What is Wireshark?
Understanding the performance and health of an organization’s network is critical to ensure business continuity. By using a network protocol analyzer, like Wireshark, you can easily discover network problems and security threats.
Wireshark definition
Wireshark, formerly known as Ethereal, is the world’s leading network protocol analyzer, used by network administrators, security professionals, and developers to capture, inspect, and troubleshoot network traffic in real time.
Originally created by Gerald Combs in 1998 and continually built and maintained since then by over 1,000 contributors, Wireshark is a free open source tool that has become an essential resource for diagnosing network issues, detecting security vulnerabilities, and understanding how applications communicate across networks.
Combs, who is the director of open source at Sysdig, is the lead maintainer of Wireshark, but it also features an active community of developers and users who contribute to it. Wireshark is available for Linux, Windows, and macOS and is included in some Linux distributions like Kali Linux.
Wireshark key features
Some key features of Wireshark include the following:
- Packet capture and analysis: Capture live traffic from networks or analyze saved packet capture (PCAP) files.
- Protocol support: Wireshark recognizes thousands of protocols, from common ones like TCP/IP, HTTP, and DNS to more obscure protocols.
- Real-time inspection: View network traffic in real time with detailed packet breakdowns of each packet.
- Filtering and search: Use advanced filters to isolate specific packets, sessions, or protocols for easier troubleshooting.
- Cross-platform: Available on Windows, macOS, and Linux, making it accessible to a wide range of users.
- Visualization tools: Generate statistics, graphs, and flow diagrams to visualize network performance and identify anomalies.
Wireshark use cases
As a packet sniffer, Wireshark is a tool used to monitor networks by capturing and analyzing data traffic. Network admins and security teams can use it to diagnose network performance or security issues by inspecting traffic packets.
Use cases for Wireshark include:
- Network troubleshooting: Determine how traffic flows on the network and troubleshoot performance bottlenecks, including latency, packet loss, and connectivity issues.
- Security analysis: Observe network traffic to identify anomalous behavior and potential security threats and review post-incident breaches.
- Protocol development: Capture and analyze traffic sent through communication channels to uncover and solve performance and security issues, including debugging new protocols or apps by inspecting network behavior.
- Learning and training: Wireshark is an invaluable tool for networking students and professionals to learn about protocols and network operations.
Network threats that Wireshark can identify
While Wireshark isn’t an intrusion detection system (IPS) or a threat response tool, it can be used by security teams to discover and analyze suspicious or anomalous network activity.
Wireshark can identify and help analyze cybersecurity threats such as:
- Command and control servers: Malware hidden in systems may communicate with external servers for further instructions. Wireshark can help in detecting unusual DNS queries,HTTP headers, and traffic connecting to unknown remote servers that indicates a potential C2 server and attack.
- Man in the middle attacks: Threat actors intercept data shared during communications between two parties, often when one party connects to an unknown or insecure network. Wireshark can help analyze network traffic for duplicate ARP responses, increased ARP traffic, or unknown MAC addresses that indicate a MitM attack.
- Data exfiltration: Threat actors collect and send sensitive data from inside the network to an external source. Wireshark can analyze outbound traffic, including DNS, protocol, or HTTP, for anomalous patterns and large packets.
How does Wireshark work?
Wireshark captures data from network interfaces (like Ethernet, Wi-Fi, wireless LAN, Bluetooth, and VPNs) and displays the raw traffic in a readable format.
Wireshark captures packets in real time, including the source and destination addresses, protocol used, length, and contents information from the user’s desired network interface.
Wireshark UI consists of three different panes that display data from captured packets. The top panel shows the packets captured during the session and the above data.
When a user selects a specific packet for analysis, Wireshark will show the packet details in the second panel. The tool breaks down the packet into layers in OSI or TCP/IP layers and can be expanded into fields showing ports, flags, TTL values, and more.
The third panel in the Wireshark UI shows the raw data of a packet in hexadecimal and ASCII format for further analysis.
