Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

10 minutes to pain. When it comes to cloud security, 10 minutes or less is what bad actors need to execute an attack. Does it mean your business could be at risk if you fail to detect and respond to an attack in less than 10 minutes? Absolutely yes.

With more and more sophisticated security attacks actively occurring nowadays, security teams need to hold themselves to a modernized benchmark. The 555 Cloud Detection and Response Benchmark, built in partnership with our customers, industry analysts, and the Sysdig Threat Research Team (TRT), sets a new standard for operating securely in the cloud.
Sysdig is collaborating with Tines, one of our Threat Detection and Response (TDR) technology partners, to integrate with orchestration and automation features that help security teams tackle the most complex attacks. The Tines smart, secure workflow platform tears down barriers to timely response and reduces the complexity of automation for TDR. DevSecOps, operations, and security teams can now simplify security workflows, shorten response time, and ultimately stay ahead of potentially major security incidents.
Detect, triage, and respond at cloud speed
The 555 Benchmark sheds light on the time it takes attackers to cause harm once they exploit vulnerabilities. It also challenges organizations to perform at a higher level to respond faster than attackers:
- 5 seconds to detect security threats
- 5 minutes to triage and correlate
- 5 minutes to initiate a response
Initiating a quick and effective response can be tricky. Human latency makes reaching a 5 minute response time extremely difficult. One of the most recent examples of a complex and sophisticated attack is Scarleteel. Discovered by the Sysdig Threat Research team in early 2023, with Scarleteel, bad actors gained access to a system by exploiting a vulnerability, then not only performed malicious activity like running cryptominers, but also moved laterally after stealing credentials via abusing and attacking the cloud metadata API. What initially seemed to be a single-target attack, quickly became a much more serious and complex security threat spread throughout the cloud infrastructure. If not stopped in a timely manner, an attack of such a magnitude can cause unrecoverable damage.
Adding automated response to the equation with Tines
DevSecOps, and security operations teams triage and analyze massive numbers of security findings as they emerge. Live data if available, besides dumps or captures gathered from containers or cloud services, are fundamental elements for any forensics efforts and incident investigation. However, responding immediately, without delay, is a must. Security Orchestration, Automation and Response (SOAR) tools help to tackle critical security menaces like Scarleteel.
Sysdig partner, Tines, is a next-gen, no-code SOAR tool that empowers security teams to respond automatically to security threats.
The way it works is simple. Users can either choose to use predefined stories (workflows) available in the Tines library, or come up with their own workflow definitions. Workflows are the way data is handled, transformed, and processed towards reaching a desired state.
In order to support workflow creation, Tines comes with tons of out-of-the-box actions for interacting with almost every vendor in the IT landscape. Tines users only need to select the actions they want to use from the library, drag and drop, configure, and connect actions to achieve an outcome.
So far so good. But how can Sysdig and Tines can help with detecting and responding to the most complex and modern security attacks like Scarleteel?
SOAR to overcome security threats
Thanks to the Sysdig and Tines partnership, joint customers can take advantage of SOAR techniques to respond to security threats. It expands response capabilities to stop security attack patterns like Scarleteel. Let's see it in action!
