
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

The origins of Sysdig, Falco, and Wireshark can be traced back to one fundamental need: making sense of complex, real-time network traffic for better security and operational insights. Long before containers and cloud security became pressing concerns, Gerald Combs and Loris Degioanni, creators of Wireshark, were solving a different but related problem: how to capture and analyze packets to understand what was happening across networks. Wireshark emerged as a critical tool, providing unprecedented visibility into network behavior and setting the standard for packet analysis.
The shift toward cloud-native environments brought new challenges, and traditional packet capture alone were no longer enough. Technologies like BPF, libpcap, tcpdump, and Snort laid the groundwork, but as workloads moved to containers and distributed systems, deeper runtime visibility and security monitoring became essential. This evolution led to the creation of open-source Sysdig and Falco, which were designed to bring the same level of runtime insight to the world of containers and cloud security that Wireshark had brought to network traffic. However, many engineers and analysts still needed an open source tool that could enable them to analyze and troubleshoot cloud system calls and logs with the level of granularity that Wireshark afforded them on networks.
Stratoshark promises just this: extending the principles of packet capture to monitor and secure modern, distributed environments and push the boundaries of real-time cloud system analysis with a workflow that Wireshark users will find familiar.
Understanding the foundation of packet capture
At its core, Wireshark relies on libpcap, a versatile library that manages live packet capture, filtering, and file handling. Libpcap became a foundation for countless tools, providing a generic interface that could be extended to fit various needs. Snort, for instance, built a powerful rule engine for network intrusion detection directly on top of libpcap, leveraging its packet capture capabilities to detect and prevent suspicious network activity.
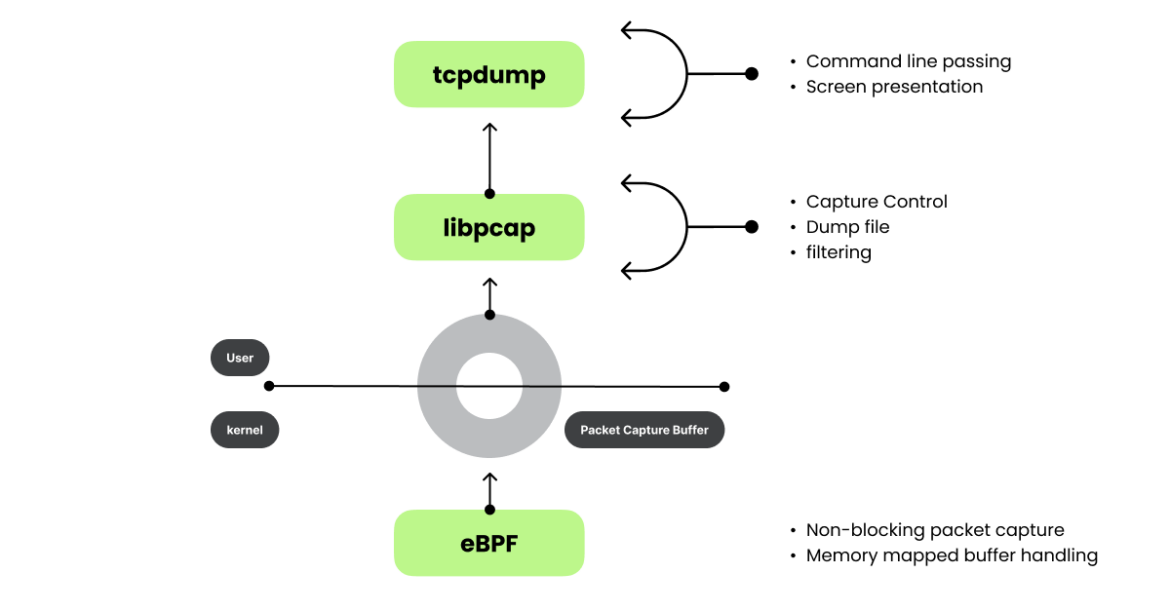
Drawing from the libpcap model, Falco emerged as a runtime security tool that monitors Linux, containers, and Kubernetes environments. Instead of packets, Falco focuses on system calls to detect anomalies, applying principles similar to those used in network monitoring. At the heart of Falco’s architecture are two essential libraries: libscap and libsinsp. These libraries mirror the role of libpcap in the packet world but for system calls and system state capture. Libscap handles low-level capture tasks, managing live data collection and recording, while libsinsp abstracts system information, offering higher-level insights and filtering capabilities. Together, they provide detection analysts with deep, real-time visibility into system activity and enable faster detection, investigation, and response to security threats and performance issues.
