Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

What happened?
- Vulnerabilities in CUPS (Common Unix Printing System) allow remote attackers to add a fake printer and execute arbitrary commands when a print job is processed
- Although the commands run under the 'lp' user with limited privileges, this still poses a risk due to the possibility of privilege escalations and misconfigurations
- The attack specifically targets CUPS through the "cups-browsed" process listening on UDP port 631
On September 26th, 2024, details were released about several vulnerabilities in the Common Unix Printing System (CUPS) package. A total of four CVE's (CVE-2024-47176, CVE-2024-47076, CVE-2024-47175, and CVE-2024-47177) have been released, affecting many Unix and Linux distributions. Three of the vulnerabilities are rated High, while one is rated Critical. If left unpatched, a remote attacker is able to execute arbitrary commands on the affected system.
Below we analyze the potential impact of the four used together, how to detect them with Falco, and mitigation steps you can take.
How Do I Know If I'm Affected?
To manually determine if your system is affected:
Check if the CUPS service is enabled (for systemctl-based systems):
sudo systemctl status cups-browsedCheck if port 631 (both UDP and TCP) is open:
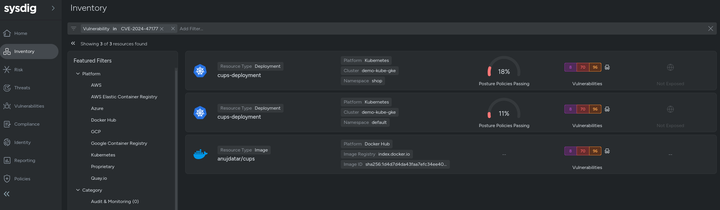
sudo ss -lntup | grep 631Alternatively, Sysdig's Vulnerability Management can already identify these vulnerabilities. Simply use the Inventory feature to search for the relevant vulnerability IDs and quickly assess your exposure.
Vendors, such as Ubuntu and RedHat, have already released patches for their distributions which will allow the vulnerability management process to quickly start.
Sysdig Secure Inventory View:
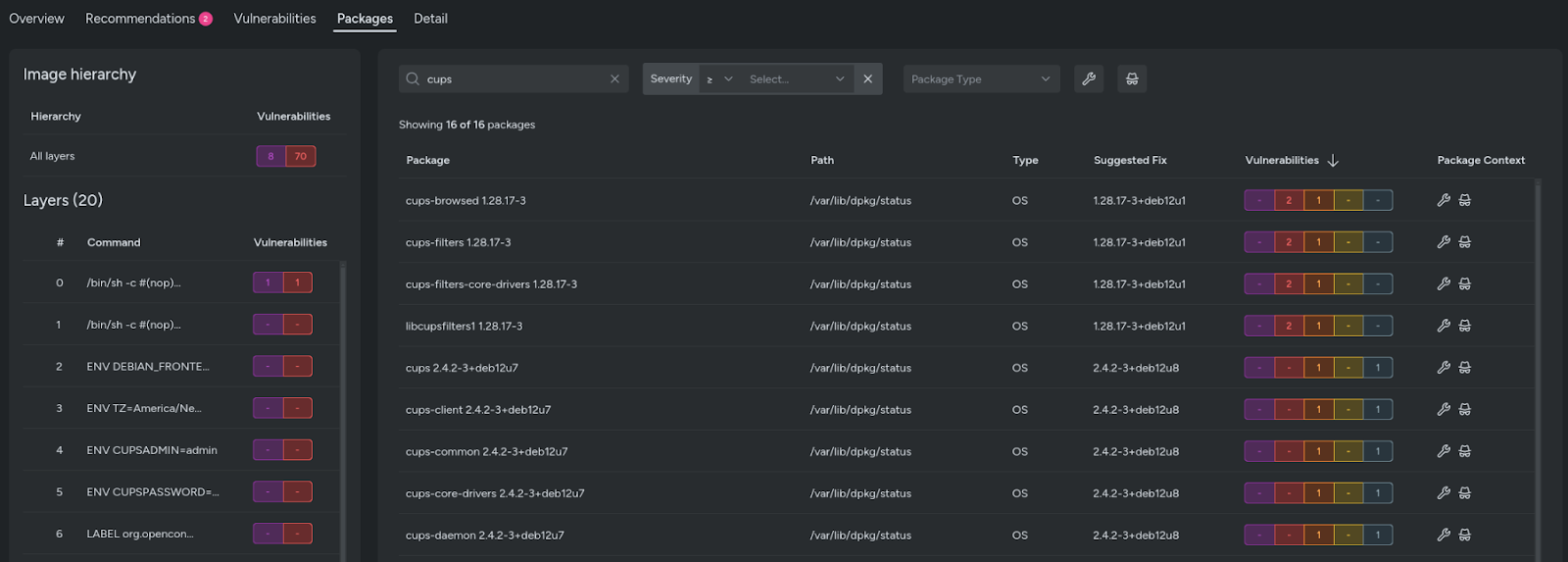
Sysdig Secure Vulnerability management:
Analysis
The process being exploited here is "cups-browsed", which is used for printer discovery and accessibility. By default, it is listed on UDP port 631 and is open to the world. No authentication is required to interact with this service remotely. According to the researcher, a couple hundred thousand systems had this port open to the internet and the "cups-browsed" daemon responded.
The four vulnerabilities involved are used together to achieve remote code exploitation in vulnerable CUPS installs.
