
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

What if a malicious threat actor would want to get into the U.S. Department of Defense's (DoD) network. Could they do it?
You may think this only happens in the movies, right? In this case, reality surpassed fiction.
On Dec.20, 2018, the APT10 Group did exactly that. Members of APT10 stole personal, confidential information, including social security numbers and dates of birth, from over 100,000 Navy personnel.
They hacked into a managed service provider (MSP) who had access to lots of networks, and then spidered into each of the customers' networks, running scans on the DoD's IPs to see if there were any shared folders open to the DoD's network.
You can read about it here.
If you are already working to some degree with the DoD of the U.S., you may already know about DISA STIG compliance. But if your organization has never done business with the DoD, you may not know how all these intricacies work.
This blog post is an in-depth exploration of DISA STIGs, what they are, the different categories, and how Sysdig Secure can help your organization achieve DISA STIG compliance for Docker and Kubernetes.
What are DISA STIGs?
DISA STIGs are security guides that contain technical advice to properly harden those contractor systems that attempt to communicate with the DoD systems of the U.S. That's something our MSP friends should have done if they happened to host systems that had that type of relationship with the DoD, right?
Defense contractors process, store, and secure DoD data-related contracts. To better protect this highly sensitive data, the Defense Information Systems Agency (DISA) created a set of mandatory configuration standards, known as Security Technical Implementation Guides (STIG).
These are designed to make devices (both hardware and software) as secure as possible, safeguarding the DoD IT network and systems.
STIGs are available for a variety of IT systems including operating systems, virtualization software, network appliances, databases, or open source software applications, among others. The DoD has released hundreds of STIGs, and the process has evolved to meet the needs and challenges of cloud-native software development.
DISA STIG Compliance Levels
Within the STIGs, there are three compliance levels, named categories. The categories indicate the severity of the risk of failing to address a particular weakness.

DISA STIGs for Containers and Kubernetes
Docker Enterprise was the first container platform to pass the STIG process. DISA released the Container Platform Security Requirements Guide (SRG) in December 2020 to direct how software containers go through the STIG process.
The Kubernetes STIG was released April 21, 2021.
Some of the requirements included in DISA STIG for Docker and Kubernetes are shared among other compliance or best practices policies, like NIST, FedRamp, or CIS:
- Communication channels must be encrypted
- Run the containers with policies that limit the use of resources (CPU, memory, storage)
- Follow Container Best Practices
- TLS certificate authority (CA) certificate file ownership must be set to root:root
Sysdig Secure is designed specifically to understand all the nuances of Kubernetes workloads. We are built to be the best companion the container's orchestrator can have, almost like its psychoanalyst. Based on our no-secrets relationship, Sysdig is able to automate the task of assessing DISA STIG compliance for Docker and Kubernetes.
Why DISA STIG Is Important
All Government agencies are mandated to receive an Authorization to Operate (ATO) before they can connect to the DoD network or system. System integrators (SIs), government contractors, and independent software vendors must comply with relevant STIGs as a major part of the process.
If you plan to work for the DoD, you must prepare your systems to be DISA STIG compliant.
Once the accreditation is earned, the ATO must be maintained. Non-compliance can result in millions of dollars in fines and detailed investigations to be carried out on the agencies.
STIGs are notorious for their complexity and the hurdle that STIG compliance poses for technology project success in the DoD. Oftentimes we find organizations with limited staff to perform the lengthy STIG compliance scan, remediation, and reporting tasks. We can almost imagine the pain of the program managers in charge of this task. DISA STIG compliance can turn out into a nightmare, that one in which you fall forever, like the feeling of a never-ending catchup to ensure all of the systems are in compliance.
Automation is the clear path forward.
How to Use Sysdig Secure for DISA STIG
Although the DoD Cloud Computing SRG indicates that CIS Benchmarks are an acceptable alternative in place of STIGs, many organizations are still required to demonstrate compliance with STIGs specifically.
Sysdig Secure offers more than 50 out-of-the-box security policies, with DISA STIG for Docker and Kubernetes included as part of the bundle.
