Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Sysdig continues to evolve this June with major advancements in AI-driven security insights, threat management, incident response, and securing cutting-edge AI workloads.
Sysdig Sage for Search
Why it matters:
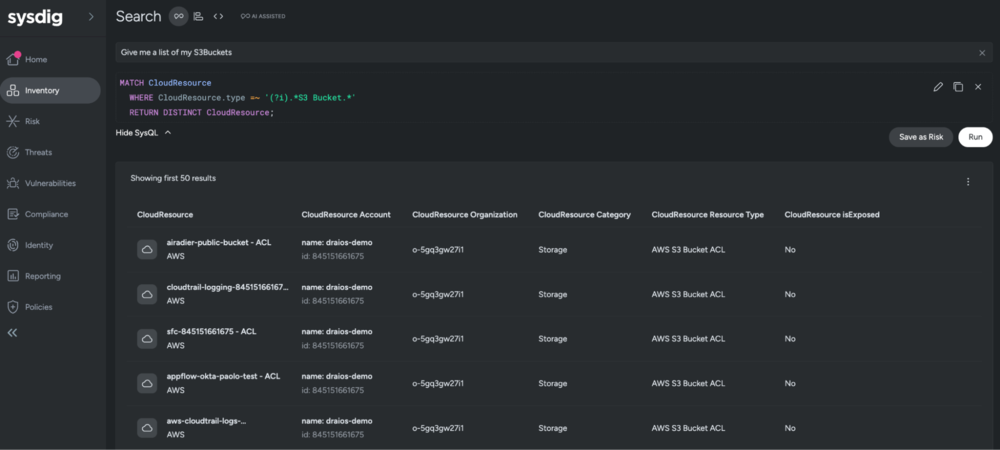
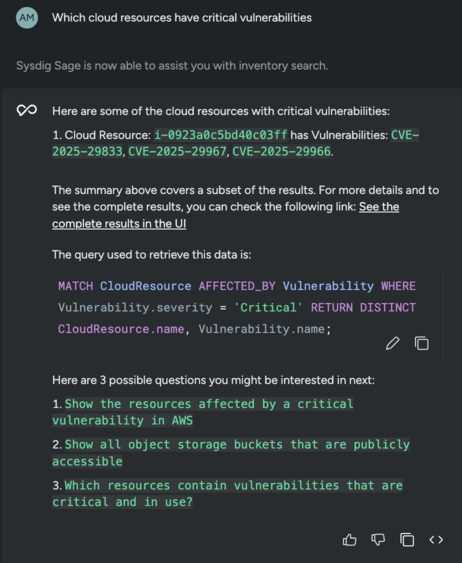
Sysdig Sage for Search brings AI-powered search capabilities to the Sysdig Secure platform, making it easier for teams to explore cloud resources, assets, and security posture findings across multi-cloud and Kubernetes environments without needing deep technical knowledge of query languages or cloud security frameworks. It includes two main components: a SysQL Translation feature that converts plain language questions, such as “What are my EC2 instances with critical vulnerabilities?”, into the required SysQL queries, and an Assistant that enhances search results with clear explanations, suggests follow-up questions, and provides guidance for refining queries.
Customer impact:
This feature simplifies security and DevOps workflows by enabling users to ask questions in plain language, eliminating the need for learning SysQL. It provides unified visibility across major cloud platforms (AWS, GCP, Azure), delivering key insights into vulnerabilities, misconfigurations, and compliance risks. Additionally, it aids in data exploration, revealing relationships between resources and events, and offers AI-powered assistance for deeper analysis and refined investigations.