Understanding the current state of system call capture
Open source Sysdig was the first project to link these libraries into a user-facing tool, much like tcpdump provides an interface for libpcap. Sysdig combined libscap and libsinsp to offer deep visibility into system behavior, allowing users to trace activity across containers and hosts with ease. Although Falco and Sysdig share components, Falco does not directly depend on OSS Sysdig; instead, it leverages sysdig-probe, libscap, and libsinsp through clean, modular interfaces. This separation reflects a deliberate design choice to keep the core capture libraries versatile, fostering the development of multiple tools from a common base.
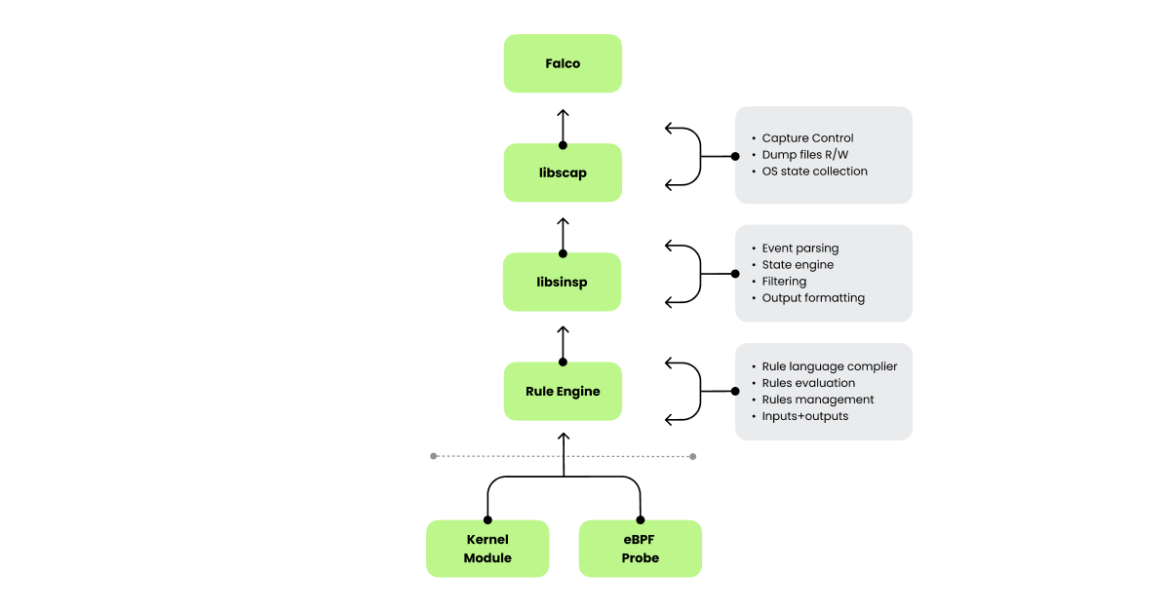
The parallels between Snort and Falco extend beyond their reliance on capture libraries. Just as Snort employs libpcap to analyze packet data, Falco uses libscap and libsinsp to analyze system calls. Falco’s rule engine, inspired by Snort’s design, applies pattern-matching principles to runtime data, focusing on cloud workloads and container environments rather than traditional network packets.
Wireshark was developed during an era when traditional on-premises networks were the norm, and packet sniffing on physical networks was standard practice. AWS cloud services didn’t emerge until 2006. When Docker popularized containerization, Sysdig quickly followed to provide system visibility. Similarly, as Kubernetes gained traction, Falco was introduced to enhance container security. Now, with widespread cloud adoption, network engineers are eager to apply their packet analysis expertise — honed through Wireshark — to the world of Linux containers and cloud environments. This need for seamless packet inspection in modern infrastructures led to the creation of Stratoshark.
Stratoshark bridges the gap between network packet analysis and modern cloud-native security. The tool relies on libscap and libsinsp, sourced from the falcosecurity/libs repository, alongside plugins from falcosecurity/plugins. In doing so, Stratoshark extends the evolutionary arc that began with Wireshark. By integrating familiar packet inspection techniques with contemporary runtime monitoring, Stratoshark represents the next step in unifying traditional network security with the demands of cloud-native environments.
