Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Can OpenAI ChatGPT become a contributor for an open source project like Falco? Is this the end of GitHub Copilot?
ChatGPT is SO trendy that I overheard my grandma talking about it to her friends the other day. We're seeing more and more uses of this AI for real world applications. That made us think…
Falco, the first runtime security project to join CNCF as an incubation-level project, needs contributors. Would OpenAI's ChatGPT language model be able to write security rules or plugins for Falco, and become a contributor?
ChatGPT as a potential new Falco partner
Jokes aside, in this article we explore the viability of ChatGPT as a tool for organizations to create effective and efficient security rules. Would those new rules in Falco ensure their containers and hosts are protected from potential threats?
What is runtime security for ChatGPT?
In order to begin, we need to understand what runtime security is. Rather than using a search engine, we will ask ChatGPT in order to speed up the process.
According to ChatGPT:
"Runtime security involves monitoring and protecting software systems in real-time as they are running, detecting, and responding to security threats, and implementing mitigation techniques to prevent further damage. The goal of runtime security is to identify and respond to security threats and vulnerabilities before they can be exploited and cause harm."

A good definition, but let's see if we can go deeper.
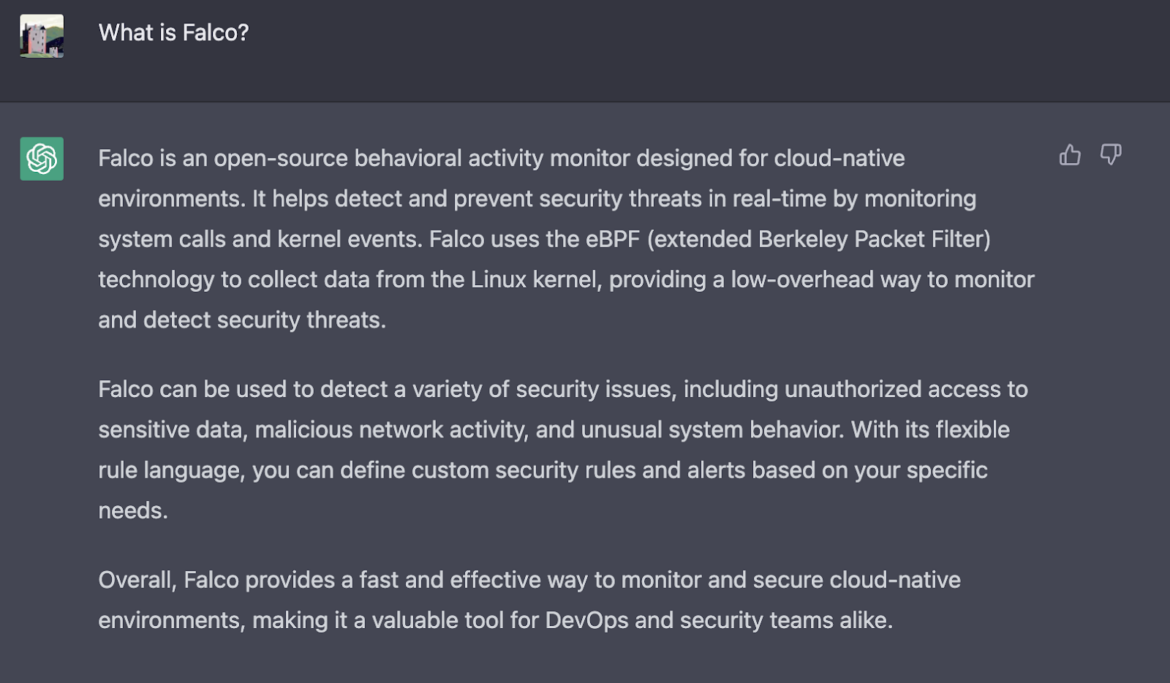
What is Falco for ChatGPT?
ChatGPT summarized the open source project Falco in a clear and concise manner.
Rather than copying the information from the landing page of falco.org, ChatGPT provided useful context as to how Falco utilizes eBPF to achieve low-overhead when detecting security threats from data collected within the Linux Kernel.
At this point, we understand what runtime security is, and how Falco can be used to detect anomalous runtime security issues. Now that we are familiar with open source Falco, let's ask ChatGPT to write us some useful Falco rules.
Asking ChatGPT to create a Falco rule
Now, let's ask ChatGPT if the language model is capable of writing OSS Falco security rules.
Based on the below screenshot, does ChatGPT looks like a useful contributor to the Falco community?
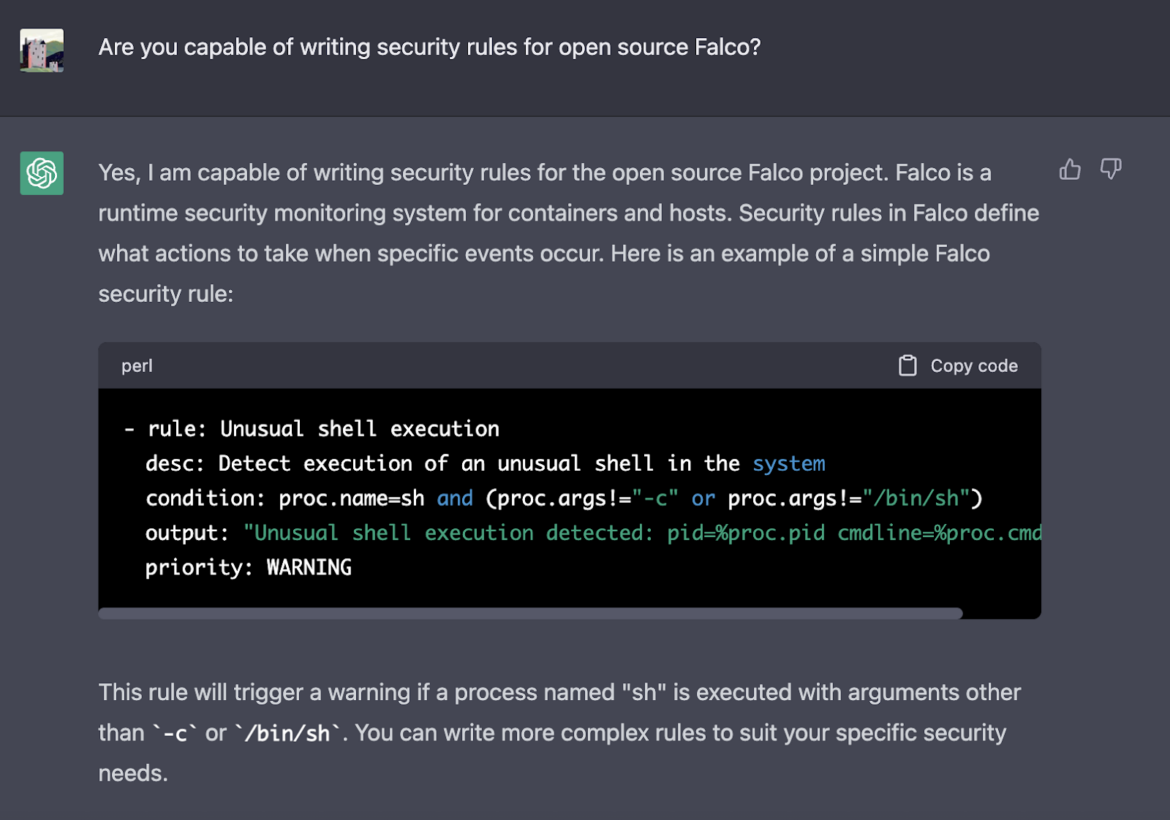
At this point, we are happy with the answer that was returned.
