Content
A Cloud-Native Application Protection Platform (CNAPP) is an all-in-one security solution that safeguards cloud-based applications and infrastructure, providing centralized controls, threat detection, and incident response capabilities.
Gartner defines CNAPP as “a unified and tightly integrated set of security and compliance capabilities designed to secure and protect cloud-native applications across development and production. CNAPPs consolidate a large number of previously siloed capabilities, including container scanning, cloud security posture management, infrastructure as code scanning, cloud infrastructure entitlement management, runtime cloud workload protection, and runtime vulnerability/configuration scanning.”
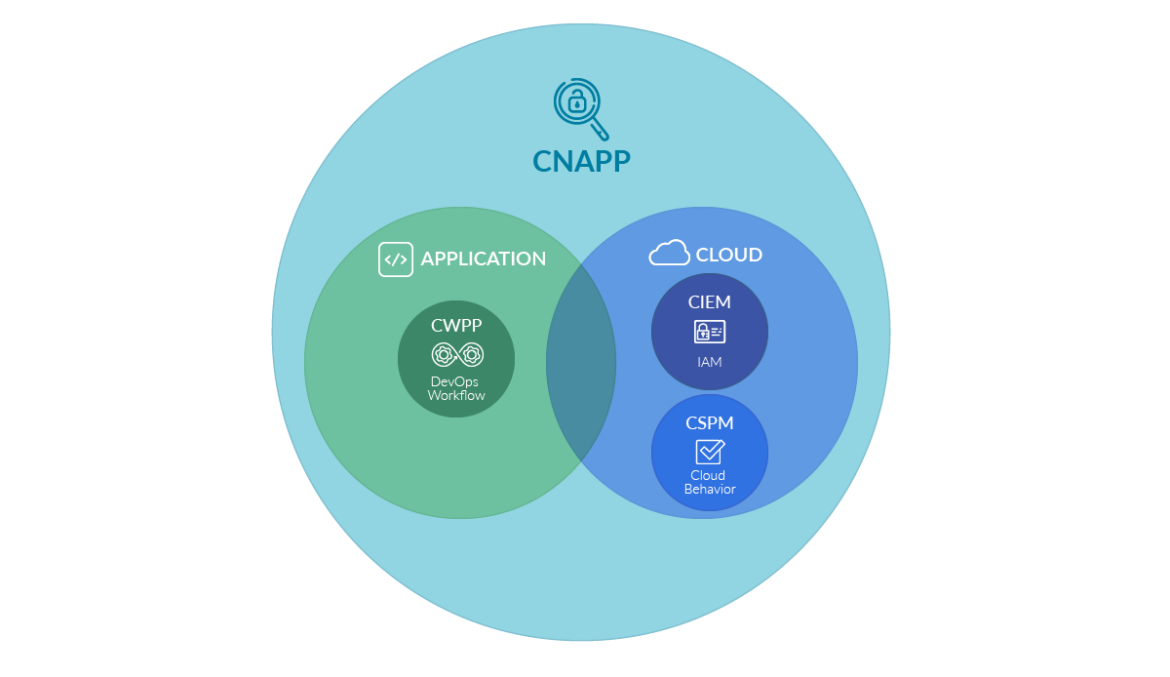
Why CNAPP?
A CNAPP is essential in today’s digital landscape to address the ever-growing need for robust cloud security consolidation and enhanced software development lifecycle (SDLC). With the rapid adoption of cloud computing and the increasing complexity of modern applications, traditional security measures often fall short in effectively protecting against sophisticated cyber threats.
A CNAPP incorporates “shift left” and “shield right” security concepts to provide a comprehensive and robust security strategy throughout the application lifecycle.
By shifting security to the left, organizations can leverage security controls, vulnerability scanning, and compliance checks from the very beginning of the application development process.
The “shield right” concept focuses on detecting and responding to security incidents in real time during the runtime phase of the application. Despite best efforts to secure applications during development, vulnerabilities may still exist, or new threats might emerge, and that’s why a CNAPP must adopt and streamline these two concepts.
What are the key features of a CNAPP solution?