- CVE-2024-47176 is in reference to "cups-browsed" having port 631 being open and allowing unauthenticated access.
- CVE-2024-47076 allows the exploit to pass data without any validation or sanitization.
- CVE-2024-47175 allows the exploit to continue further as it is another validation and sanitization issue.
- CVE-2024-47177 allows the execution of the data which has been passed using the previous vulnerabilities using the "foomatic-rip" process.
In practice, this exploit only requires an attacker to send a UDP packet with a URL to a system which the attacker controls. From there, the attacker has a listener waiting and can start the exploit chain once a vulnerable system connects. Finally, they can execute arbitrary commands as the "foomatic-rip" process and continue with their post-exploitation goals.
Detection
This exploit can be detected by looking for the "foomatic-rip" process executing commands, as this isn't normal behavior. Alternatively, if CUPS should not be running in your environment, looking for any process listening on UDP port 631 is an option. Sysdig Secure detects an extensive amount of post-exploitation activities out-of-the box but these rules will provide additional visibility.
Falco can also be used to detect this exploit with the following rules:
The following rule is available automatically to Sysdig Secure customers in the Sysdig Runtime Threat Detection policy.
- rule: Possible Arbitrary Command Execution through CUPS (CVE-2024-47177)
desc: The footmatic-rip process was seen executing common shell programs which may indicate that an attacker has exploited CVE-2024-47177. Ensure that this is expected behavior and CUPS has been patched for this vulnerability.
condition: spawned_process and shell_procs and proc.pname="foomatic-rip"
exceptions:
- name: proc_name_pname
fields: [proc.name, proc.pname]
comps: [in, in]
output: The process %proc.pname was seen executing the shell %proc.name with cmdline %proc.cmdline which may indicate arbitrary command execution through the CUPS vulnerability CVE-2024-47177. (proc.exepath=%proc.exepath proc.cmdline=%proc.cmdline user.name=%user.name image=%container.image.repository:%container.image.tag proc.pcmdline=%proc.pcmdline container.id=%container.id container.name=%container.name)
priority: CRITICAL
tags: [host, container, MITRE]The following rule is available automatically to Sysdig Secure customers in the Sysdig Runtime Notable Events policy.
