
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Use of container platforms like Azure Kubernetes Service (AKS) is accelerating quickly and driving the need for cloud-native security automation. This includes key workflows like image scanning across CI/CD pipelines and registries. Sysdig Secure integrates with Azure Container Registry (ACR) to provide image scanning for AKS and other container platforms. Sysdig analyzes Common Vulnerabilities and Exposures (CVE) within OS packages as well as 3rd party libraries to help DevOps teams know what to fix. In addition, Sysdig Secure identifies misconfigurations that should be remediated before pushing to production.
In this blog we will dive deeper into how to integrate Sysdig Secure with ACR to scan images for Kubernetes for security and compliance purposes. Sysdig has offered unified visibility and security for container and Kubernetes deployments on Azure for years. Now with native CI/CD and registry integrations, you can shift security visibility earlier into your build pipeline.
About Azure Container Registry
ACR provides a container image registry that allows you to store container images for all types of orchestration platforms including Kubernetes, Docker, and Red Hat OpenShift as well as Azure services such as App Service, Machine Learning, and Batch. ACR handles private Docker container images as well as related content formats, such as Helm charts, OCI artifacts, and images built to the OCI image format specification.
Azure Container Registry Security and Sysdig Secure
Scanning images in Azure Container Registry is the same as scanning from any other Docker v2 compatible registry. Once configured, the entire registry or individual images and tags can be analyzed and then evaluated against a Sysdig Secure Scanning policy.
The first step is to pass the ACR credentials into Sysdig Secure to give access to the registry. Once configured the Sysdig Secure scanning engine can pull any image stored within the registry into the engine for analysis.
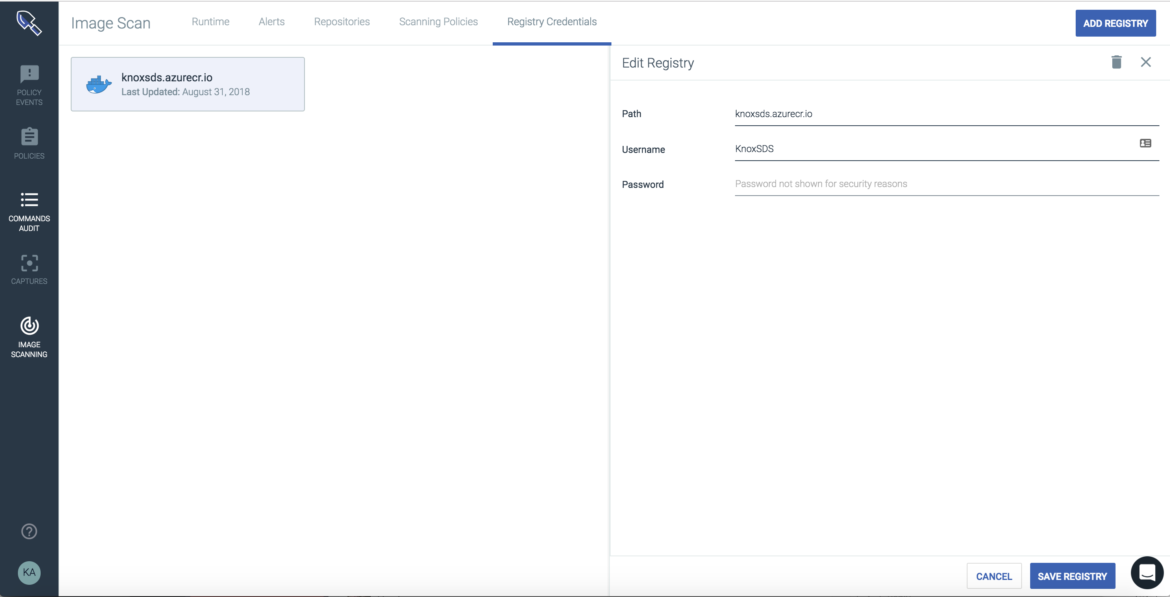
When an image is pulled into the scanning engine Sysdig Secure will provide visibility into:
- Official OS packages
- Unofficial packages
- Configuration files
- Artifacts such as Javascript NPM modules, Python PiP, Ruby GEM, and Java JAR archives
- Secrets, credentials like tokens, certificates and other sensitive data
- Known vulnerabilities & available updates
These artifacts are then stored and evaluated against custom scanning policies to spot vulnerabilities, misconfiguration, or compliance issues within your images.