We've created separated policies to support the different STIG categories:
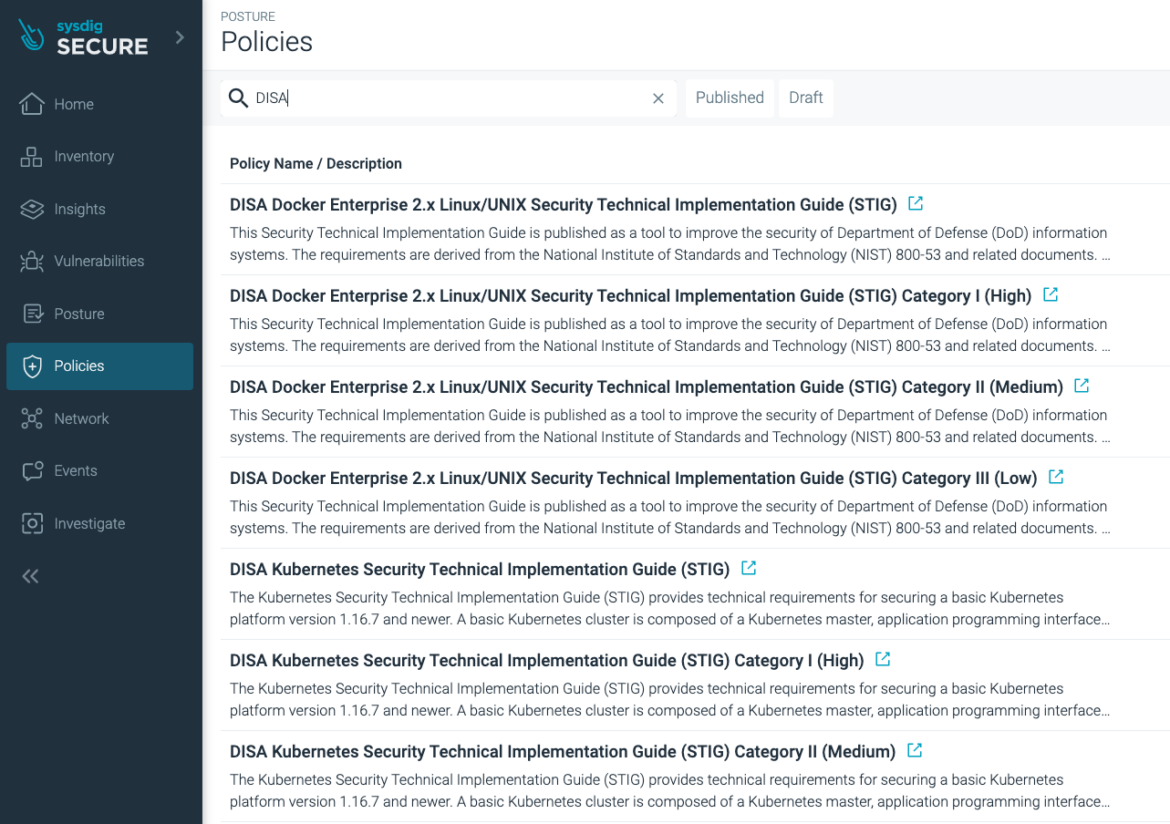
These compliance policies map individual STIG requirements to compliance controls based on Open Policy Agent (OPA) and its policy-as-code foundation.
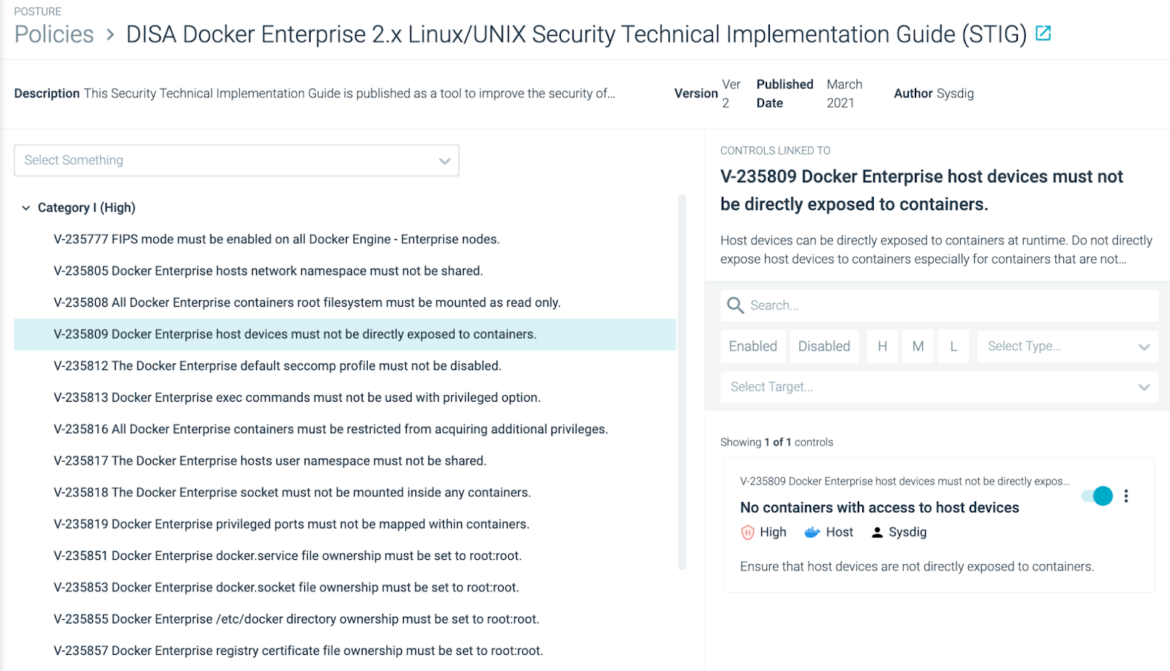
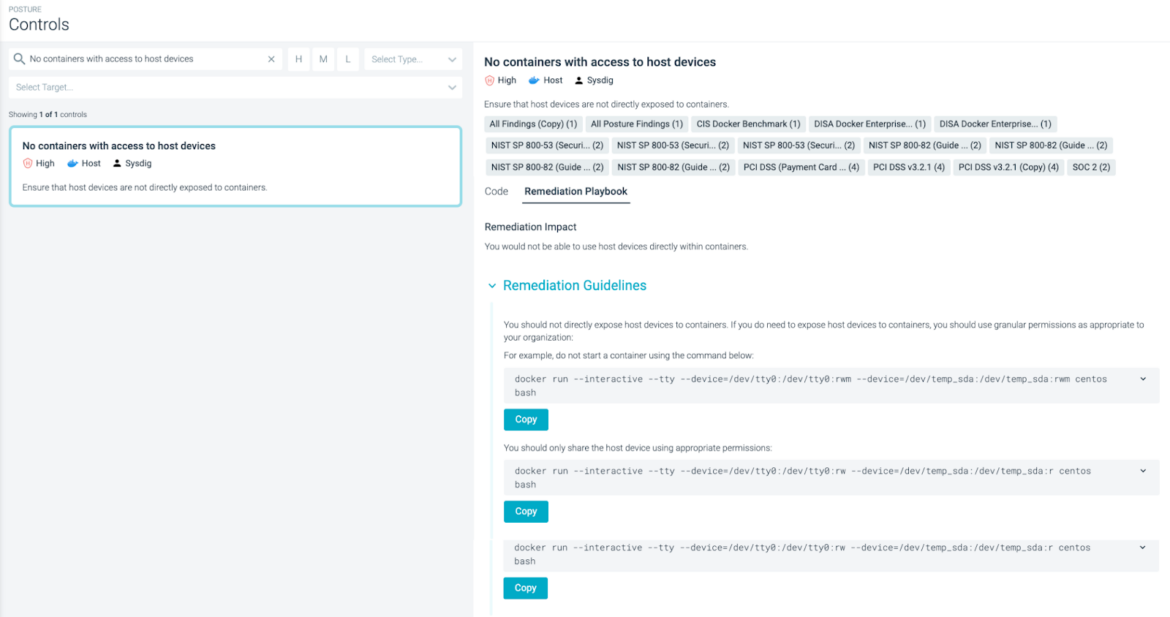
Sysdig Secure makes compliance scalable and predictable by enforcing policy as code as part of DevSecOps workflows. Plus, Sysdig Secure can be used to enable continuous compliance across hybrid infrastructure by scanning for adherence to security requirements, ensuring secure system configuration.
While automation is extremely helpful in configuring systems to be compliant at deployment, system states will inevitably drift over time and fall out of compliance. So, you want to make sure that your compliance automation platform checks for drift and provides remediation playbooks in order to speed up the remediation process.
To check the security posture of a particular Docker/Kubernetes environment for DISA STIG, you just have to create a Zone and select the DISA STIG policy to enable all relevant controls, automatically applying to the appropriate scope of K8s nodes or Docker applications, reaching hundreds or thousands of nodes at once.
If you are monitoring the security posture of your Docker/Kubernetes environment for other relevant Compliance policies, just add the DISA STIG policy to the list and you will be set.
