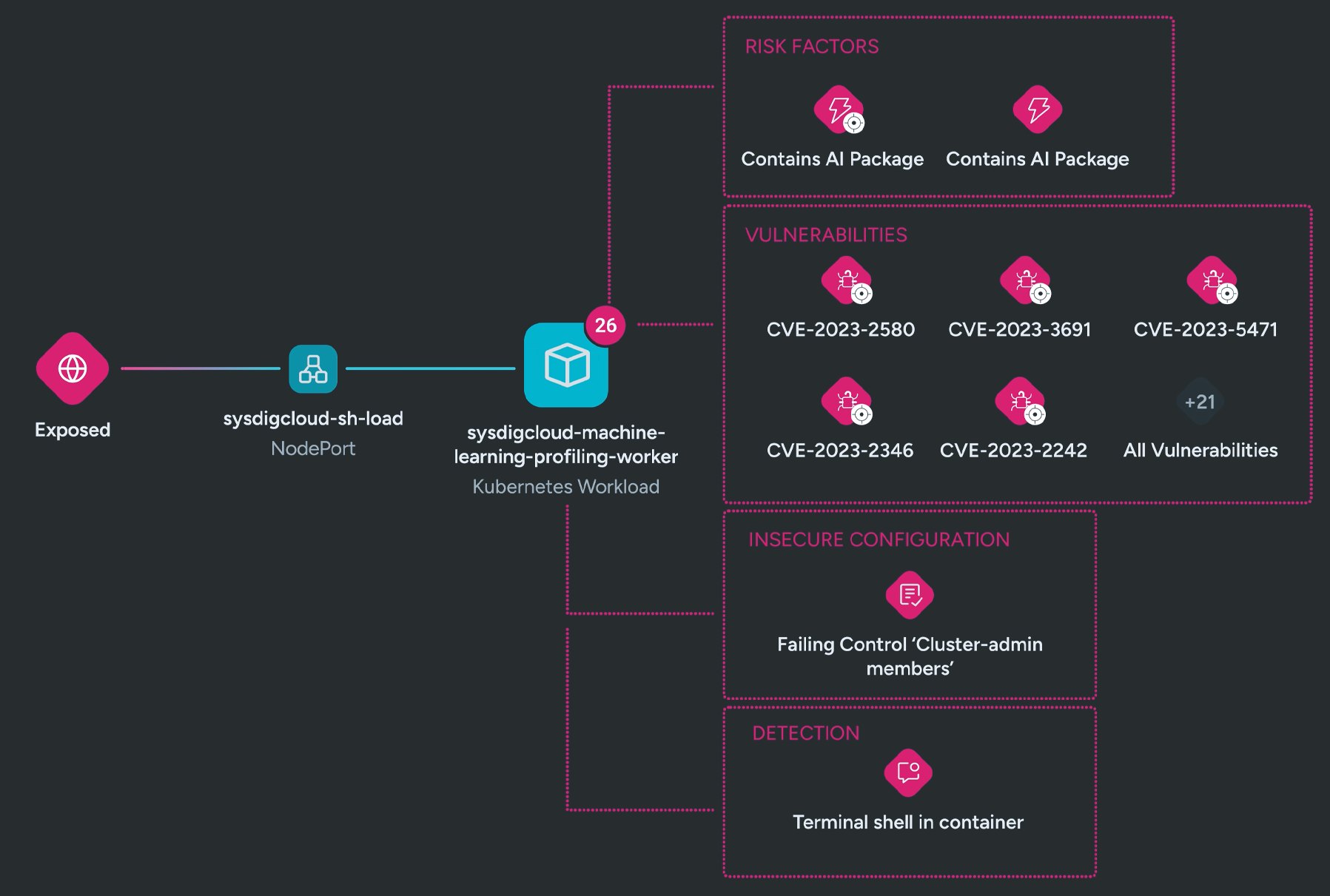
Attack path analysis
Uncovers hidden attack paths by correlating AI assets with activity, visualizing risks across interconnected resources. With runtime insights and real-time detections, it identifies active lateral movement, so you can stop attackers in their tracks.
Runtime vulnerability exposure
Prioritizes critical vulnerabilities in your AI deployments by leveraging runtime insights to identify the highest-risk AI packages in use, ensuring the most critical vulnerabilities are addressed first.