Scanning Container Images in Azure Container Registry
Adding an image to the scanning engine from ACR is as simple as copying the registry URL/image/tag into the Sysdig Secure UI and clicking scan image. This process can also be easily scripted to import all images and to watch repositories for updates.
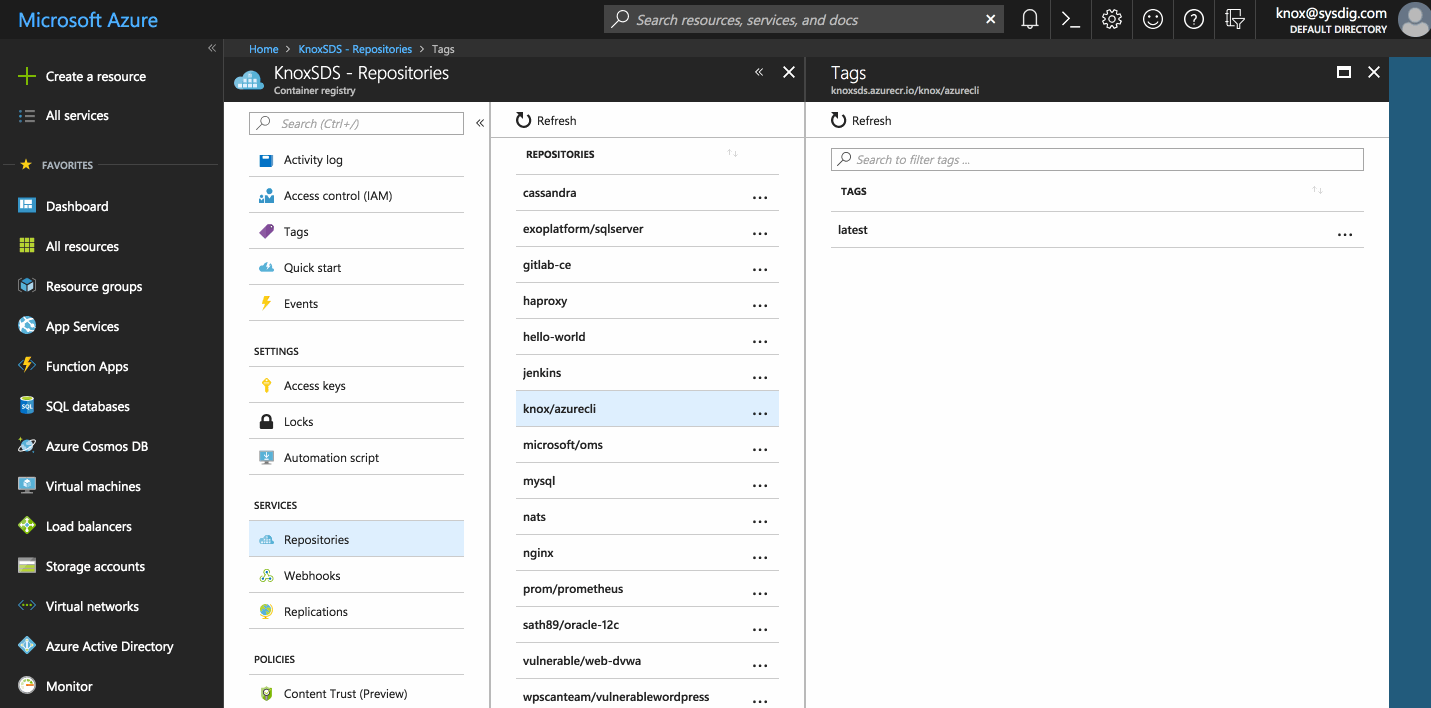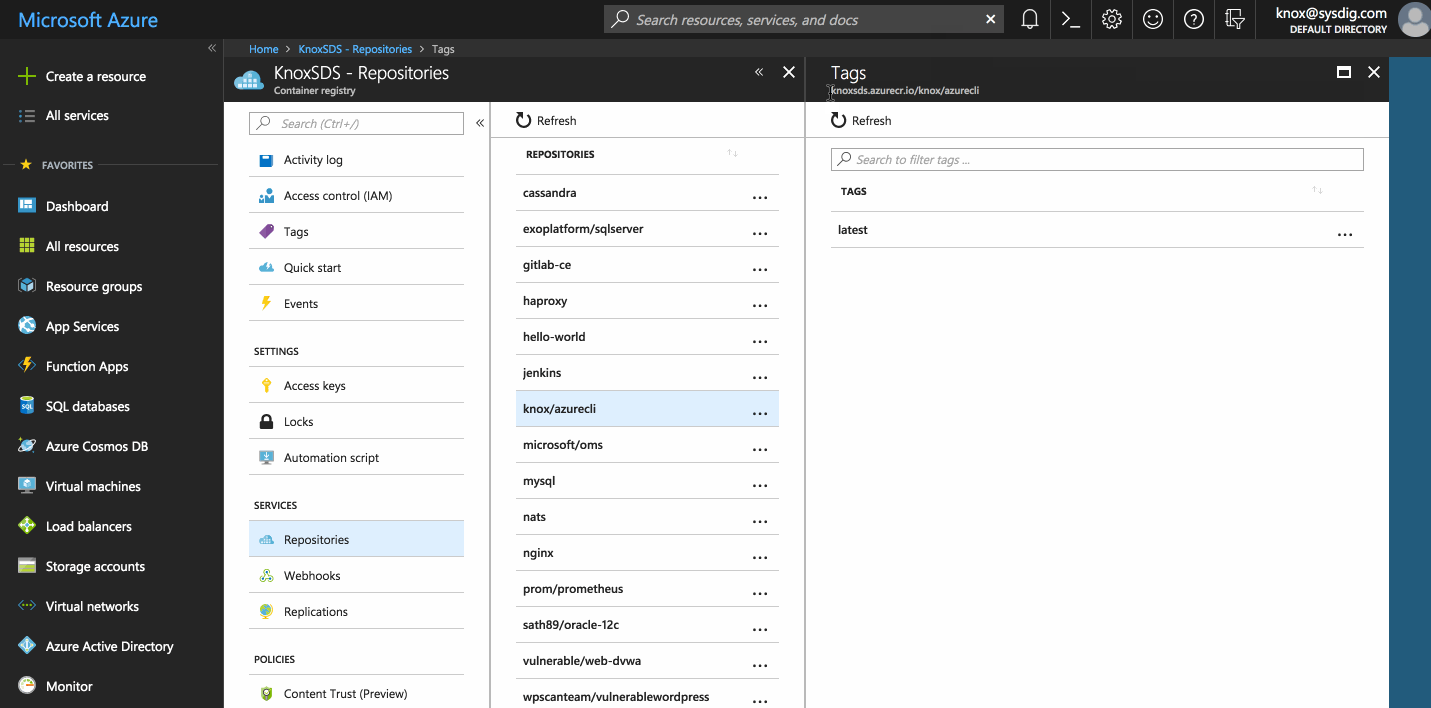