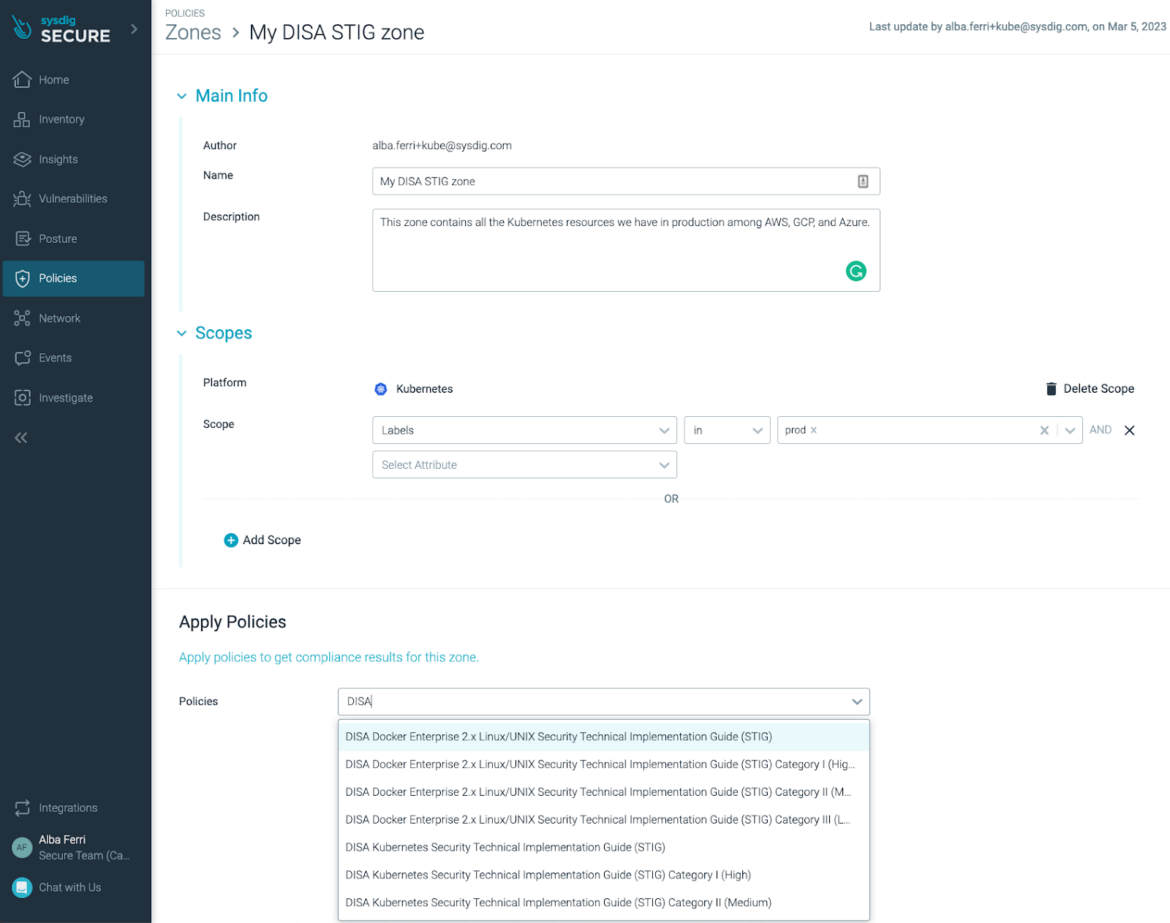
Sysdig Secure allows teams to assess infrastructure-wide compliance and quickly identify workloads that don't meet security requirements.
After defining your baseline compliant state configurations, Sysdig Secure will continuously check your infrastructure so whenever a system drifts from its compliant state, it will automatically flag those changes.