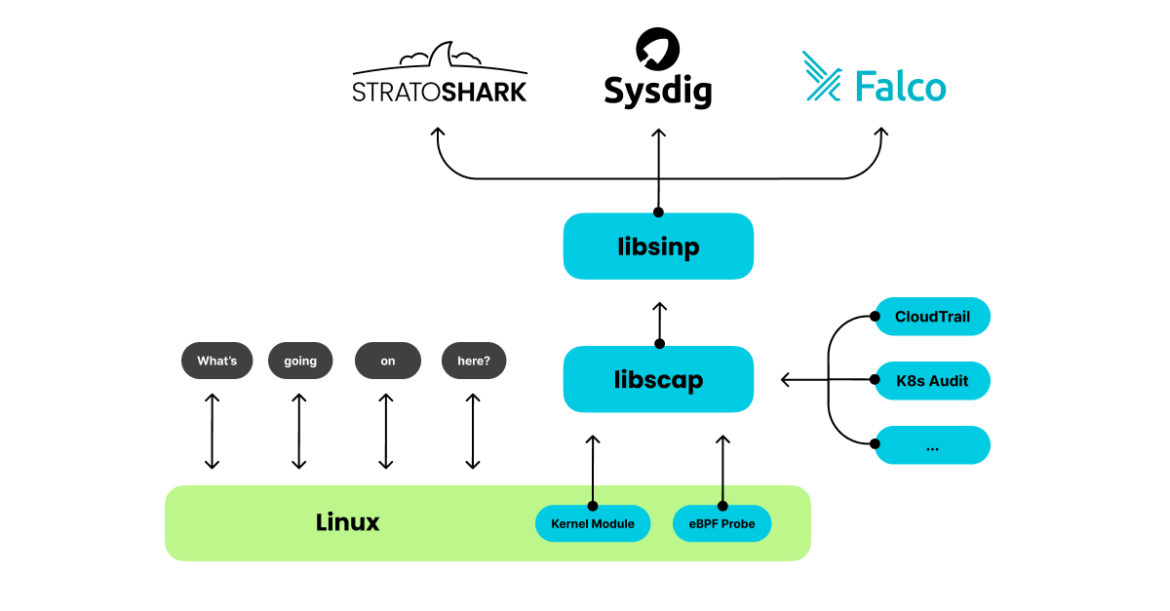
Monitoring Cloud Audit Logs in Stratoshark
falcodump is an extcap tool that allows users to capture log messages from cloud providers. The extcap interface is a versatile plugin interface that allows external binaries to act as capture interfaces directly in Wireshark. In the case of Stratoshark, each plugin is listed as a separate interface. For example, the AWS CloudTrail plugin would be listed as “cloudtrail.” All instances of Stratoshark come packed by default with the Falco CloudTrail plugin, which can pull AWS CloudTrail logs from an S3 bucket or SQS/SNS.
While Stratoshark can be installed on Windows and MacOS, native system call captures aren’t yet supported on those platforms. This can only be done on Linux systems, similar to Falco, which you need to build from scratch with the appropriate Falco libs and plugins. If you are interested in installing on other systems, you can get the early development packages for Windows and OSX.
1. Collecting an SCAP file
The easiest way to collect a Syscall CAPture (SCAP) file is via Sysdig OSS. The Sysdig OSS Github repository provides a single-line command to install Sysdig OSS on just about any Linux distribution, or you can run Sysdig as a Docker container:
You can run the below 5-second timeout command to get a 5s capture from your Linux environment into a file called generic-capture.scap:
2. Reading the SCAP in Stratoshark
If you are not interested in capturing your own .scap file right now, you can download one of the examples provided below:
- 502 Error capture for troubleshooting HAProxy 502 – Download
- 404 Error capture of a 404 error from a leaky file – Download
- curl-wsdl-win64.scap capture of curl activity – Download
- Active Malware capture from Kubernetes – Download
When you open the Stratoshark user interface (on Mac), you’ll notice the ability to either open an existing SCAP capture file from Sysdig OSS or connect to AWS using the Falco Cloudtrail Plugin. The final option is to connect to an SSH remote syscall server via sshdig.
