Stop cloud vulnerabilities at the source
Build secure infrastructure from day one with Sysdig
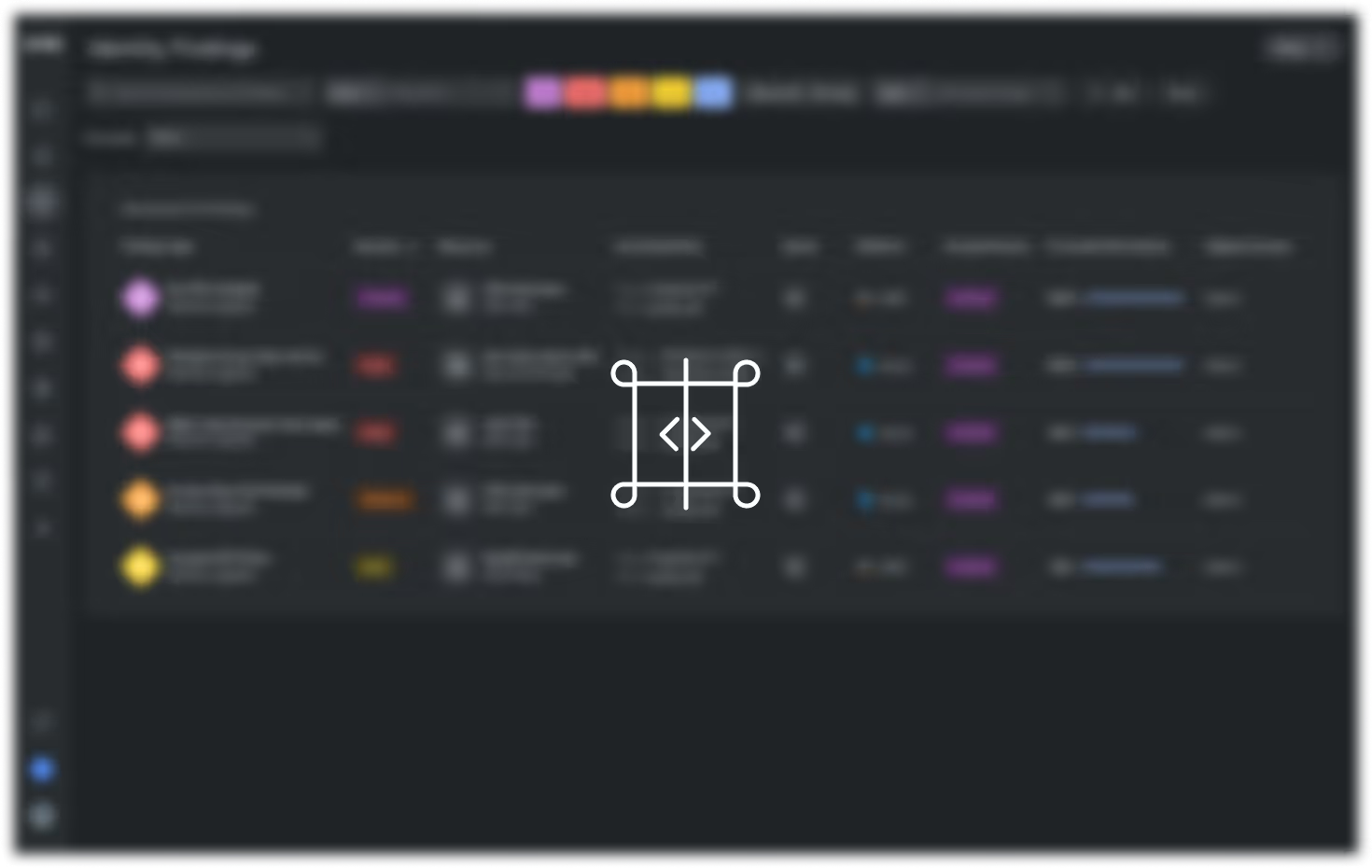
Automated IaC scanning
Sysdig automatically scans infrastructure code during development to detect misconfigurations, policy violations, and vulnerabilities in Terraform, CloudFormation, Kubernetes manifests, and other IaC templates before they reach production.