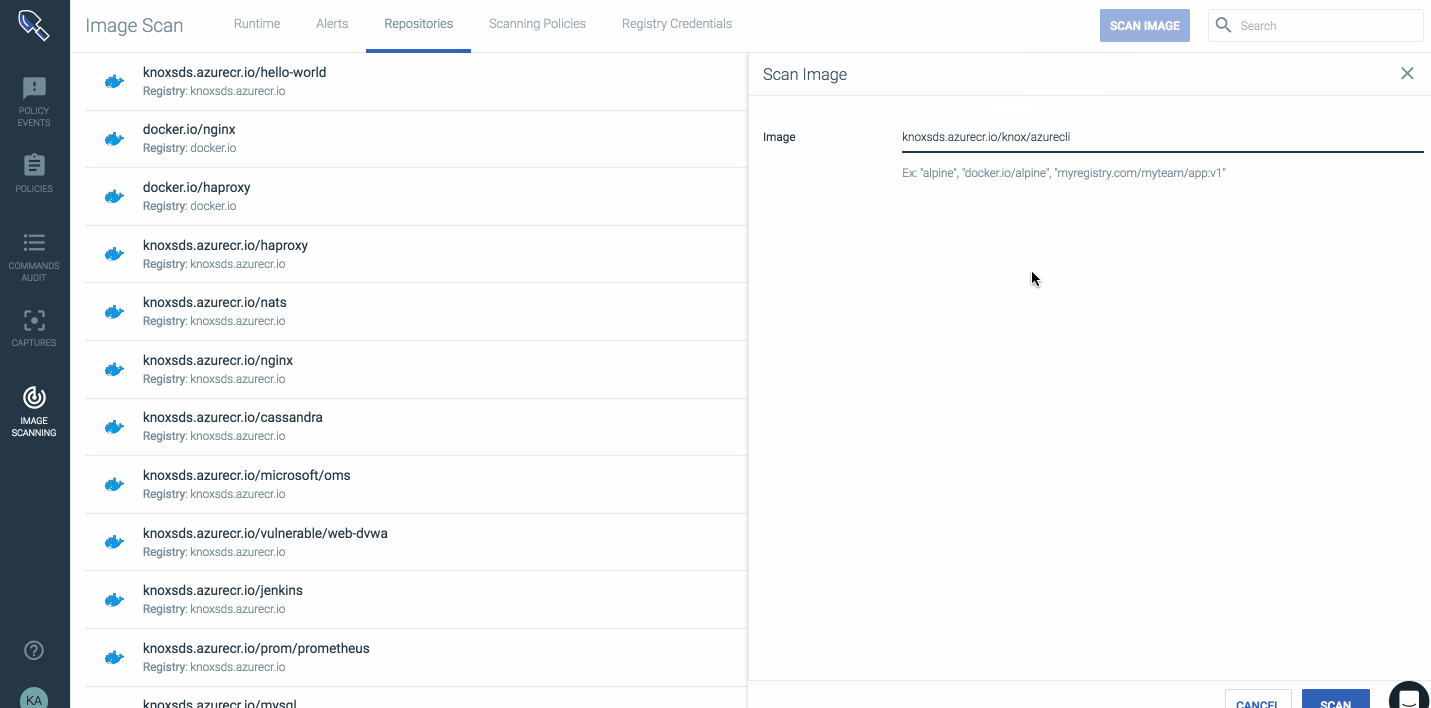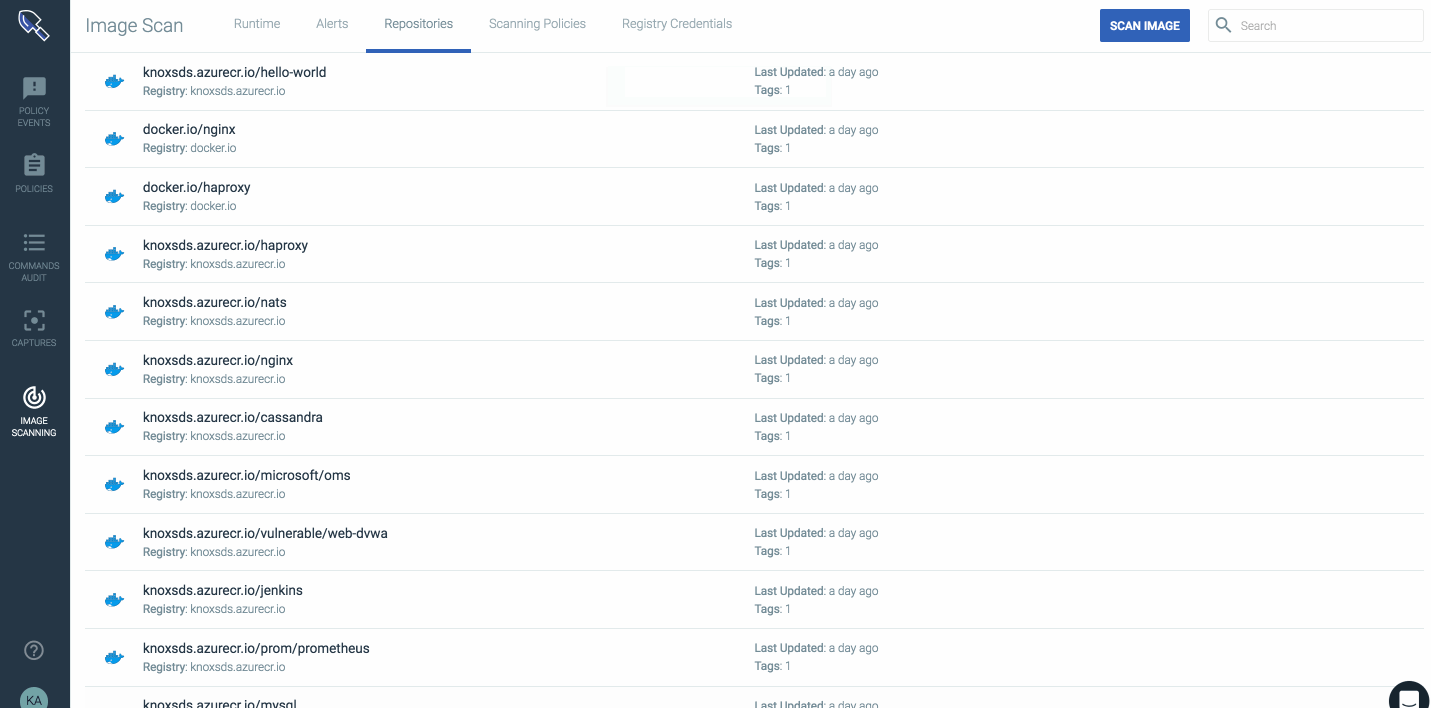
Once an image has been analyzed a report will be generated that has the outcome of the policy evaluation, all