
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Crystal Morin is Cybersecurity Strategist at Sysdig. Steve Riley is Vice President and Field CTO at Netskope.
93% of last year's data breaches began with compromised credentials. Before the cloud, security perimeters were defined by physical walls and network boundaries, but in the cloud, that perimeter has all but dissolved.
Consider what happened in November 2023, when a cloud observability vendor found evidence of unauthorized access to its staging environment — an environment that housed customer data and PII. During the course of the investigation, it was discovered that the attacker used stolen credentials in connection with a single employee's account that gave them access and the ability to escalate privileges.
Unfortunately, such examples are plenty. Attackers' modus operandi will vary, but all of them rely on user or machine credentials to some extent — obtaining access to cloud applications or services, and then elevating their permissions or privileges to exfiltrate data.
Attacks involving misused or exploited identities can cost organizations millions of dollars. When attackers get past your proactive security defenses, you must find and stop them before they get too deep. To that end, Sysdig has prioritized identity security through announcements, like Cloud Identity Insights, and partnerships, like that with Netskope.
Netskope is a global secure access service edge (SASE) leader that enhances customers' preventive and reactive identity security with cross-domain identity management. With Sysdig and Netskope, security teams can minimize overly permissive and risky users, and work more efficiently. Compliance is simplified with automated prevention.
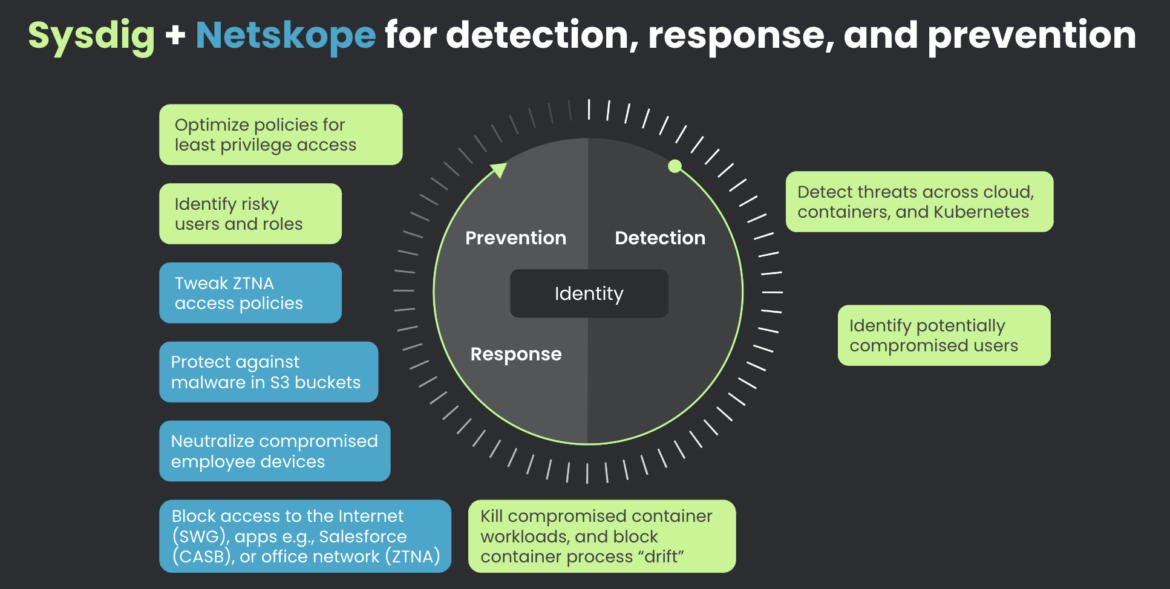
Sysdig detects, Netskope blocks
Security teams need to care about the cloud, regardless of whether or not their organization is cloud-first, cloud-native, or cloud-last; through modern supply chains, every organization touches the cloud in one way or another. This requirement is amplified by the increased number of lateral movement attacks from and to the cloud. Attackers can move across machines in the cloud, decoupling identity behavior from workload activity and making it difficult to reconstruct the full history of an attack even after initial detection. The explosion of non-human/machine identities adds even more complexity, as cloud infrastructure has expanded to encompass a vast array of identities and roles.
Leveraging runtime insights for your cloud environments is the best defense for the cloud, no matter how your organization sets up the cloud — public, private, on-prem, or hybrid. The Sysdig and Netskope partnership improves visibility across networks, clouds, and edge, accelerating threat detection and response to stop attacks in real time. It's as easy as creating a webhook in Sysdig to forward security event alerts and customizing real-time block/restrict rules in Netskope.
