In this blog, we introduce the new integration between Sysdig Secure and Red Hat® Advanced Cluster Management for Kubernetes that protects containers, Kubernetes, and cloud infrastructure with out-of-the-box policies based on the Falco open-source runtime security project.
Organizations are quickly growing their Kubernetes footprint and need ways to achieve consistent management and security across clusters. Sysdig and Red Hat are collaborating to help users deploy apps, simplify management, and enforce configuration and policy management across multiple clusters at scale.
What is Red Hat Advanced Cluster Management for Kubernetes?
Red Hat Advanced Cluster Management for Kubernetes is a management solution designed to help organizations extend and scale Red Hat OpenShift, the leading enterprise Kubernetes platform. As cloud teams deploy more and more Kubernetes clusters to support cloud-native applications, enterprises need a way to consistently manage and secure their expanding environments. Red Hat Advanced Cluster Management for Kubernetes enables management consistency across the hybrid cloud deployments including on-premises and public clouds like Amazon Web Services, Google Cloud Platform, IBM Cloud, and Microsoft Azure.
Key capabilities of Red Hat Advanced Cluster Management for Kubernetes:
- Unified multi-cluster management – Centrally create, update, and delete Kubernetes clusters across multiple private and public clouds.
- Policy based governance, risk and compliance – Centrally set and enforce policies for security, applications, and infrastructure.
- Advanced application lifecycle management – Define and deploy applications across clusters based on policy.
- Centralized visibility of hybrid cloud container environment performance – Get a unified view of cluster health and performance with integrated open source projects Thanos and Grafana, making it easier to maintain optimal metrics for cluster operations.
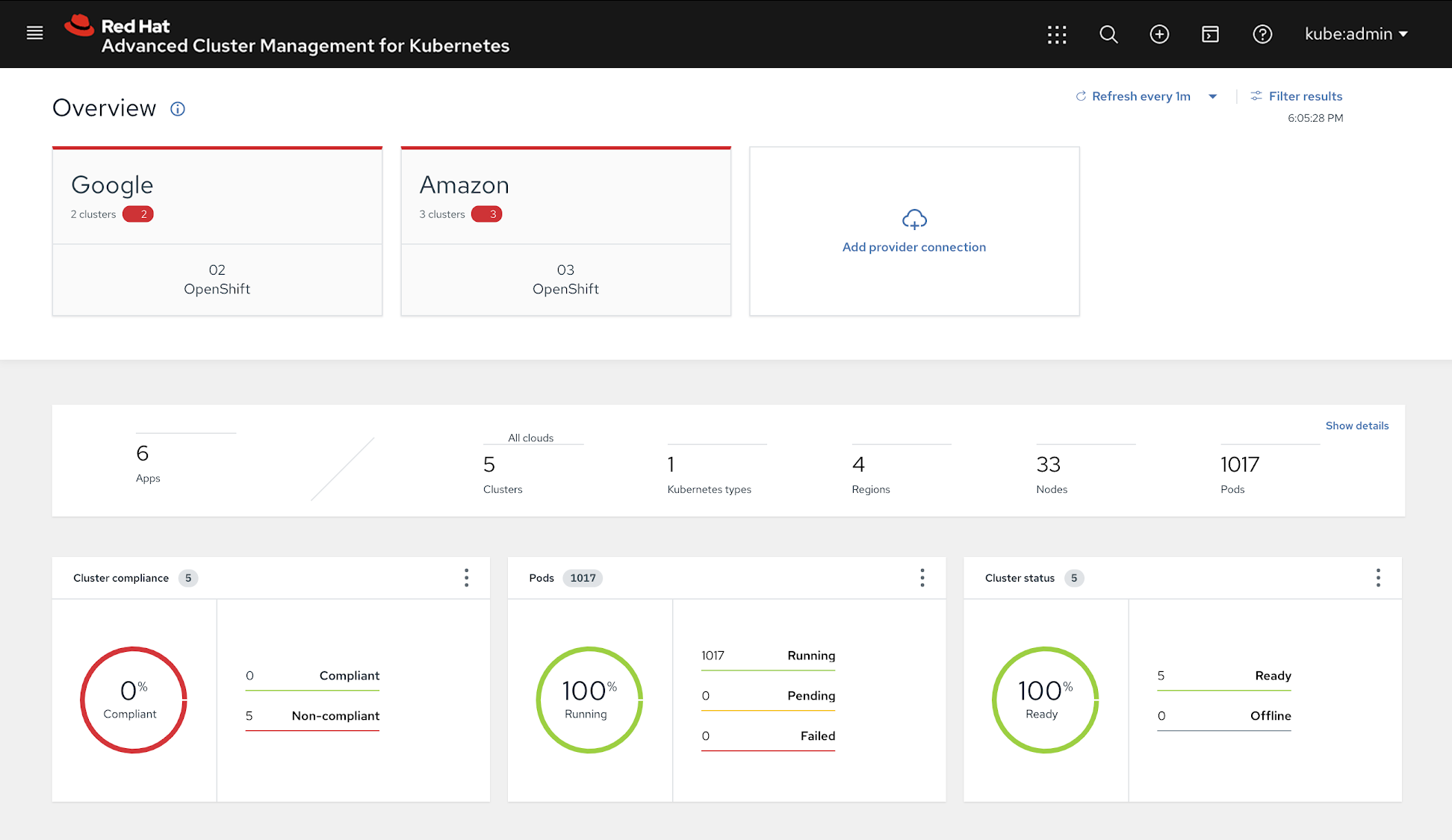
Multi-cluster security with Sysdig Secure and Advanced Cluster Management
Sysdig Secure addresses the unique security challenges of containers, Kubernetes and cloud. It helps cloud teams confidently secure the build pipeline, detect and respond to runtime threats, continuously validate compliance, and perform container forensics.