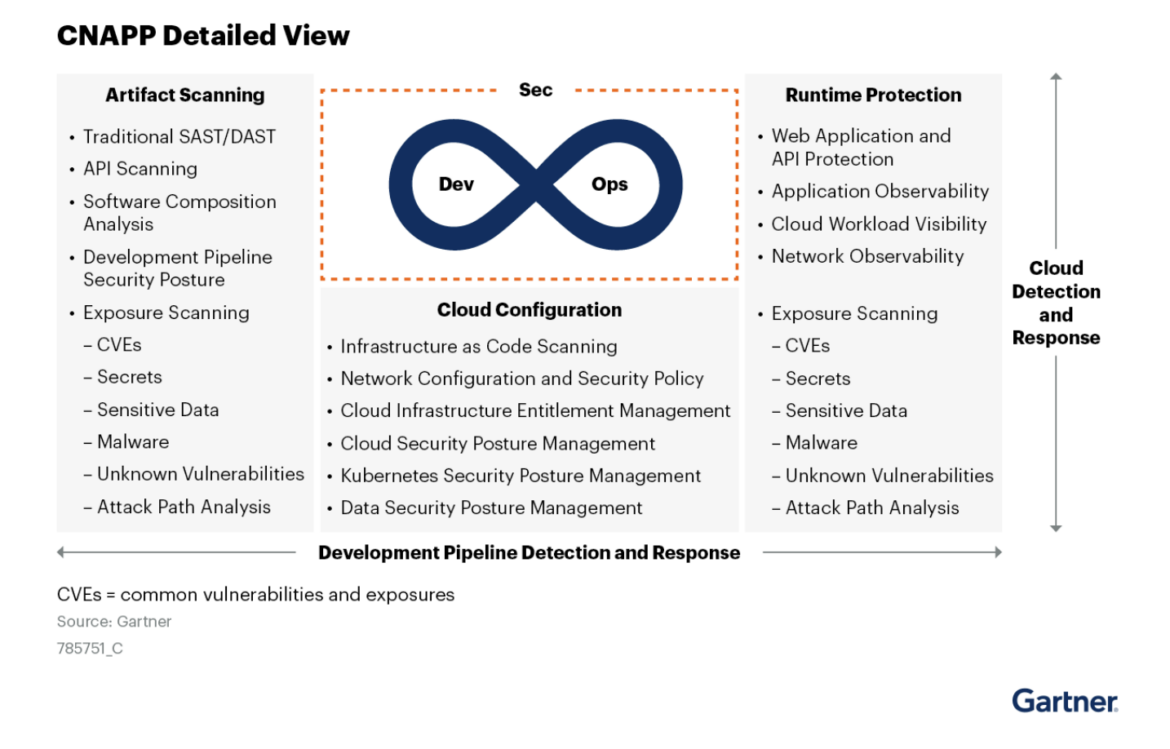
CNAPP provides security capabilities that span the many stages of the software supply chain, ensuring comprehensive protection throughout the development and operational lifecycle. Gartner combined these capabilities under four main categories.
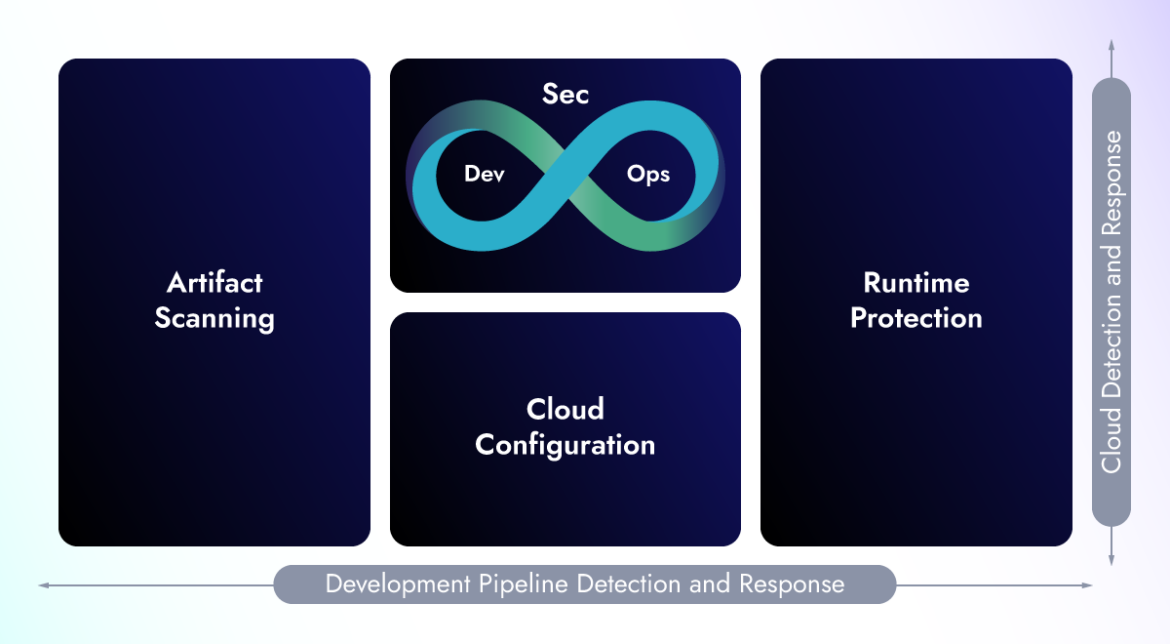
Artifacts scanning
Artifacts scanning is one of the core CNAPP components to support the shift-left security approach. Shifting risk visibility and scanning left requires integration into the development pipeline tools the development organization uses.
There are two major areas of artifact scanning, whether artifacts are source code or a compiled binary. They are Software Composition Analysis (SCA) and application security testing.
SCA reviews an artifact to find any open source libraries it has included. Then, it flags the version and license for the library in use. With that information, it can then list any common vulnerabilities and exposures (CVE) and their rating, and attach that in a report or as metadata for the artifact in the repository it lives in.
Application security testing falls into three main groupings: static (SAST), dynamic (DAST), and interactive (IAST). SAST looks at the source code or built artifact for best practices and common mistakes that can be found in code like unchecked buffers. DAST treats the artifact as a black box while it is running. It pokes at it like an attacker would, looking for things like input validation or unsecured pages. IAST works inside the application while it is running but only analyzes the application code as it is executed. It is most often seen in environments where QA teams are running functional tests.
Cloud configuration
Cloud Security Posture Management (CSPM)
CSPM is the continuous monitoring, detection, and remediation of cloud security misconfiguration to ensure that cloud infrastructure is configured correctly and locked down. It validates what is running and alerts on anything that doesn’t match how it expects to see things. Examples would be open ports or security roles with more access than required.
Cloud Infrastructure Entitlement Management (CIEM)