Through this partnership, Sysdig is extending the power of Netskope to the cloud to enhance identity-infused cloud detection and response (CDR) and also contain the breaches that move beyond the cloud:
- Prevent breaches from happening with the ability to tweak multiple zero trust network access (ZTNA) policies, letting you optimize your Least Permissive Policy. 98% of permissions granted go unused, but you can do better.
- Protect employees from using malware-laden S3 buckets or infected cloud assets.
- Detect potentially compromised users and non-human identities in seconds.
- Respond faster to risky users and roles by tracking and neutralizing compromised employee devices.
- Contain the threat and compromised user by blocking access to the internet, applications, or enterprise networks.
Real-life use case
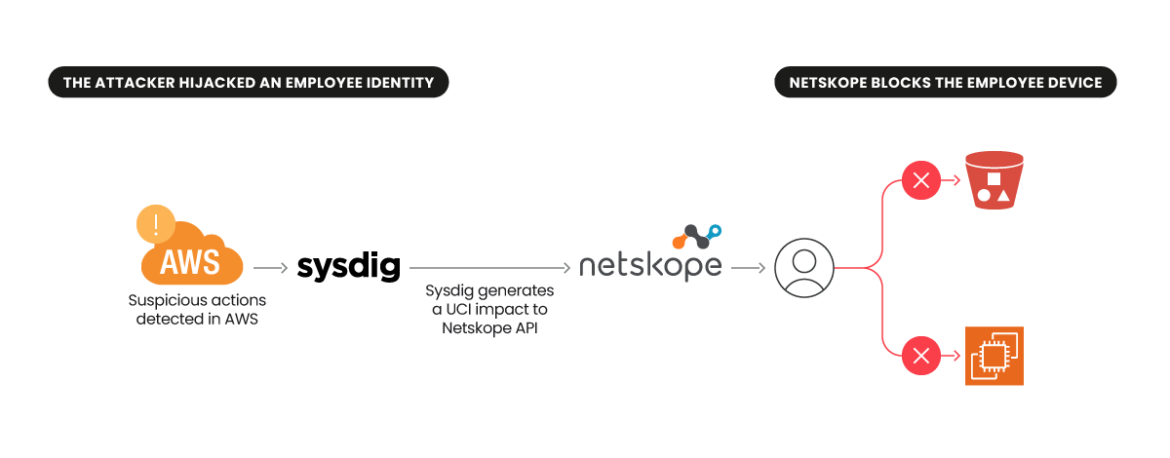
The story:
A malicious actor obtains access to a company's AWS console through a stolen identity purchased on the Dark Web. The identity belongs to a developer or network administrator who needs access to AWS for day-to-day actions. The actor, like many, is conscious of evading detection, and therefore navigates to CloudTrail logs and deletes their logged actions, erasing evidence of initial access.
- In Sysdig, a "CloudTrail Trail Deleted" event is considered high severity. The event context includes the account, region, user, risk tags, and more.
- Through the partnership integration, the event details are automatically translated into Netskope's user confidence index (UCI) based on the event type, severity, risk rating, and a combination of what Netskope already knows about the user's prior behavior, along with what Sysdig knows about the user's device risk.
- Netskope maintains and tracks all users' UCI scores within the user and entity behavior analytics (UEBA) dashboard. After receiving a Sysdig alert, the user's UCI score is updated (it decreases) in the Netskope UEBA.
- Anomalous user behaviors prompt a Netskope non-compliance action popup on the user's enterprise device in which the user must justify their actions or report a false positive. This response and correlated incident information is sent to the organization's Netskope administrators for review.
- Sysdig supports/enables investigations by tracking the actor's behaviors and movement, including the deleted CloudTrail logs. In the case of a false positive, Netskope administrators can restore the UCI.
- Following an investigation, security teams can tag an identity as "compromised" in Sysdig and include it in blocklists. Going forward, this triggers automated restrictions based on the predetermined parameters.
Conclusion
This integration increases the scope of the preventive actions customers can take beyond the cloud. When Sysdig detects suspicious activity in the cloud, you can block the associated identities and roles beyond the cloud utilizing Netskope. This proactively protects the organizational network, edge devices, and any SaaS applications that the account had been given access to in the past.
Visibility restrictions no longer exist because Sysdig and Netskope allow you to track an identity's lifecycle across physical or network devices and the cloud. With the known scale and speed of cloud attacks, this integration allows security teams to respond to potential threats in minutes, greatly reducing an attacker's opportunity to inflict pain.


