Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

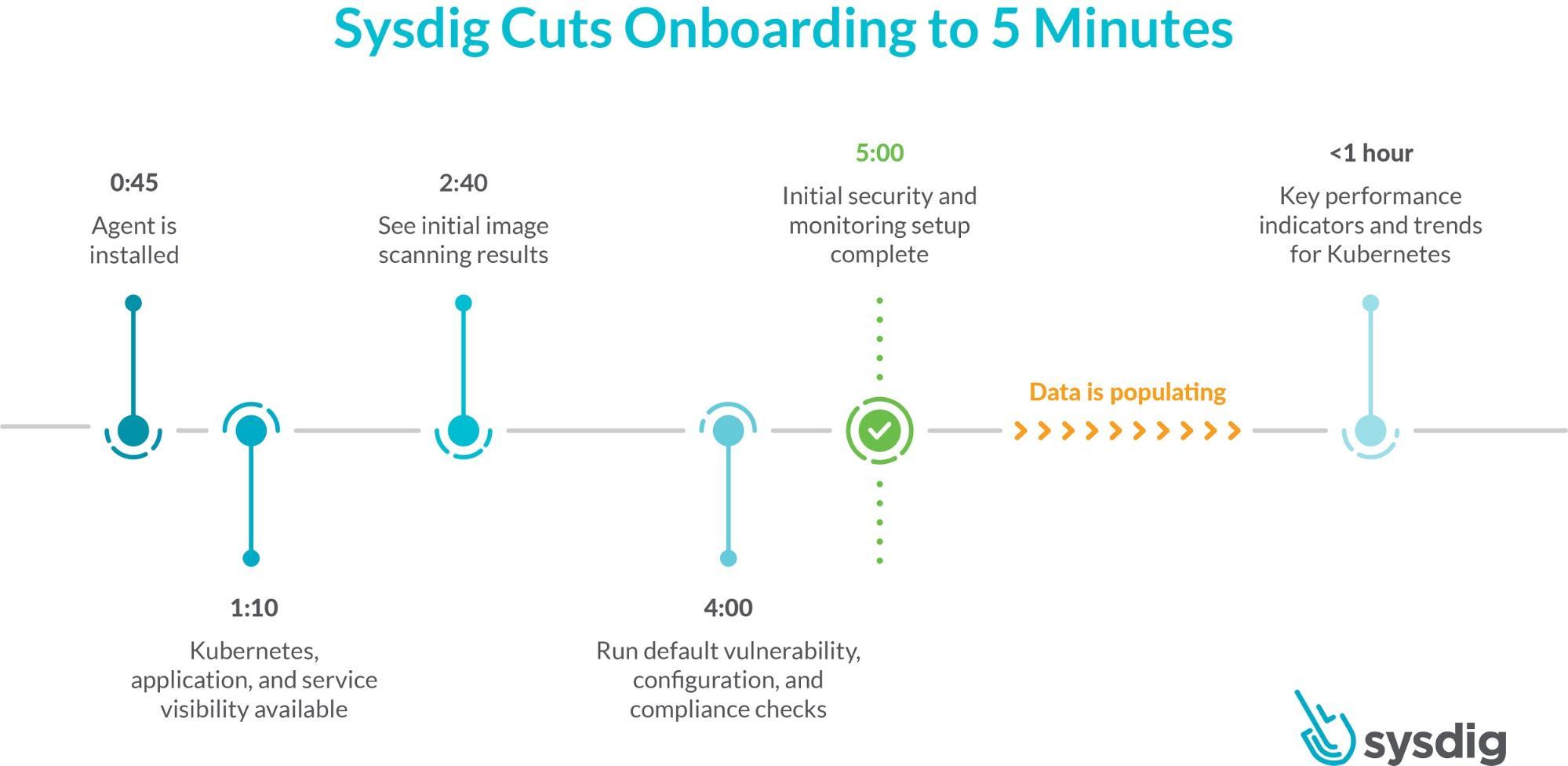
Today, we are excited to announce a faster onboarding for Kubernetes visibility and security. With the SaaS-first approach and new enhancements to the Sysdig Secure DevOps Platform, you can get results after just a five-minute setup. This release includes a new guided onboarding process, out-of-the-box dashboards as part of curated essential workflows, and a new Sysdig Essentials tier.
