Too many permissions, too little time
Right-size permissions
— the right way
Problem
Solution
98% of granted cloud permissions are not used, and these excessive permissions create risk
Optimize permissions with automatically generated policies and total visibility of in-use permissions
With so many identities to manage, it’s hard to spot compromised users in time
Analyze identity activity patterns to identify risky or compromised users in real time
The growing complexity of cloud identities has made compliance more difficult than ever
Integrate identity and access management compliance seamlessly into your workflows
Least privilege starts here
Cloud Identity Insights
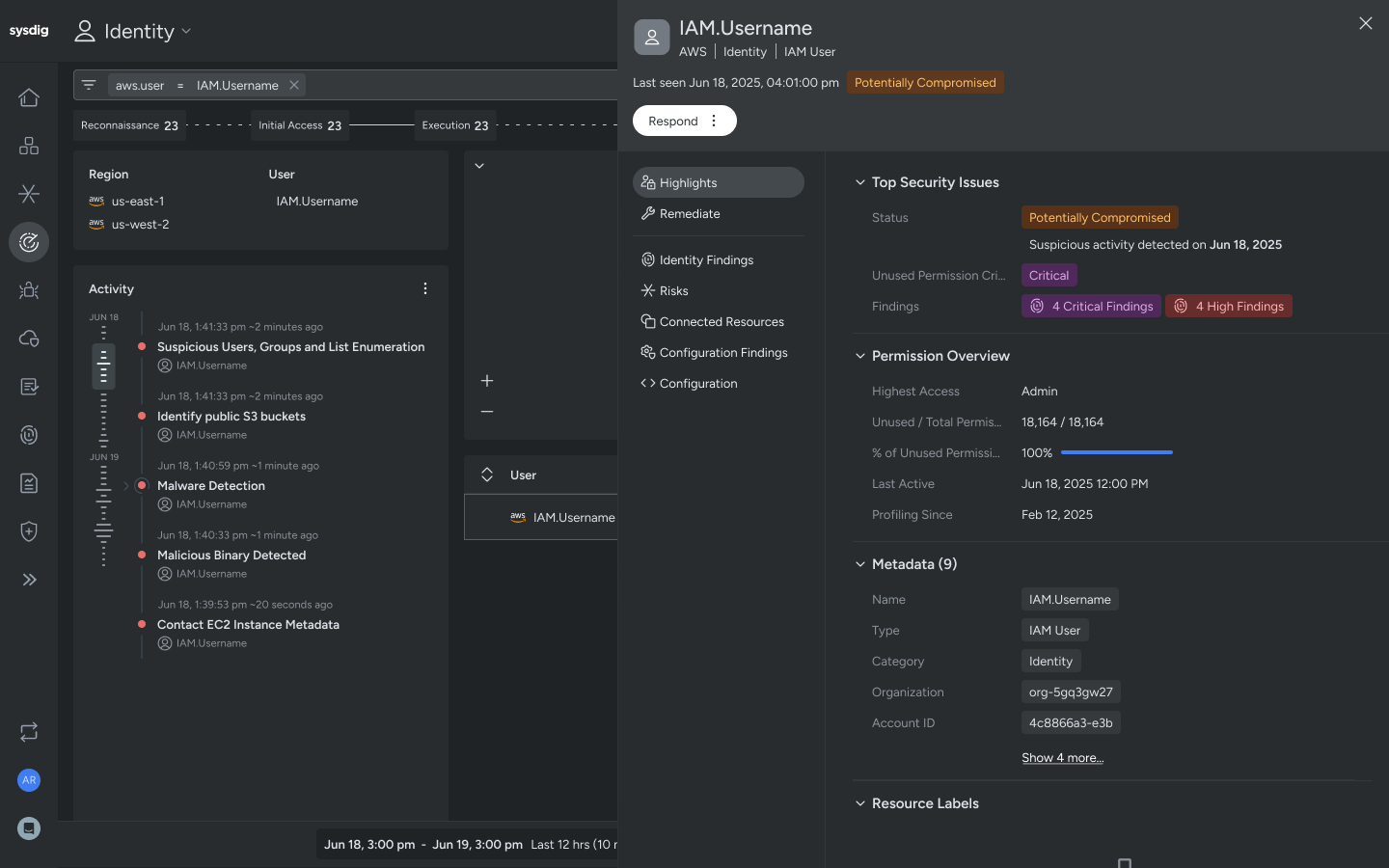
Identify compromised users based on the earliest indicators of privilege escalation and account compromise.