vulnerabilities discovered in OS packages, configuration files, and many other artifacts that are stored for audit and compliance reasons.
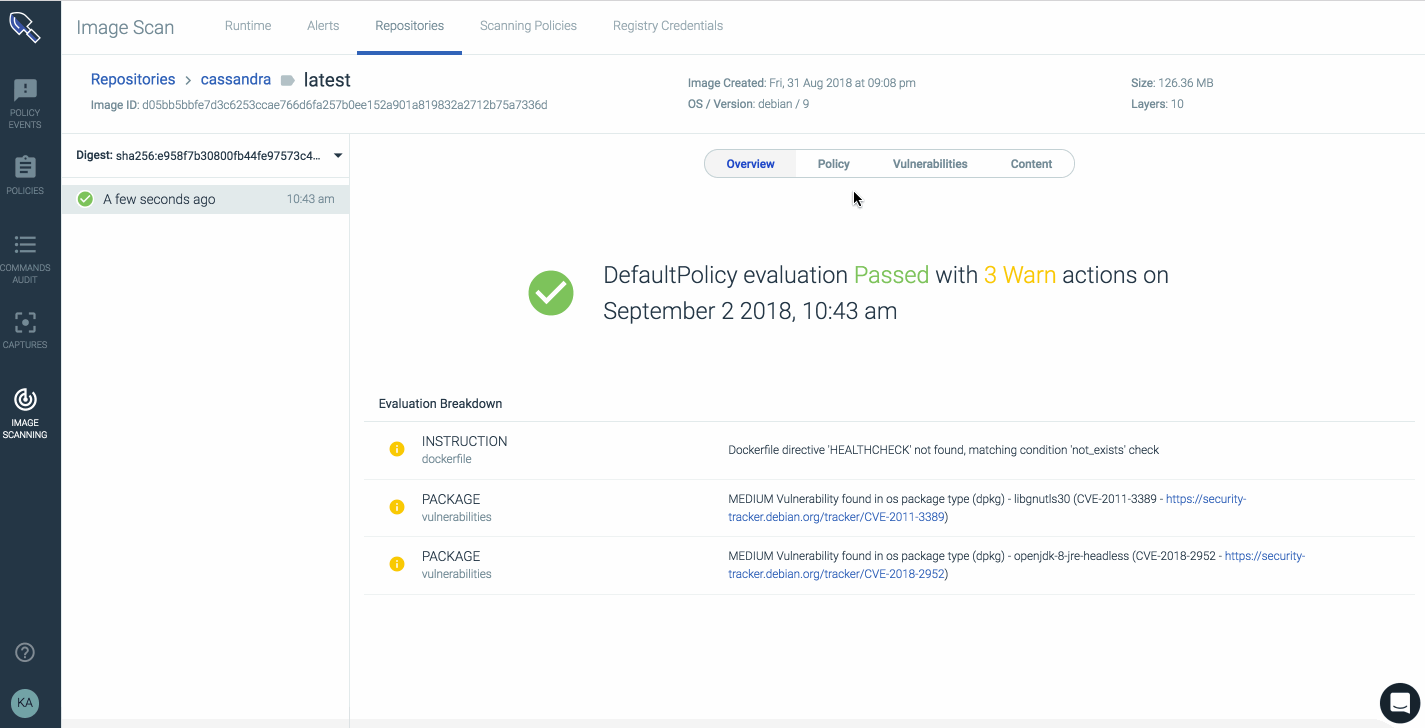