Anyone who works in the software security industry knows that attackers have a multitude of tools and techniques at their disposal. Additionally, attackers have plenty of time to experiment, use trial-and-error techniques, and figure out how to break into systems.
Understanding how attackers work and what techniques they use should remain a top priority for web administrators. For the benefit of the security teams who need to understand the threat landscape, those techniques should be cataloged, documented, and proven in practical scenarios.
The MITRE ATT&CK framework, developed by MITRE in 2013, is the answer to that problem. It is a comprehensive knowledge base of tactics and techniques for everyone to adopt. By leveraging MITRE methodologies and mitigation actions, security teams can gain an upper hand in this long-standing battle to protect critical systems.
This article explores the MITRE ATT&CK framework, the ATT&CK Matrix, its main benefits, and how to use it to strengthen the security posture of organizations.
The ATT&CK Matrix breakdown
The ATT&CK framework is a curated knowledge base of attacks and techniques used by threat actors to conduct illegitimate business. Put differently, the framework tells you what attackers are doing when they try to attack an organization.
You can trust this framework for assessing your systems’ security considerations because it’s populated based on certified and publicly available threat intelligence data and research conducted by vetted governing bodies. Each technique has been independently tested in separate lab environments.
The ATT&CK framework reference guide is formulated as a matrix, where each column represents a tactic category and each row within a column represents a technique. A technique shows a specific way in which an adversary may try to achieve an objective.
Each technique can also be broken down into one or more sub-techniques that represent the variations of a technique or details about a particular attack. The actual step-by-step guide to implementing a technique is documented in a series of procedures and actions. Finally, mitigations and detections show techniques for detecting and preventing attacks before they take place.
Currently, the ATT&CK matrix has three variants: one for Enterprise, one for Mobile Platforms (Android and iOS), and one for Industrial Control System (ICS) Networks. The following image shows the ATT&CK Matrix for Enterprise:
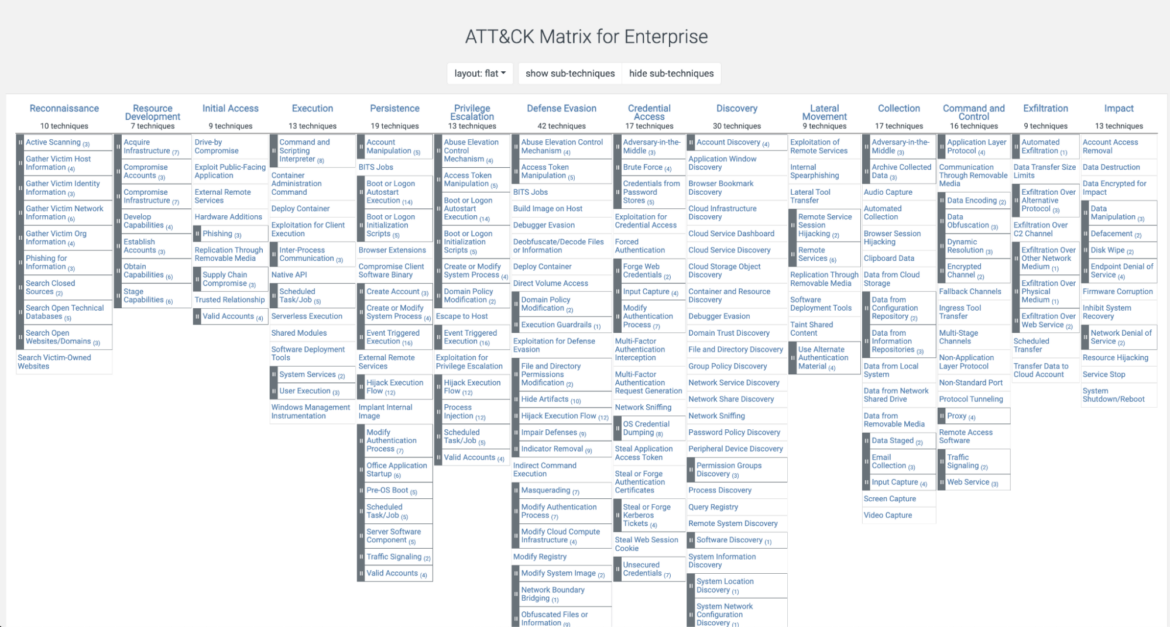
As of 2023, there are 193 techniques and 401 sub-techniques listed. It is updated and corrected on a regular basis.