Working with Red Hat, Sysdig has enabled integration of Sysdig Secure into Red Hat Advanced Cluster Management to centralize container security deployment and runtime policy management to gain deep visibility into security events. This combination helps cloud teams detect threats, enforce compliance, and audit activity in real-time across Kubernetes clusters.
Jaya Ramanathan, Distinguished Engineer, Chief Security & Governance Architect at Red Hat, explains, “The policy-based governance capability of Red Hat Advanced Cluster Management for Kubernetes enables enterprises to operate to internal and external standards related to security, resiliency, and software engineering. Customers can implement these standards using built-in OpenShift features as well as take advantage of partner provided capabilities. ACM policies ensure these features are in place and configured to enforce industry best practices.”
“Sysdig Secure integration with ACM enables DevOps teams to use policy-based governance to ensure container integrity monitoring controls are deployed and leveraged at scale to detect threats and analyze root cause for quick resolution.”
How Sysdig with ACM works
Red Hat Advanced Cluster Management for Kubernetes supports the creation of custom policies to integrate third-party controls with its Governance Risk and Compliance (GRC) framework. Using this facility, Sysdig has created a custom policy that deploys the Sysdig agent on all targeted clusters using the Sysdig operator.
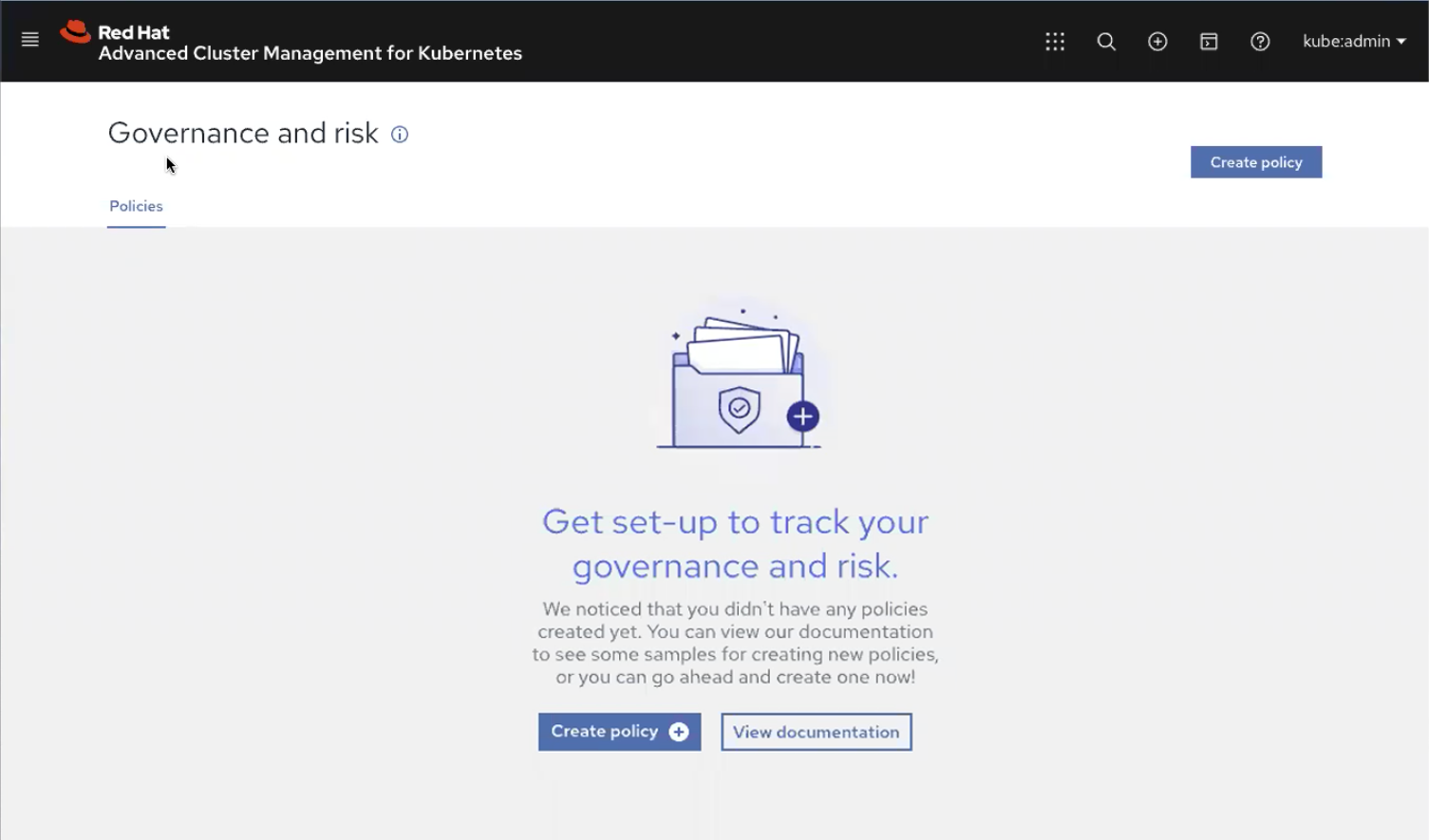
To get started, you can select create policy in the Governance and risk section of the ACM interface and insert the pre-built policy-sysdig.yaml provided by Sysdig on GitHub.
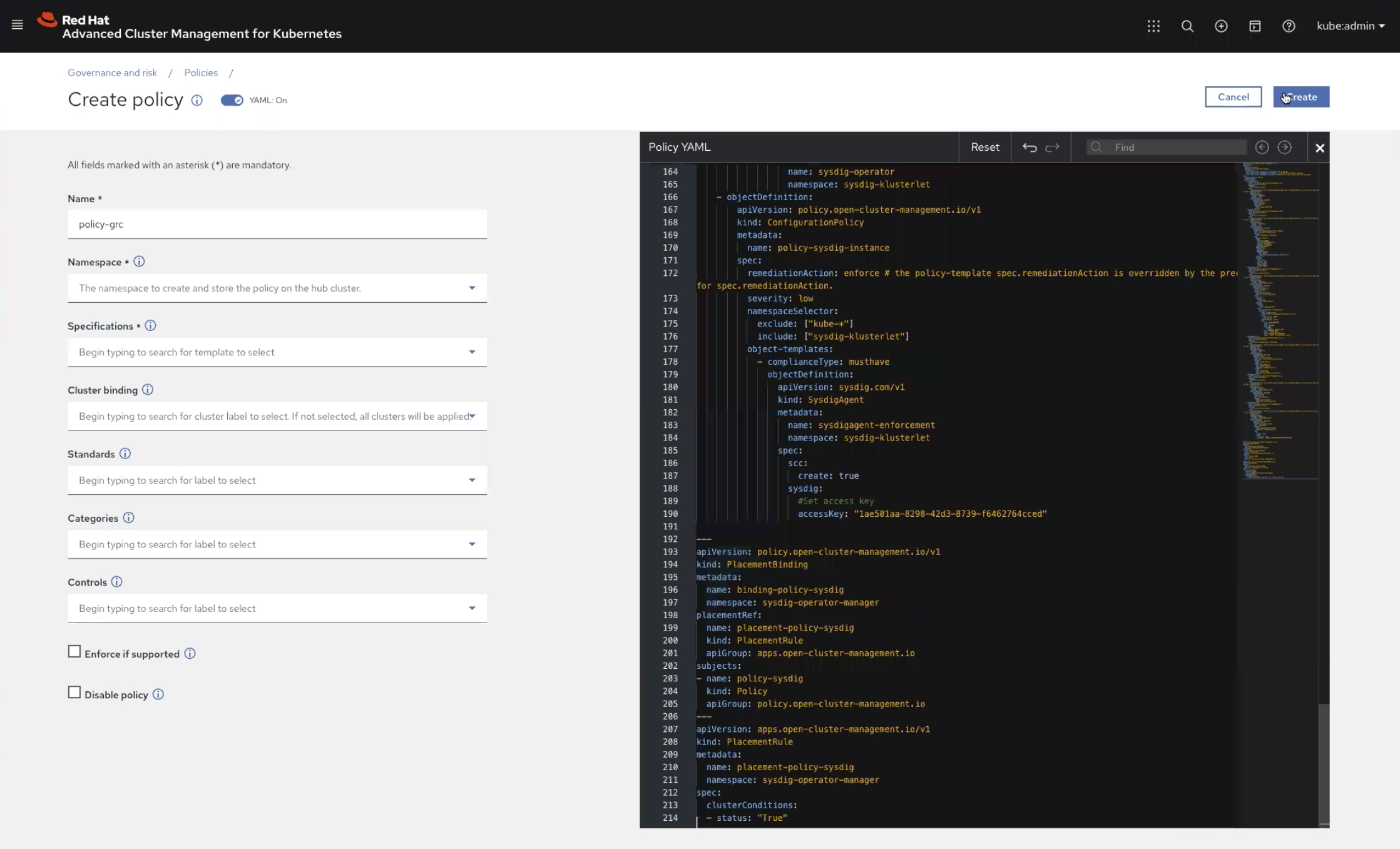
Once you select create, the policy ensures that the Sysdig agent is deployed to the nodes on all specified clusters. When successfully completed, you’ll get a green checkmark confirmation and see the word Compliant, indicating that runtime security visibility is active and available.
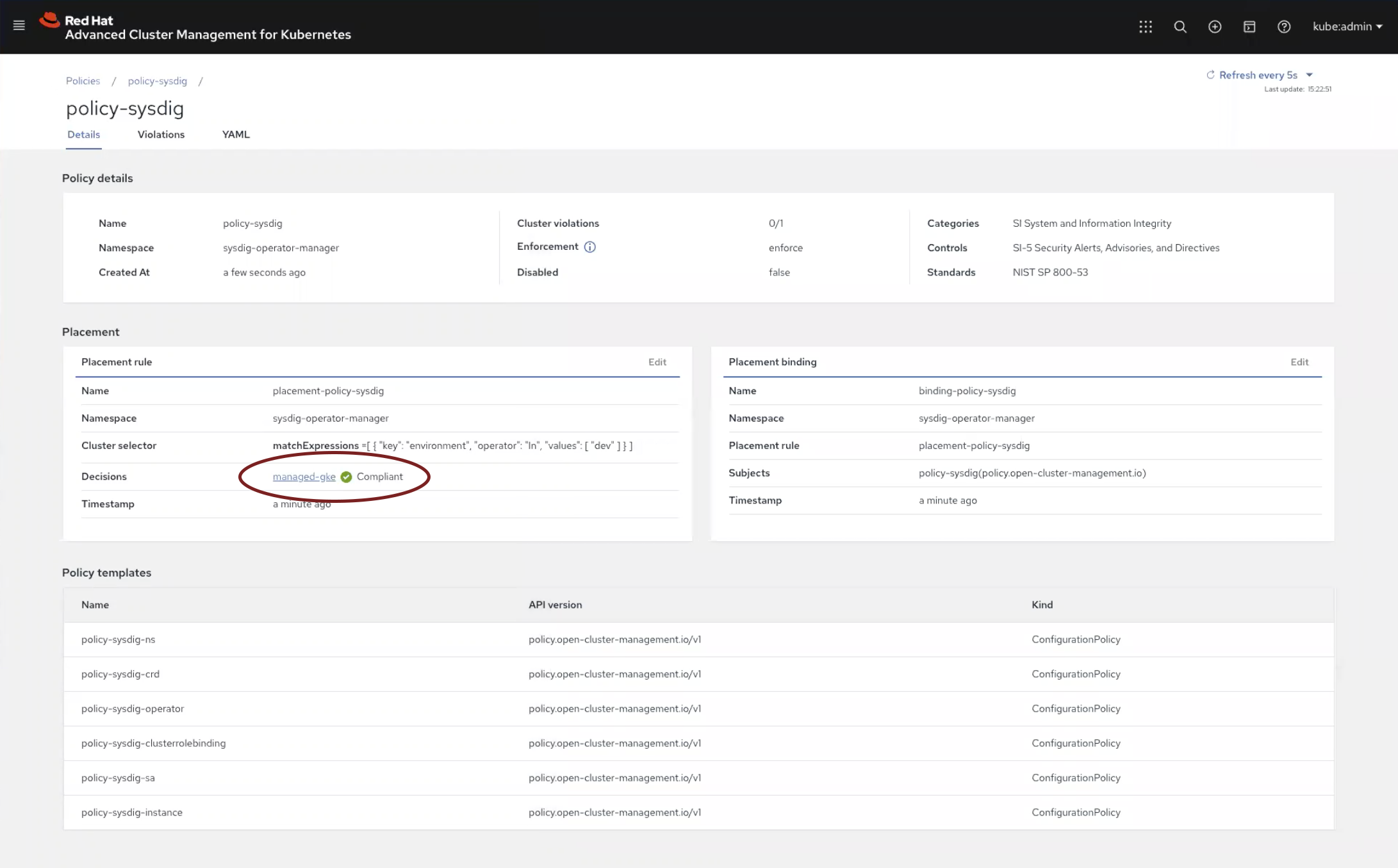
Visibility and Security for Containers, Hosts, and Kubernetes
Sysdig Secure is built on Falco, the open-source CNCF® runtime security project originally created by Sysdig. With it, DevOps teams can enable out-of-the-box security and compliance policies as well as define custom security rules to detect and respond to zero-day threats and anomalous activity at runtime.
Here are a few examples of the runtime security detections included with Sysdig Secure:
|
|
|
|
|
|
|
|
|
|
|
|
|
|
In addition, Sysdig has translated leading security standards like NIST SP 800-190, PCI DSS, and HIPAA into a set of curated detection policies to simplify achieving compliance within your OpenShift and Kubernetes clusters.
Detections take place leveraging a single source of truth based on granular Linux syscall data as well as other rich data sources such as Kubernetes Audit Logs and AWS CloudTrail. In addition to specifying what to detect, Sysdig Secure policies can be configured to send alerts and automatically remediate by triggering response actions such as pause or kill containers to block threats.
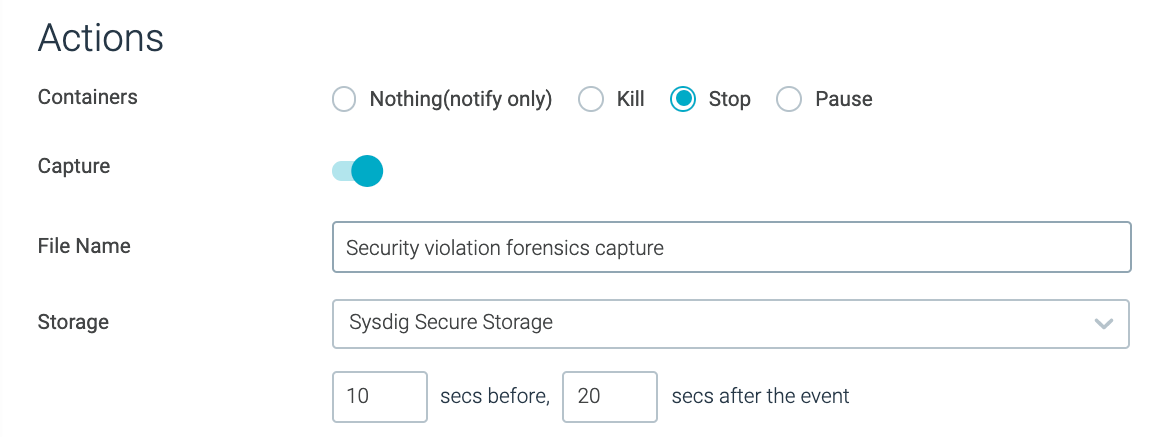
What’s more, you can also configure a policy to create a capture file that is a recording system activity before, during, and after a triggered event to support incident response and forensics – even after containers are gone.
As events occur across the managed OpenShift and Kubernetes cluster environments, detailed information about policy violations, including host, Kubernetes, and container location, and detailed activity audit and capture data are available to support investigation and resolution by DevOps and security teams.