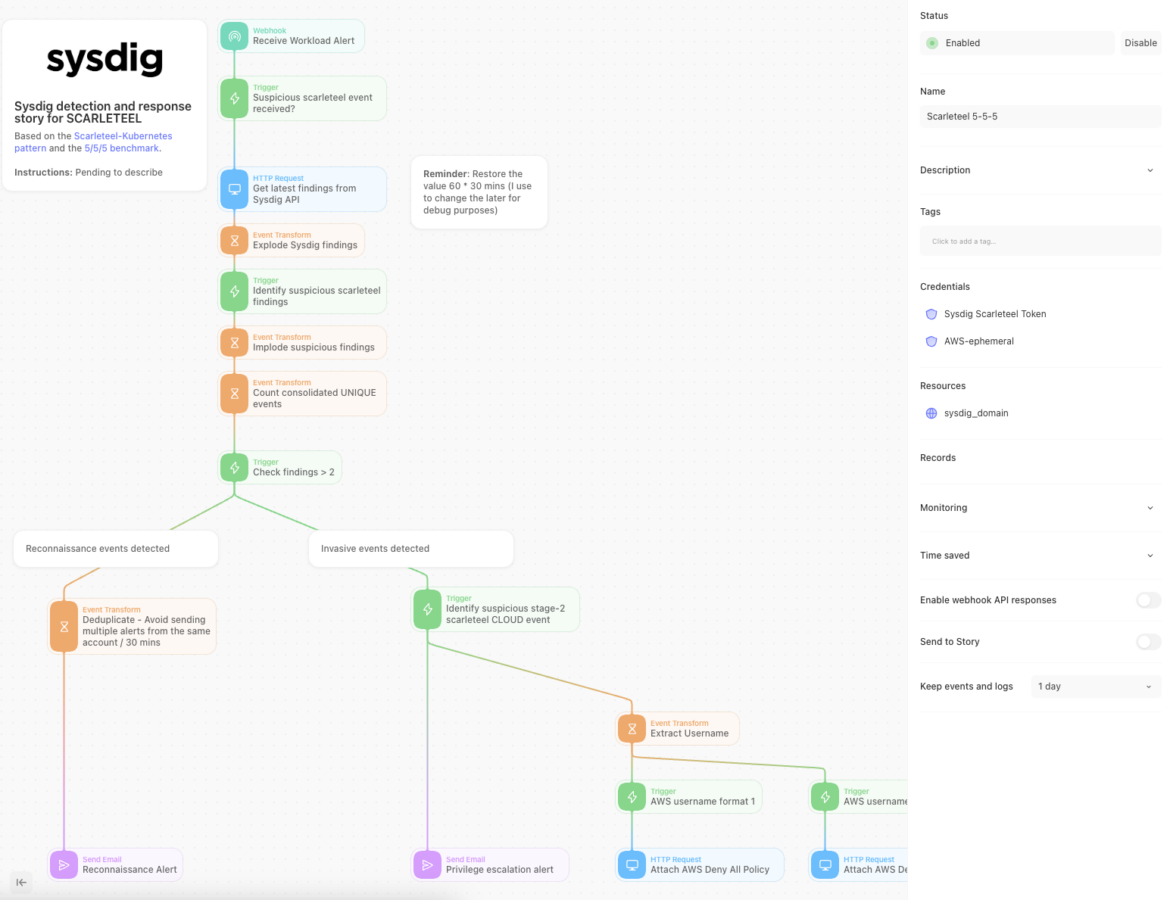
This is how the Scarleteel story by Sysdig looks like with Tines. In short, the data flows the following way:
- Initial security events are gathered from the Sysdig API endpoint, and triaged by an action set in Tines workflow. Meanwhile, Tines keeps looking for any new Sysdig security events, which may provide additional context as to what's unfolding in real-time.
- Tines identifies suspicious events from common Scarleteel patterns. This data is sorted and deduplicated to avoid unnecessary noise. If reconnaissance-related Scarleteel events are found, an alert is sent immediately from Tines to inform users a likely Scarleteel attack just started.
- In workflow stage two, Tines continues analyzing events. If invasive Scarleteel events like stolen credentials or lateral movement are detected, Tines stops the attack automatically by removing permissions in the cloud provider, like AWS IAM.
By implementing very simple workflows like this one, Sysdig and Tines users are not only able to detect complex attacks like Scarleteel, but also automatically stop threats in only a few seconds! Other response actions like step-up monitoring on suspicious processes or terminating compromised containers are also possible depending on the risk appetite of the organization. Thanks to this partnership, exposure, risk, and potential damage are reduced or fully mitigated at cloud speed.
There is more, though. Cloud integrations, project management tools like Jira, CRMs like Salesforce, messaging apps like Slack, and much more can be integrated into your Tines workflow. Expand possibilities by adding new actions to your workflows at any time.
Conclusion
When it comes to stopping a critical security incident like Scarleteel, time is gold. Adopting a less-than-5-minutes-to-respond strategy should be the goal for companies that want to be safe against bad actors in the cloud.
Sysdig and Tines joined forces in this new partnership to help our joint customers detect, triage, and respond effectively to the most modern and advanced cloud attack techniques. As highlighted in this article, advanced SOAR workflows help with response automation by providing mechanisms to get, correlate, and take action based on real data.
Watch the SOAR Into 2024: Power Your Cloud Detection and Response solution forum presentation to learn more. You'll hear how to keep your cloud-speed business innovation secure from cloud-speed exploitation.
Click the banner below to watch on-demand:



