Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

On January 16, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) sent out a Cybersecurity Advisory (CSA) about active threat actors deploying the AndroxGh0st malware. This is significant as cyber criminals are actively using this malware to target Laravel (CVE-2018-15133) (an open source PHP framework).env files and obtain credentials for various high profile applications like Office365, SendGrid, and Twilio.
The joint advisory committee recommends security teams to implement specific controls to limit the blast radius and stop threat actors from stealing sensitive data. It also reports that cyber criminals use AndroxGh0st to target websites with the PHPUnit module (CVE-2017-9841) and scan servers running vulnerable Apache services (CVE-2021-41773).
Phishing emails linger around
Emails are the leading threat vector exploited globally by cybercriminals. The growth in the number of weaponized emails is alarming. The numerous built-in functions in AndroxGh0st crack open Simple Mail Transfer Protocol (SMTP) to scan and exploit exposed credentials, application programming interfaces (APIs), and launch web shell deployments.
Cybercriminals, therefore, repeatedly abuse popular email services with AndroxGh0st to spread malicious links, attachments, and viruses through a potential trusted entity. The malware parses a configuration file (.cfg) for specific variables and pulls out their values for follow-on abuse. The python-based malware has inspired many similar tools like AlienFox, GreenBot, Legion, and Predator.
The established botnets scan the Internet for exposed domain root-level .env files. This file commonly stores credentials and threat actors target high-profile services to exfiltrate it from your cloud environment. Later, they can either issue a HTTP GET or a POST request to ship the sensitive data out of your environment. They can even encrypt PHP code with the exfiltrated application keys to perform cross-site forgery.
Sysdig shields up against AndroxGh0st
An attack of this nature can result in both reputational damage for the targeted company, and like other phishing scams, can result in data theft and ransomware for the targeted individuals and companies. This attack trail also reinforces the importance of following best practice guidelines from the cloud providers.
This attack could have been prevented in a number of ways, including:
- Vulnerability management to prevent initial access.
- Secrets management to ensure credentials are not stored in the clear where they can be stolen.
- CSPM/CIEM to ensure the abused account had the least amount of permissions it needed.
- Threat detection and response to identify whenever any of the above fail and quickly mitigate the attack.
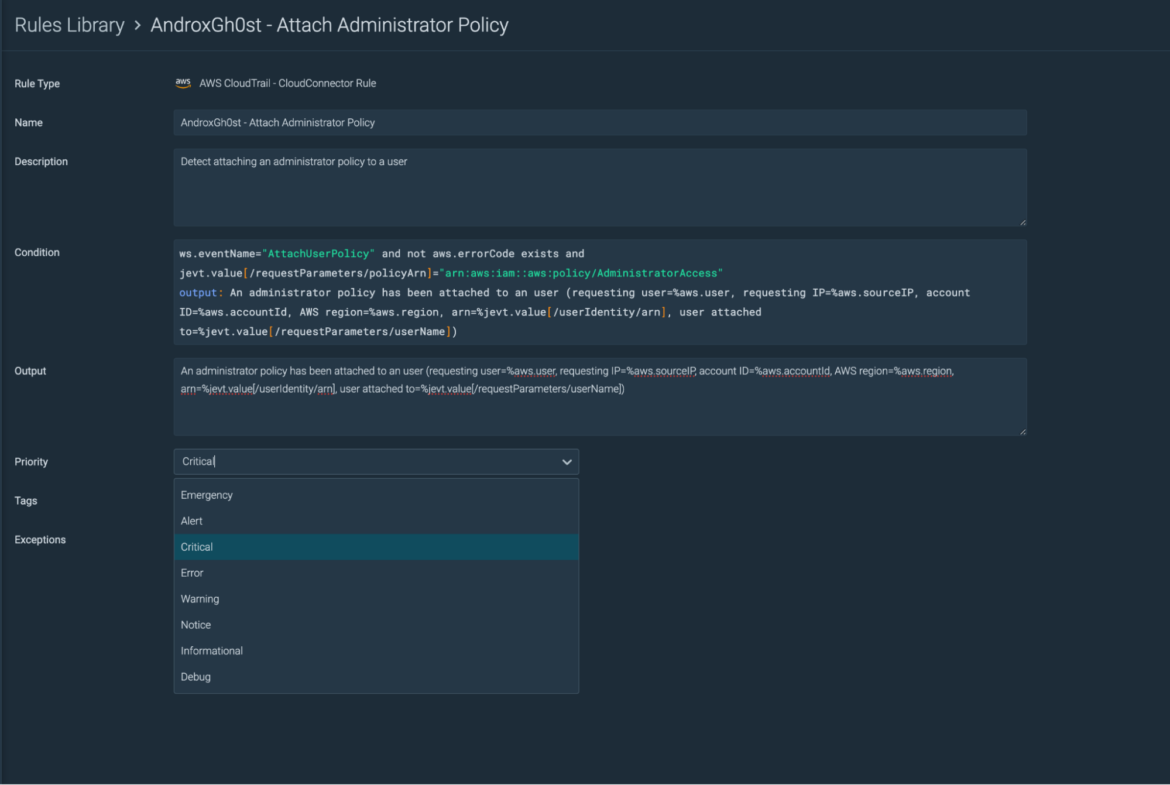
Sysdig Secure enables complete visibility into the security and integrity of your cloud environments to identify potential threats from modern-day cybercriminals. It provides high-fidelity events based on data collected to uncover threats that operate in stealth mode.
With Sysdig, you have a comprehensive runtime security library (available out-of-the-box) with container-specific rules (and predefined policies) defined by our threat research team. These rules detect events in real time and respond to security violations, suspicious behavior, and anomalous activities within your environment.
Learn how other antivirus vendors detect AndroxGh0st, and view the Indicators of Compromises (IOCs) and CISA recommendations.
Cloud security needs a new benchmark
Malicious actors need less than 10 minutes on average to execute an attack in cloud environments. No organization can stay safe without a threat detection and response program for addressing zero-day exploits, insider threats and other malicious behavior. Cloud-native development and release processes pose unique challenges for threat detection and response.
Like the AndroxGh0st incident, you saw that attackers focused heavily on cloud service compromise and identity abuse – both human and machine. Your cloud security program needs a new benchmark.
The 5/5/5 benchmark – 5 seconds to detect, 5 minutes to triage, 5 minutes to respond – challenges organizations to acknowledge the realities of modern attacks and to push their cloud security programs forward. The benchmark is described in the context of challenges and opportunities that cloud environments present to defenders. Achieving 5/5/5 requires the ability to detect and respond to cloud attacks faster than the attackers can complete them.
Conclusion
Cloud-based email services can be abused to launch phishing attacks, which are still extremely effective. Phishing still leads to the most prolific ransomware attacks and can have major impacts on unexpecting end users.
In the cloud, every second counts. Attacks move at warp speed, and security teams must protect the business without slowing it down. Evidence of cloud-based attacks are emerging daily that indicate that attackers are aware of the many different services and will exploit them to reach their goals – no matter how obscure the services may be.
Dig deeper into how Sysdig provides continuous cloud security across AWS, GCP, and Azure.


