Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Container security has experienced significant transformation over the past decade. From the emergence of foundational tools like Docker to the maturation of orchestration platforms such as Kubernetes, the container security landscape looks different than it did even a few years ago. With Gartner predicting 95% of organizations will be running containerized applications in production by 2028, it’s clear that container security is going to be a key priority for most organizations moving forward.
The rapid evolution of technology has not only driven advancements in containerization but has also created opportunities for attacks targeting containers and cloud-native infrastructure. Attackers are able to automate their reconnaissance and other tactics due to the uniformity of cloud providers’ APIs and architectures, executing attacks in less than 10 minutes. Organizations need to rethink their approach to cloud container security and workload protection or risk being outpaced by these attacks.
A new normal brings new challenges
In modern application development, containers are quickly becoming a popular tool for developers, providing numerous advantages including improved agility and scalability. They provide developers with flexibility to update a specific container or microservice instead of the entire application, greatly speeding the pace of innovation. The convergence of cloud migration and widespread adoption of DevOps practices has pushed containerization as a prevailing trend, empowering organizations to streamline their operations and increase the pace of new releases.
While adoption increases every year, containers are still a relatively young technology, with many companies still in the early stages of their containerization journey. The ever-evolving technology ecosystem surrounding containers, including Kubernetes, introduces constant shifts and updates, and development teams and infrastructure expanded faster than security teams. As a result, there is a general scarcity of cloud-native security talent and expertise needed to effectively secure these environments. We have also seen developers increasingly shoulder security responsibilities as organizations embrace DevSecOps strategies. Containers offer many advantages for innovation and agility, but they also expand the potential attack surface, posing a challenge for security teams trying to balance security and speed.
Two sides of container security
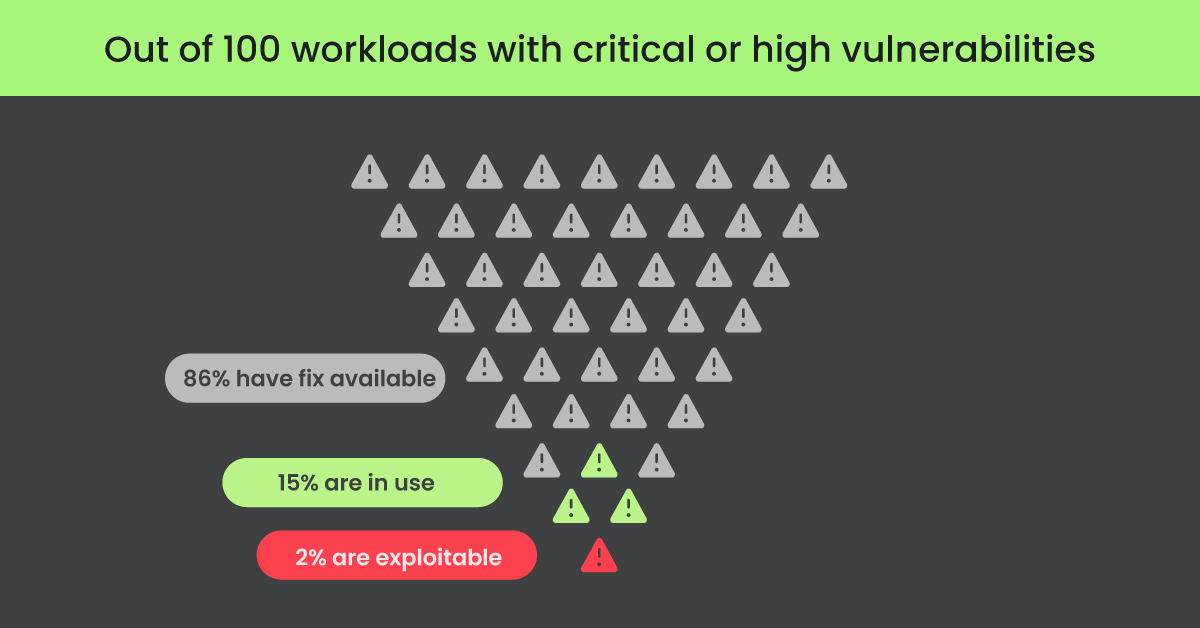
As container technology continues to mature, two key security trends have emerged over the last few years. The first revolves around key risks getting obscured by the endless noise and alerts created by many security tools. Under the DevSecOps model, developers are often responsible for fixing vulnerabilities in the code packages they deploy but find themselves overwhelmed by the sheer volume of alerts. Our research found that of cloud workloads with critical or high severity vulnerabilities, only 1.2% are exploitable, have a fix, and are actually in use by the application.The number of new cloud-related CVEs increased by nearly 200% in 2023, and the sharing of open source container images has left security teams facing a large number of critical and high-severity container vulnerabilities. The challenge many organizations face lies in discerning which of these risks actually have a high chance of exploitation and which can be deprioritized. The last thing any developer or security team wants is to waste valuable time sifting through a long list of security findings, only to discover that many are inconsequential.

