Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

In today's digital landscape, cyber threats continue to evolve at an alarming pace, with hackers constantly finding new ways to infiltrate systems and compromise sensitive data. One such sophisticated threat is fileless malware, a stealthy form of malicious software that operates entirely in the computer's memory without leaving any trace on the hard drive. Unlike traditional malware that relies on executable files, fileless malware exploits existing legitimate processes, making it incredibly difficult to detect and eradicate.
This poses a significant challenge for cybersecurity professionals, as the absence of file-based indicators makes traditional antivirus solutions ineffective. However, there is a ray of hope on the horizon. Sysdig Secure, a cutting-edge security platform, has recently introduced advanced capabilities to detect and combat fileless malware, offering a robust defense against this insidious threat. In this blog post, we will delve deeper into the world of fileless malware, understand its implications, and explore how Sysdig Secure is revolutionizing the fight against this worrisome menace.
What is memfd?
Memfd (short for memory file descriptor) is a Linux kernel feature that allows the creation of in-memory file objects without the need for a physical file on the disk. It provides a unique way for processes to share data and resources by storing them directly in memory. This feature has gained significant attention in the context of fileless malware attacks due to its potential for stealthy execution.
Since memfd files reside solely in memory and are not visible in the file system, they present an ideal avenue for attackers to leverage fileless techniques. By utilizing memfd, malware can execute its malicious code directly in memory, evading traditional file-based detection methods and leaving no trace behind. This makes memfd an attractive option for cybercriminals seeking to bypass security defenses and carry out stealthy and persistent attacks. The rise of memfd underscores the need for advanced security measures that can effectively detect and counter fileless malware threats.
Using Falco to detect a fileless attack
Fileless attacks can be executed by leveraging the capabilities of the memfd_create or memfd_secret syscalls: these calls allocate a section of memory and return a file descriptor that points to it. Once the fd is available it's possible to write an ELF file directly in the memory and use one of execve or execveat syscalls to execute the binary. Those syscalls use the pointers provided as input to refer the ELF's bytes and run it: the result is a process named as the fd (so it will be basically the number of the file descriptor), the execution path can be empty but – in the process args – we'll always see the EXE_FROM_MEMFD flag.
The below rule basically looks for these two types of executions where the name starts with memfd:
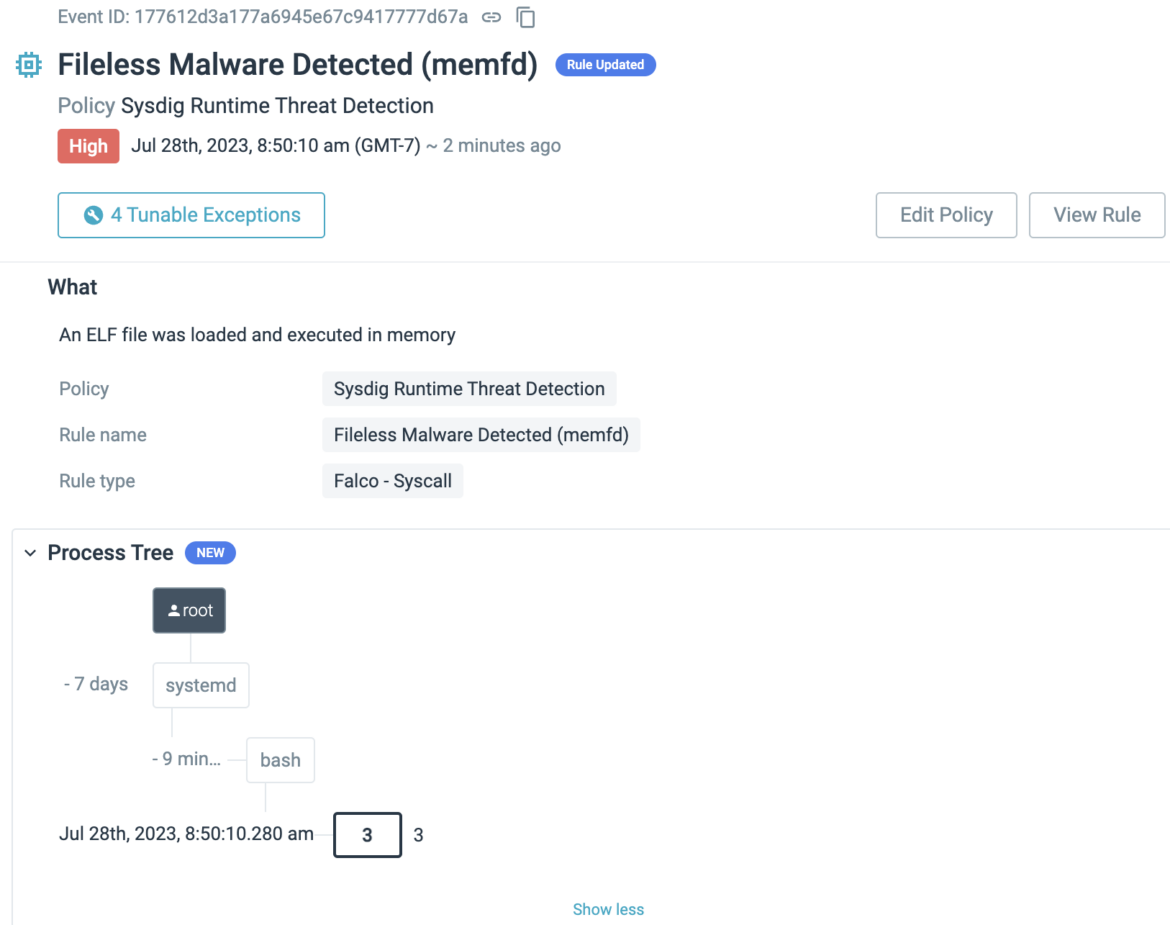
How do I enable the above rule?
