What is CIEM (Cloud Infrastructure Entitlement Management)?
Cloud environments are too complex for traditional IAM solutions to effectively protect accounts and permissions. CIEM enables organizations to solve tricky cloud identity challenges.
CIEM definition
Cloud infrastructure entitlement management (CIEM) grants, resolves, enforces, or revokes the access rights or privileges of all identities, human or non-human, in a cloud system. CIEM tools limit what identities can do or what they can access, with the objective of mitigating the risks resulting from misconfigured permissions levels.
Excessive permissions is when a user account is granted access to sensitive data beyond the scope of the role or administrator-level permissions, providing full system access instead of more limited rights.
Consider the following questions about whether your organizations needs CIEM to manage cloud identities and access:
- Does your system have overpowered identities that are not used anymore?
- Are the overpowered identities ones that are habitual in your cloud environment?
- Are you sure about what privileges you give to third parties in your system?
- Is there impostor code among us?
Traditional identity and access management (IAM) struggles to provide visibility into complex cloud environments and discover elevated permissions and privileges in cloud accounts. A CIEM solution helps identify where cloud risk exists as a result of human and non-human identities with elevated privileges and excessive permissions.
CIEM can be deployed as a discrete cloud security solution, but is also commonly part of cloud-native application protection platforms (CNAPP) alongside cloud workload protection platform (CWPP), cloud security posture management (CSPM), vulnerability management, and threat detection capabilities.
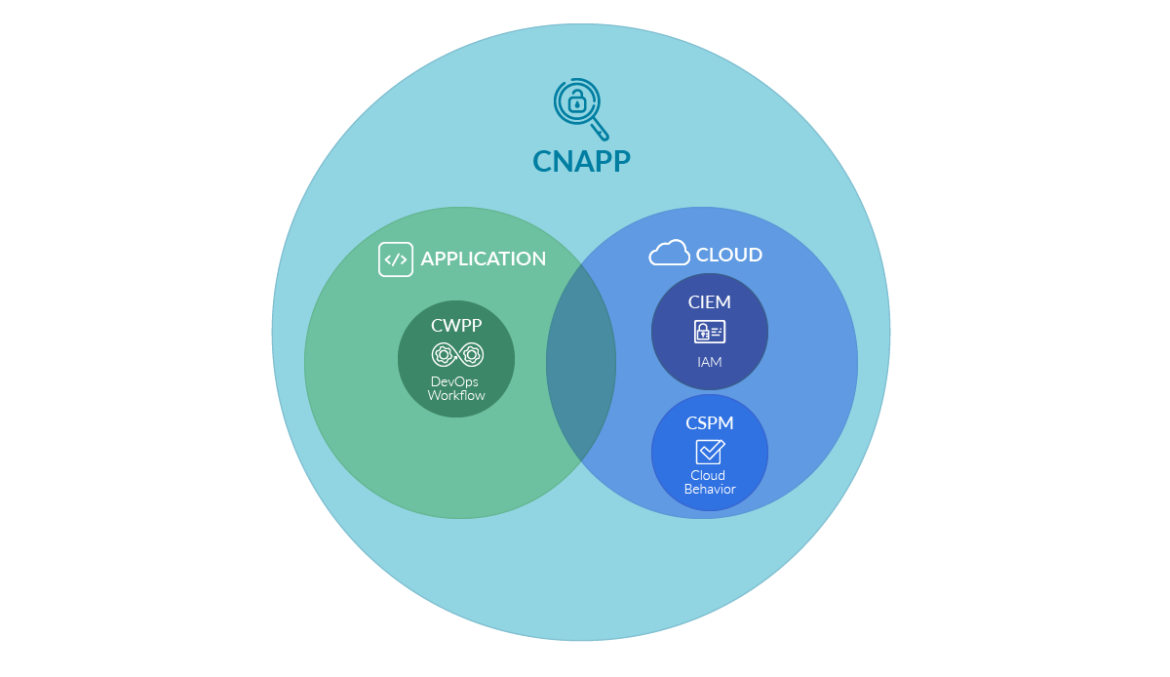
Whether you are a veteran CISO or new to managing privileges in the cloud, stick with us and we'll show you why it's crucial to use CIEM.
Why is CIEM important?
CIEM is important because traditional IAM solutions are designed for static infrastructure, but cloud infrastructure includes dynamic and ephemeral environments, like containers and virtual machines. CIEM is specifically designed to address identity management in complex cloud environments.
Imagine that you have a cloud environment where you have many human and non-human identities with access to sensitive resources, such as data, services, etc.
Some of these cloud resources need limited access, requiring that you grant privileges to identities so only those with permissions can access those resources.
This can be fully solved with an IAM service that can help you manage these privileges for your cloud environment identities. But hold on, what if…
- For no reason, one of your identities is working as it shouldn't?
- Something or someone is doing what it wasn't supposed to?
- There is actually a reason and you weren't aware of it?
IAM can manage privileges, but can’t always check and determine whether they are too broad or overpowered. CIEM can review permissions and modify them as necessary.
Challenges of CIEM
In order to ensure that identities and permissions are correct, CIEM solutions can use different approaches for an issue. There are different CIEM challenges and approaches:
- Inactive identities and super identities: A cloud environment can have unused identities with compromising privileges or access rights for the environment, which sometimes can be unlimited to the cloud resources.