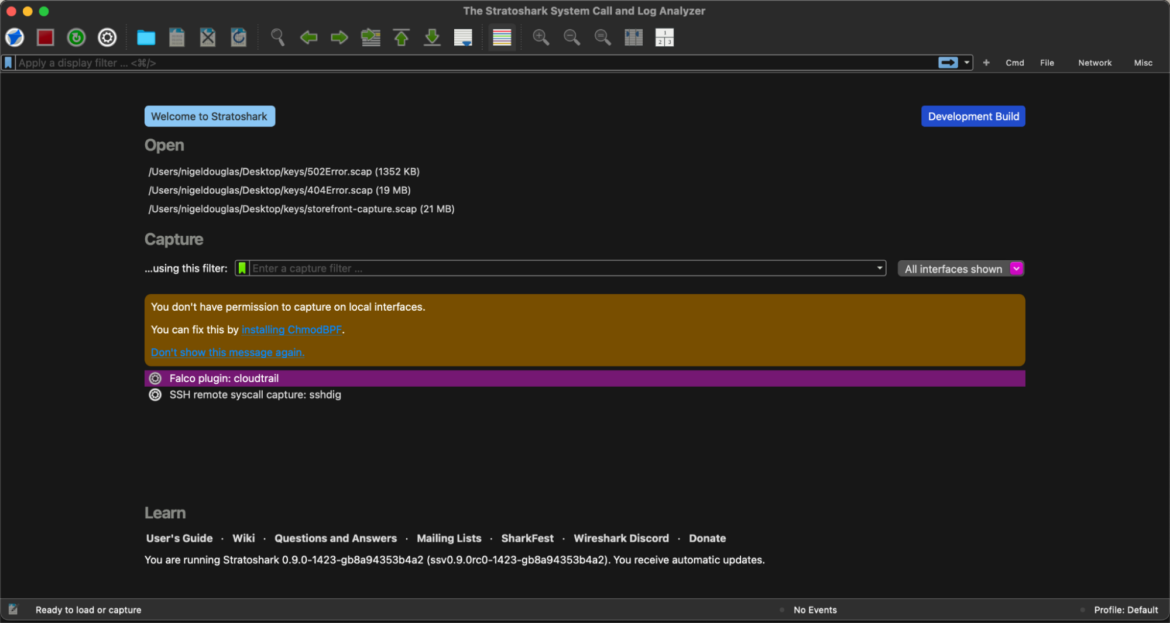
As of the version Stratoshark 0.9.0rc0-974 and later packages provided here, Stratoshark includes a new capture source named “sshdig.” It lets you capture syscalls from a remote host using Sysdig over SSH. You’ll need to know the SSH server address, username, and password credentials to connect.