Sysdig Secure's Managed 'Sysdig Runtime Threat Detection' Policy will now include the new detection rule 'Fileless Malware Detected (memfd)' by default, with a high severity rating. Once you have upgraded to agent version 12.15+, the policy will allow you to detect fileless malware without the need for any additional configuration steps.
How to trigger the detection
You'll need a script to trigger this detection rule. It basically loads an executable in memory and runs it directly from the memory. In the case of the detection output, we ran a Python script using this tool to generate the activity. This tool generates interpreted code which creates the supplied ELF as a file in memory and executes it (without tmpfs). This makes it possible to execute binaries without leaving traces on the disk.
import ctypes, os, base64, zlib
l = ctypes.CDLL(None)
s = l.syscall
c = base64.b64decode()
e = zlib.decompress(c)
f = s(319, '', 1)
os.write(f, e)
p = '/proc/self/fd/%d' % f
os.execle(p, 'dummy', {})Understand context in the Activity Audit
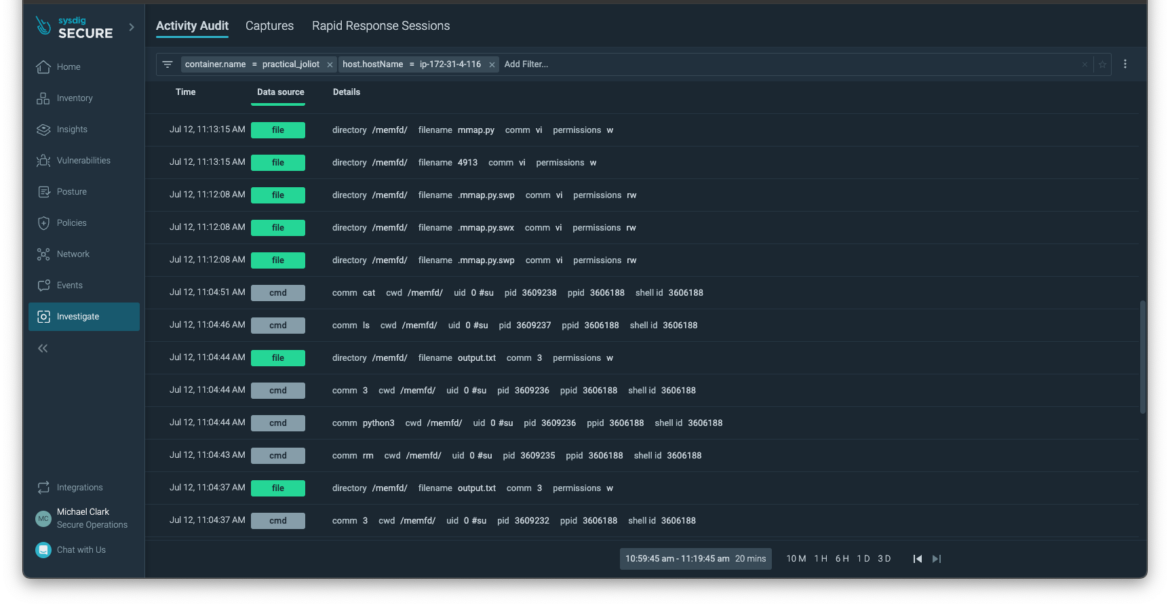
The audit log presents evidence of a download taking place, along with a significant process replacement event. For shared context, fileless attacks commonly involve the downloading of a malicious binary, which is then stored in a memory-backed file descriptor. This descriptor serves as a means to execute the downloaded binary. The unique aspect of these attacks lies in the fact that the descriptor resides solely in memory and lacks a corresponding presence in the file system, rendering many conventional defense mechanisms ineffective. To enhance the accurate identification of such incidents, the Sysdig Secure team has introduced a new indicator called proc.is_exe_from_memfd. This flag will be set to true whenever a memory file descriptor is employed to reference the underlying backing storage of a file, enabling more precise detection of fileless malware activity.
Conclusion
Building an endpoint protection agent based on a real-time, system-call architecture is crucial for effectively detecting and preventing fileless malware attacks. Relying solely on file-based detection methods becomes inadequate in identifying such threats. By utilizing a real-time, system-call architecture, an endpoint protection agent can monitor and analyze the dynamic behavior and interactions between processes and the operating system.
To learn more, check out the Sysdig blog: Fileless malware mitigation