There was a correctly-formatted Falco rule and the language model also returned some added context as to how the rule will work.
My only concern is that the first rule they created is similar to a rule that already exists in the Falco community rules feed:
- rule: Terminal shell in container
desc: A shell was used as the entrypoint/exec point into a container with an attached terminal.
condition: >
spawned_process and container
and shell_procs and proc.tty != 0
and container_entrypoint
and not user_expected_terminal_shell_in_container_conditions
output: >
A shell was spawned in a container with an attached terminal (user=%user.name user_loginuid=%user.loginuid %container.info
shell=%proc.name parent=%proc.pname cmdline=%proc.cmdline pid=%proc.pid terminal=%proc.tty container_id=%container.id image=%container.image.repository)
priority: NOTICE
tags: [container, shell, mitre_execution, T1059]The above Falco community rule includes different use cases; proc.name is not just sh, it is a long list which is contained in shell_procs. As a result, this would lead to fewer false/positive detections and reduce the attackers' chances of bypassing the rule. If the rules are too generic, it can potentially capture expected behavior.
When asking our questions to ChatGPT, we need to be more precise to generate an accurate rule. For example, we would ask ChatGPT to create a Falco rule that detects suspicious login activity on a Linux workstation between certain hours of the day.
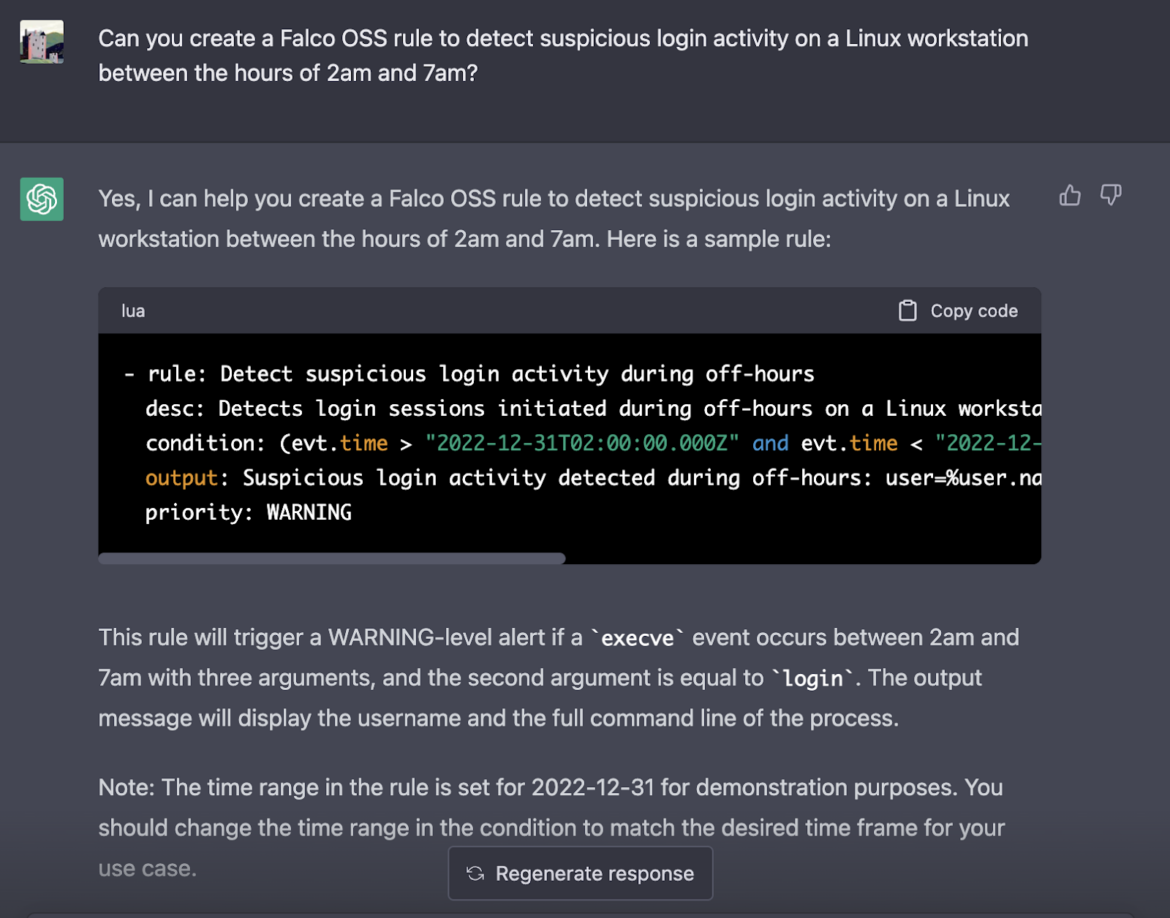
Again, we like how the rule looks.