CIEM is the security process of managing access rights, permissions, or privileges for the identities of a single or multi-cloud environment. This process helps to identify and avoid risks resulting from privileges being higher or broader than they should.
Examples of issues CIEM security covers are not revoking long, unused credentials or giving unneeded wildcard permission to the EC2 instance.
Infrastructure as Code (IaC) Scanning
A big draw of the cloud-native ecosystem is the ability to automate everything an application needs to run. IaC can be things like templates for CloudFormation, Kubernetes manifests, Dockerfiles, or Terraform plans. The idea behind IaC scanning is to find obvious security flaws before they make it to production and cause problems.
IaC scanning solution should include the following:
- Prevent Drift: Scan IaC files before deployment. Map misconfigurations in production back to source.
- Prioritize Risk: Prioritize security fixes based on application context, requirements, and dependencies.
- Remediate at the Source: Receive fix recommendations at the source with auto-generated pull requests.
Runtime protection
Cloud Workload Protection (CWPP)
This is the part that operations teams would care the most about. A CWPP is the runtime enforcement part of the CNAPP security suite. It works towards having a zero trust model in place where nothing is automatically trusted.
It will perform actions like:
- Runtime detection: Detect and prevent suspicious behavior in containers at runtime. Automate response for container threats.
- System hardening: Protecting Linux hosts or VM-based workloads running on top of the host by reducing its vulnerability surface with restrictive configurations as a preventive control.
- Vulnerability management: Vulnerability detection in container images in the CI/CD pipeline and registries before deploying to production.
- Network security: Enforce Kubernetes-native network policies, including segmentation, and provide network traffic visualization down to the container level.
- Compliance: Validate container compliance and ensure File Integrity Monitoring inside containers.