Links:
Threats: Context-driven correlation with AI-powered insights
Why it matters:
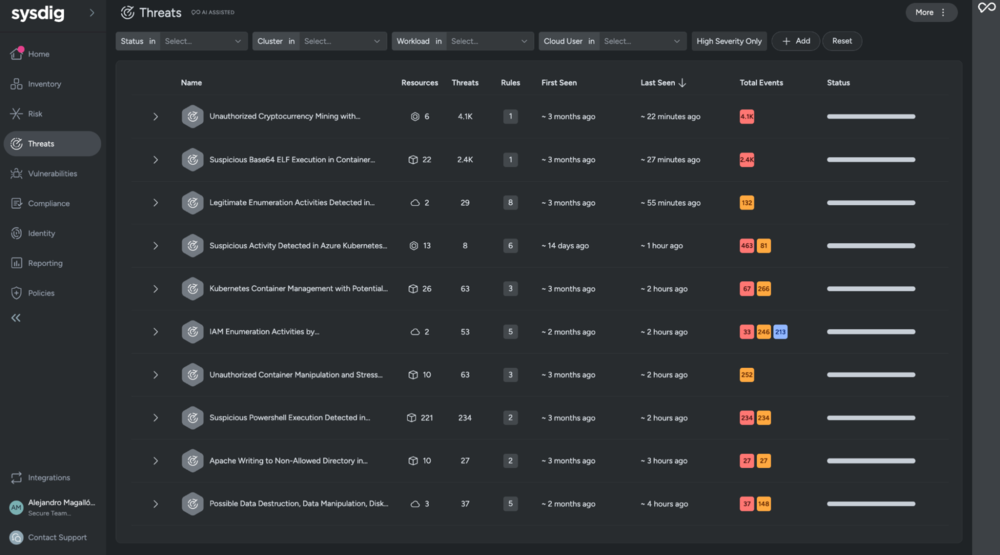
Sysdig’s new “Threats” capability changes how security incidents are managed. It aggregates multiple related security signals (based on shared entities like Kubernetes workloads or cloud identities, attacker behavior, and time proximity) into a single, actionable security incident. Key aspects of this capability include the population of Threats in the graph database, enabling customers to correlate them with other findings, such as identifying if a CVE has a related Threat indicating active exploitation. Additionally, Threat Management leverages Sysdig Sage™, our generative AI security analyst, to enrich threats with easy-to-understand summaries and high-fidelity context, provided Sysdig Sage is enabled.
Customer impact:
The introduction of Threats leads to reduced alert fatigue as the consolidation of related events into a single “Threat” minimizes noise and helps teams focus. It enables faster decision-making because AI-enriched summaries and contextual information provide better situational awareness. Investigative efficiency is enhanced as analysts can quickly grasp the scope of an incident. Overall, teams can manage alerts more efficiently with streamlined workflows that include inline actions like status changes, rule tuning, investigations, and response actions, all from a unified interface.
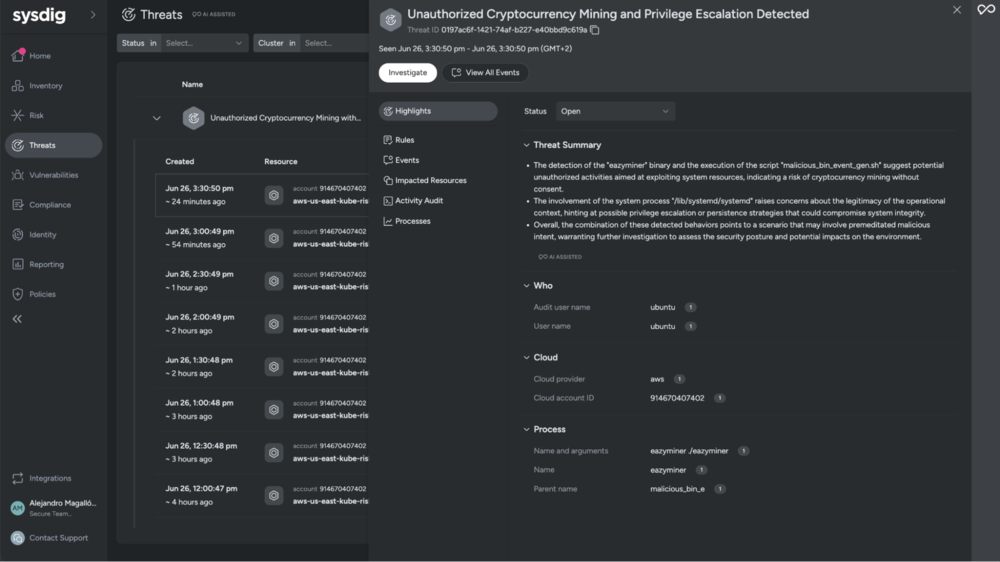
Links:
Response actions: Manually respond to threats with ease
Why it matters:
Responding effectively to events often requires quick action. Sysdig now empowers security teams with the ability to manually execute critical Response Actions directly from an event within the platform. This complements existing automated policy actions and investigation tools by providing immediate, reactive capabilities without needing to pre-configure every response scenario. Available manual actions include container kill, stop, or pause, process kill, file acquisition for forensic analysis, and file quarantine. These actions can be reverted where applicable, offering flexibility during an investigation.
