Permissions & Entitlement Management
Optimize Identities and Access in the Cloud
98% of granted cloud permissions are not used. Eliminate excessive entitlements with access policies based on in-use permissions and real-time incident data. Gain visibility into cloud identities and enforce least privilege with cloud infrastructure entitlement management (CIEM).
Address Excessive Permissions Risks in Minutes
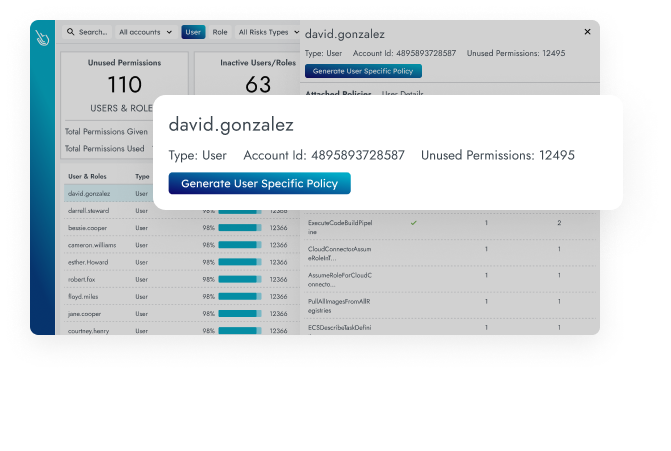
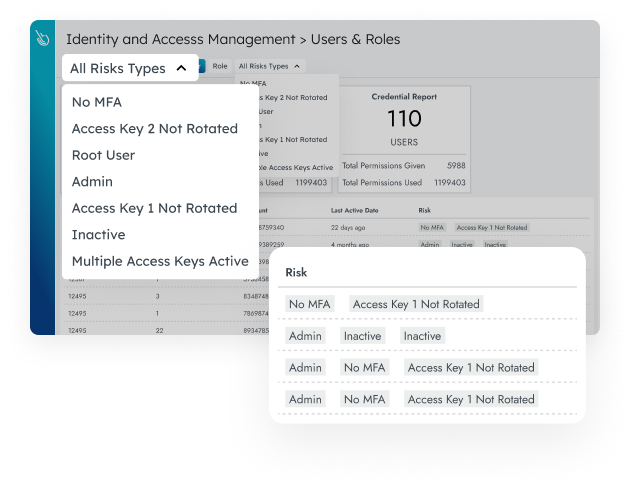
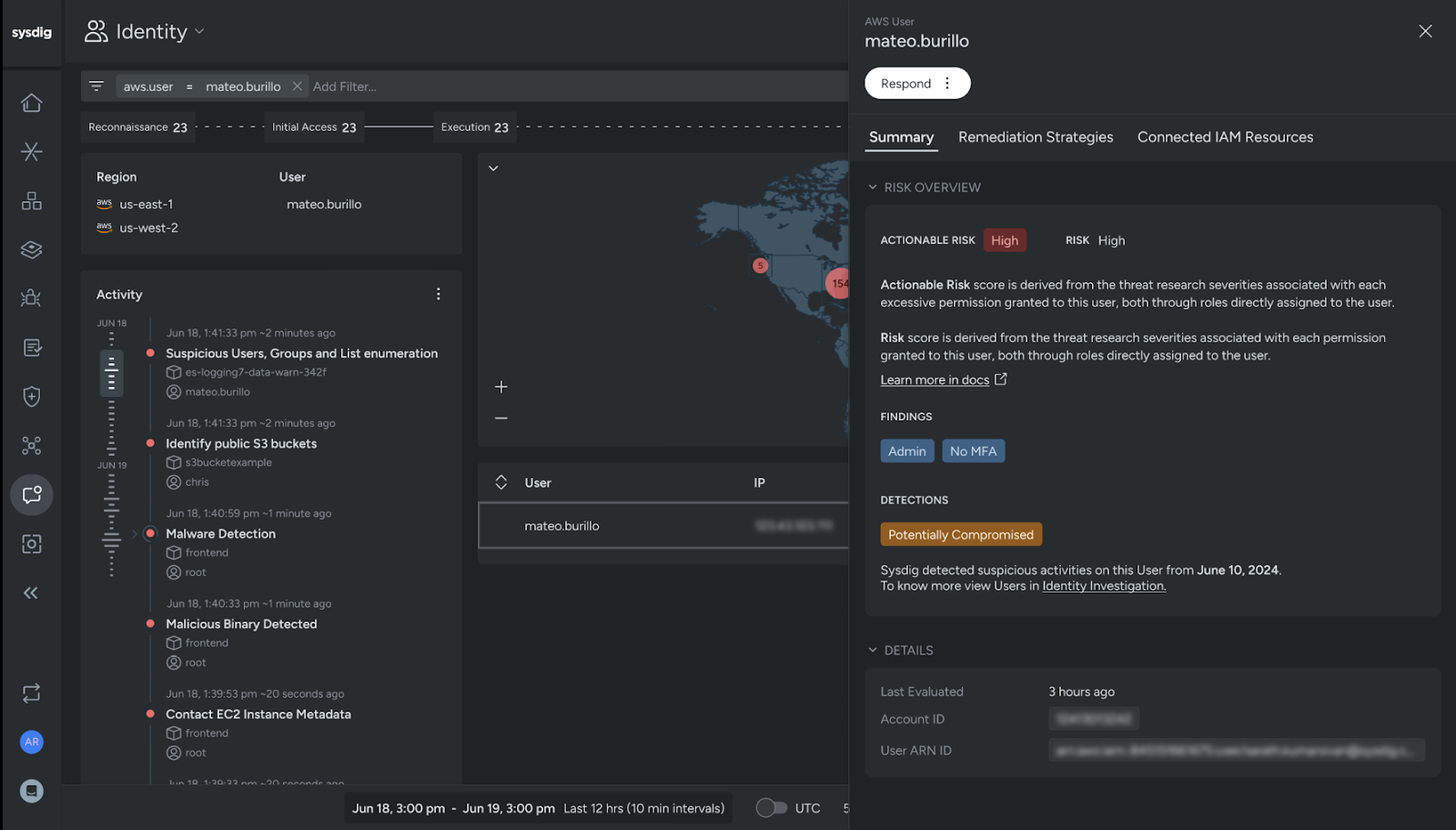
Identify inactive users and identities with excessive permissions. Optimize access policies to grant just enough privileges.