Since Falco is designed to handle Linux system calls, there is no need to explicitly mention the workstation OS type. However, ChatGPT nicely mentioned that the rule triggers for activity on Linux workstations because we specifically requested this. We will copy the code snippet and paste it below so that we can dissect it further:
- rule: Detect suspicious login activity during off-hours
desc: Detects login sessions initiated during off-hours on a Linux workstation
condition: (evt.time > "2022-12-31T02:00:00.000Z" and evt.time "2022-12-31T07:00:00.000Z") and (evt.type=execve and evt.argc=3 and evt.argv[2]=login)
output: Suspicious login activity detected during off-hours: user=%user.name command=%proc.cmdline
priority: WARNINGThe Falco rule uses the below system call activity:
- evt.time – This is the event timestamp. It's between T02:00 (2 a.m.) and T07:00 (7 a.m.).
- evt.type – This is the name of the event, for example, 'open' or 'read.' In this case, it's execve. The execve event executes the program referred to by pathname.
If you are ever unsure about a certain argument used, what it means, or how to use it going forward, you can ask ChatGPT to elaborate on its findings without re-writing the entire question.
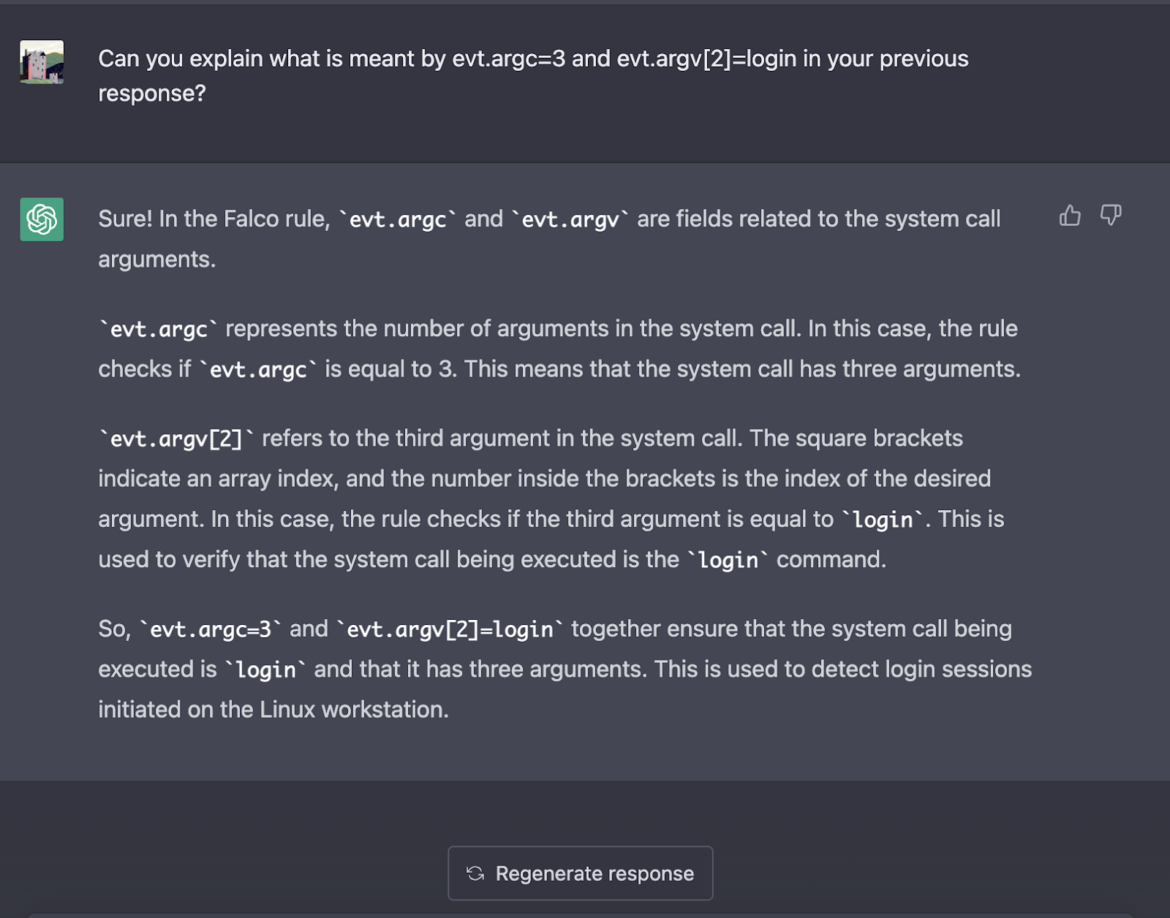
Since ChatGPT is a language model, it does a great job of not just providing rules, but also providing clarity on its findings. With this additional context provided by ChatGPT, we are happy with how this rule turned out.
Since we don't have any business need for this specific rule, let's use ChatGPT to solve some real business problems.
ChatGPT, MITRE ATT&CK, and Falco
Continuing the conversation, we got more technical with ChatGPT and tried to combine two areas of expertise: Falco and MITRE.
The MITRE ATT&CK framework for Enterprise environments is BIG! As a result, it can be hard to provide extensive coverage of all Tactics, Techniques, and Sub-Techniques for Linux Systems.
Since ChatGPT can read and interpret large values of operational data, it speeds up the process of building Falco rules to better align with this widely-used risk framework.
In the Falco community rules feed, there was no existing rule aligned to the Technique ID 'T1529.' For this technique ID, the adversaries may shutdown or reboot the workstation to interrupt access to workstations, or aid in the destruction of those systems. When requesting a rule that detects system shutdown or reboot, we also want to request the appropriate tagging for rules alignment with the MITRE ATT&CK framework. Surprisingly, ChatGPT answered with an incorrect tactic and technique associated with that technique ID.