Organizations often delay investments in security, compliance, and monitoring, thinking it will slow their release train. This places teams in a reactive position, responding to performance and availability issues for applications already in production. Making teams feel unprepared, not only when addressing these issues, but also when they are asked for proof of security controls and regulatory compliance – and even more so if a data breach occurs.As cloud adoption matures, organizations realize automating is key for their success. By embedding image scanning, runtime security, and compliance – along with monitoring – into their DevOps process, it doesn't slow organizations down but rather helps them ship applications faster.
Getting results quickly with Sysdig
Our belief is that by making it easier to get a secure DevOps workflow started, teams will implement security, compliance, and monitoring sooner in their migration to container and Kubernetes environments. This puts them in a better position to succeed.
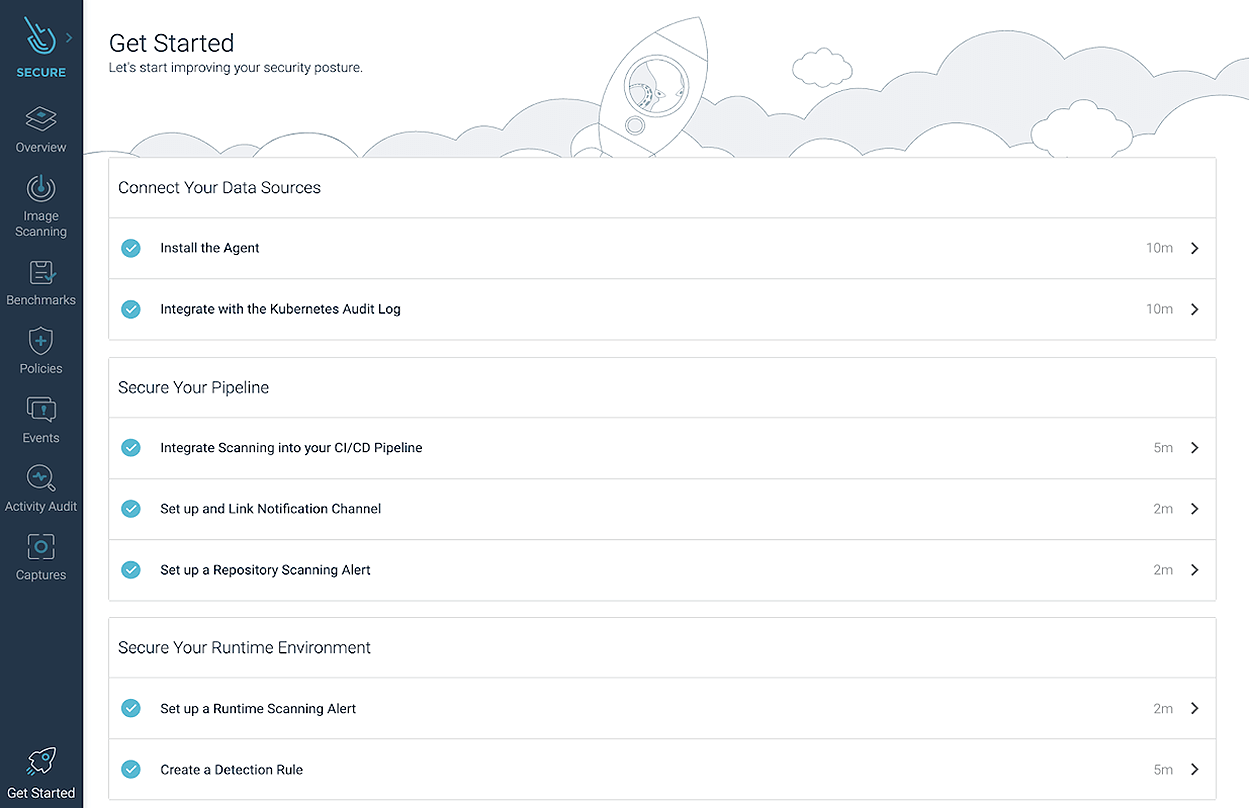
The new simplified onboarding will get you started on the most critical security, compliance, and monitoring functions…in just a few minutes!

Focusing on each of the key secure DevOps workflows, we offer guided onboarding, turnkey workflows, as well as pre-built integrations, policies, and dashboards that will reduce the time it takes for your DevOps team to obtain insights.Finally, our new Sysdig Essentials tier will help organizations that are getting started with container and Kubernetes environments to focus on the essential use cases of a secure DevOps workflow.