- rule: Suspicious cups-browsed process listening on UDP (CVE-2024-47176)
desc: The cups-browsed process was seen listening for incoming connections on port 631. This may indicate that it is vulnerable to CVE-2024-47176. Ensure that this is expected behavior and the process has been patched.
condition: evt.type=bind and evt.dir=< and fd.l4proto=udp and fd.port=631 and proc.name="cups-browsed"
exceptions:
- name: proc_name_proc_pname
fields: [proc.name, proc.pname]
comps: [in, in]
output: Process %proc.name is listening on port %fd.cport using the %fd.l4proto protocol which may indicate it is vulnerable to CVE-2024-47176. (proc.name=%proc.name proc.pname=%proc.pname fd.name=%fd.name proc.cmdline=%proc.cmdline proc.pcmdline=%proc.pcmdline container.id=%container.id evt.type=%evt.type evt.res=%evt.res proc.pid=%proc.pid proc.exepath=%proc.exepath container.name=%container.name image=%container.image.repository)
priority: INFO
tags: [host, container, MITRE]Mitigation
There are several options to mitigate this attack, such as disabling the CUPS browser service or blocking port 631 at the firewall.
Disable the CUPS Browsed Service:
sudo systemctl stop cups-browsed
sudo systemctl disable cups-browsed
sudo systemctl restart cups
Block Access to UDP Port 631:
Update your firewall settings to block access to UDP port 631:
sudo ufw deny proto udp from any to any port 631For more tactical mitigations, services can be shut down and firewall rules can be used to prevent access to the vulnerable services. Latio Tech has a number of additional suggestions for how to implement these mitigations.
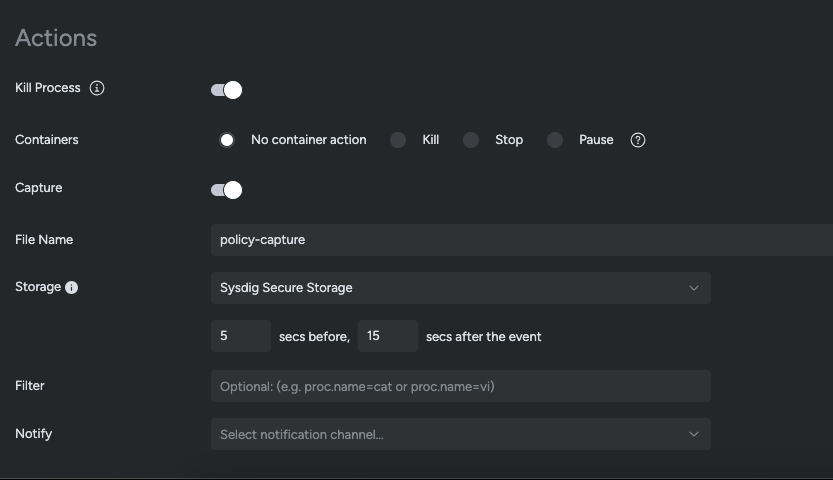
If you are a Sysdig Secure customer, the platform offers several options for how to respond if one of the above rules is triggered. "Kill Process" can be used to terminate the shell that the attacker launches. Or for a more complete response in a containerized environment, "Kill Container" can be used to eliminate the entire workload. For deep forensic review, a syscall capture can be taken automatically.
Prevention
If you are a Sysdig Secure customer, we have already implemented policies to help you stay ahead of this misconfiguration. Specifically, our Cloud Security Posture Management (CSPM) solution includes a control called "Print server disabled in all runlevels." This control is designed to detect if the Common UNIX Printing System (CUPS) service is improperly configured and running at any runlevel, which could expose your systems to potential attacks. By proactively identifying this vulnerability, Sysdig enables you to quickly remediate the misconfiguration, hardening your Linux environments against exploitation.
Conclusion
While CUPS isn't likely to be used within a cloud environment, it does come enabled from certain vendors and may be active without the team's knowledge. Having a robust vulnerability management system that includes an inventory will enable visibility to discover these vulnerable software packages. In order to protect your systems while rolling out patches, real-time threat detection and response will enable you to react to any incidents and automatically respond to them.