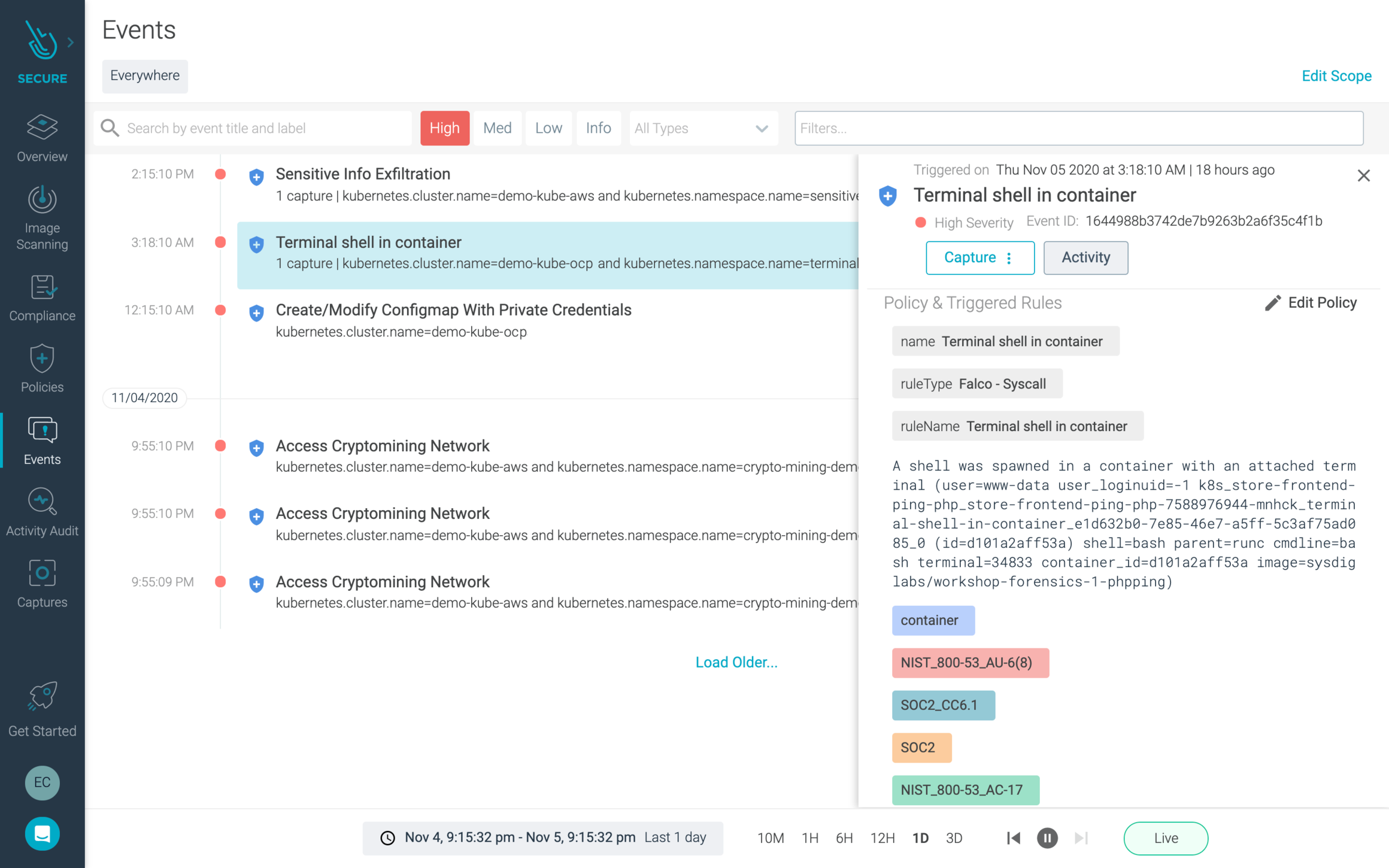
To learn more about all of the ways Red Hat and Sysdig extend security for OpenShift environments check out our Security Guide.
Get started today
As enterprises begin to move from initial Kubernetes deployments to running cloud-native applications across multiple clusters and clouds, the operational challenges of management, governance, compliance, and security are amplified.
Red Hat and Sysdig help provide the visibility, governance, and control that organizations need to easily grow and manage their container environments. With Red Hat Advanced Cluster Management for Kubernetes, users have a single view to create and manage clusters reliably, consistently, and at-scale. Sysdig adds the deep visibility and security automation needed to keep pace with threats, reduce risk, and confidently run containers, Kubernetes, and cloud services.
A special extended free trial of the Sysdig Secure DevOps Platform is now available for Red Hat users. You can experience the combined solution today – and it’s easy to get started. Just click here.


