
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

A new zero day vulnerability actively exploited in the wild has been found in Atlassian Confluence. The vulnerability CVE-2022-26134 affects all supported versions of Confluence Server and Confluence Data Center allowing an unauthenticated user to run arbitrary commands remotely.
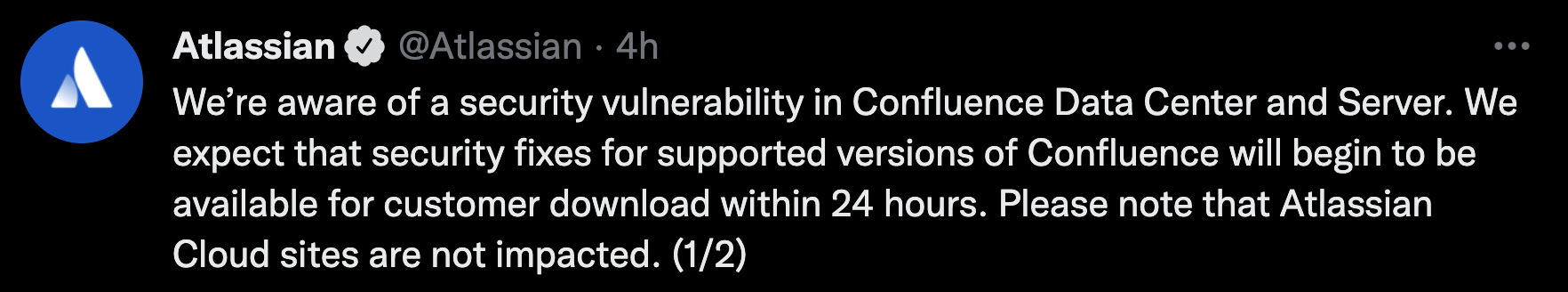
The Atlassian team confirmed the vulnerability with an official tweet and then also published a security advisory to update its customers.
It is still not clear which are the earliest affected versions of Confluence Server and Confluence Data Center. What is known is that the vulnerability is already being exploited by attackers.
UPDATE: Released versions 7.4.17, 7.13.7, 7.14.3, 7.15.2, 7.16.4, 7.17.4 and 7.18.1 which contain a fix for this issue.
We strongly recommend upgrading to a fixed version of Confluence.
Rapid7 has reported about how the exploit actually works. It is very simple and just requires a string such as ${@java.lang.Runtime@getRuntime().exec("whoami)} to be placed in the URI string.
In this article, we are going to cover what we currently know about vulnerability CVE-2022-26134, why it is so dangerous, and how to detect it with Falco rules.
What is Atlassian Confluence?
Confluence is a very popular wiki tool that simplifies team collaboration and knowledge sharing.
In August 2021, Atlassian disclosed the vulnerability CVE-2021-26084 that could enable a threat actor to run arbitrary code on unpatched Confluence Server and Data Center instances.
Almost one year later, during the Memorial Day weekend in the United States, Volexity discovered a new vulnerability in Confluence. It was found after suspicious activity was detected during a Volexity incident investigation, evidence was seen that indicated a new vulnerability is being exploited in the wild.
In this case, CVE-2022-26134 is a critical vulnerability allowing remote code execution by unauthenticated users. Atlassian recommends that you upgrade to the latest Long Term Support release. It has been suggested by Volexity that multiple threat actors are currently leveraging this exploit.
The impact of CVE-2022-26134
The impact of the vulnerability CVE-2022-26134 is widespread due to the fact that it affects all the supported Confluence Server and Data Center.
Atlassian Cloud sites are not affected by this vulnerability.
Exploiting this vulnerability allows remote command execution on the impacted systems for unauthenticated users. It means that attackers can run arbitrary commands and gain full control of an affected Confluence environment without any authentication.
In a nutshell, as long as any impacted Confluence Server or Data Center instance is reachable on the network it can be exploited by malicious actors. For this reason, this vulnerability is considered critical. However, at the time of this writing, a CVSS score has not yet been assigned to the CVE.
No exploits have been publicly disclosed yet. The complexity or details of the exploit are not known yet which makes prevention and detection difficult.
Detecting CVE-2022-26134
The Volexity blog post reported the attack found in their customers' hosts.
What can immediately sound suspicious from the scenario they reported is that the execution dumped from the hosts memory belonged to a strange process tree. Something like this:
|java
|----bash
|--------python
|------------bash
And so a bash process, spawned by a python one, whose father was another bash one and then the java root process name. Such a kind of execution can be easily detected with Falco.
Falco, a CNCF incubating project, is an open source tool that detects anomalous executions at runtime in your cloud-native environments. In order to detect suspicious runs, like the process tree described before, you can use this Falco rule:
- macro: java_bash_python_bash
condition: proc.name in (shell_binaries) and proc.pname contains "python" and proc.aname[2] in (shell_binaries) and proc.aname[3]=java
- macro: java_python_bash
condition: proc.name in (shell_binaries) and proc.pname contains "python" and proc.aname[2]=java
- rule: Suspicious Java Child Processes
desc: Detect suspicious process trees involving Java that are used to exploit Remote Code Execution
condition: spawned_process and (java_bash_python_bash or java_python_bash)
output: Detecting Suspicious Java Child Processes (command=%proc.cmdline connection=%fd.name user=%user.name user_login uid=%user.loginuid container_id=%container.id image=%container.image.repository)
priority: WARNING
Moreover the Volexity team has also provided the IoCs exploiting or interacting with the Confluence Servers. If you want to trigger alerts if any of these indicators are reached in outbound by your instances, you can fill the c2_server_ip_list list with the reported IP addresses and use the following rule:
- list: c2_server_ip_list
items: []
- rule: Outbound Connection to C2 Servers
desc: Detect outbound connection to command & control servers
condition: outbound and fd.sip in (c2_server_ip_list)
output: Outbound connection to C2 server (command=%proc.cmdline connection=%fd.name user=%user.name user_loginuid=%user.loginuid container_id=%container.id image=%container.image.repository)
priority: WARNING
tags: [network]
These indicators, along with many others, are already provided to Sysdig customers and will be constantly updated as the Sysdig Threat Research Team discovers them.
Mitigating CVE-2022-26134
If you are unable to upgrade Confluence immediately, then as a temporary workaround, you can mitigate the CVE-2022-26134 issue by updating the following files for the specific version of the product.
Atlassian released versions 7.4.17, 7.13.7, 7.14.3, 7.15.2, 7.16.4, 7.17.4 and 7.18.1 which contain a fix for this issue. The security advisory provides full details on how to update your vulnerable Confluence server.
Conclusion
The CVE-2022-26134 is a new critical vulnerability affecting all the supported versions of Confluence Server and Data Center.
It is already being exploited in the wild by malicious actors to run arbitrary executions and to grant full control over the impacted systems. The Atlassian team released versions to fix it, to prevent any exposure of the impacted instances the suggestion is to update as soon as possible or disable them or reduce their access from the internet.
Instead, if you are unable to take these actions, you can adopt Falco to detect possible intrusions.
After that, if you would like to find out more about Falco:
- Get started at Falco.org.
- Check out the Falco project on GitHub.
- Get involved with the Falco community.
- Meet the maintainers on the Falco Slack.
- Follow @falco_org on Twitter.