- Incident Response: Forensics Analysis and incident response for Kubernetes and the containers it manages even after the container is gone.
Gartner recently emphasized the importance of the runtime security part and stated that “Favor CNAPP vendors that provide a variety of runtime visibility techniques, including traditional agents, Extended Berkeley Packet Filter (eBPF) support, snapshotting, privileged containers, and Kubernetes (K8s) integration to provide the most flexibility at deployment.”
Cloud Detection and Response (CDR)
Cloud Detection and Response (CDR) plays a vital role in a CNAPP by providing advanced threat detection, incident response, and continuous monitoring capabilities specifically designed for cloud environments. CDR within CNAPP leverages cloud-native security controls, such as cloud workload protection platforms (CWPP) and cloud security posture management (CSPM) tools, to gain real-time visibility into cloud assets, configurations, and activities. By continuously monitoring and analyzing cloud logs, network traffic, and user behavior, CDR helps detect indicators of compromise (IOCs), anomalies, and suspicious activities that could indicate a security incident or breach.
Once a potential threat or breach is detected, CDR enables rapid incident response by providing automated or guided response actions. It facilitates the containment, investigation, and remediation of security incidents, helping organizations minimize the potential impact and mitigate further risks.
Integrating CDR into CNAPP creates a comprehensive security solution that combines proactive cloud security controls, vulnerability management, secure coding practices, and continuous monitoring and response capabilities. It ensures that cloud-native applications are protected throughout their lifecycle, from development to deployment and beyond, safeguarding against emerging threats and enabling organizations to maintain a strong security posture in their cloud environments.
Why must CNAPP have Runtime Insights?
CNAPP is becoming a platform that ingests and analyzes multiple data sources. The data volume is exploding, as you factor in the adoption of microservices built on containers/Kubernetes. This can quickly result in a gargantuan volume of both high- and low-fidelity signals, ultimately raising the question: how do you focus on the most critical risks in your cloud native infrastructure?
This is where having deep knowledge of what’s running right now can help you shrink down the list of things that need urgent attention. Simply put, knowledge of what’s running (i.e., runtime insights) is the necessary context needed by security and DevOps teams to take action on the most critical risks first. Ultimately, this context can be fed back early in the development lifecycle to make “shift-left” use cases of CNAPP better with actionable prioritization.
Day-to-Day Examples of Runtime Insights in Action
Here are some examples where having a CNAPP will enable valuable and consistent enforcement of policies:
Example 1: In-use packages
The build teams have implemented security scanning in the build and test pipeline, which is fantastic. Let’s say an SCA tool is running against the registry where artifacts are stored, and is tagging them with known vulnerabilities from the CVE database. What happens if something that is already in production is tagged with a new critical alert? If it is severe enough, like Log4Shell vulnerability, then impacted applications need to either be immediately shut down or have the potential attack otherwise mitigated. A powerful CNAPP leverages runtime insights to identify if the vulnerable library is already in use or not and, accordingly, prioritizes risks and mitigation. Also, you should be able to automate the response to this type of event.
Example 2: In-use permissions
An organization utilizes Amazon Web Services (AWS) for their cloud infrastructure. A custom permission called “CreateS3BucketAdmin” was created for a specific project but is no longer in use. This permission grants full administrative access to create and manage S3 buckets within the AWS account.
This situation poses a significant security risk. If compromised, an attacker could leverage this unused permission to create and manipulate S3 buckets, potentially leading to data exposure, data loss, or unauthorized access to sensitive information.
A CNAPP can play a crucial role in identifying and mitigating such security risks. It can define policies automatically based on your users’ behavior and analysis of the permissions they typically use. This information can be used to generate baselines which are ideally codified, and then enforceable. This “in-use” permission policy works as filters and automatically generates recommendations and can make this process more efficient.
How does a CNAPP work?
CNAPP enables cloud security consolidation by combining the requirement for runtime risk visibility, cloud risk visibility, and development artifact risk visibility in one solid platform.
To have this integrated set of capabilities, CNAPPs generally follow two different instrumentation paradigms: agent-based and agentless.