- Overpowered active identities: Some active identities can have higher permissions than they should if assigned to accounts without considering the principle of least privilege (POLP).
- Cross-account access: In some situations, it could be necessary to create accounts (cross-account or IAM roles) that allow identities or third parties to access different resources of the cloud (for development, testing, production, etc.). Misconfigured or overpowered account privileges could compromise the entire infrastructure.
- Machine identities with unauthorized access: A non-human identity is designed to perform a controlled sequence of actions, unless it's changed. If the behavior or results of the non-human identity change unexpectedly, someone could have altered the internal design or is injecting outside actions.
Benefits of using CIEM
Based on the above challenges, CIEM is a solution that brings several benefits together in a centralized way, independent of whether your cloud is a single environment or multi-cloud one:
- Compliance: CIEM will monitor all your cloud or multi-cloud identities and check if each one complies with its given privileges, as well as if these privileges meet compliance requirements and standards.
- Detection and remediation: CIEM will detect any unexpected behaviors that involve misconfigured or bypassed privileges and remediate them automatically.
- Governance: CIEM will monitor your identities along your different cloud environments and verify that these comply with defined governance.
- Visibility: CIEM allows you to view all of your identities and privileges in one place, whether from one cloud or different ones.
How does CIEM work?
CIEM is a solution that brings all identity information and executions together in a centralized place, it is also a solution based on a continuous "match, check, and remediation" method and the CIEM lifecycle.
What does the "match, check, and remediation" method mean? In order to monitor your cloud, the CIEM solution performs the following:
- Initially, the CIEM solution will request two types of information from the IAM service:
- Cloud identities: Anything that can access your cloud services or resources. These can be human (user, administrator, developer) or non-human (software, external device) identities.
- Cloud entitlements: Once the CIEM has the identity, it will get its entitlements — that means the tasks and the access privileges that the identity is supposed to have.
- With identity and the entitlements data, CIEM will verify the behavior and actions of all identities and contrast them against the entitlements.
- If there is suspicious activity that bypasses any of the given privileges, CIEM will remediate it by removing all the privileges, deactivating the identity, or lowering its privileges in the IAM service.
- Your CIEM tool will repeat the same steps continuously.
CIEM lifecycle
CIEM also works based on least-privileged access to manage identities' private and public cloud permissions. This helps to minimize and mitigate any possible risk of excessive privilege, such as cloud leaks, data breaches, or insider threats.
POLP is a concept in cybersecurity that states you should limit user access rights to only what is strictly necessary to do the job.
To scale enforcement of POLP across the cloud, CIEM solutions follow the CIEM lifecycle:
- Account and entitlement discovery: A CIEM solution must continuously search and list every existing entitlement in the cloud to properly apply least privilege.
- Cross-cloud entitlement correlation: In general, cloud environments are multi-cloud, so the solution must provide consistent mechanics for entitlement policies across the different clouds.
- Entitlement visualization: The solution must allow the visualization of the different entitlements of the cloud and its accesses, or filtering through specific entitlement or access type.
- Entitlement optimization: The solution must also, besides searching for new entitlements, regulate entitlement privileges and remove those that can be excessive, reducing the attack surface.
- Entitlement protection: The solution could detect when an entitlement's access has changed and create an alert for the possibility of a threat (e.g., privilege escalation). It should also provide optionally configurable rulesets to define the entitlement guardrails.
- Entitlement detection: The solution must also have the ability to detect any suspicious activity at the moment of monitoring the entitlements (for searching, optimizing, etc).
- Entitlement remediation: The solution must support multiple means of remediation.
Does my organization need CIEM?
Consider the following CIEM use cases to help you decide if your organizations needs CIEM:
- You could use CIEM if:
- You want a sandbox environment for developing apps and assets and testing functionalities.
- You have a cloud environment where there are a huge number of identities.
- You have a multi-cloud environment and you want to monitor every identity in a single place.
- You want automated management and monitoring of privileges, although there are few identities.
- You want to apply compliance standards.
- You wouldn't use CIEM if:
- You have a cloud environment where there aren't too many identities, and it isn't very crowded. Traditional IAM still works well here.
- You have a private cloud environment strictly for your own use.
How to choose a CIEM solution
Once you have decided if you really need a CIEM solution, now you have to compare different solutions to choose which fits better to your cloud. There isn't any standardized checklist or guideline that will tell you which solution will be better or worse.
A good approach is taking the CIEM lifecycle and studying which requirements your cloud environment has and which of them could be fulfilled with a CIEM solution. Then, you can select different solutions and verify which solutions are stronger or weaker for your particular identity and access needs in the cloud.
Take control of cloud identities with Sysdig
Too many permissions on too many accounts increases the risk of compromised accounts. About 98% of granted cloud permissions aren’t used, but over-permissioned accounts create risk, especially in complex cloud environments.
With Sysdig CIEM, organizations can analyze identity activity patterns to discover risk and compromised accounts in real time. Track key IAM risks, such as inactive accounts or elevated permissions, and implement least-privileged access to better protect cloud resources.
%201.svg)