The second major trend is the impressive speed at which cloud attacks now move. As more companies have shifted to cloud-native applications, attackers have adapted to leverage the architecture upon which these apps are built. After finding an exploitable asset, malicious actors need only minutes to execute an attack and start causing damage. The initial stages of cloud attacks can be heavily automated, and attackers are coming up with all sorts of sophisticated techniques to disguise their presence. In just the past year, we’ve observed numerous attacks where a malicious actor gained initial access through a vulnerability in a container image or open source software dependency, including the well-known SSHD backdoor in XZ Utils. Once infiltrating the environment, attackers can easily move laterally – whether from workload to cloud or vice versa – hunting for credentials or sensitive data to exploit for profit.
A modern approach to cloud and container security and workload protection
As the container security landscape evolves, organizations are looking to strike a balance between prevention and defense. Initially, many utilized different tools to secure their containers than they used for other parts of their cloud infrastructure. However, container threats now often cross cloud domains, making this segmented approach slow and outdated. The lack of communication between these tools results in viewing container security in isolation. While an isolated tool might detect a malicious actor breaching a vulnerable container, the post-escape attack path remains obscured. A more robust approach is to use a unified platform that connects the dots across your broad cloud infrastructure to thwart and respond to threats with agility. Already, numerous enterprises have started this journey towards consolidating cloud security. In the 2023 Gartner® Market Guide for Cloud-Native Application Protection Platforms (CNAPP), Gartner predicts this trend will continue, forecasting that by 2025, 60% of enterprises will have consolidated cloud workload protection platform (CWPP) and cloud security posture management (CSPM) capabilities to a single vendor or CNAPP. Container security falls squarely into this category of CWPP and security leaders and practitioners will need to keep up with this change as the boundaries between domains across the cloud begin to blur.
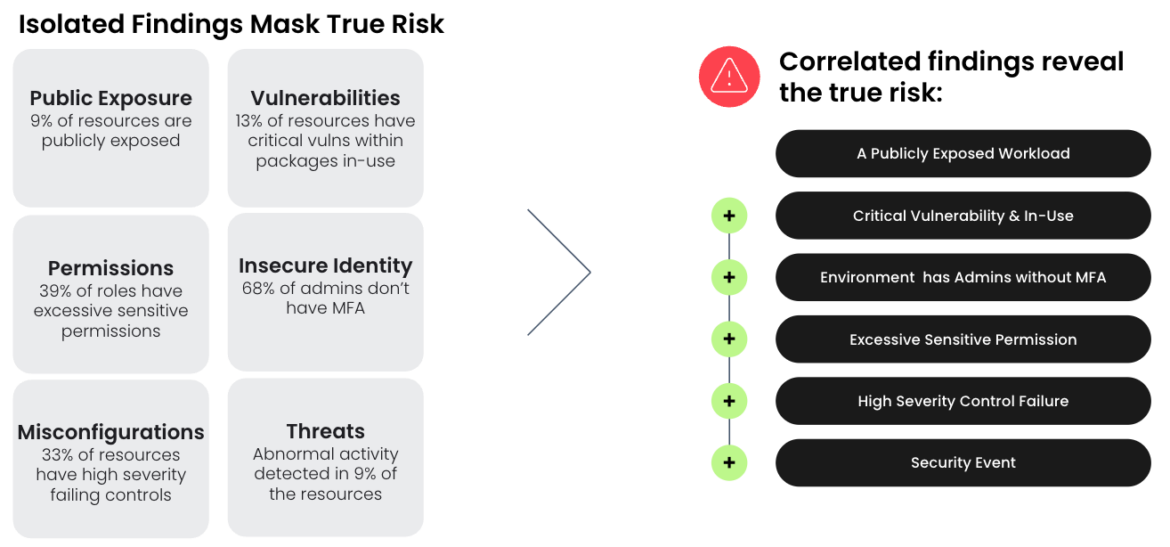
To adapt to this new normal, organizations need to rethink their approach to container security. Despite the evolving threat landscape, the fundamental challenge remains the same: security and developer teams must catch vulnerabilities in container images and detect threats at runtime. But now, they must approach this challenge with a different lens. In the modern environment, container security and workload protection need cloud context to be truly effective. Correlating container findings with context across the cloud is essential to getting the full picture of how an attacker can exploit your environment. Armed with this context, teams can focus on active real-time risk in their organization and view containers as part of a larger story.