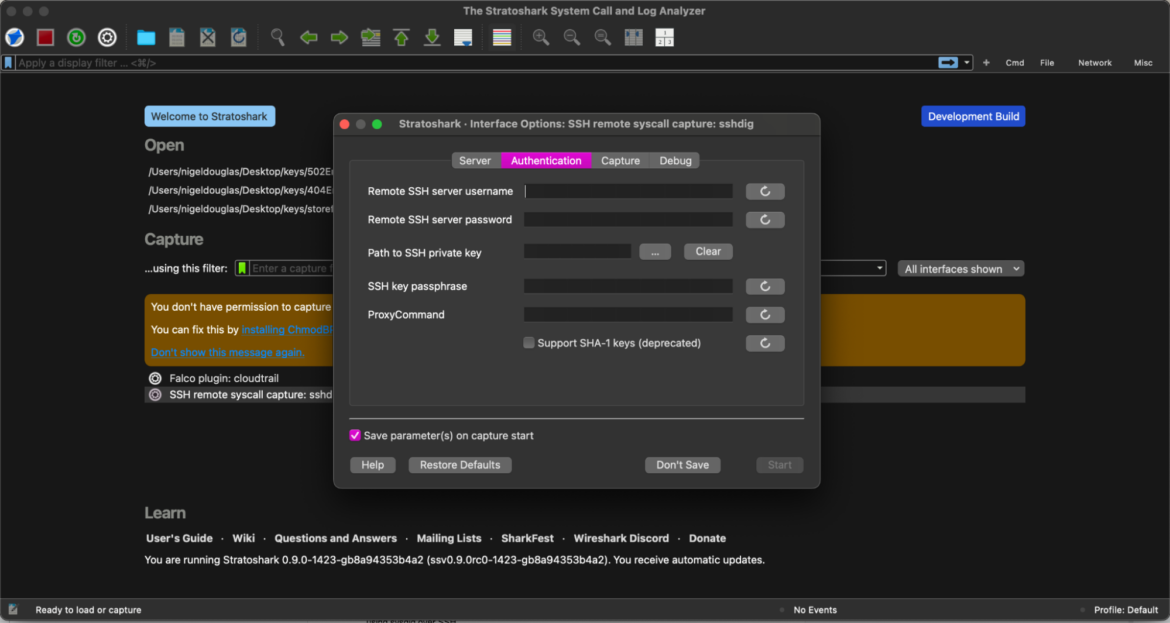
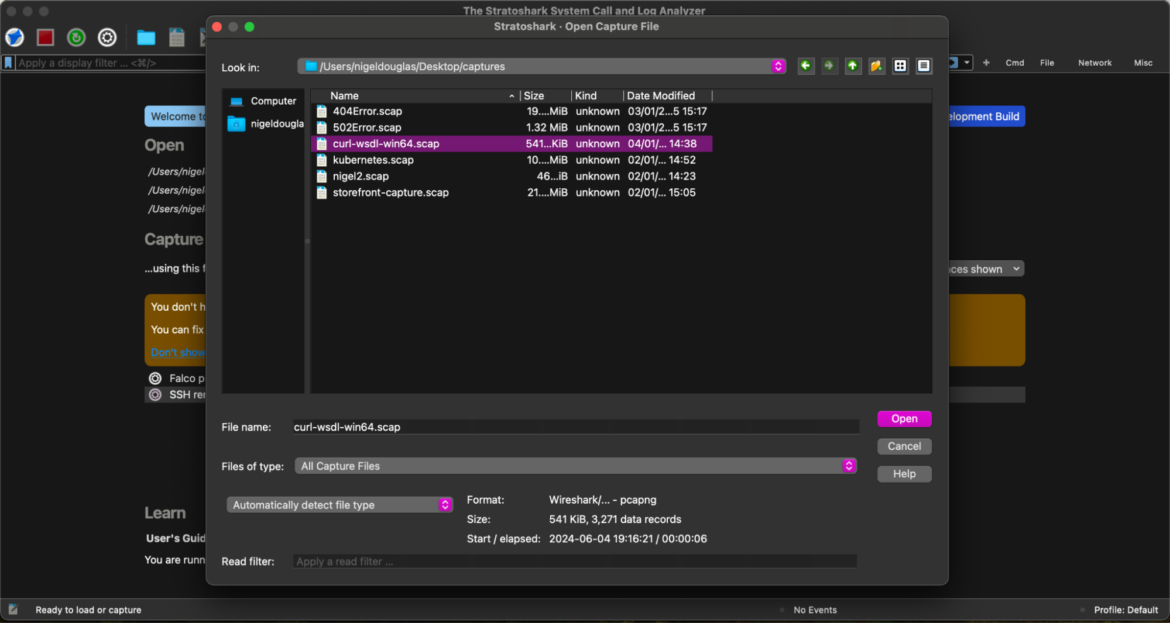
For this tutorial, we will use Stratoshark with the curl-wsdl-win64.scap capture file provided by the Wireshark team on Discord. Click on the blue folder icon in the upper toolbar and open the .scap capture – similar to how you’d open a PCAP file in Wireshark.