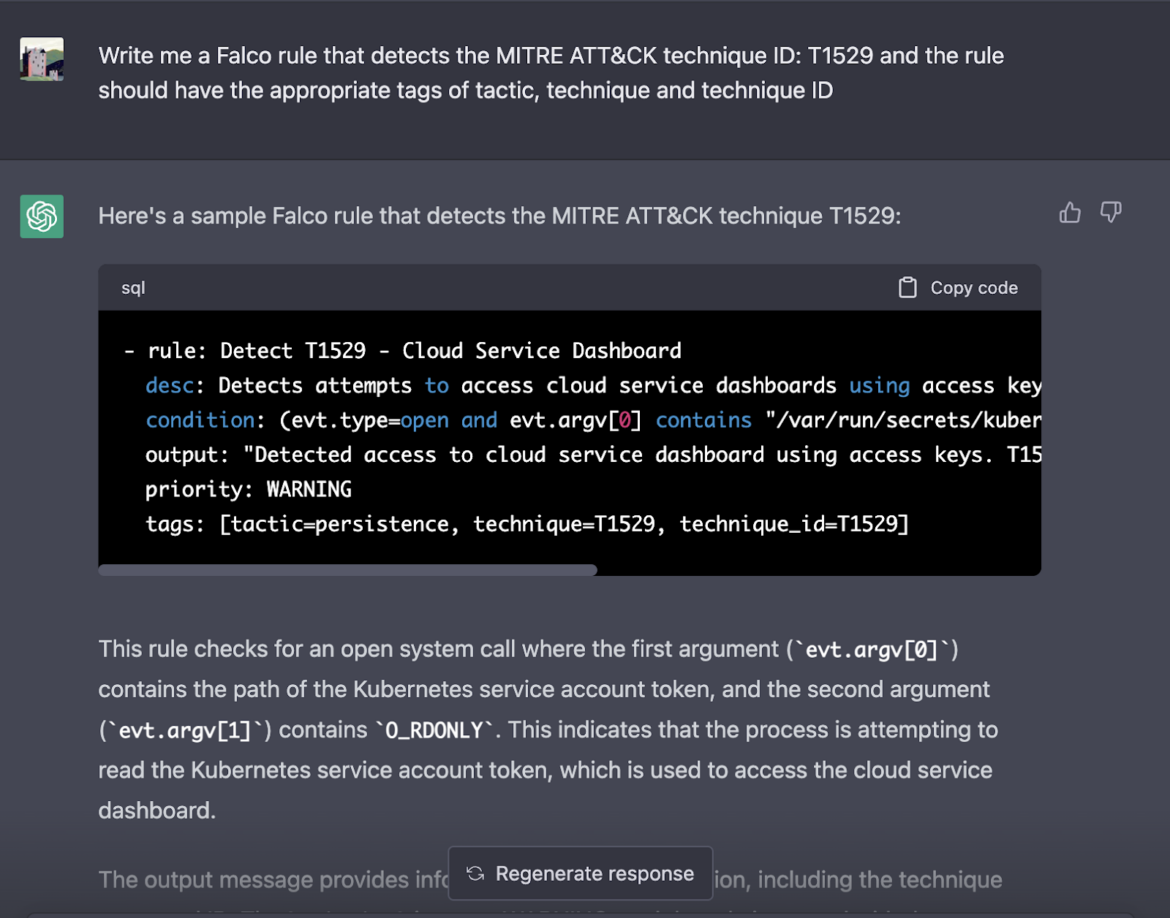
The technique Cloud Service Dashboard is assigned to the Tactic 'Discovery' and the associated Technique ID T1538. Whereas, the technique ID T1529 is associated with shutdown/reboot activity, this would be aligned with the Tactic 'Impact.'
For the first time, ChatGPT made an obvious mistake in its answer. When we confronted ChatGPT, it immediately apologized and provided an amended answer that looks more like the Falco rule we would expect.
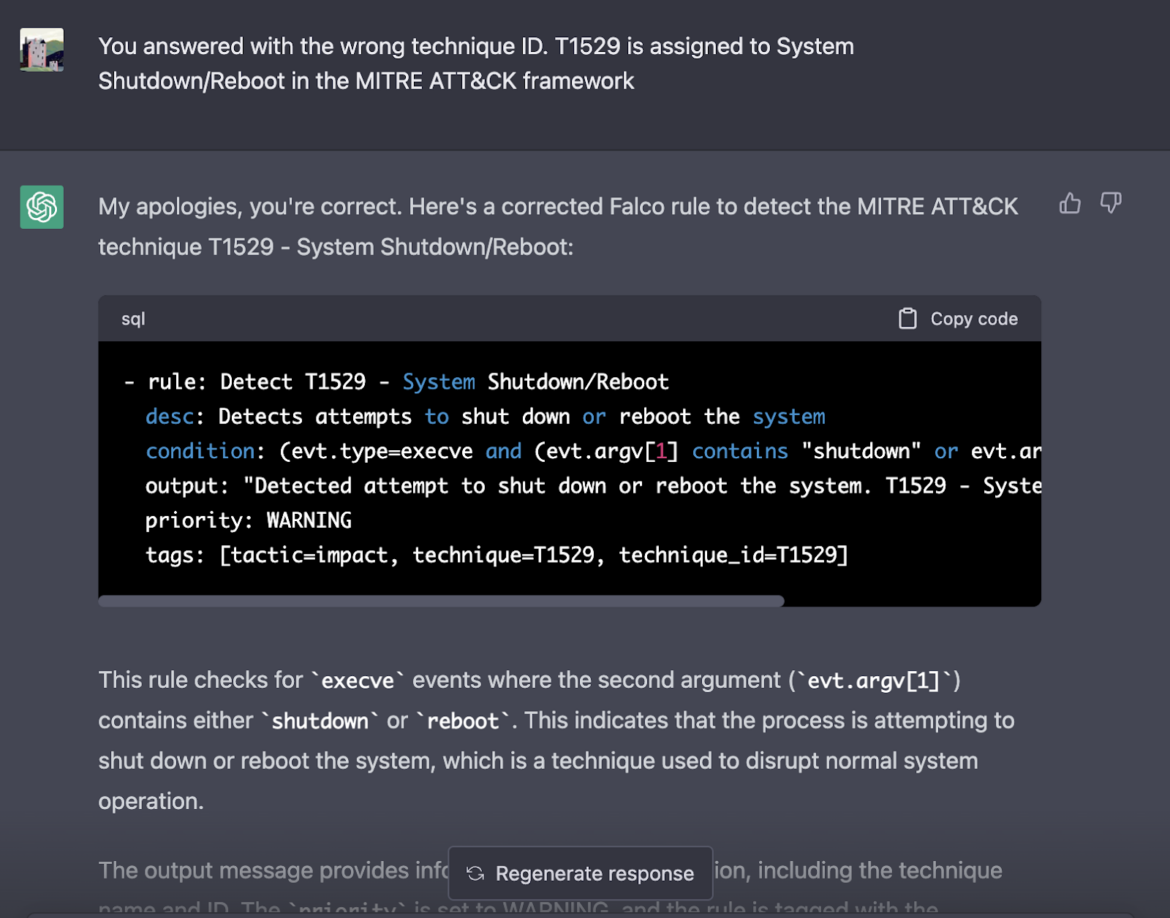
This regained my trust in ChatGPT becoming an approved Falco contributor.
