
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

On April 3, 2025, the National Security Agency and other partner agencies released a critical advisory about DNS and Fast Flux. They even called it a national security threat due to the potential dangers involved. In this article, we’ll go over what Fast Flux is and how Sysdig Secure detects this attack technique. We’ll also cover gathering potential Fast Flux domain names from VirusTotal.
What is Fast Flux?
Fast Flux is the rapid shuffling of the IP address that a domain name resolves to obfuscate the attacker’s infrastructure. DNS records have a configurable Time To Live (TTL) value, which tells servers how long they should cache the corresponding IP address. The default TTL can vary, but it is commonly between 1-24 hours.
When employing the Fast Flux technique, the TTL value is set to be much shorter. The TTL is typically set to 5 minutes or less (or seconds in some cases). This short timeframe allows the attacker to continuously change the IP Address of their Command and Control (C2) infrastructure.
Why attackers use Fast Flux
There are several advantages to using the Fast Flux technique for attackers.
- IP Blocklists become ineffective if you can continuously change the IP address of the C2 server while the malware uses a domain name to determine its location.
- Fast Flux makes it difficult for the host server to be taken down by authorities and providers. The new IP address could be in different networks and countries. By the time it is investigated, it may have already moved.
- It improves the reliability and resiliency of the attackers’ C2 infrastructure, ensuring that the malicious domain either serving phishing or malware content can rapidly be back up in seconds Threat actors also commonly use DDoS attacks against each other. By shifting their server’s IP address around, they can help mitigate this risk.
Detecting Fast Flux with Sysdig Secure
Sysdig Secure can detect malicious programs communicating Fast Flux servers at runtime. Using advanced DNS inspection, domains with low TTLs and resolving to multiple IP addresses will trigger the DNS Fast Flux Activity Detected event in the Sysdig Runtime Notable Events managed policy. Sysdig Secure has had this detection since October of 2024.
In the example below, the malicious domain has a TTL of 58 seconds.
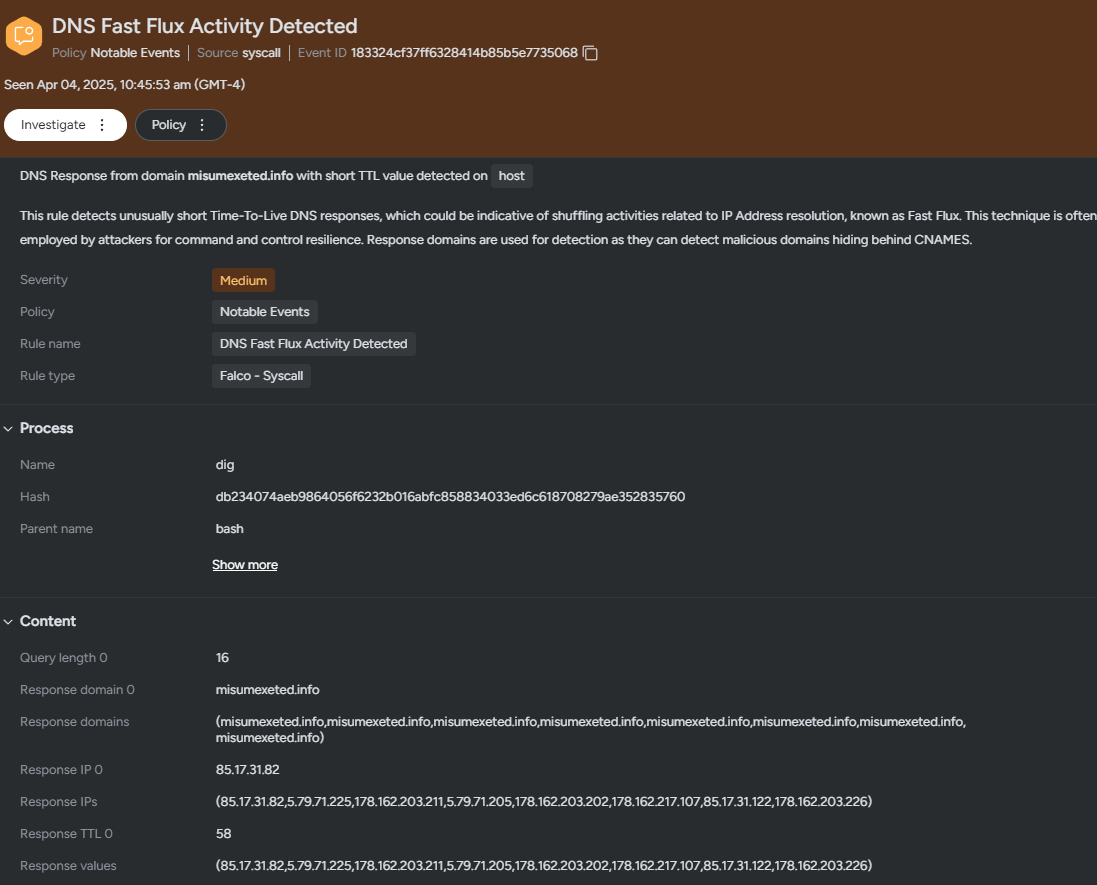
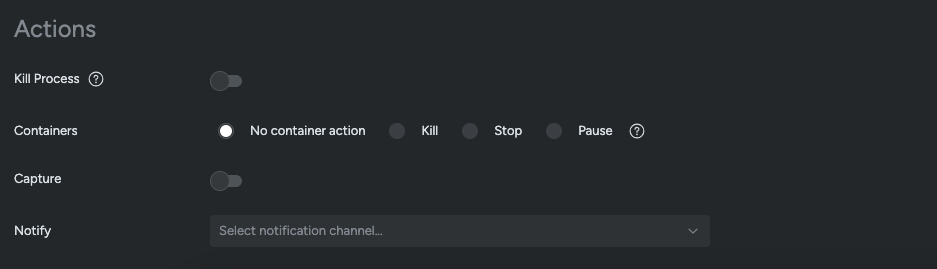
Sysdig Secure supports multiple response actions, such as killing the process seen communicating with a Fast Flux server. This option should be used with care, as false positives may interrupt normal functionality. Fast Flux detection can be challenging due to legitimate servers also using DNS records with a low TTL value. For these servers and programs, exceptions can be easily added.