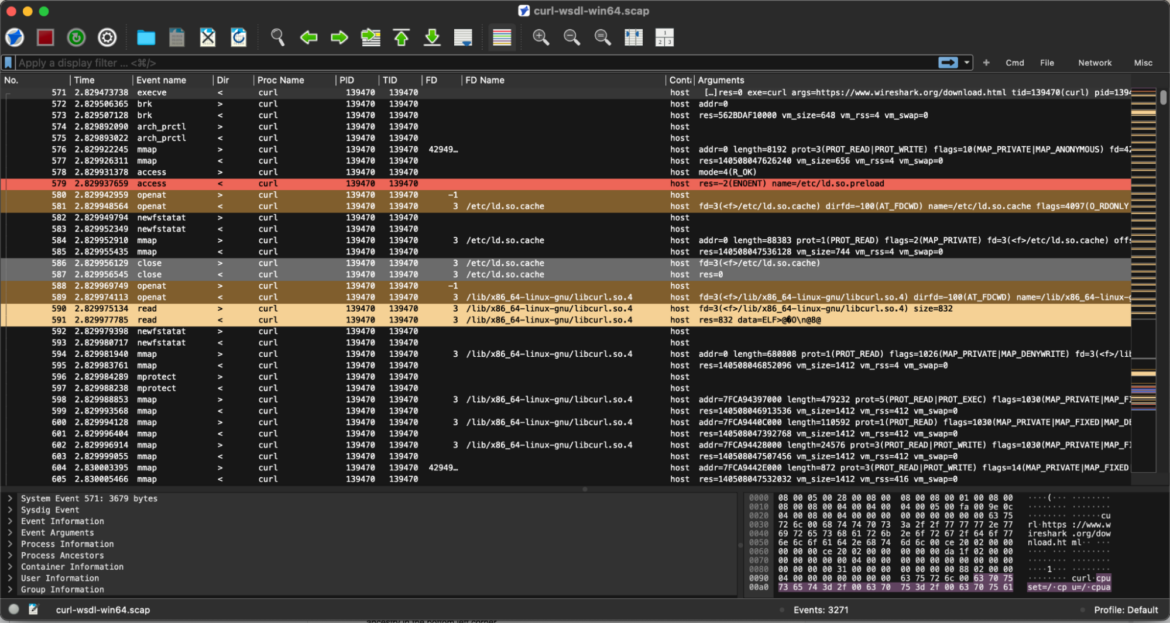
When you open the file, you’ll notice the interface closely mirrors the familiar user experience of Wireshark. However, unlike traditional packet inspection, additional fields in the bottom left corner provide insights into events, users, and process ancestry, offering a more comprehensive system activity view.
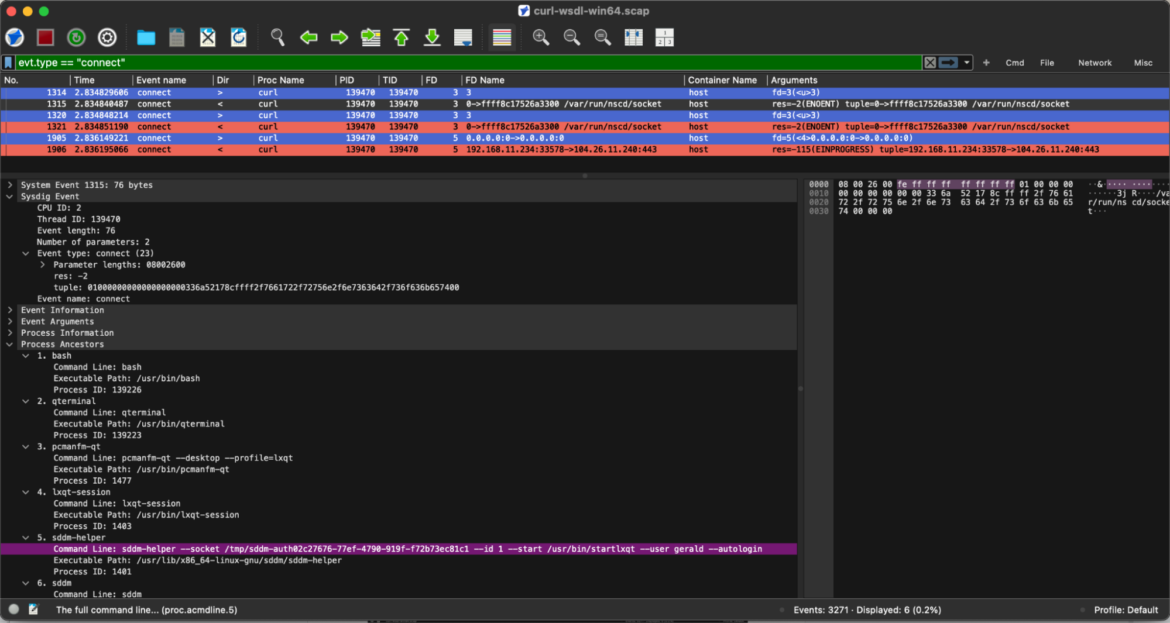
To identify all outbound connection requests initiated by curl, we can effortlessly apply the following event filter search:
By examining the process ancestry, we can trace the exact command-line argument that initiated the outbound network connection. This not only highlights the specific cURL request responsible but also reveals the full context surrounding the event — from parent processes to associated threads — offering a clearer picture of how and why the connection was made. This level of visibility is crucial for troubleshooting, auditing, and enhancing overall network security.