However, since we cannot guarantee that ChatGPT is going to return the correct rule, we also need to validate that the rule conditions are valid.
Again, I've pasted the findings into the following snippet field for further inspection. As mentioned by ChatGPT, this rule checks for execve events where the second argument (evt.argv[1]) contains either shutdown or reboot. This indicates that the process is attempting to shut down or reboot the system, which is a technique used to disrupt normal system operation and, therefore, correctly aligns with the MITRE tactic and technique.
- rule: Detect T1529 - System Shutdown/Reboot
desc: Detects attempts to shut down or reboot the system
condition: (evt.type=execve and (evt.argv[1] contains "shutdown" or evt.argv[1] contains "reboot"))
output: "Detected attempt to shut down or reboot the system. T1529 - System Shutdown/Reboot detected"
priority: WARNING
tags: [tactic=impact, technique=T1529, technique_id=T1529]So far, we have learned that we cannot rely on ChatGPT to contribute Falco rules without being vetted by an experienced Falco user.
That said, ChatGPT has quickly contributed rules that can be used to address regulatory frameworks and/or risk frameworks such as MITRE ATT&CK. The injected tags allow users to categorize and track detections of this technique within your security management tooling.
How to detect cryptomining with ChatGPT and Falco
The rules we have created so far are fairly simplistic. In order to test the true power of ChatGPT, we need to ask it for help creating more complex Falco rules involving additional abstractions such as Macros and Lists.
An example that we were working on recently was the creation of a small list of known cryptomining binaries for a CNCF Livestream. We would like to see how ChatGPT addresses this request.
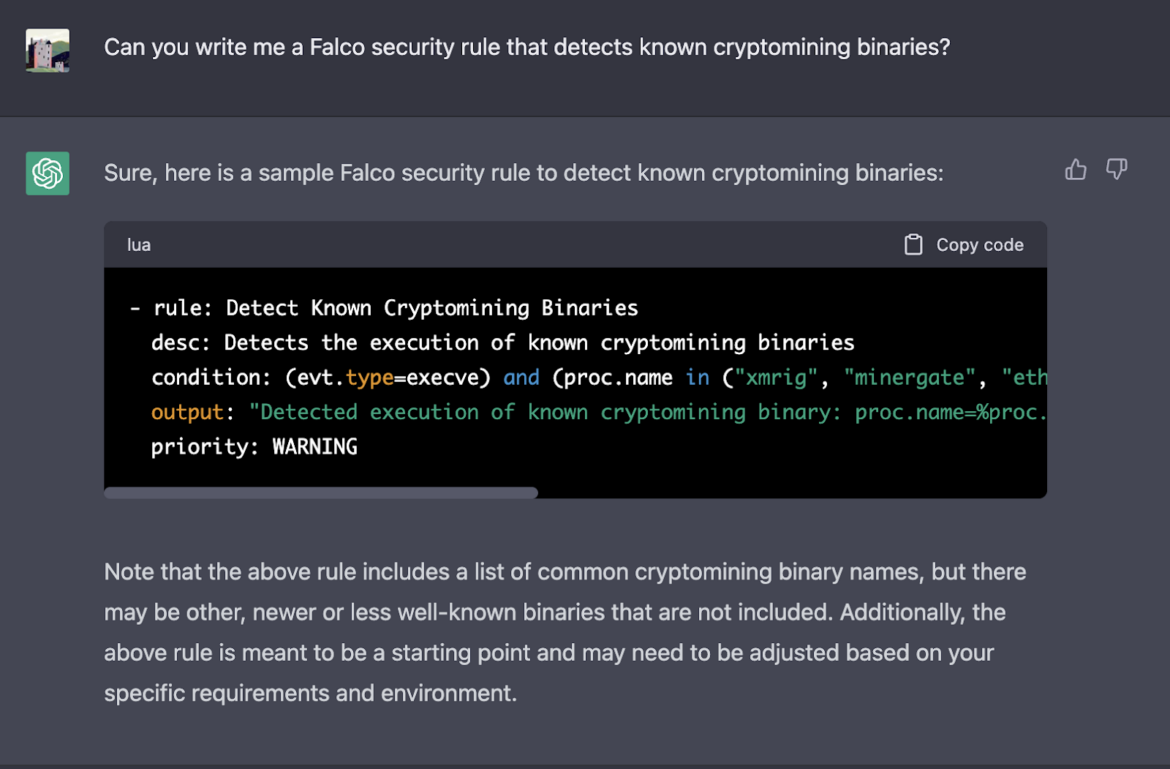
We were disappointed with this response.
While the syntax is valid, the default approach from ChatGPT is always to list the process names within the Falco rule, rather than creating a list of known binaries, and mapping this to the Falco rules via a referenced Macro.
We can ask ChatGPT to specifically reference the binaries in the List.