Container security and workload protection typically encompasses use cases like threat detection and response, vulnerability management, and Kubernetes security posture management (KSPM). These elements remain critical, but this new approach integrates them with findings like real-time configuration changes, risky identity behavior, and cloud log detections. These other findings are usually associated with CSPM but are becoming relevant for container security. Combining these factors with real-time contextual insights on vulnerabilities and container threats paints a comprehensive picture of potential attack paths throughout a user’s environment. Solely focusing on containers may reveal an initial breach but fails to unveil the extent of damage or anticipate the attacker’s next move. As long as your organization has workloads running in the cloud, this additional cloud context provides great value.
Bringing the best of agent and agentless to workload protection
The best way to achieve this balance of security and speed combines agent-based and agentless strategies. There is an ongoing debate over whether agent-based or agentless approaches are more effective, with agentless instrumentation becoming a popular approach due to its ease of deployment and rapid time to value. For this reason, many security teams prefer to implement an agentless approach wherever possible. While there are benefits to both approaches, the most effective solutions will integrate both for comprehensive visibility. For containers, agents provide deeper runtime visibility and real-time detection for faster time to discovery. Unfortunately, it is not always possible to deploy them universally due to resource constraints.
In these cases, leveraging agentless instrumentation to supplement agents ensures full breadth of coverage across your infrastructure. For container security, deploying agents strategically allows you to prioritize vulnerabilities based on in-use packages and detect threats in real time – capabilities that are not possible with a solely agentless approach. Supplementing this with agentless deployments enables quick basic vulnerability scanning across all containers. As previously highlighted, integrating cloud context into workload protection – often achieved through agentless means – is a great way to anticipate and combat live attacks. This approach not only tackles the traditional challenges associated with container security and workload protection but also provides a full picture and rich context to address the most significant risks. Both approaches bring clear benefits to container security, but this new approach of implementing agentless where possible to supplement the deeper insights from agents brings the best of both worlds.
Security must continue to adapt
The rise of containerization and cloud-native applications, along with the advances made by attackers, has brought us to a challenging point for workload protection. In this constant chess game, security teams must remain proactive and adaptable, continuously evolving their defenses or risk being breached by emerging threats.
Ultimately, organizations that adapt the quickest will be best equipped to detect attacks that strike without warning in a matter of minutes. As boundaries between cloud domains continue to become less defined and the market moves towards consolidation, the ability to connect events across your entire cloud infrastructure will be key to protecting your assets and mitigating risk.
Ready to see how Sysdig can help you go from visibility to action?
👉 Request a demo to see how Sysdig works.