Five essential workflows for secure DevOps
Taking the first steps to embed security, compliance, and monitoring in DevOps may look overwhelming. That's why we highlighted these five essential workflows for secure DevOps to help you get started:
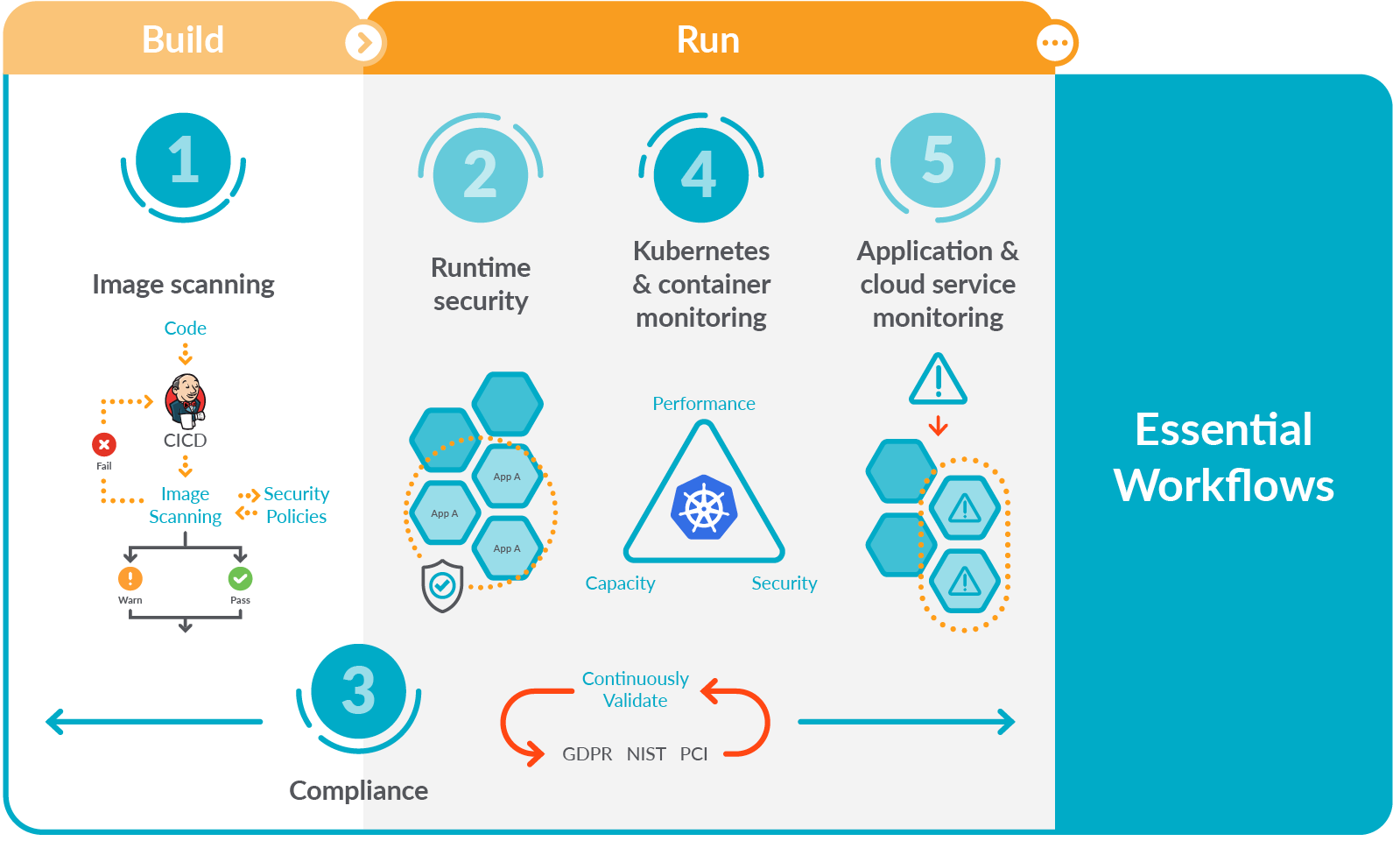
Image scanning: Organizations can manage security risk by finding and fixing vulnerabilities and misconfigurations early in the DevOps process through image scanning. Sysdig continuously scans images both within registries and CI/CD pipelines, as well as during production. This saves time by uniquely mapping vulnerabilities to Kubernetes-based applications.Runtime security: Using Falco, Sysdig enables organizations to detect threats at runtime without impacting performance. Falco is the open-source Kubernetes runtime security project created by Sysdig, and is now a Cloud Native Computing Foundation incubating-level project.Compliance: Passing compliance audits can be time consuming and failing audits is costly. Organizations can continuously validate using out-of-the-box rules mapped against common compliance frameworks including PCI, NIST, and CIS.Kubernetes and container monitoring: With Sysdig, cloud teams receive automatic alerts and detailed health and performance information, including golden signals for clusters, deployments, namespaces, and workloads. Deep visibility into container activity, enriched with cloud and Kubernetes context, allows teams to manage the complexity that is a reality in a containerized ecosystem.Application and cloud service monitoring with full Prometheus compatibility: By leveraging native support for PromQL and Prometheus metrics, DevOps teams can use the industry standard their developers prefer, without running into scaling challenges. Out-of-the-box dashboards display metrics from cloud services, databases, and other key components in their application environment.If you want to learn more, check our guide to the five essential workflows for secure DevOps, including comprehensive explanations, examples, and resources.Further on, as your team gains more experience with Kubernetes and containers, and your environment expands, you can move on to more advanced workflows that further strengthen security and resilience.