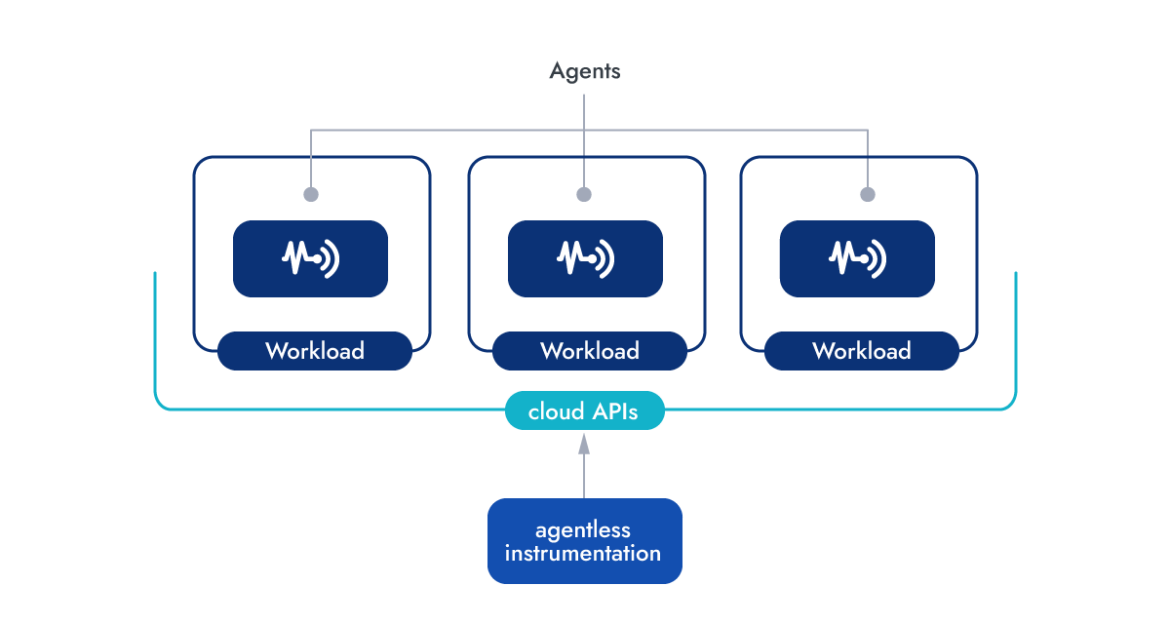
- Agent-based stays close to the workloads. It requires an agent (often called sensor or probe) executing alongside the workloads on the instrumented machine. Being on the same host grants real-time visibility on the runtime and allows access to system-level context information, something that is not available otherwise.
- Agentless is enabled by the APIs made available by cloud providers to gather relevant context without the necessity of an agent running along the workloads. It often leverages the ability to take snapshots to defer the security scans on a point-in-time copy, leaving the original workload unaltered. While this approach lacks the deep runtime insights that an agent provides, it offers a frictionless solution for tackling issues that do not need to rely on real-time data, like building an asset inventory, or identifying known vulnerabilities and anomalous behavior in audit logs.
A robust CNAPP solution needs to employ both instrumentation approaches to be as effective as possible. Use Agent for real-time visibility on the runtime and for better access to system-level context information, and Agentless to identify known vulnerabilities and anomalous behavior in audit logs.
Can a CNAPP solution integrate with my existing security tools and systems?
CNAPP requires integration into the runtime cloud environments and development pipeline tools that the development organization uses.
Integration into CI/CD Pipeline
CNAPP must integrate into your CI/CD development toolset to limit the risk of exposure from vulnerabilities and misconfigurations at build time. This integration is vital for artifact scanning, whether source code or a compiled binary, and it’s extended to cover artifacts audit/logging telemetry.
Integration with cloud providers
As agentless instrumentation evolves, CNAPP vendors increase their integration level with cloud providers to leverage the APIs made available to gather relevant context without needing an agent to run along the workloads.
Most of the existing CNAPPs support the three major cloud providers: Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP). In addition, some vendors expanded their integration to other providers like Oracle Cloud, IBM Cloud, Alibaba Cloud, VMware Tanzu, and others. So, make sure you choose the solution that supports your infrastructure.