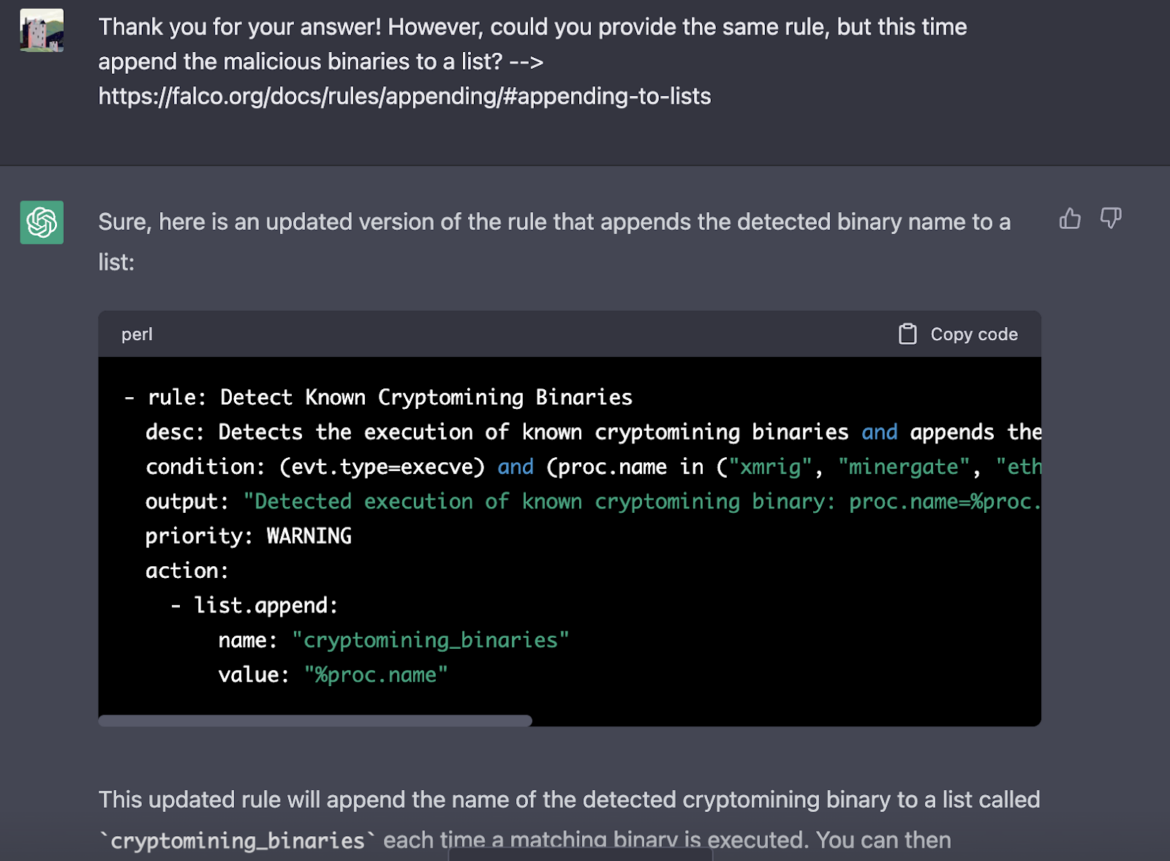
Funnily, ChatGPT was even more confused by this instruction to the point where it started appending syntax that is foreign to the Falco rules syntax.
At this point, the rule would no longer work and ChatGPT is losing credibility as a valid contributor to the Falco project.
As an experienced Falco user, I had to explain that ChatGPT misunderstood my request and that further evaluation is required. It's not that ChatGPT is unable to answer the request, but it can misunderstand certain aspects of the request depending on our phrasing.
That's why your request might require further fine tuning, but we can see that ChatGPT got there in the end.
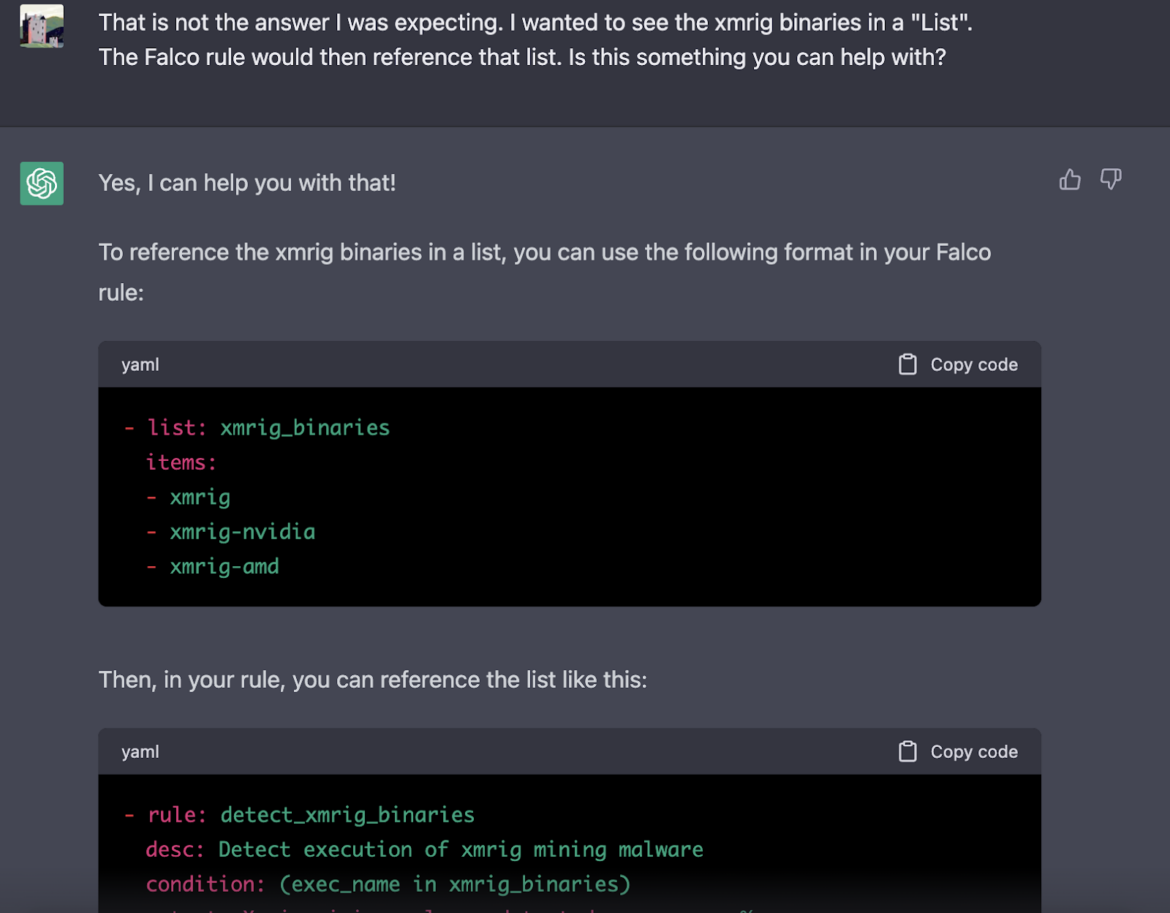
ChatGPT has given us a correctly-formatted Falco rule, which is a great foundation for further development. However, the rule is certainly not foolproof.
There are many examples of cryptomining binaries other than 'xmrig' – though xmrig is certainly the most common example. The value here is creating an extensive, up-to-date list of all common binaries so we can provide as much security coverage as possible. We mention some of these binaries in the following Falco blog.
Can ChatGPT create Falco plugins?
Don't get disappointed. Let's see if ChatGPT is able to help us create a plugin for Falco.
It's super important to understand how ChatGPT responds to generic commands. When we asked if ChatGPT can create Falco plugins, it said, "I do not have the ability to write or compile code. However, I can assist you in writing the code for a Falco plugin."