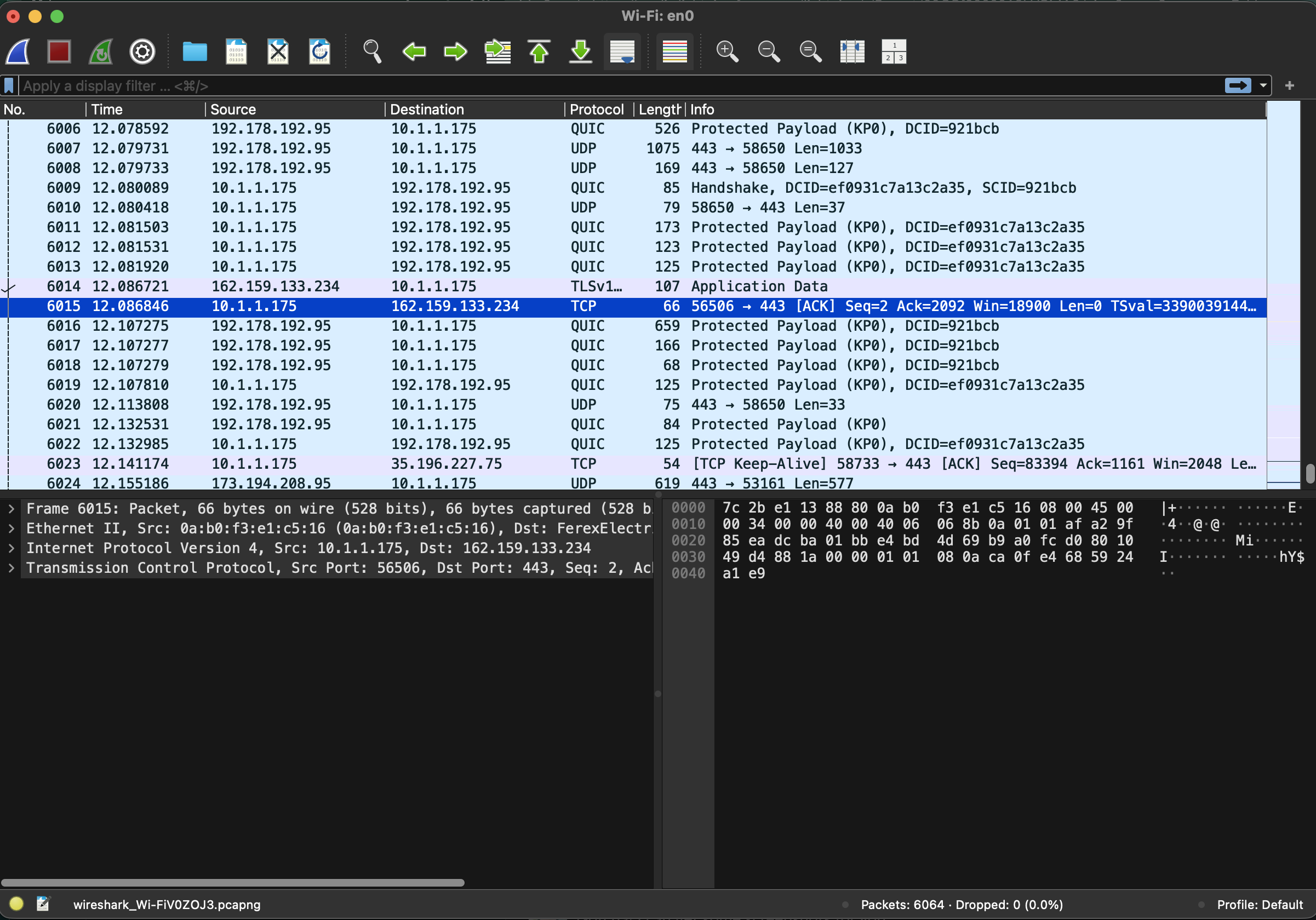
Users can apply filters to view specific streams of data or analyze how different devices communicate. Display filter options include IP address, source IP, destination IP, DNS or HTTP traffic, and packet errors. Before running a session, users can also select a capture filter, such as traffic to a single host, port 80 traffic, or TCP.
Use this guide for further learning of how to use Wireshark.
Wireshark and Stratoshark
Stratoshark is an open source companion tool for Wireshark that shares the same UI, dissection engine, and filtering code, making it easier for Wireshark users to pick up and learn it quickly.
Stratoshark captures and analyzes system calls and log messages using libsinsp and libscap to provide visibility into processes, containers, and hosts, and creating SCAP files for review.
It was released in 2025 and donated to the Wireshark Foundation to build on Wireshark’s legacy. Like Wireshark, Stratoshark works on Linux, Windows, and macOS, though native system call capture isn’t currently supported for the latter two OSes.
Learn more about Wireshark
Wireshark is available on the official Wireshark website to download. Some additional information of Wireshark and the Wireshark foundation can be found here:
%201.svg)