Integration with Infrastructure as Code (Iac) tools
With this integration, CNAPPs scan IaC files before deployment and detect runtime drift. An example would be Git Integrations to scan incoming Pull Requests (PRs) for security violations based on predefined policies. The results of the scanning evaluation are presented in the PR itself. If passed, the user can merge; if failed, the user cannot merge. Information provided in the PR also targets the problem area to assist the user in remediation.
Integration with key management systems (KMS)
This is mandatory to allow the scanning of encrypted or signed resources for risk.
Case Study: How a leading Bot Mitigation company achieved cost savings, alert reductions, and tool consolidation with CNAPP
A leading Bot Mitigation company recently adopted a CNAPP to bolster its cloud security infrastructure. By implementing CNAPP, the company achieved significant benefits, including the consolidation of security tools, reduction in alerts, and cost savings.
Prior to CNAPP adoption, the company utilized six different security tools, each serving a specific security function within their cloud environment. This fragmented approach resulted in operational complexities, overlapping functionalities, and increased maintenance costs. With the introduction of CNAPP, the company was able to consolidate all security tools into a single platform, streamlining their security operations and reducing administrative overhead.
The CNAPP implementation also proved instrumental in optimizing the alert management process. By leveraging the platform’s advanced threat detection and response capabilities, and Runtime Insights to focus on in-use packages and prioritize risk, the company experienced a remarkable 30% reduction in the number of security alerts generated. This improvement was achieved through intelligent and context-driven alert prioritization, empowering the security team to focus on the most critical threats while minimizing noise and false positives. Consequently, the team’s efficiency and responsiveness significantly improved, allowing them to promptly address genuine security incidents.
Moreover, the consolidation of security tools with CNAPP brought about substantial cost savings. By eliminating the licensing fees, maintenance costs, and operational overhead associated with multiple security tools, the organization achieved a 20% reduction in overall security expenditures. The simplified management and streamlined operations provided by CNAPP not only reduced costs but also freed up valuable resources, allowing the company to allocate them to other strategic initiatives.
Overall, the adoption of CNAPP led to a consolidated security infrastructure, streamlined alert management, and significant cost savings. This comprehensive and unified approach to cloud security resulted in enhanced operational efficiency, improved incident response capabilities, and a strengthened security posture for the organization.
What benefits can a CNAPP tool provide for my organization?
1. Enhanced cloud security
CNAPP is an End-to-End solution that provides breadth across any workload, cloud, or service, allowing organizations to maintain consistent threat detection and visibility regardless of their cloud infrastructure. It also offers depth that comes from combining various techniques, such as machine learning (ML), rules, threat feeds, etc., enabling it to detect and respond to threats effectively. CNAPP also reduces the attack surface in cloud-native environments by providing attack path analysis, highlighting gaps in environment configuration as a type of preventive control.
2. Real-Time Threat Detection
CNAPP offers advanced threat detection capabilities in real time. It leverages cloud-native security controls and runtime visibility techniques to identify security incidents, anomalies, and indicators of compromise (IOCs) promptly. CNAPP provides end-to-end detection, enabling organizations to respond swiftly to emerging threats and minimize the impact of security breaches.
3. Simplified Compliance
CNAPP helps organizations meet regulatory and compliance requirements by offering security controls and mechanisms that align with industry standards and best practices. It assists in identifying and remediating security vulnerabilities, ensuring that applications adhere to compliance frameworks such as PCI DSS, HIPAA, GDPR, etc.
4. Improved DevOps Collaboration
CNAPP promotes collaboration and alignment between development and security teams, and finds a balance between security and digital innovation. It integrates with DevOps tools and processes, enabling security to be seamlessly incorporated into continuous integration and continuous deployment (CI/CD) pipelines.
5. Operational Efficiency
By consolidating security controls and providing centralized management, CNAPP simplifies security operations. It offers a single pane of glass for detection, response, and managing security events.
Conclusion
With CNAPP, organizations can consolidate cloud-native security tools, streamline operations, prioritize risks, and enhance their overall security posture.
By leveraging CNAPP’s runtime insights, businesses can:
- Prioritize risks based on what’s used by the organization.
- Enable continuous and Real-Time Detections.
- Enhance data visualizations that highlight where gaps are present in environment configuration using Attack Path Analysis.
- Achieve End-To-End detection on everything in cloud environments.