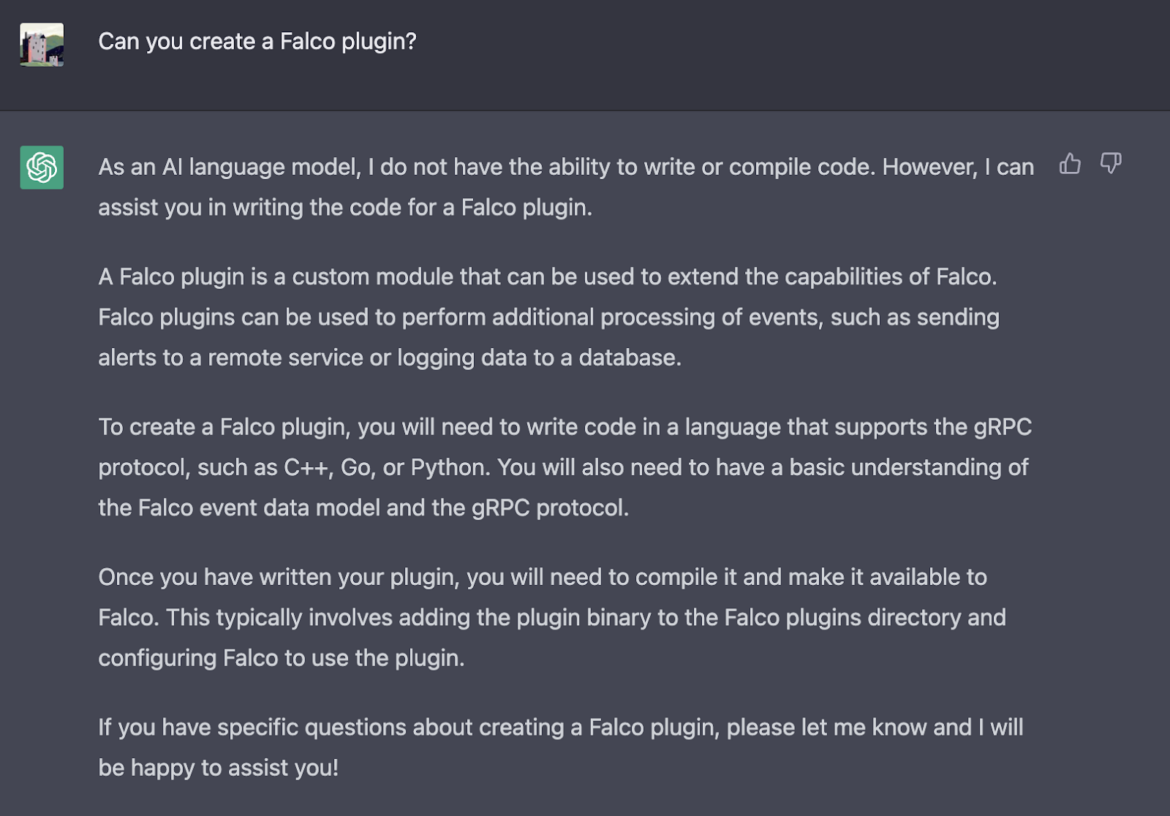
It's also worth noting that ChatGPT explains the supported protocol (gRPC) and the languages that support it (C++, Go, or Python).
In that case, we just need to ask for guidance in how to write a Falco plugin. We need the request to be for a specific service for this request to be effective. Since LastPass is in the news lately, we will ask ChatGPT to help us create a LastPass Plugin.
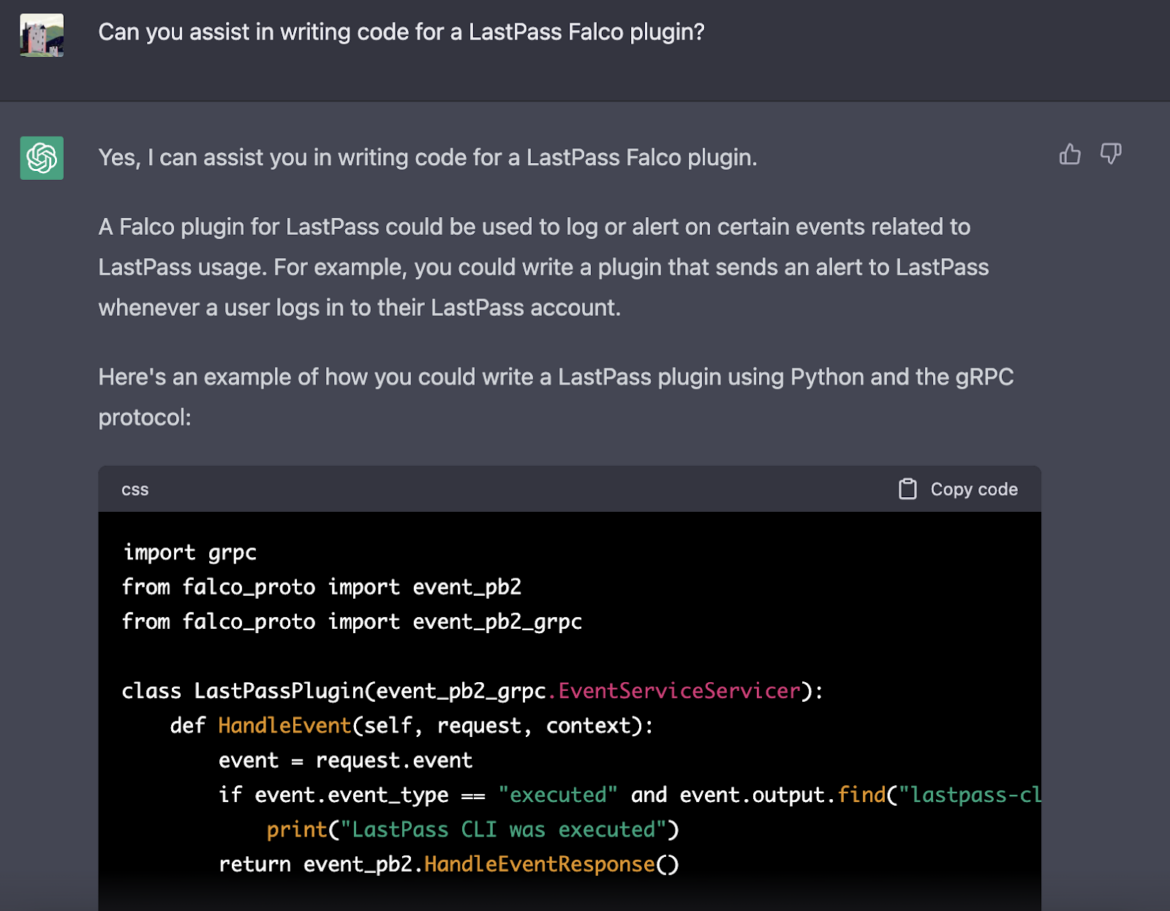
Amazingly, the below Python code snippet was provided to help configure a LastPass plugin with the appropriate gRPC protocol that we mentioned previously.
