
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Identities have become one of the most common ways modern threat actors gain a foothold in the cloud. From stolen credentials to overly permissive roles and privilege escalation, attackers use a range of tactics to exploit identities and use them to launch devastating breaches. Once inside your environment, they can move laterally, exploit resources, or steal sensitive data, leaving security teams scrambling to contain the damage. Numerous major attacks in the last year, including ones targeting Snowflake and Ticketmaster, have exploited compromised users.
The frequency of these identity-based attacks highlights how critical it is to detect early in the attack chain. Detecting compromised users in real time can stop attackers in their tracks, while measures like enforcing least permissive access policies can prevent attacks before they happen. With better visibility into identity activity, organizations can limit their exposure and respond more effectively when a breach occurs. Strong cloud infrastructure entitlements management (CIEM), combined with tools to flag risky users and roles, are key to staying ahead of attackers.
To tackle identity-based threats head-on, organizations need to shift from reacting to incidents to addressing them proactively. By leveraging identity context and enforcing zero-trust principles, security teams can both reduce their attack surface and respond with precision when threats emerge.
Stolen credentials fuel AI attacks
Compromised identities are often the starting point for attacks targeting not only sensitive data, but also valuable resources like AI workloads, which are becoming a prime target for attackers. Sysdig’s Threat Research Team (TRT) observed one case in May 2024 where threat actors used stolen cloud credentials to target cloud-hosted large language models (LLMs), known as LLMjacking. Once access to the LLM is obtained, attackers can sell access to it for financial gain or take advantage of the free LLM resource access themselves. The stolen enterprise access in the identified LLMjacking attack was a local Anthropic Claude 2.x model that could cost victims up to $46,000 per day, but model advancements and price increases can now run victims over $100,000 daily. Beyond the financial impact, attackers can also go after valuable training data, showing just how dangerous these identity-driven breaches can be.
Sysdig expects attacks like LLMjacking to become more common in 2025. As threat actors automate their efforts and use AI to scale operations, it will be even harder for security teams to keep up. The best defense starts with catching compromised users early, stopping attackers before they can exploit cloud environments.
Detecting compromised users
The best way to find compromised users is by monitoring identity behavior for signs of suspicious activity. Indicators like unusual logins, privilege escalation attempts, or sudden spikes in API calls are often the first signals of an attack. It’s not just about spotting these warning signs — security teams also need the context to understand what’s happening, so they can quickly stop attackers from exploiting compromised accounts.
Sysdig Cloud Identity Insights help customers streamline this process with the context they need to get ahead of attacks and take action. A strong defense starts with identifying unusual activity, like a user probing resources they don’t typically access, engaging in reconnaissance, or attempting privilege escalation. But the work doesn’t stop there. From there, teams need to be able to rapidly investigate and confirm whether an account is truly compromised. This is where having the right context makes all the difference — understanding the timeline, scope, and related activity can help teams act fast and avoid wasting time on false positives. Once compromise is confirmed, containing the threat becomes the priority, whether that’s revoking credentials, locking down access, or isolating the account. By taking these steps, organizations can stay ahead of attackers and keep their cloud environments secure.
Identifying the riskiest users and roles
While detecting compromised users is critical to stopping breaches, attacks will keep happening unless organizations also focus on strengthening their security posture and improving identity hygiene. Pinpointing the riskiest users and roles in your cloud environment is a great way to prevent breaches before they start. Sysdig helps with built-in risk policies that highlight users and roles that pose the highest threats. By focusing on these risky users and roles, security teams can prioritize their efforts and shore up their defenses where they’re needed most.
There are several factors that can make a user or role particularly risky. Accounts without multi-factor authentication (MFA) are an obvious target, as they’re easier to compromise. Roles with excessive permissions, especially administrator privileges, can open the door to lateral movement or privilege escalation if they fall into the wrong hands. Inactive or orphaned accounts can also be a problem — forgotten but still accessible. Another red flag is accounts that don’t rotate access keys regularly, leaving static credentials vulnerable to theft or misuse. By identifying these risk factors, Sysdig helps security teams zero in on the accounts that require the most attention.
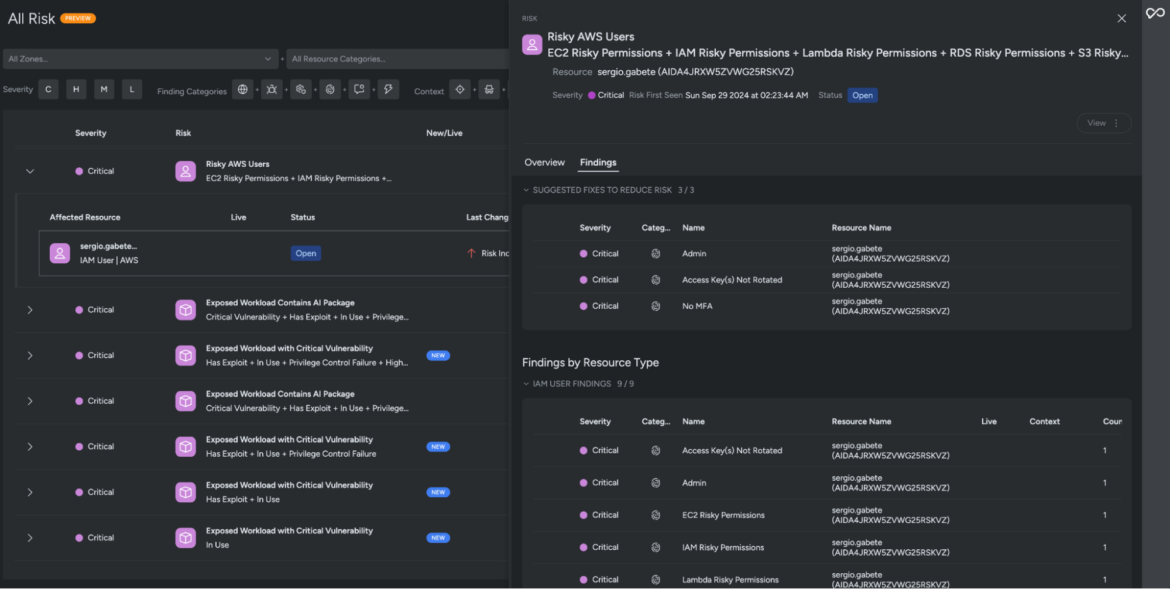
The goal isn’t just to find risky users and roles, but to act on that information. Enforcing least privilege policies, adding MFA, tightening permissions, and enforcing key rotation policies are some of the steps teams can take to reduce risk. By tackling the identities that are most likely to be exploited first, organizations can stay ahead of potential threats.
Conclusion
Compromised identities and risky roles are some of the most common ways attackers gain access to cloud environments. Detecting suspicious activity early and fixing gaps in identity hygiene can go a long way toward preventing breaches. By focusing on both immediate detection and long-term posture improvements, organizations can reduce their exposure and make it harder for attackers to succeed.
Sysdig helps security teams take on these challenges with solutions like CIEM and Cloud Identity Insights. By providing real-time visibility into identity behavior and highlighting risky users and roles, Sysdig makes it easier to catch threats early and stay ahead of attackers.
Want to learn more about how to secure your identities? Don’t hesitate to reach out to connect with one of our experts!