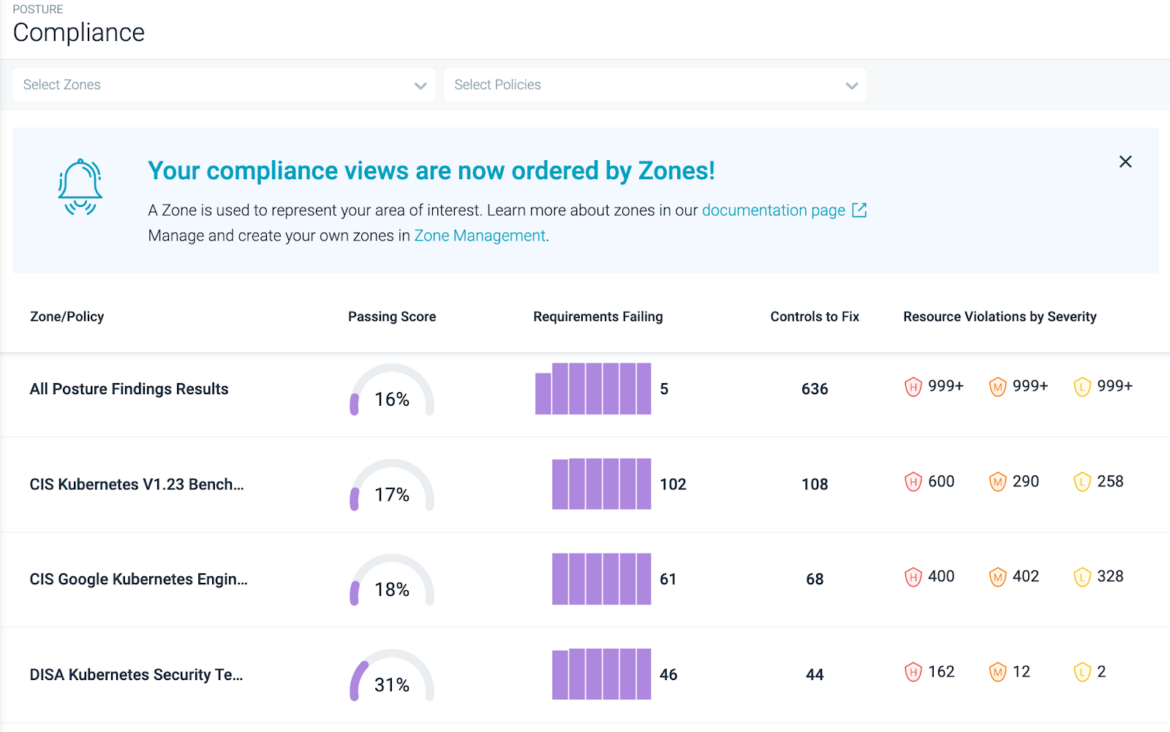
To get a clear view of the status of each control, Sysdig users are able to see a resource centric inventory with all the resources that need to pass a particular control and its status (passing or failing). Sysdig Secure allows you to reduce workforce costs associated with compliance and generate automatic reports to stay ahead of audit preparation.
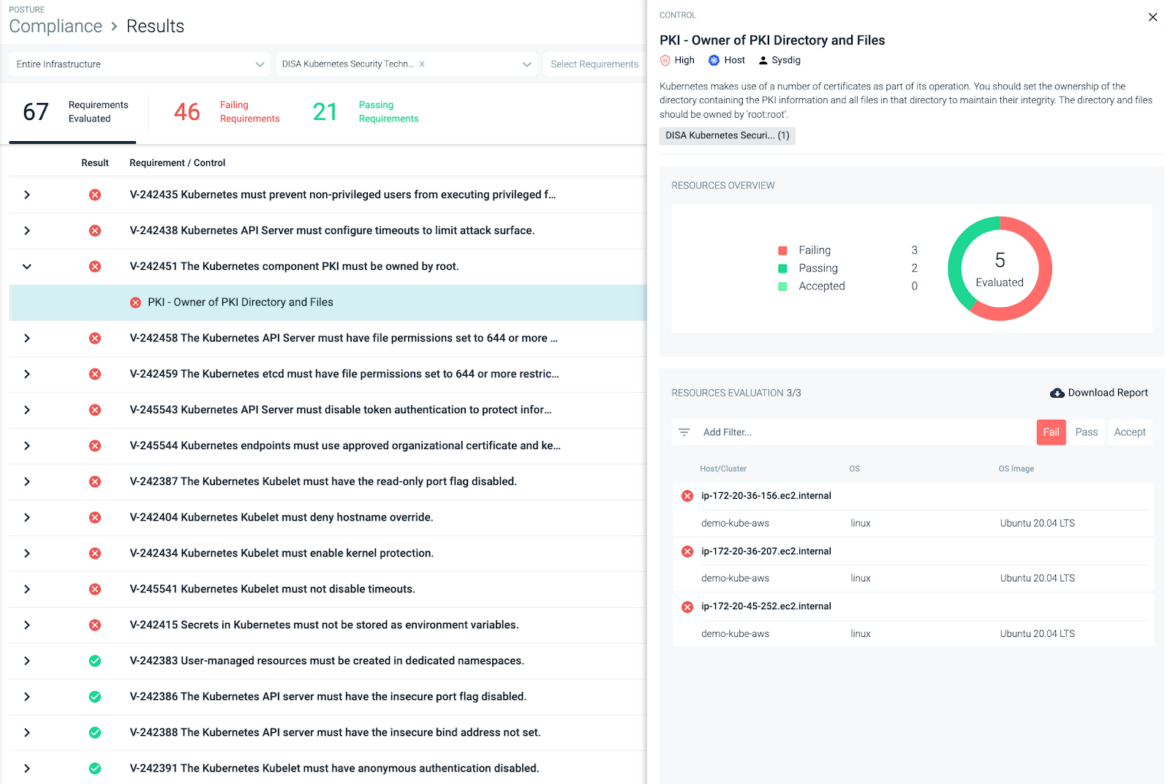
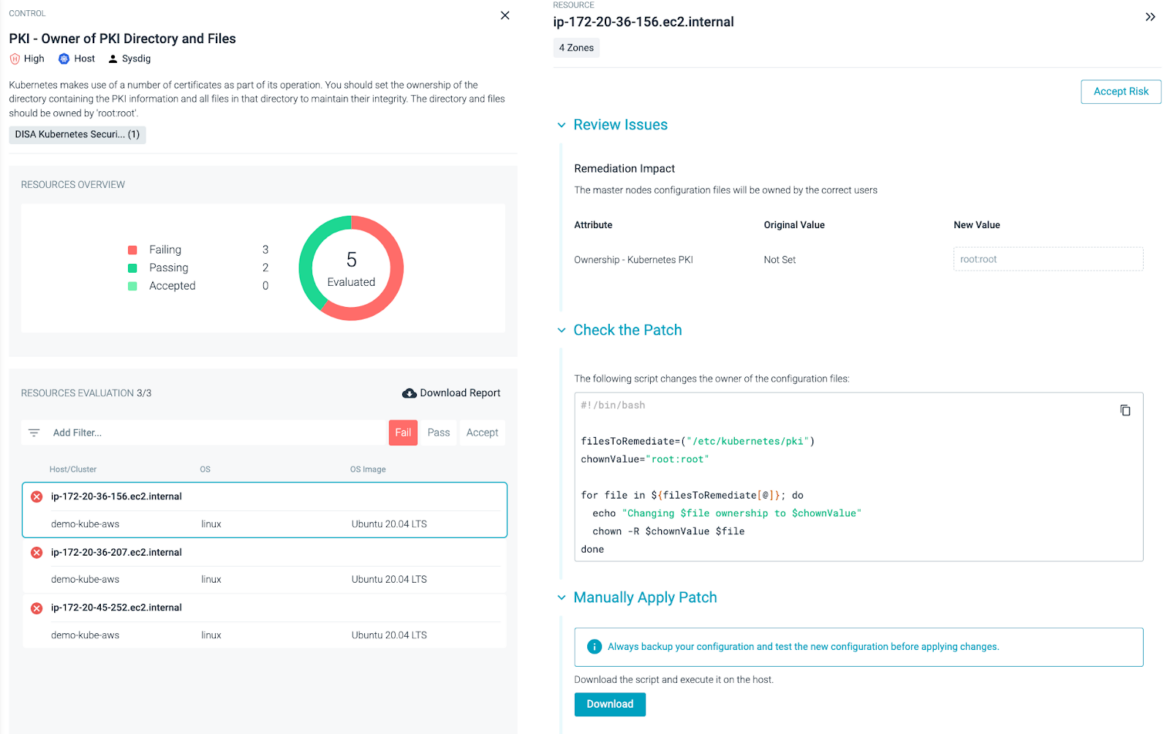
You can remediate compliance failures and build a framework for ongoing compliance with content created by Sysdig experts and tailored to your environment.
Conclusion
With hundreds of different controls, DISA/STIG compliance audits can require significant resources to complete manually. Oftentimes, companies don't have the time or the bandwidth to tackle it. Automated auditing tools that check against the latest STIGs requirements can save valuable time.
Sysdig Secure offers an enterprise solution custom made for Docker and Kubernetes. Automating government security and compliance with Sysdig ensures containerized applications are configured correctly to meet the requirements, helping you stay that way.
If you want to learn more about how Sysdig Secure can help with the Security Posture of your environments, visit the Sysdig Secure trial page and request a 30-day free account.
You'll be up and running in minutes!