Quick summary of the tactics
There are currently 14 tactics cataloged in the Enterprise Matrix. Let’s take a brief look at them. Each column is sorted logically starting from the left with intelligence gathering. As we move to the right, we acquire techniques for exfiltrating information:
- Reconnaissance: Here, adversaries use information-gathering techniques that can be used for further operations. Having all the initial information they can get from an organization helps them plan a suitable course of action based on the assessed target.
- Resource development: Adversaries work to acquire relevant resources, accounts, VMs, or domains that will be used to infiltrate and attack the target. The main consideration here for the attackers is to cover their tracks and make it impossible to detect their source of information or their real identities.
- Initial access: At this stage, they catalog specific techniques for gaining initial entry into the organization’s network. These techniques can only be used for bait-and-switch scenarios so that adversaries can record the initial reaction time. This includes phishing attacks.
- Execution: Adversaries perform active attacks to install malicious code, exploits, or malware. Their main intent is to establish remote access and persistent connections. The result of a successful spear-phishing campaign, for example, is a downloaded executable that an adversary leverages to gain a foothold.
- Persistence: Once the adversaries gain a foothold in the system, they need to maintain it. These techniques represent actions that try to prevent security controls from working correctly or attaching multiple facets for continuous re-entry. For example, backdoors are included in this category.
- Privilege escalation: Adversaries try to gain root or elevated privileges to perform malicious attacks without compromisation. This includes gaining sudo access or exploring known issues to elevate privileges.
- Defense evasion: Techniques related to avoiding detection or mitigation measures are included here. (Although we listed these techniques here in this order, they are often performed earlier in the process.) This stage also includes attacks that hide processes, accounts, and logs.
- Credential access: Adversaries attempt to steal or extract application-specific secrets, passwords, or credentials that can be used to access encrypted data. Examples include attaching keyloggers and MITM proxies.
- Discovery: Adversaries utilize techniques to gain a wider understanding of the system and the network topology. This information can be used later for attempting more sinister actions if necessary.
- Lateral movement: Adversaries use techniques to secretly navigate to other systems from their foothold toward their intended goal. SSH hijacking and “pass the hash” attacks are included here.
- Collection: Having reached their target, the attackers gather information related to their objective. This includes capturing input data or API calls.
- Command and Control: Adversaries create various communication channels to transfer data back to base without triggering alerts. This includes encoding and encryption data techniques.
- Exfiltration: Attackers use techniques to steal data from a network. This includes transferring data through various mediums (web, usb, bluetooth, etc.).
- Impact: Depending on the final objectives of the attackers, they can try to destroy information that impacts the integrity and availability of the system. This includes disk wiping and Denial of Service attacks.
Examples of techniques for the aforementioned tactics
Let’s explore some interesting techniques that the ATT&CK framework includes and explain how to interpret them in practice.
Take a look at the Use Alternate Authentication Material technique under Defense Evasion:
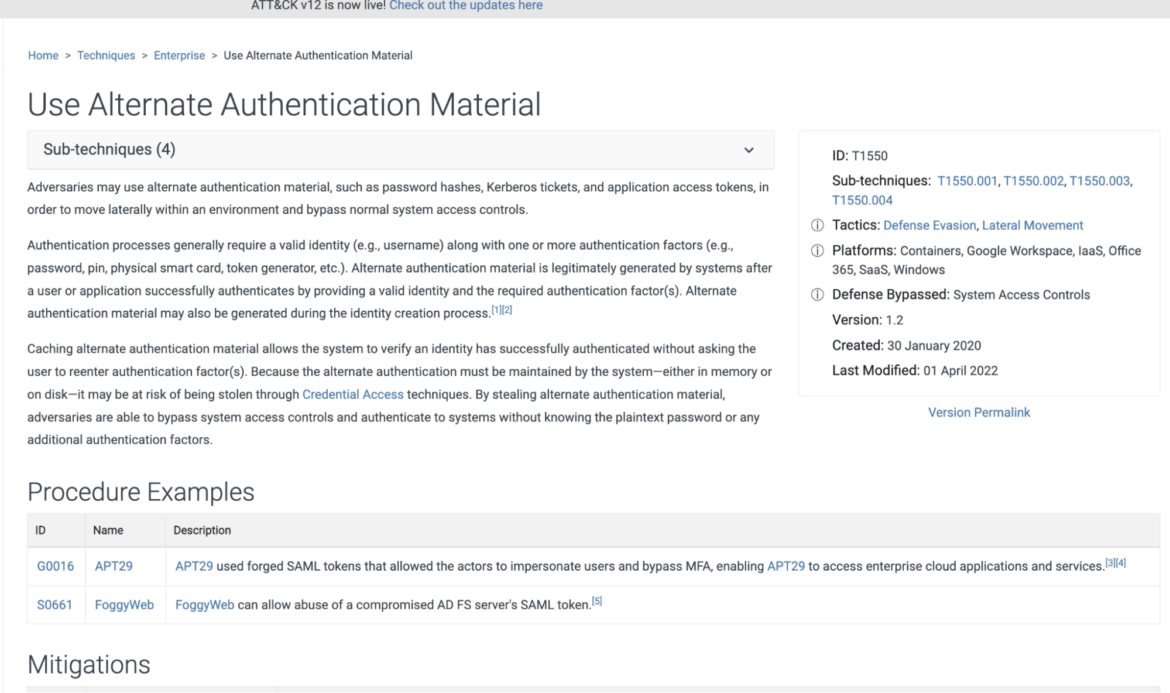
For each technique, the framework includes:
- A description of the technique.