Least permissive policy optimization
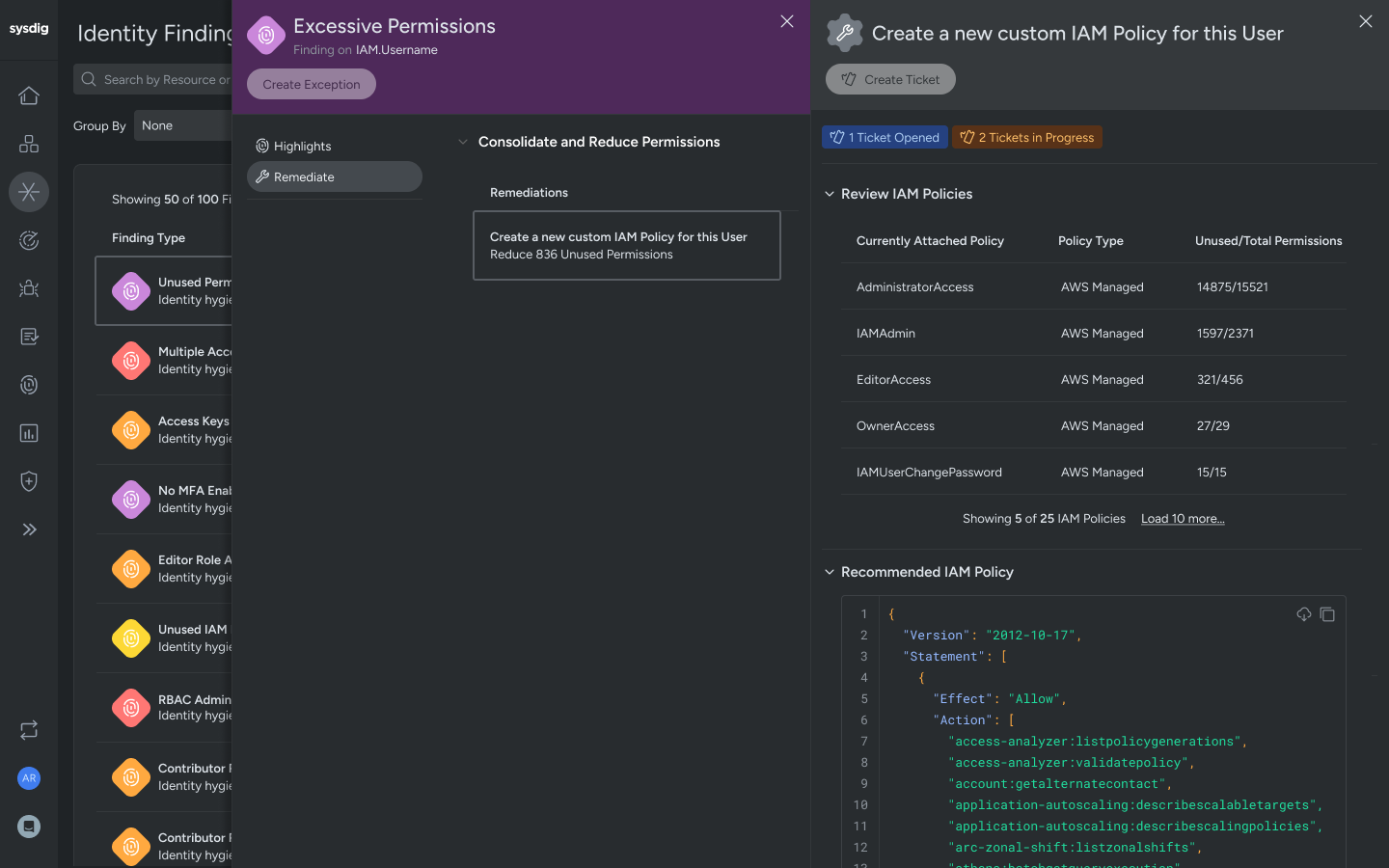
Prevent future attacks with real-time incident context, automatically recommending access policies that limit users to permissions used before compromise.
