Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

If you're running containers and Kubernetes on IBM Cloud, you can enable the key security workflows of Sysdig for your IBM Cloud deployments. The IBM Security and Compliance Center (SCC) Workload Protection service, powered by Sysdig, makes it easier for you to implement policies and safeguards to secure your containers and your Kubernetes in the cloud. With it, you'll be able to secure your build pipeline, detect and respond to runtime threats, and validate compliance across your containers and Kubernetes infrastructure.
What container security workflows are available on IBM Cloud?
IBM SCC Workload Protection provides security across the life cycle for containers, Kubernetes and cloud services. The security capabilities available to you on IBM Cloud span four key practices:
- Secure Build Pipelines: Scan images for vulnerabilities and misconfigurations
- Manage Posture and Compliance: Identify and address misconfigurations
- Detect Runtime Threats: Get real-time visibility to detect production threats
- Respond Rapidly: Capture detailed insights to speed incident response and forensics
Each of these areas provide a range of capabilities that not only help you manage risk, but also block threats, and enable you to better meet compliance requirements for your business. You'll be able to see inside containers and better handle the dynamic nature of Kubernetes at scale.
Let's get slightly more specific into a few of the features that you can integrate into your DevOps workflow on IBM Cloud to secure your environment:
All of the security features for container, Kubernetes, and cloud are integrated and available through an easy-to-use web UI.
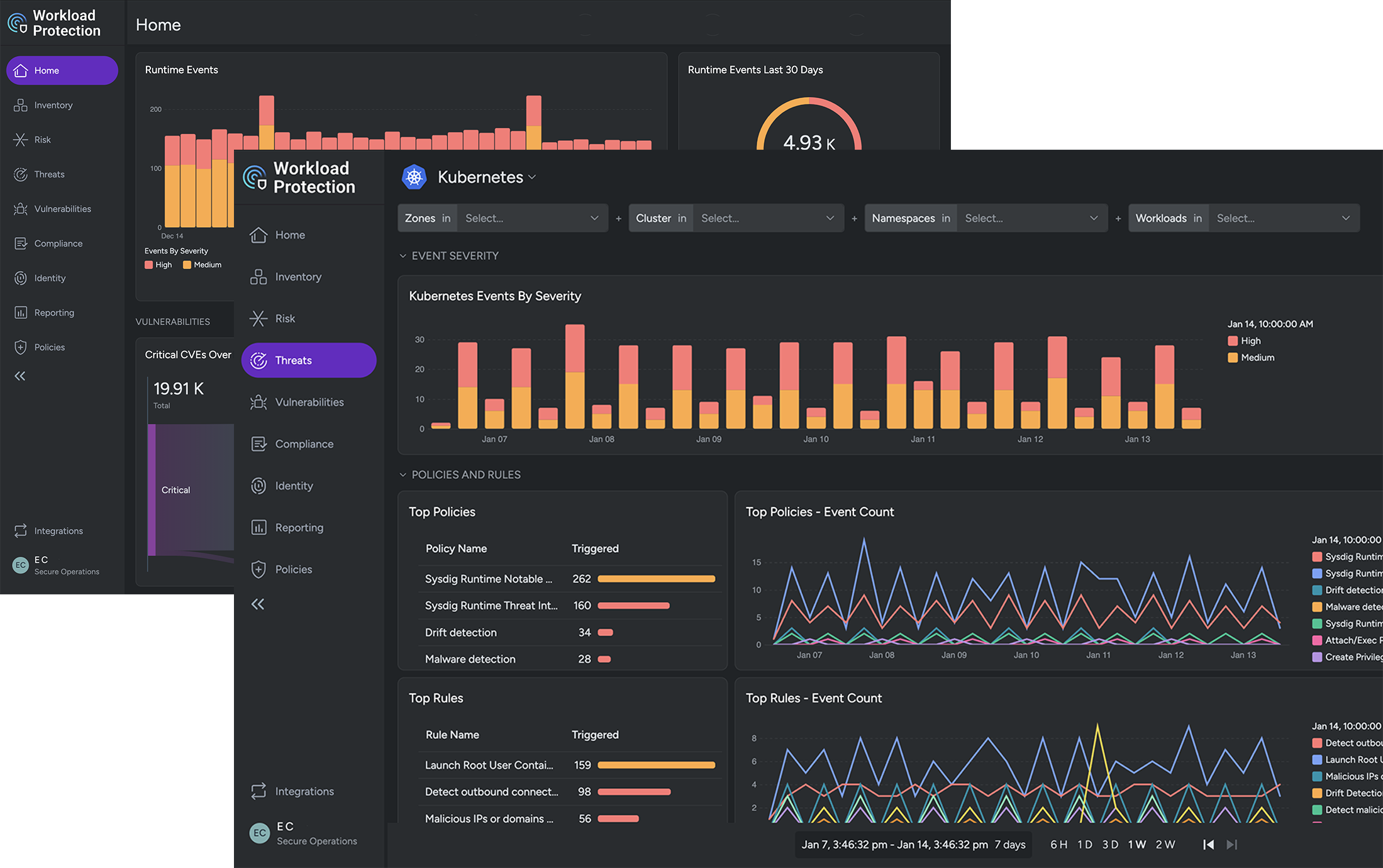
Application development has transformed CI/CD, containers and open source. If you find yourself struggling with how – and where – to enable security controls for your containers, Kubernetes, and cloud, check out what the IBM SCC Workload Protection service has to offer. One place to start is to read our Kubernetes Security Guide.
Getting started on IBM Cloud
The IBM SCC Workload Protection solution based on Sysdig is available globally in 10+ regions. If you're looking to jump right in, check out the Getting started page that outlines the steps to deploying an instance. You can get going in a few simple steps, which typically takes only a few minutes.
Don't have an IBM Cloud account? You can create an account and get started today!