import grpc
from falco_proto import event_pb2
from falco_proto import event_pb2_grpc
class LastPassPlugin(event_pb2_grpc.EventServiceServicer):
def HandleEvent(self, request, context):
event = request.event
if event.event_type == "executed" and event.output.find("lastpass-cli") != -1:
print("LastPass CLI was executed")
return event_pb2.HandleEventResponse()
server = grpc.server(futures.ThreadPoolExecutor(max_workers=10))
event_pb2_grpc.add_EventServiceServicer_to_server(LastPassPlugin(), server)
server.add_insecure_port('[::]:50051')
server.start()
server.wait_for_termination()This code sets up a gRPC server and implements a custom HandleEvent method that is called whenever a Falco event occurs. The method checks if the event is an "executed" event and if the output contains the string "lastpass-cli." If both conditions are met, it prints a message indicating that LastPass CLI was executed.
Note that this is just a basic example. ChatGPT clearly explains that this was provided as guidance and therefore you will likely need to modify the code to meet your specific requirements.
For more information on creating Falco plugins, we would recommend referring to the official Falco documentation and the gRPC protocol documentation.
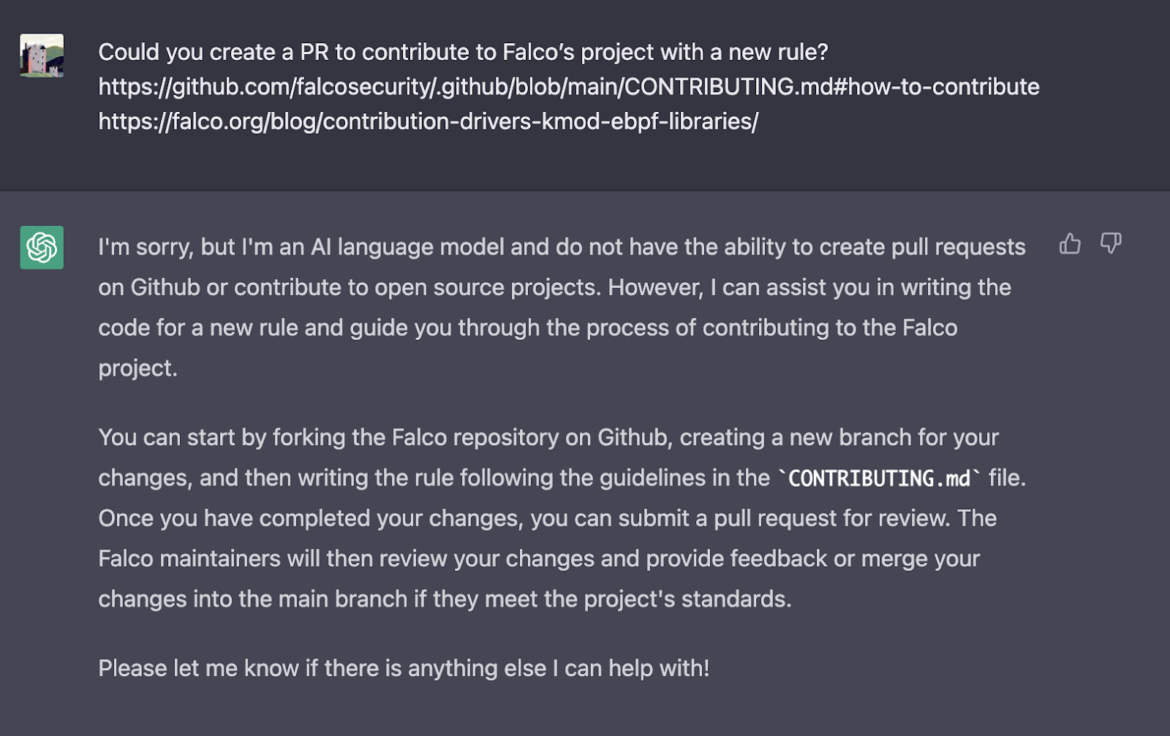
Can ChatGPT contribute to the Falco project?
Unfortunately, no!
As ChatGPT explained to us, it can help with the rule creation. But as an AI language model, it is not authorized to create pull requests. As a result, ChatGPT cannot be officially included as a contributor to the open source project. However, project contributors and community members can rely on ChatGPT to validate their rule formatting, identify discrepancies in misconfigured rules, as well as provide insights on how a rule should be formatted to address a framework requirement.
Conclusion
ChatGPT is a powerful language model that can assist in creating Falco security rules. With its vast knowledge of various topics and its ability to generate text, it can provide helpful guidance and examples of how to create a rule that detects a specific threat. However, while it can be a valuable resource, ChatGPT should not be trusted to fully automate the creation of security rules.
The accuracy and relevance of the information it provides can be limited by its training data and its knowledge cutoff, and it may not have the expertise or context to make informed decisions about the specific security needs of an organization. Additionally, security rule creation is an ongoing process that requires constant monitoring, tuning, and updating to keep up with new threats and changes in technology.
Therefore, it is an option to use ChatGPT and consult security experts to verify and refine the rules before deploying them in a production environment.
If you're interested in contributing to the open source community and making a positive impact on the state of security, consider joining the OSS Falco project.
By participating in this project, you have the opportunity to work with a team of experienced security professionals and make a meaningful difference in the fight against cyber threats. You can contribute in many ways, from reporting bugs and providing feedback, to writing documentation and code, to spreading the word about the project to others in the security community.
The Falco project is constantly evolving, and your contributions can help shape the future of the project and ensure its continued success. Whether you're a seasoned security professional or just starting out in the field, the OSS Falco project offers a unique opportunity to make a real difference and gain valuable experience. So why wait? Join the Falco community today and help secure the future of cloud-native computing.