Customer impact:
Security teams gain significant advantages, including the ability for immediate containment by taking direct action to isolate compromised containers or quarantining malicious files. Forensic capabilities are enhanced through the ability to acquire files for investigation. This feature provides an essential reactive toolkit, enabling security teams to react swiftly to evolving threats based on real-time assessment. Furthermore, Response Actions can be integrated into broader security workflows via public APIs, allowing for coordination with existing SOAR platforms.
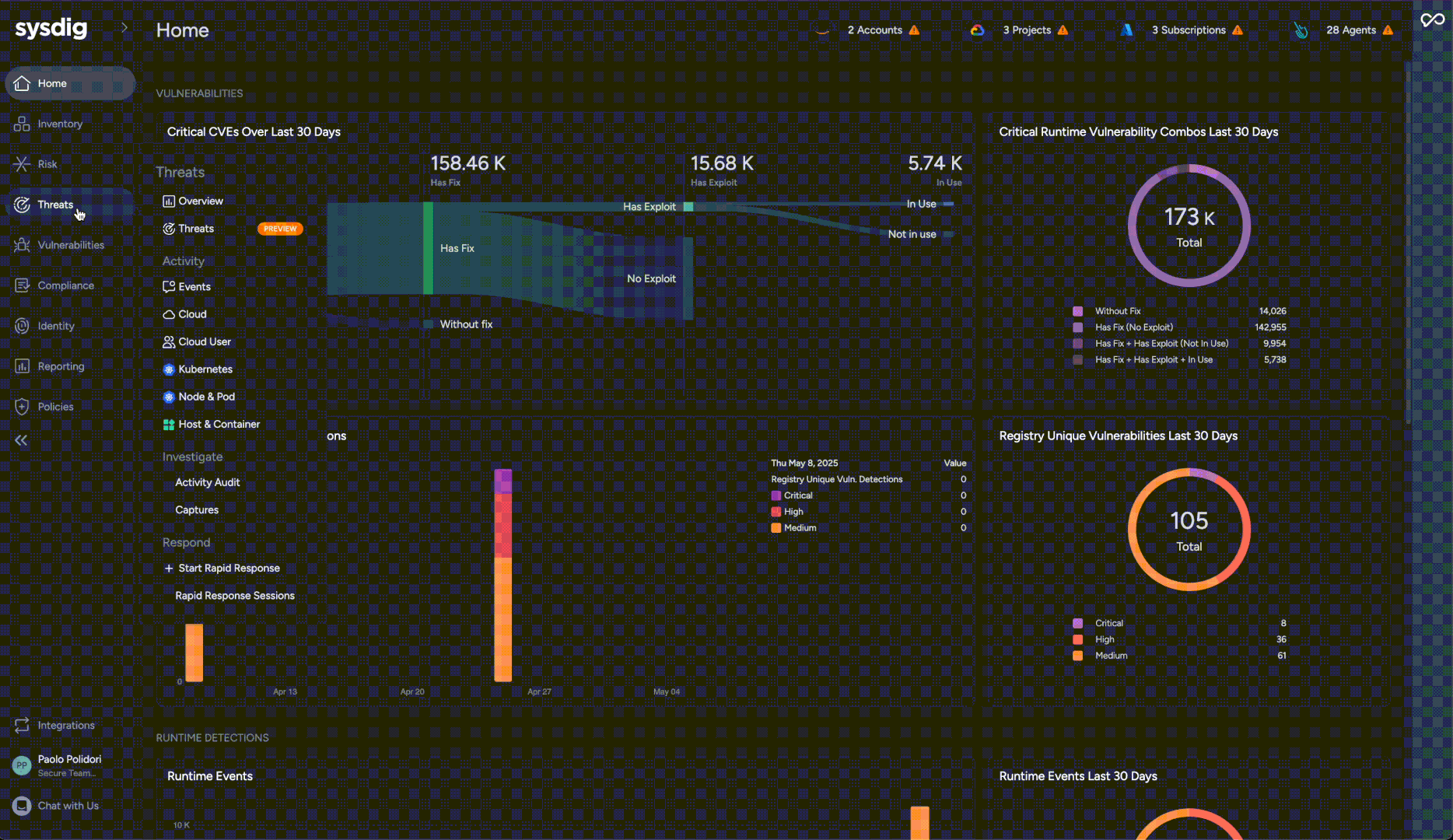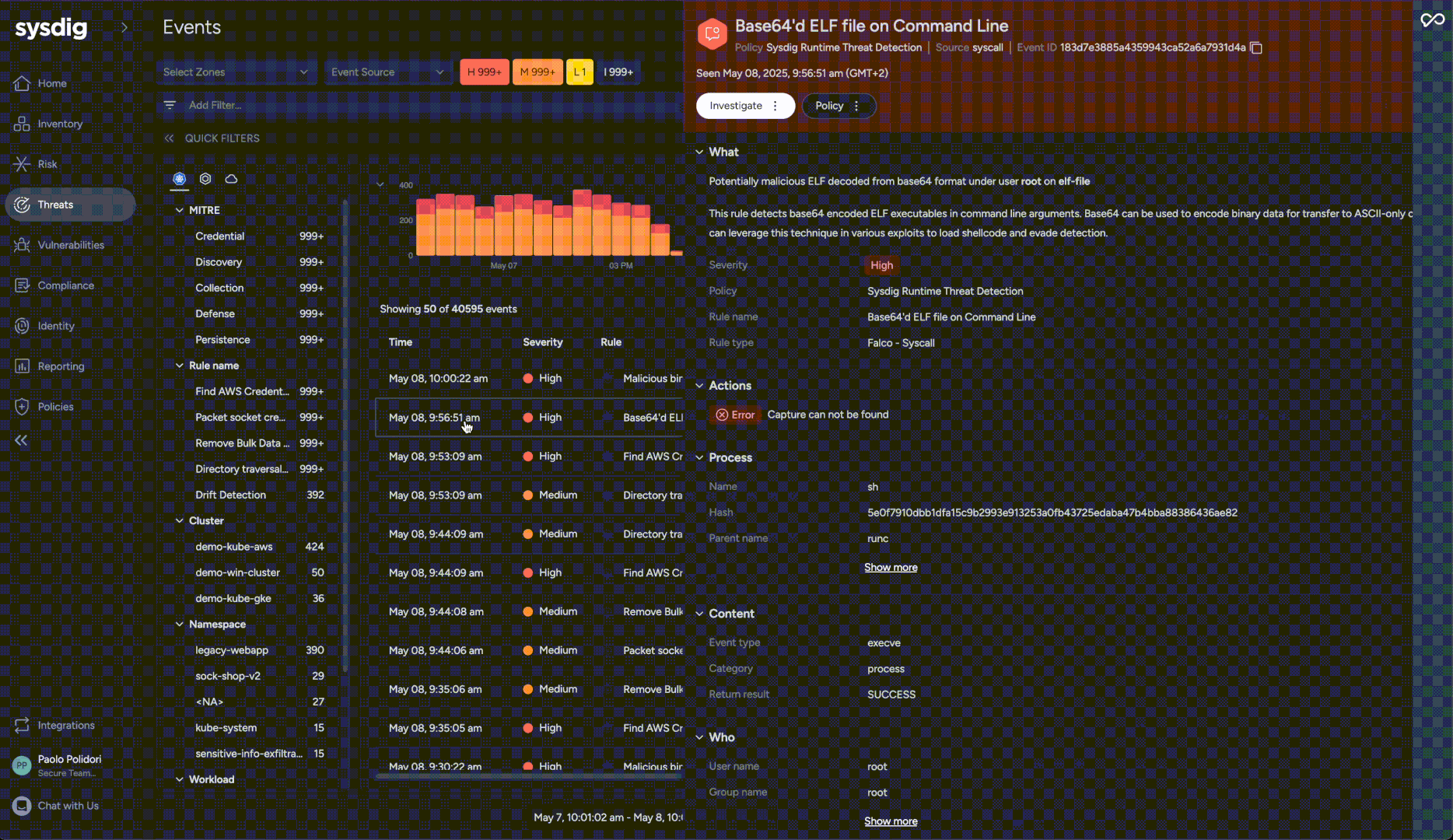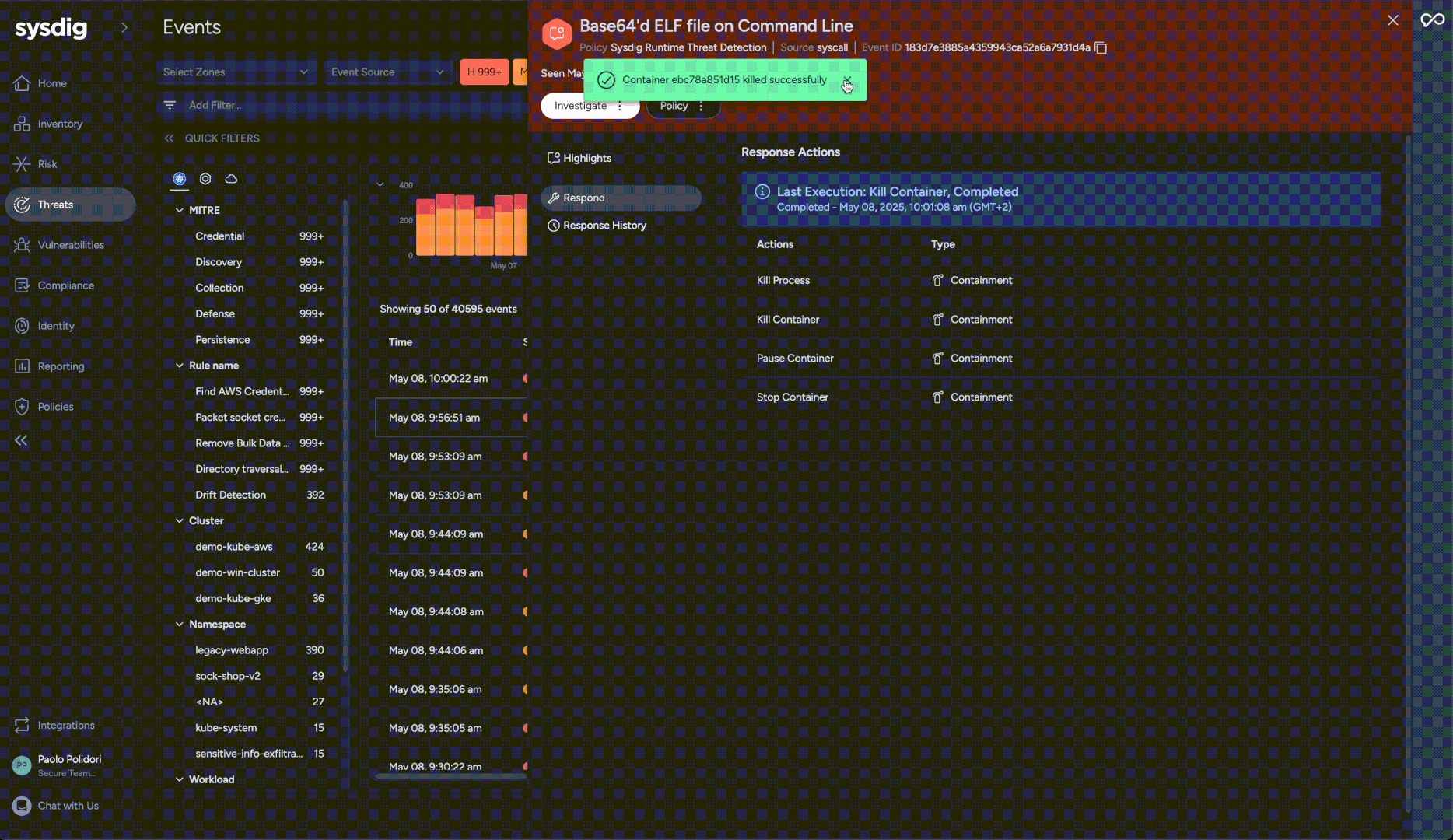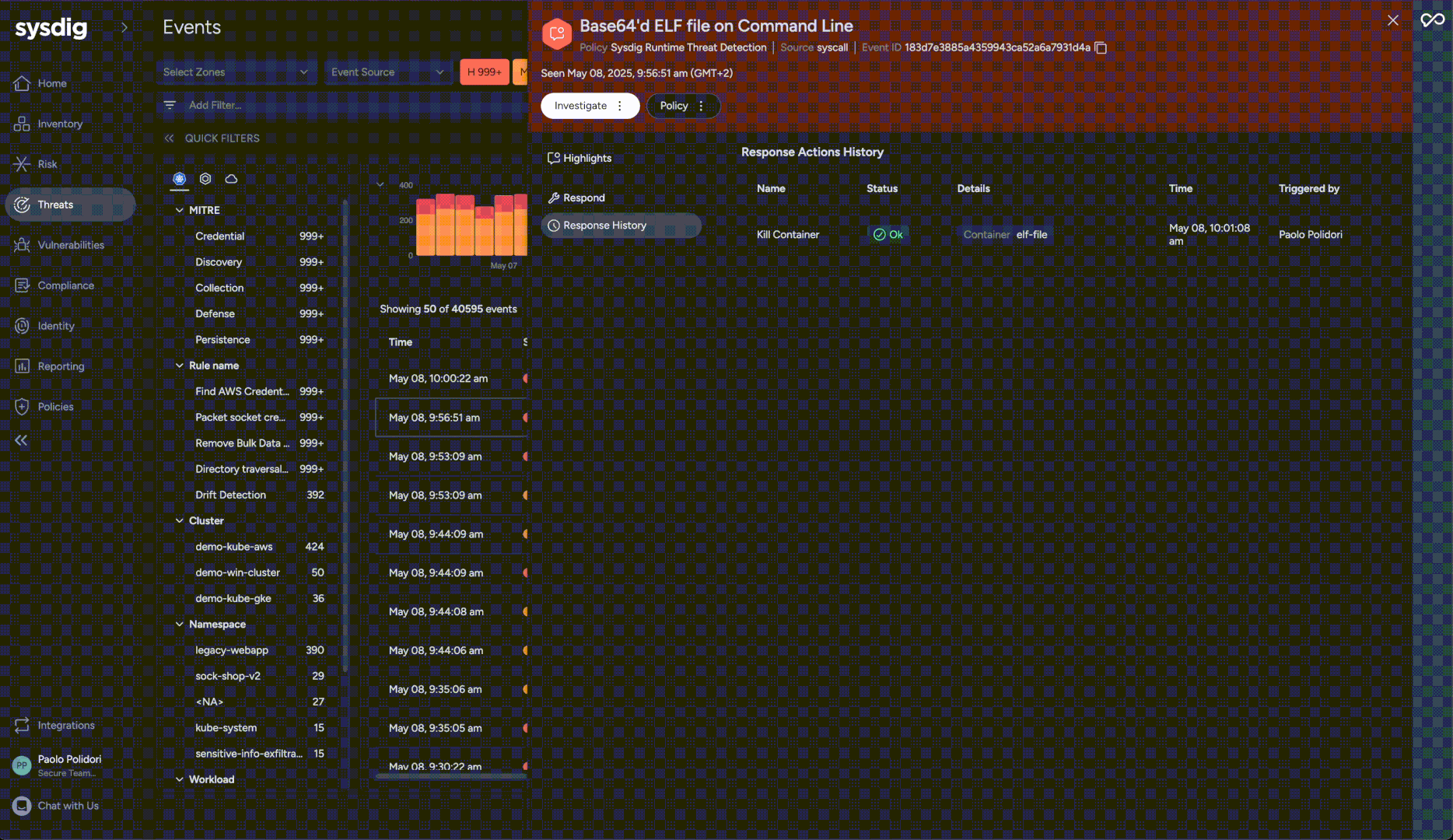
Links:
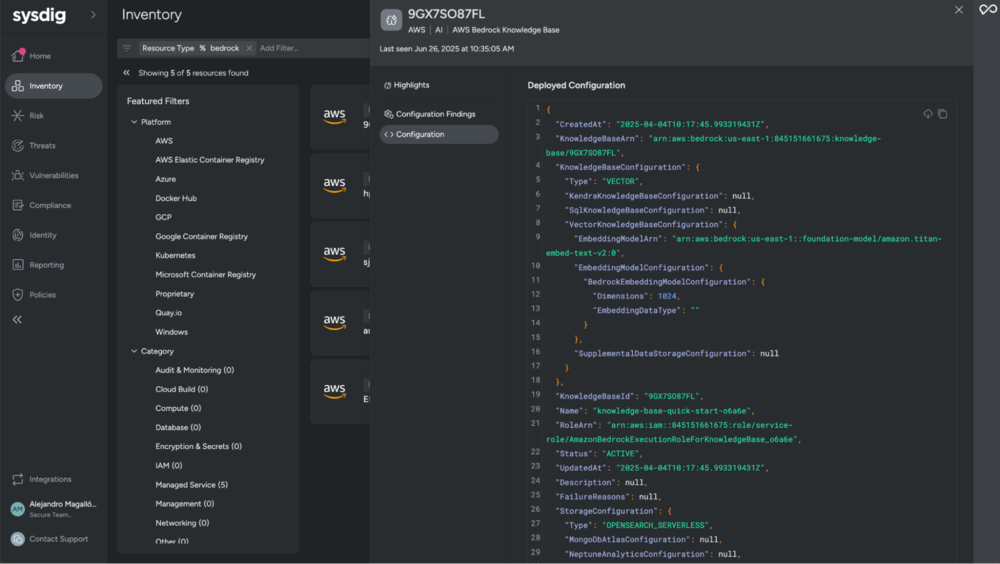
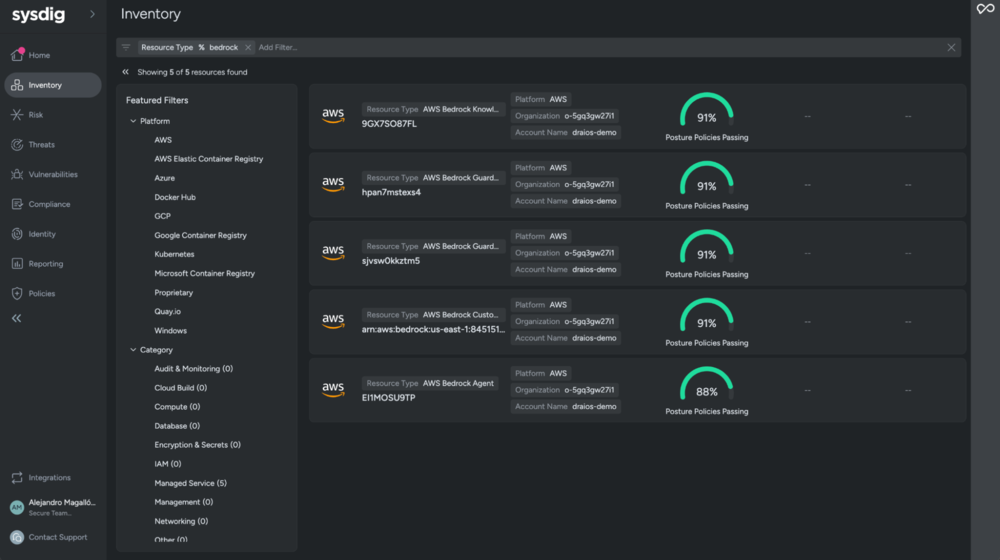
CSPM support for Amazon Bedrock: Secure your AI workloads
Why it matters:
Amazon Bedrock is rapidly becoming a core building block for enterprise AI strategies, making robust security and posture management for its