- Any related sub-techniques.
- Mitigation tactics.
- Detection tactics.
- Related metadata for indexing purposes.
- References from real incidents.
The above technique describes a very common scenario for using existing authentication tokens to access relevant systems. If attackers can capture traffic and see the tokens, they can use them to bypass authentication without having to provide passwords or other credentials.
If you follow one of the procedure links from Account Access, you will eventually be able to see some of the software that the attackers used. In the case of Advanced Persistent Threat Actor APT28, for example, they used a custom ADVSTORESHELL trojan program to open a backdoor:
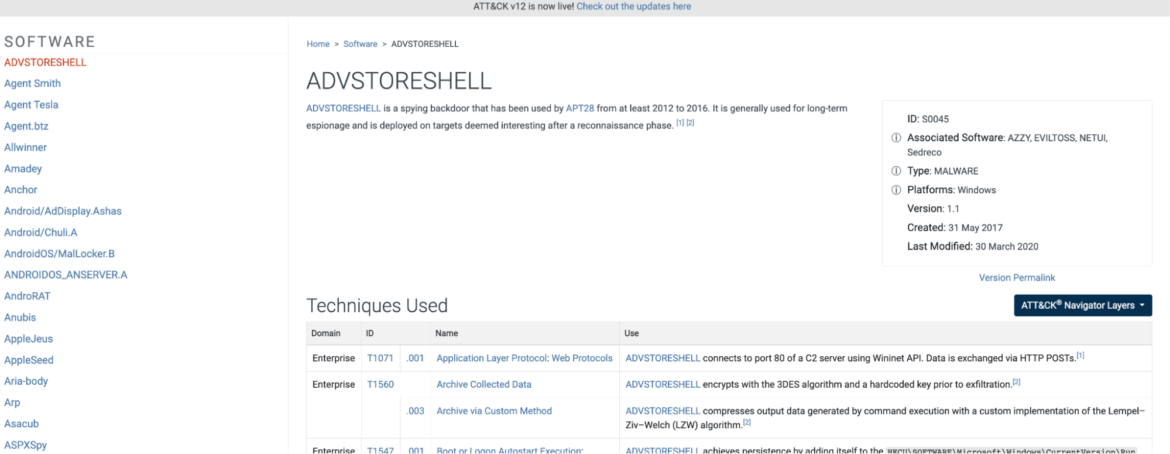
Although instructions for using ADVSTORESHELL are not included in the reference, it is helpful for security teams to know which tools the threat actors have in their arsenals.
Examples of Procedures, Mitigations, and Detections
A nice addition to this framework is the collection of related detection and mitigation techniques for each attack pattern. For example, the following are some mitigation techniques that security teams can use to prevent the risk of alternate authentication material attacks:
- Encrypt sensitive information: Service-to-service communication should be encrypted so that MITM attacks cannot sniff access tokens. See the related Mitigation.
- Use monitoring to detect suspicious traffic: Monitoring the usage of web credentials in unusual places should trigger a warning and prompt for verification procedures. For example, an attacker might try to use a token for accessing systems beyond their scope. In such cases, the request should be flagged. You should provide mechanisms to detect patterns that do not fit the organization’s baseline. See the related Detection.
The framework provides a comprehensive breakdown of techniques, tools, and mitigation procedures. However, further evaluation is needed to translate them into actionable items that fit the particular organization. Next, we’ll explain how to use the MITRE ATT&CK framework in practice.
Using the Framework
Now you have a better understanding of the MITRE ATT&CK framework, but do you know how you would use it? How would adopting this framework help your organization strengthen its cyber threat intelligence?