Indicators of Compromise
Detecting Fast Flux activities by using Indicators of Compromise (IoCs) is also possible – specifically, domain names from VirusTotal. One nice feature of VirusTotal Threat Intelligence is that they store a lot of data about domain names, including the TTL. Along with other search modifiers, a query can be made to produce a list of suspected Fast Flux domain names.
For example, this query will provide domain names (A records) that have a TTL of 5 minutes or less – 10 or more engines think is malicious – and it has been analyzed within the last month.
entity:domain a_ttl:300- category:malware positives:10+ last_modification_date:30d-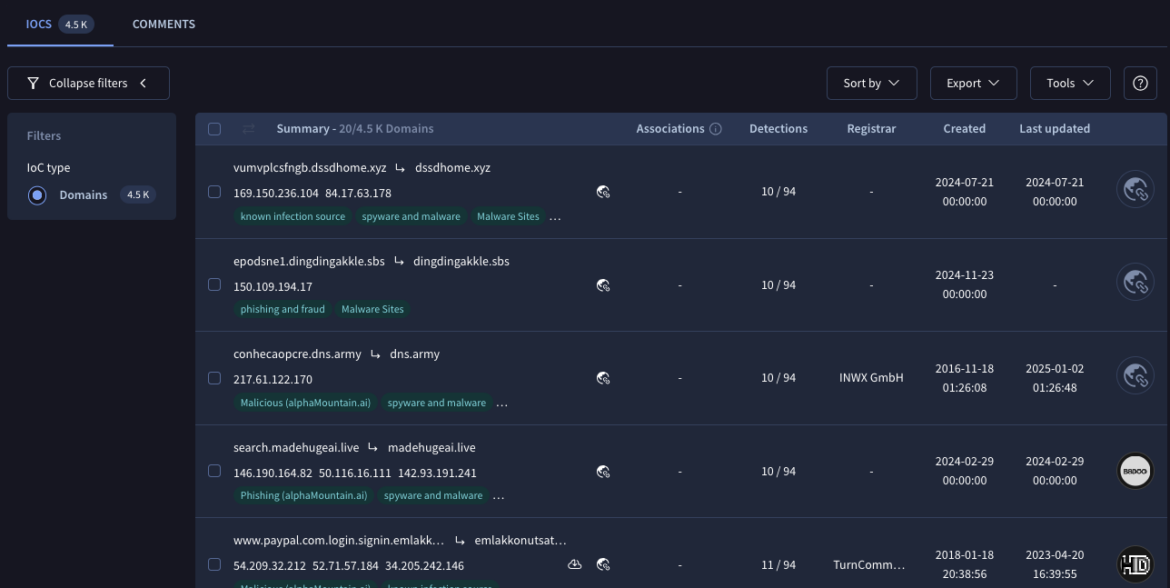
Using VirusTotal, you can augment existing detections with IoCs. While you should never rely on static IoCs like these, they are an essential part of a good layered defense strategy.
Preventing Fast Flux attacks
Fast Flux utilizes a feature of the DNS system, so it isn’t a bug that can be patched. That’s why a layered defense that includes detection and response is critical. Using tools like Sysdig Secure, Fast Flux can be identified and prevented. Another way of improving DNS security is to leverage a Protective DNS service that takes more proactive measures by managing all DNS traffic.
Staying ahead of cloud threats with Sysdig
In the cloud, every second counts. Sysdig was built to help security teams protect their organizations in real time without slowing them down. Born from the open source legacy of globally recognized tools like Wireshark, Stratoshark, and Falco, Sysdig Secure carries that spirit forward. The Sysdig Threat Research Team (TRT) upholds that ethos by actively uncovering and openly sharing threat intelligence to help security teams keep pace with the rapidly evolving cloud landscape.