resources essential. Sysdig Secure now closes a significant CSPM gap by introducing support for Amazon Bedrock, allowing organizations to extend their existing security practices to this critical AI service. Sysdig Secure can now discover Amazon Bedrock resources, including Custom Models, Agents, and Knowledge Bases, across connected AWS accounts. It also allows teams to define and evaluate custom posture controls tailored specifically to these Bedrock-based AI models, agents, and knowledge bases.
Customer impact:
This new capability enables proactive AI security, allowing customers to gain crucial visibility and control over generative AI workloads to consistently enforce security best practices. It facilitates custom governance for AI, empowering organizations to create and apply security policies that align with both internal corporate standards and external regulatory requirements. Ultimately, this empowers customers to confidently scale their generative AI initiatives, especially those in regulated industries, knowing that security and compliance are built-in.
Links:
Create a Custom Control with Rego
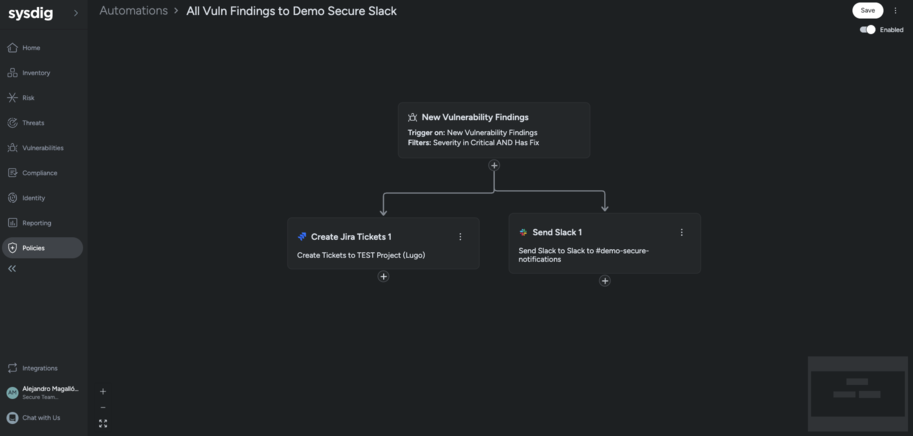
Automations: New triggers for risks, vulnerabilities, and runtime events
Why it matters:
The new Automations capability enables security teams to define response workflows for critical events. Users can now trigger actions based on vulnerability findings, risk exceptions, and runtime events, including automatic Jira ticket creation. Triggers can be tailored using filters such as zone, severity, status, and labels, allowing for highly customized alert routing and remediation workflows.
Customer impact:
Key actions can now be automated, empowering teams to reduce manual effort and accelerate incident response with this new feature. It helps contain threats, escalate findings, and enforce governance policies more efficiently across complex environments. Upcoming enhancements will further extend these capabilities with support for threat-based triggers and automated response actions, enabling end-to-end reactive security workflows.