To answer those questions, you need to do a few things. The first step is to assess the threat model of your organization’s systems and answer some crucial questions. For example, what are the potential threats and vulnerabilities? What are the weak points? Maximizing the usage of the MITRE ATT&CK framework involves taking proactive steps to strengthen the security alertness of people and tools.
Once this is done, the last step is to identify specific items in the ATT&CK Matrix that can be used for security gap analysis, alerting, and cyber threat evasion. Then, the framework can be used in the following ways:
Attack Matrix for common use cases
For common use cases, you can apply some general security steps mentioned in the ATT&CK Matrix. Some useful actions could be:
- Get familiar with your adversary’s tools and processes, especially if you provide employees with laptops and devices. Review the following list of adversary software and make sure that your antivirus and firewall software can detect it.
- Periodically review security policies and educate employees about phishing and social engineering attacks so that they can protect the house.
- Enforce strict rotation of keys and secrets.
- Enforce strict software and hardware updates so that critical vulnerabilities are patched.
- Map and integrate specific techniques with cybersecurity tools so that they can detect and prevent any unauthorized attempts.
- Focus on implementing multiple mitigations, as many attacks can be thwarted by common security techniques. For example, the use of industry-standard antivirus/antimalware software and account policies can help prevent attackers from establishing persistence.
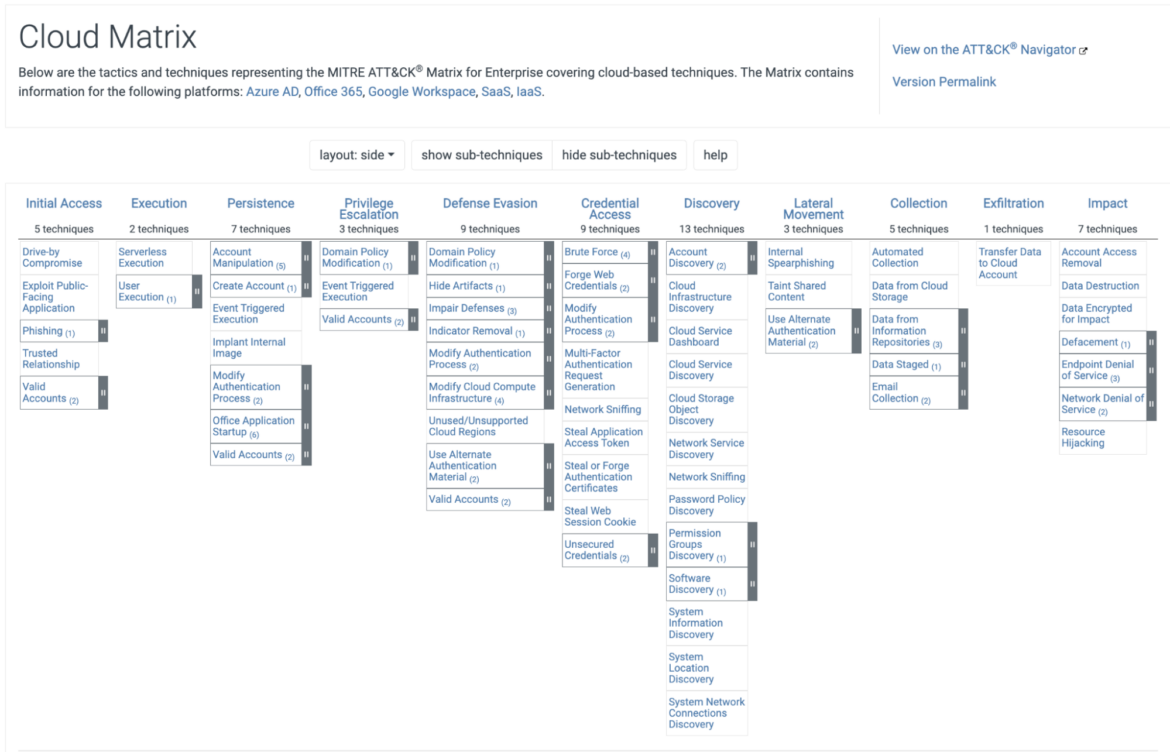
Attack Matrix for Cloud environments
The Attack Matrix for Enterprise has a subsection specifically for cloud environments. The Cloud Matrix is useful for covering cloud-based techniques like IaaS, Google Workspaces, and Azure AD.
Attack Matrix for other use cases
There are other use cases where the Attack matrix. If you are operating mobile applications, you can use the Mobile Matrix. For ICS, you want to look into the ICS Matrix.