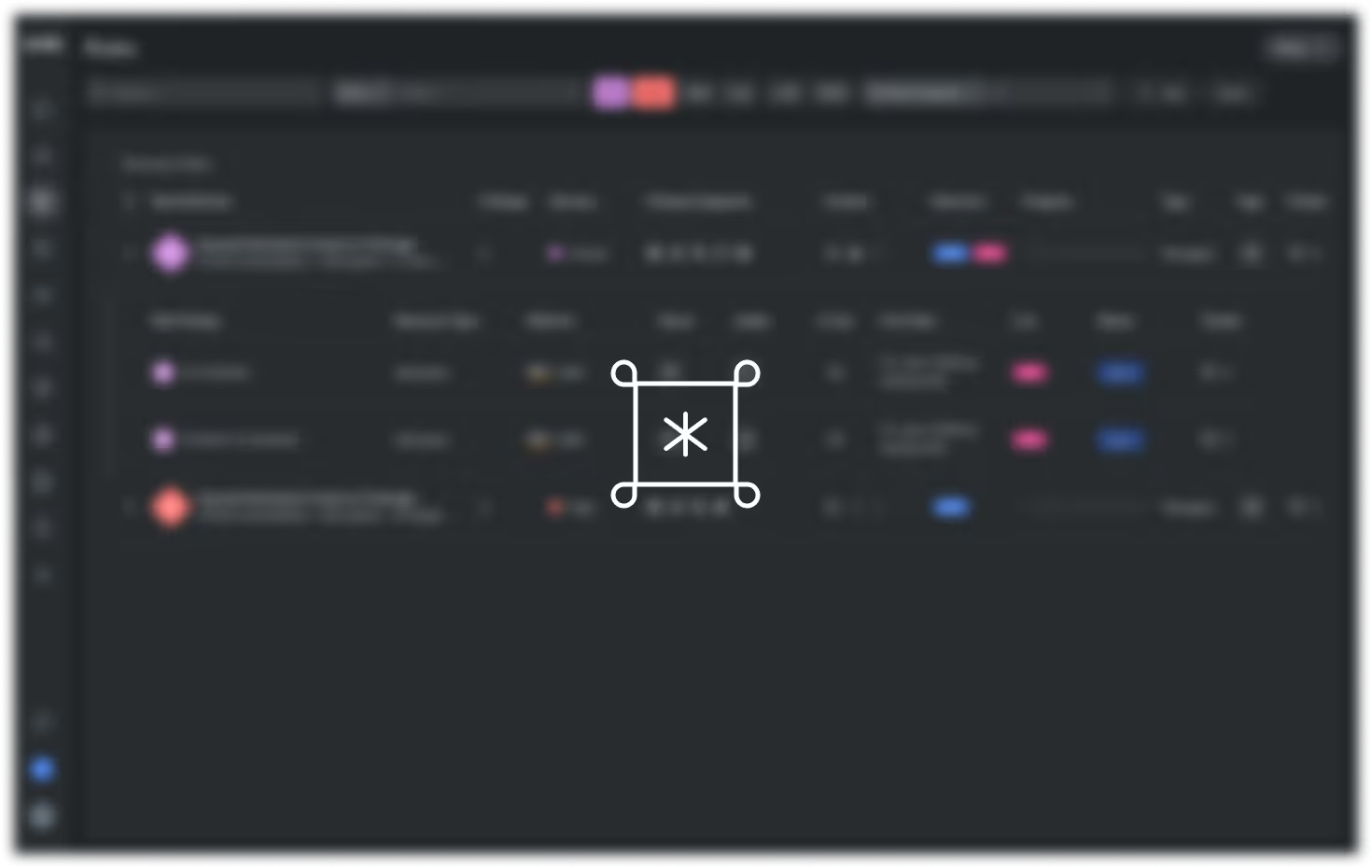
Policy as code enforcement
Our flexible policy engine enforces security standards directly in your development workflow using OPA-based policies. Implement compliance frameworks like CIS, NIST, and SOC 2 with pre-built policies or create custom guardrails for your specific requirements.