In-use permissions
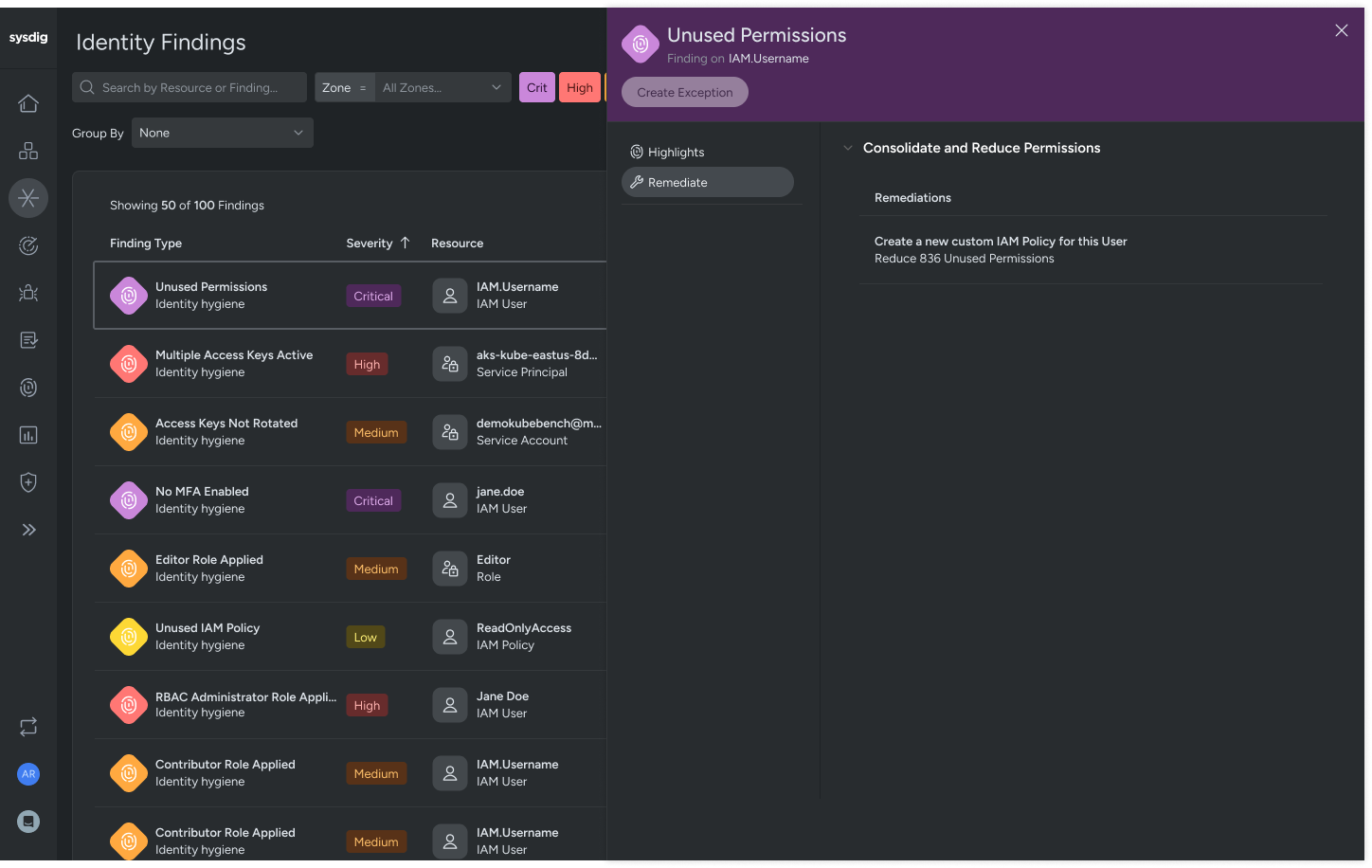
Analyze access patterns to identify unused permissions. Generate access policies to restrict privileges to precisely what users need to perform their jobs effectively.