Note that the matrix configuration is only for convenience and makes it easier for anyone to see and prioritize the most common attacks for cloud infrastructure. Security teams still have to review, assess, and create reliable security controls that are aligned with their policies.
For example, if you take a look at the Serverless Execution technique, you can read the description, review mitigation and detection actions, and read related references. If you deploy serverless applications as part of the security team and you use the content from this ATT&CK Matrix, you will want to assess how serverless applications are used in the organization, create a threat model, and implement relevant mitigations.
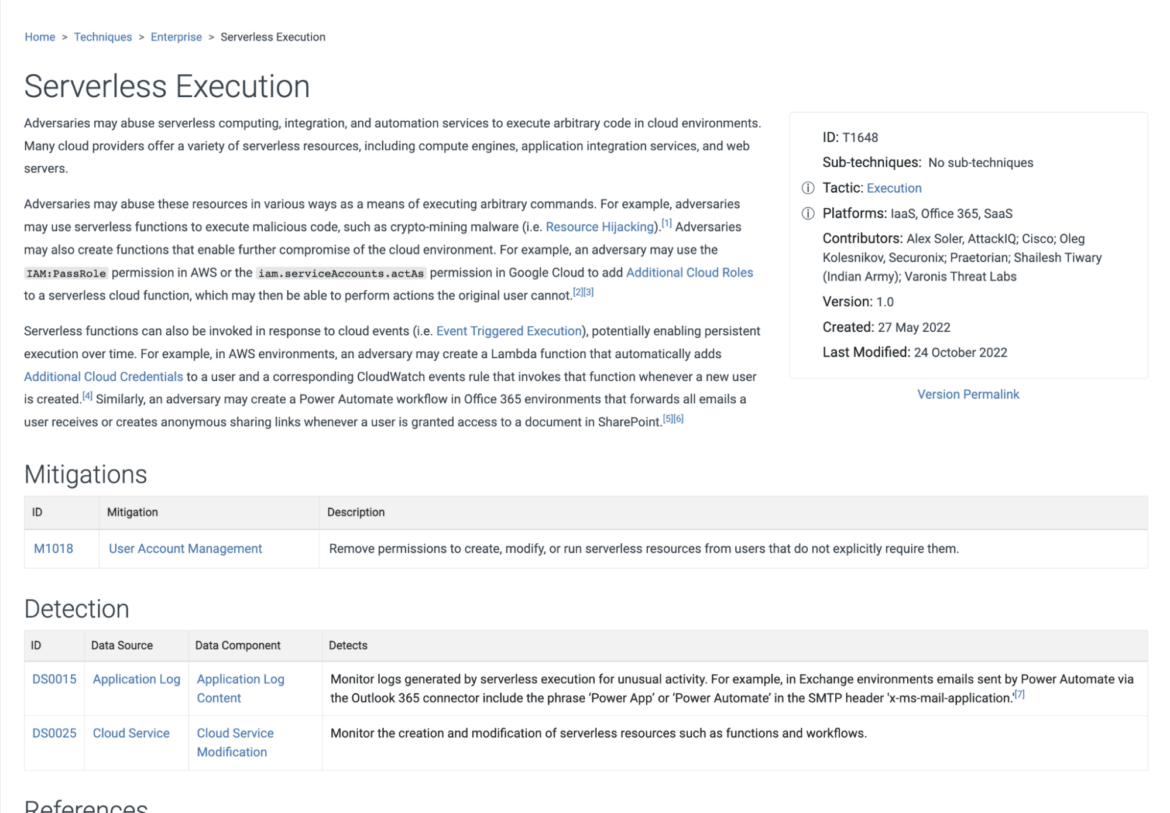
Thus, this ATT&CK Matrix acts as a good reference for further actions since it points out the dangers of running serverless applications in the cloud. It’s up to you to map this into actionable mitigation techniques according to your individual use case. Such actions might include:
- Updating your Lambda security context and IAM permissions to prevent privilege escalation.
- Placing limits on Lambda functions.
- Allowing only specific custom runtimes.
Evaluating the ATT&CK Matrix in this way helps save valuable time when triaging and implementing security controls, giving security teams valuable insights and methodologies. You can dig in more in a practical example here.
Conclusion
Securing all aspects of an organization is a very daunting task. Attackers are often driven by strong financial and existential incentives or operate as state actors, which gives them an early advantage. As attacks become more sophisticated, they increase the chance of inflicting severe security incidents. Enterprises can adopt the information and counter measures derived from the MITRE ATT&CK framework to automate all relevant mitigation steps and ensure the safety of their systems.