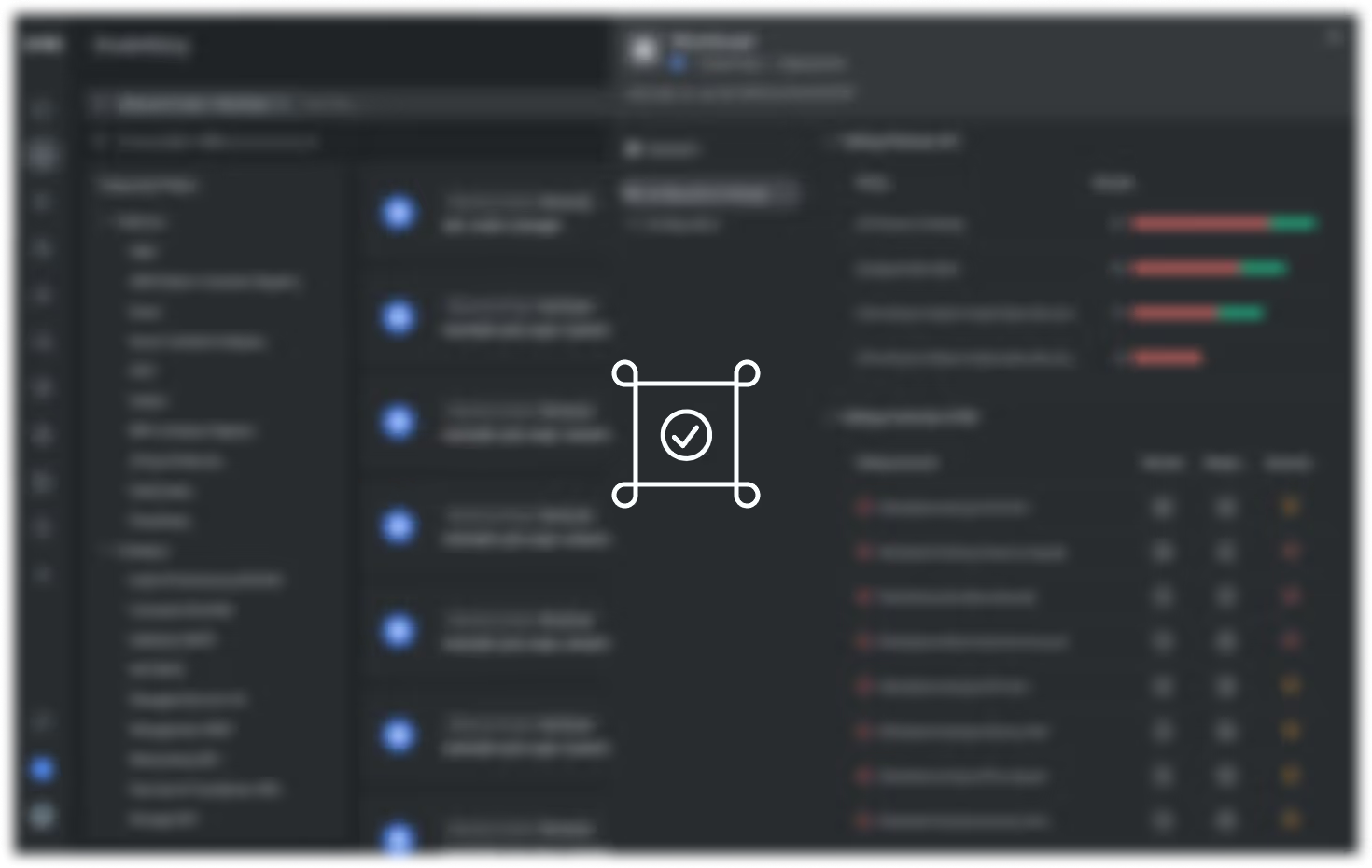
Risk-based prioritization
Intelligent risk scoring consolidates alerts from the same root cause and prioritizes issues based on application context and potential impact. This helps cut through the security alert noise and ensures your team can address the most critical vulnerabilities first.
How Sysdig’s IaC security works
Sysdig's IaC Security integrates directly into your development lifecycle through multiple touchpoints. Our solution combines static analysis of IaC templates with runtime cloud configuration monitoring to provide comprehensive protection.
During development, our scanners parse IaC files to identify potential security issues and compare configurations against policy-as-code rules stored in your repository. These checks run automatically during commits, pull requests, and CI/CD pipelines, and then the system provides actionable feedback with remediation guidance.
Post-deployment, Sysdig monitors your cloud environment and compares actual configurations with your IaC templates to detect drift. This closed-loop approach ensures security — from code to cloud — using a unified policy engine that enforces consistent standards throughout the application lifecycle.