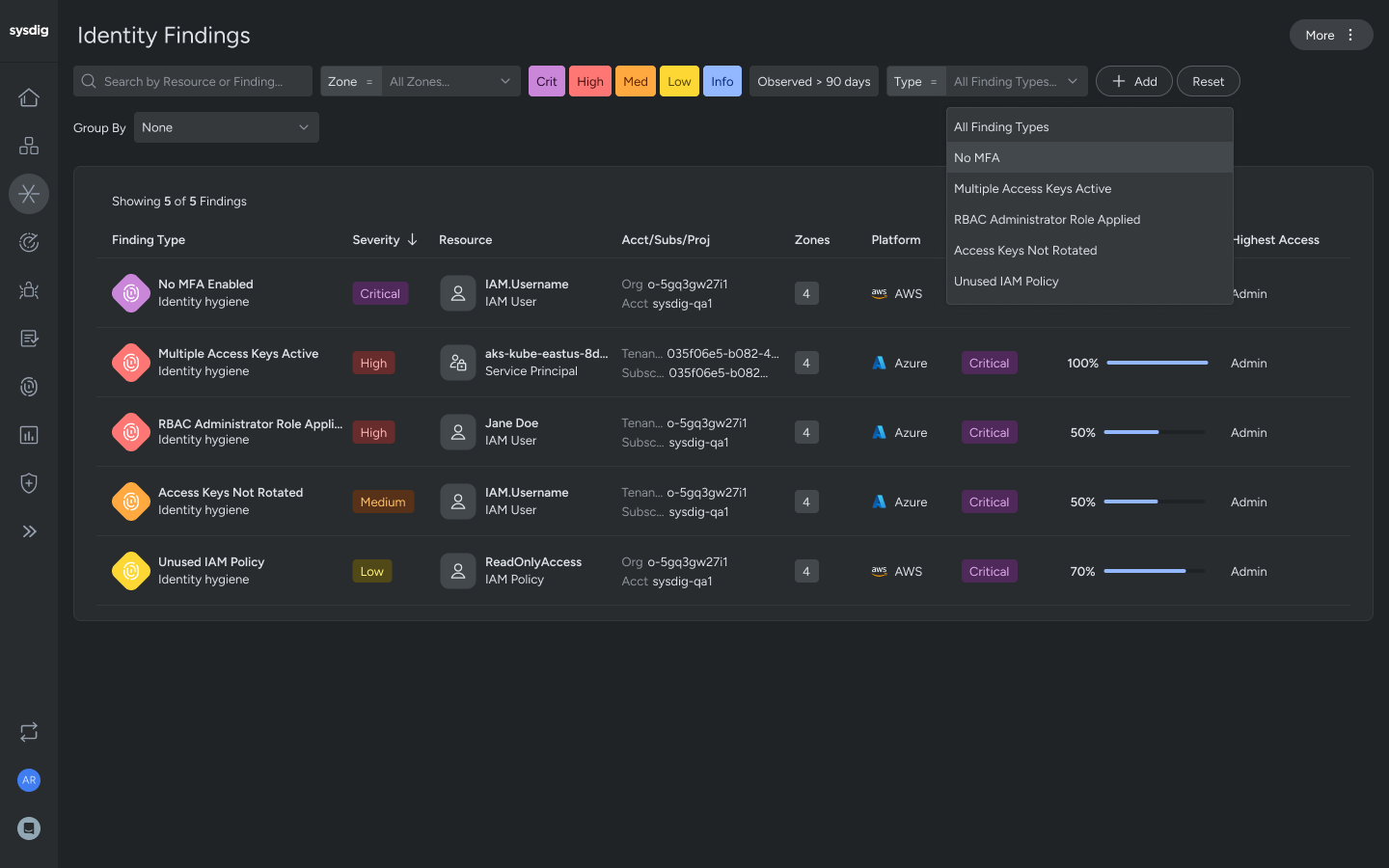
Identity findings
Automatically map IAM violations with identity findings, such as multifactor authentication, inactive user, or administrative access.

Sysdig not only helped us identify outdated access keys, but also flagged users with unused permissions, ensuring tighter control over identity security.
Director of Engineering at Syfe
How Sysdig’s CIEM works
- Sysdig Secure analyzes cloud audit logs of all executed commands in your accounts and correlates them with users, roles, and policies. Sysdig analyzes all these commands to build a live profile of permission usage, helping practitioners identify over-permissioned roles and accounts that pose a risk if compromised.
- Sysdig’s CIEM tracks key IAM risks like inactive or unused permissions, inactive users, and high-risk policies. You can drill into users or roles to see exact permission usage and last active dates, and receive suggested least-privilege versions of existing policies, making cleanup fast and low risk.
- Cloud Identity Insights enhances this by prioritizing high-risk users and roles. It also identifies when an identity may have been compromised based on early indicators of compromise. With this clear, actionable view, practitioners can focus remediation efforts where they’ll reduce the most risk. With Sysdig’s careful recommendations, teams can confidently tighten IAM policies without disrupting legitimate activity.
FAQs