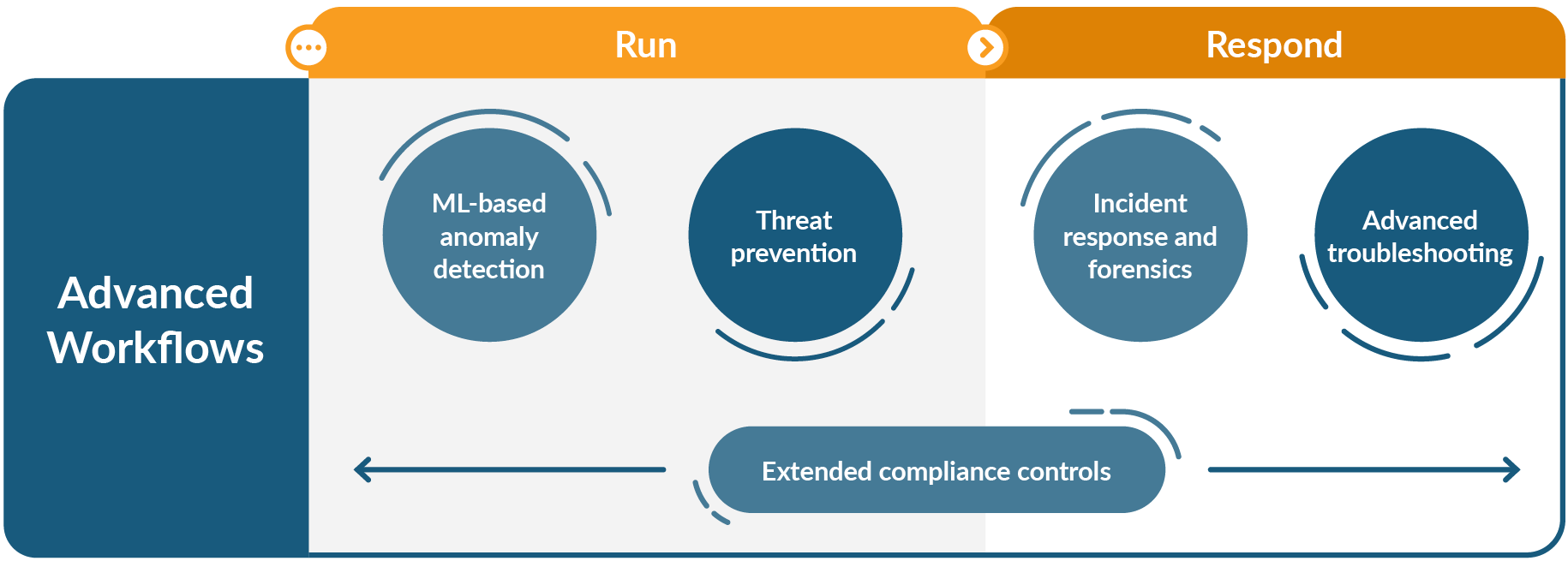
Those workflows are: Advanced troubleshooting, machine learning-based anomaly detection, threat prevention, incident response and forensics, and extended compliance controls. These advanced enterprise workflows include specialized capabilities that yield greater efficiency for DevOps teams.