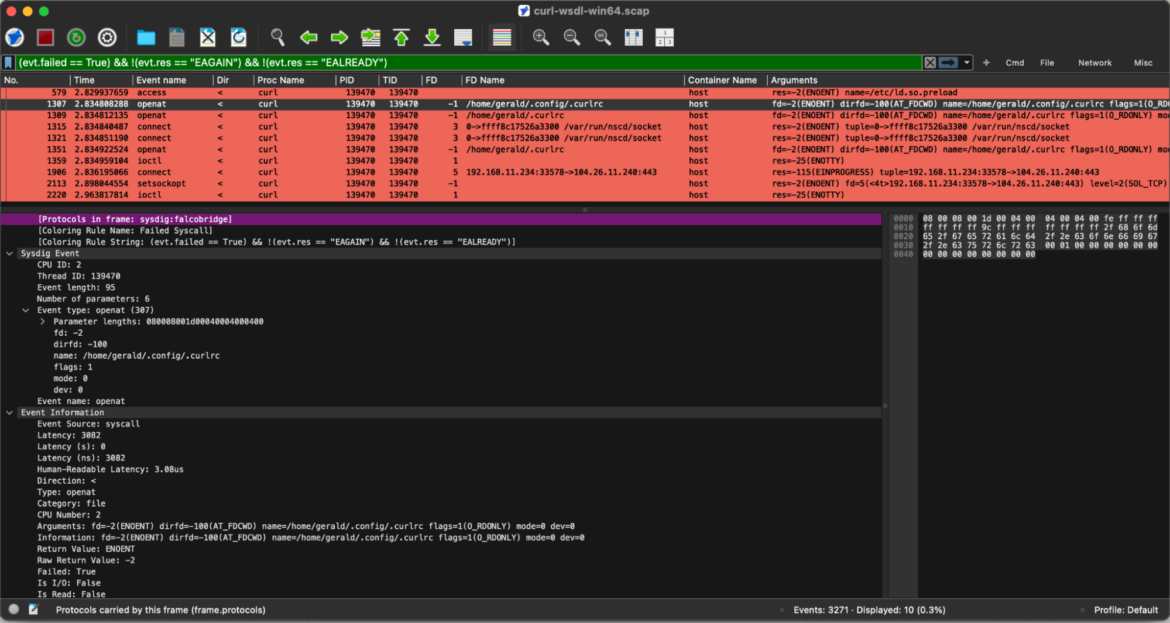
From a troubleshooting standpoint, it’s important to recognize that system calls can sometimes fail for legitimate reasons. However, identifying and understanding the root cause of these failures is critical, especially when dealing with key components or protocols, such as the Falco Bridge in this scenario. Gaining visibility into why these failures occur enables operations and security teams to conduct deeper investigations, mitigating potential system instability or performance issues before they escalate.
To streamline this process, the following Stratoshark filtered search highlights all relevant activity in red, drawing immediate attention to areas that may require closer inspection. This makes it easier to pinpoint irregularities and address them proactively.
Conclusion
Stratoshark represents the next evolution in packet analysis and the latest milestone in Sysdig’s ongoing open source journey. Stratoshark promises to bridge the gap between traditional network monitoring expertise, the dynamic nature of system call monitors in containers, and sporadic audit activity in cloud environments. Born from the open-source ingenuity behind Wireshark, Sysdig, and Falco, Stratoshark empowers engineers to extend their expertise into modern infrastructure.
Whether you’re just getting started or eager to dive deeper, there’s no better time to explore what Stratoshark has to offer. To learn more about the open-source projects driving this innovation, visit Sysdig’s contributions page. For a closer look at Stratoshark in action, don’t miss Gerald Combs’ keynote from Sharkfest Europe — it’s an essential watch for anyone passionate about the future of packet analysis.


