
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Sysdig collaborates with security organizations in the cloud security ecosystem to offer comprehensive security solutions. Cybereason, one of the top XDR (Extended Detection and Response) players in the market, is partnering with Sysdig to integrate with Sysdig's cloud threat detections to help its customers secure cloud innovation with the power of runtime insights.
Why is traditional EDR not enough?
The Gartner 2021 Hype Cycle for Cloud reports 99% of breaches start with cloud misconfigurations. Thus, having a philosophy of protecting just traditional endpoints such as servers, laptops, desktop PCs, and mobile devices with EDR (Endpoint Detection and Response) software is not enough.
What are the highlights of the integration?
The integration of Sysdig with Cybereason XDR enables Cybereason customers to tap into a broad and diverse set of threat information and runtime insights for cloud and containers. This partnership further deepens Sysdig's commitment to bring its deep CDR expertise to complementary solutions within the security ecosystem.
Here are some highlights of the Sysdig + Cybereason integration:
- Sysdig's Cloud Detection and Response – powered by Falco open source software – generates alerts and warns about suspicious events. These events, including cloud context metadata, are incorporated as signals within Cybereason's XDR.
- Cybereason XDR will further enrich and correlate these signals against endpoint, identity, and network data sources.
- Joint customers benefit from Sysdig detections to identify broader Malicious Operations (MalOps) and provide automatic response recommendations.
What is the focus of this integration?
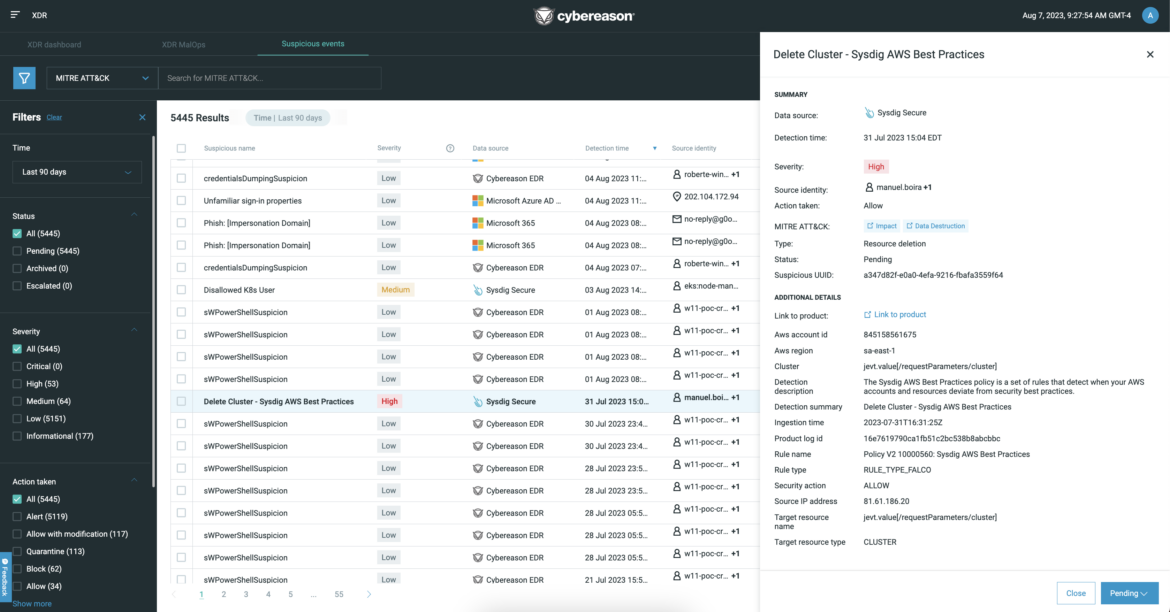
Cloud and container events identified by Sysdig are pulled into Cybereason XDR and displayed as a part of its "Suspicious Events." These events can be then correlated with other security events generated from endpoints, networks, and identity data sources within Cybereason.
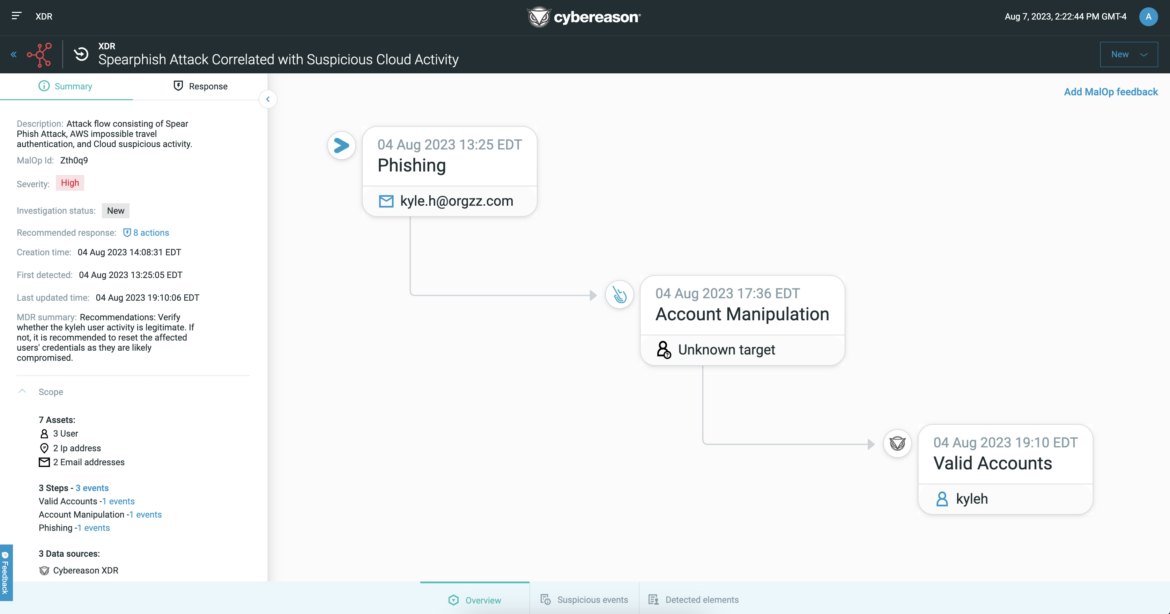
In the Cybereason UI, high-priority threats, known as Malicious Operations (MalOps), are displayed as visual attack stories, complete with response recommendations and triage from the 24/7 Cybereason Managed Detection and Response team.
Below is an example of a spear-phishing attack visualized within Cybereason with data from Sysdig about compromised AWS Cloud accounts. In this scenario, Sysdig alerts Cybereason that disallowed users for AWS have elevated their privileges. Cybereason is then able to identify, for instance, whether these users had an anomalous login, which may have originated from an AWS account credential compromise via a spear-phishing attack.
What are the benefits of the integration?
Here are some of the expected benefits of this integration for security practitioners:
- Increased visibility into security risks from cloud and containers – Cloud native applications' extra complexity generates blind spots that require specialized insight.
- Improved ability to detect and respond to threats – There is projected to be a significant reduction in mean time to detect (MTTD) and mean time to resolve (MTTR) for threats originating in the cloud.
- Increased efficiency and productivity.
What does the future of the partnership look like?
By combining the strengths of Sysdig and Cybereason, our goal is to provide a solution to help customers better protect their entire IT environments. As we progress the partnership, we will explore additional opportunities such as incorporating additional security insights, and incorporating the joint solution into Cybereason's Managed Detection and Response services. Stay tuned!