New Sysdig Essentials tier
In addition to the essential workflows introduced today, the latest Sysdig release includes the Sysdig Essentials pricing tier. This tier is aimed for organizations looking to start with the essential use cases, and provides a simplified on-ramp to a secure DevOps approach.Nothing is easier to set up than the service that is already there for you. Offering the Sysdig Essentials tier as SaaS only is yet another way to simplify your entrance to secure DevOps. SaaS provides faster adoption, more efficient management, and offers organizations security, compliance, and monitoring at a lower cost.Note that the enterprise tier of the Sysdig Secure DevOps Platform, which includes the advanced workflows, is offered both on-prem and as a SaaS deployment.
Using SaaS to your advantage
By taking advantage of the Sysdig SaaS-first platform for security and monitoring of your cloud-native environments, you will be up and running faster and reduce complexity. Other benefits include faster access to features, easy scaling, reduced costs, and greater operational efficiency. Today, one of the biggest benefits to SaaS is the luxury of being able to more efficiently adapt to business changes, as well as the flexibility of operating across different cloud environments — AWS, IBM, Google, VMware, Azure, etc. Other benefits of SaaS include:Get results faster: Getting started with SaaS is dramatically quicker than onboarding an on-prem solution. With our SaaS solution, you install the agent and you're ready to go. Metrics start to flow in less than two minutes after the agent is installed.Reduce complexity: Building, maintaining, and operating on-prem infrastructure for monitoring and security is complex and costly. From project planning and execution to purchasing, integrating, and maintaining hardware and software, there are a lot of pieces for you to manage. With SaaS, rather than focusing resources on operations, you can spend more effort on your core objective of delivering new software capabilities.No hardware costs: With SaaS, there's no need for in-house hardware to support security and monitoring. In addition, you avoid paying for accompanying software licenses and professional services – and your staff won't need to spend time on maintenance and support tasks.Lower operational costs: With a self-hosted solution, you'll require ongoing monitoring and support of the backend infrastructure and components. And, as your environment expands, you will also need to continue to provision new hardware to accommodate growth. With the Sysdig SaaS platform, as your container applications grow, you can scale up without worrying about backend hardware provisioning and ongoing data management.
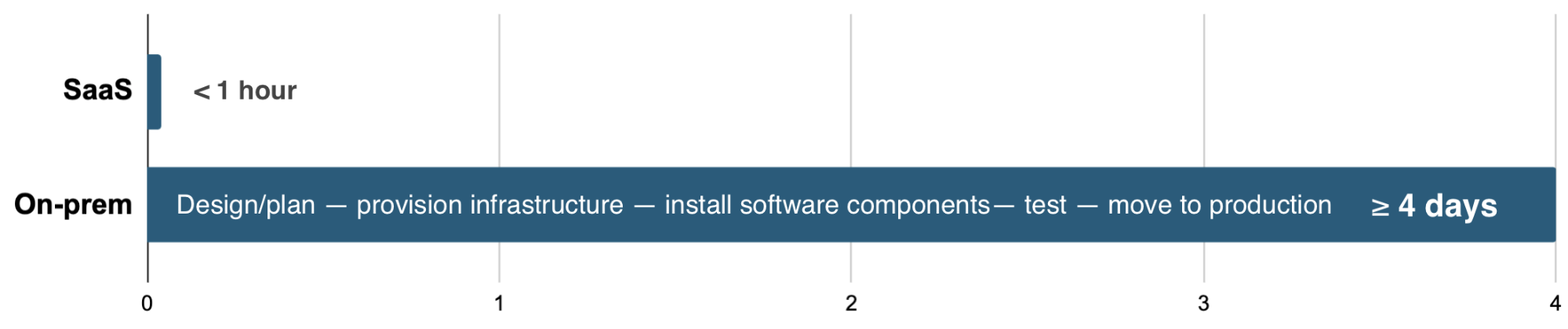
Time to readiness SaaS vs On-prem
Conclusion
Sysdig enables organizations to quickly address security, monitoring, and compliance with a single tool. The Sysdig Secure DevOps Platform is the only unified security and monitoring platform. Acting as a single source of truth, Sysdig eliminates silos of information between development, DevOps, and security teams. With this approach, organizations can resolve issues quickly by analyzing granular system data automatically correlated to cloud and Kubernetes context.Now, with our simple set up and onboarding, DevOps teams can get results quickly while confidently running their workloads in production. And with the new essentials tier, organizations have it easier than ever to control costs and improve efficiency.Try Sysdig today! The new tier starts with a 14-day free trial. All Sysdig products and tiers are priced per host/month, you can find the full details on the Sysdig pricing page.