-
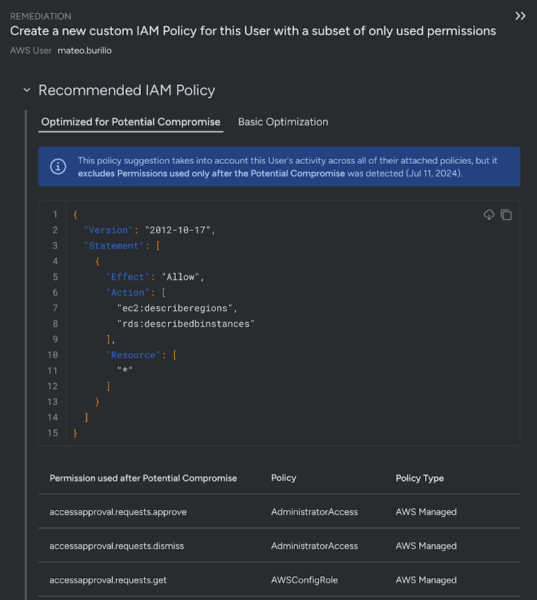
Enforce least privilege
Right-size permissions using automatically generated policies, with a view of in-use permissions across your clouds.
-
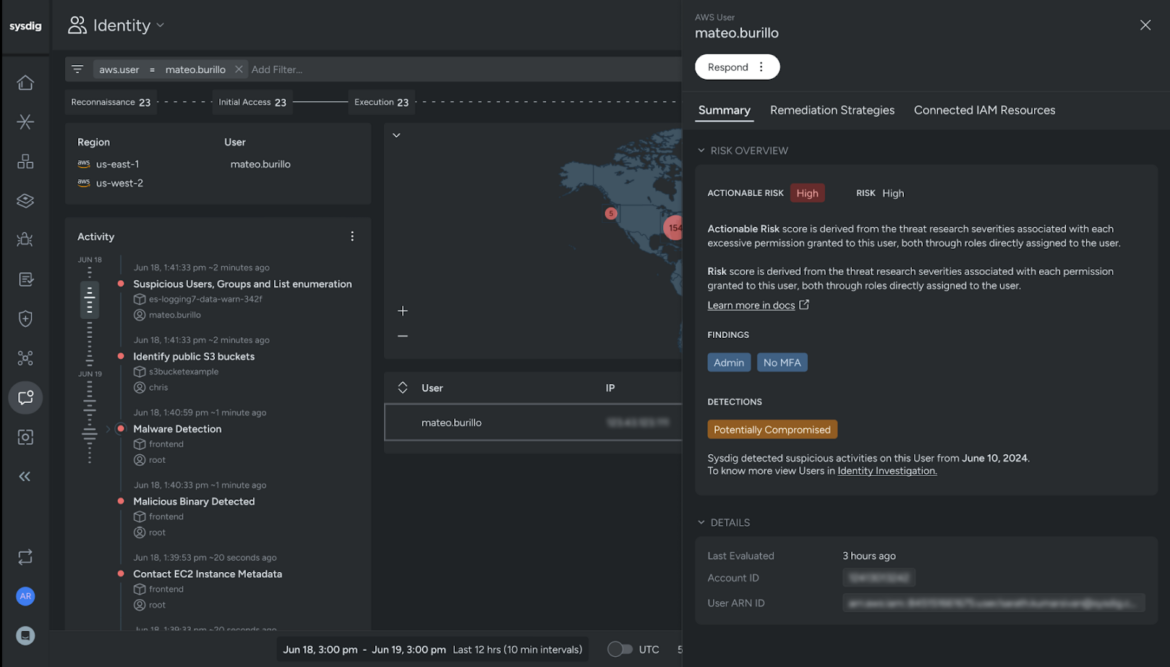
Identify compromised users
Analyze identity activity patterns to identify users that are actively compromised, as well as other risky users and roles.
-
Simplify compliance
Meet specific identity and access management requirements for standards, including PCI, SOC 2, NIST, ISO 27001, and more.
Harden cloud security posture with CIEM
Inadequate identity and access management (IAM) is one of the most common causes of security failure. Sysdig’s CIEM uses runtime insights to optimize permissions for overprivileged users.
Prioritize risk with runtime Insights
Sysdig’s runtime insights provide unique visibility to focus on the most significant risks. Only Sysdig offers:
Take the Next Step!
See how you can secure every second in the cloud.