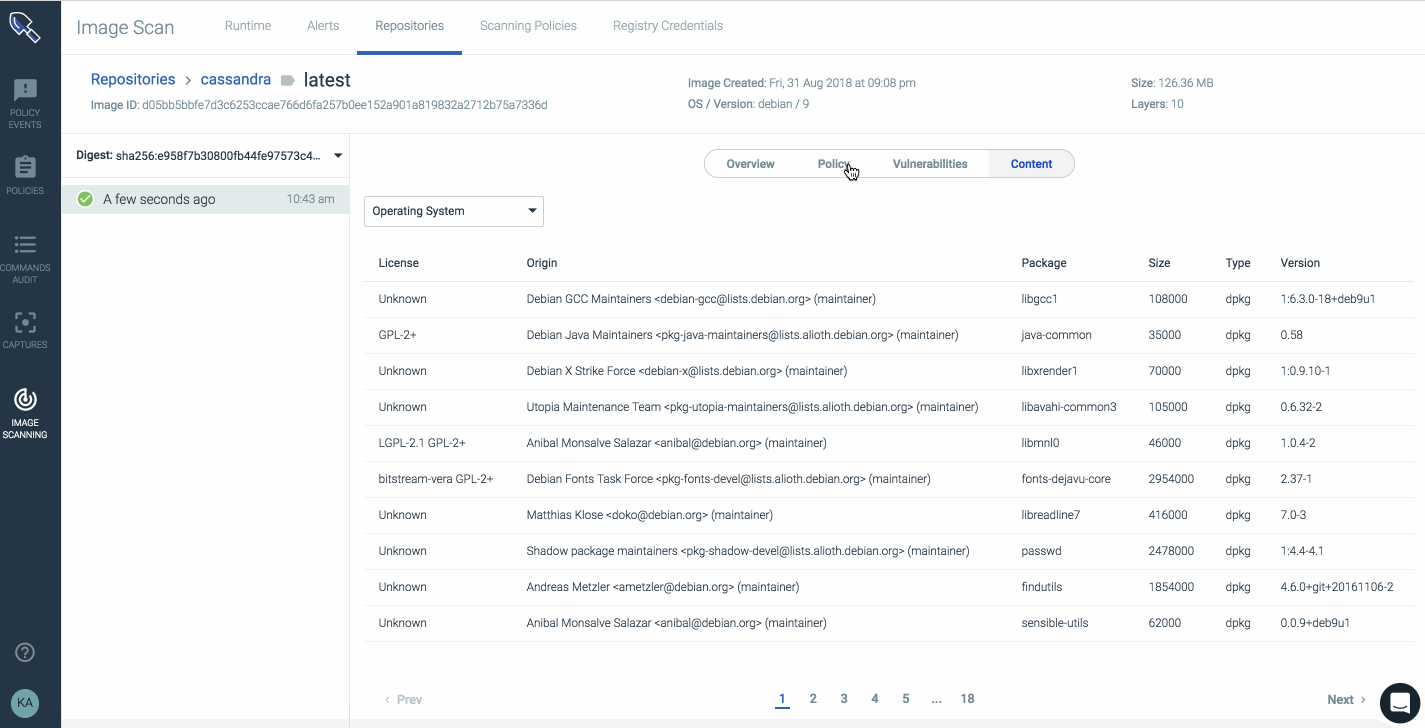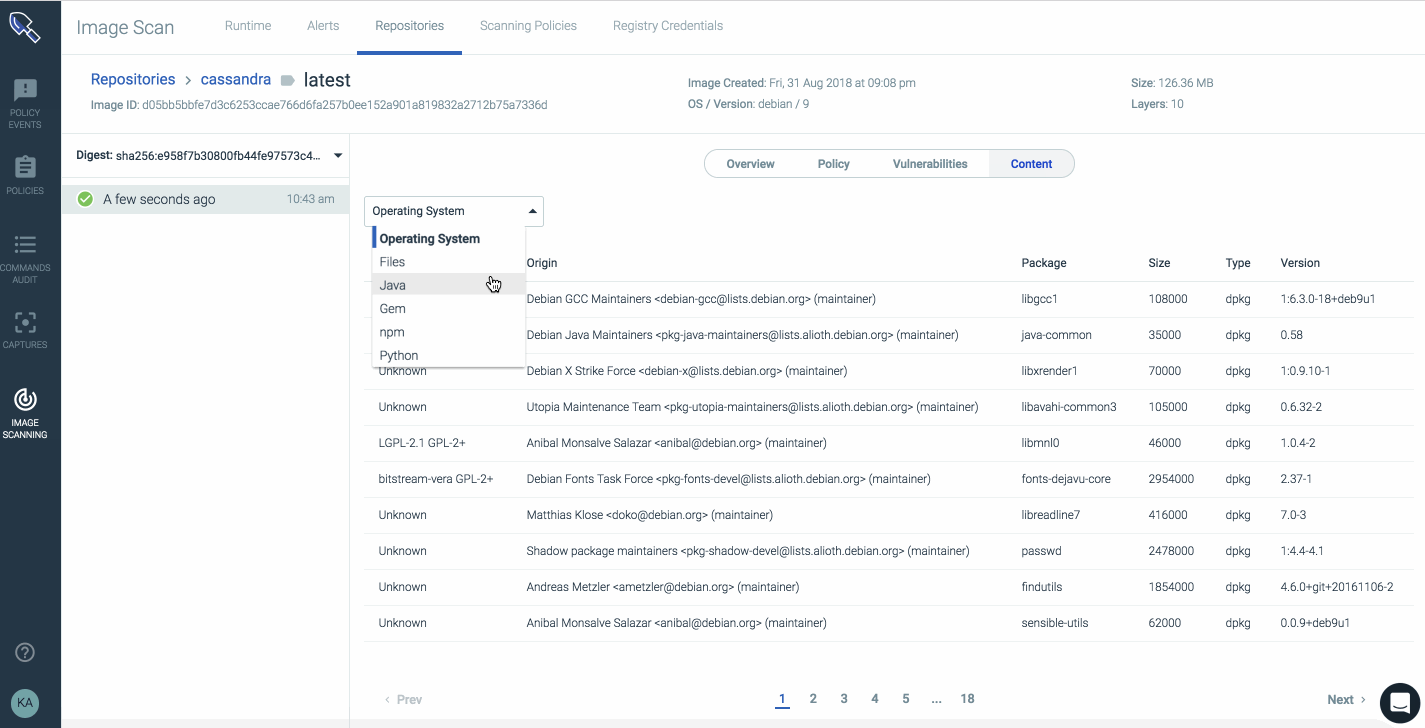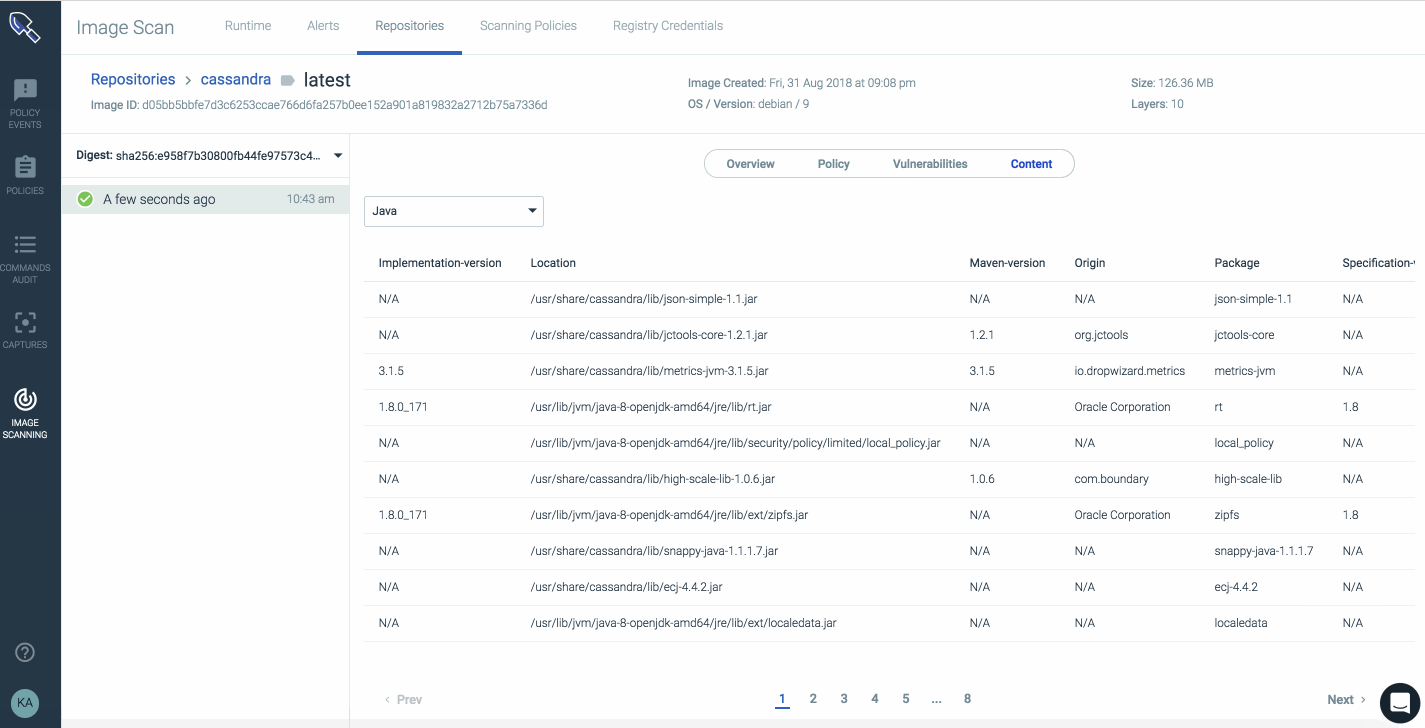
This report has details showing knoxsds.azurecr.io/cassandra:latest has passed the policy evaluation, including image metadata, vulnerabilities, and even JAR archives information included in the image.
Conclusion
Hopefully you can see how easy it is to get up and running with both Azure Container Registry and Sysdig Secure. If you'd like to see the integration in action sign up for a trial and follow our blog for more posts about securing containers on Azure.


