
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

As cyber threats continue to evolve, the European Union (EU) has introduced two pivotal regulations to enhance cybersecurity: the Digital Operational Resilience Act (DORA) and the Network and Information Security Directive (NIS2), which revises and replaces NIS. These frameworks establish comprehensive standards for compliance, risk management, and incident reporting, aiming to bolster the cybersecurity posture of modern organizations across Europe.
Navigating these regulations can be complex, but Sysdig simplifies the process. As the first Cloud-Native Application Protection Platform (CNAPP) to offer out-of-the-box compliance policies for DORA and NIS2, we assist businesses in aligning with these requirements while enhancing their security measures.
The impact of DORA & NIS2
Previously, cybersecurity compliance audits were conducted periodically — monthly, quarterly, or annually. However, the dynamic nature of cyber risks necessitates more immediate responses. DORA and NIS2 introduce updated reporting requirements to ensure timely action:
- DORA, effective January 17, 2025, mandates that financial entities report major incidents within four hours of classification.
- NIS2, effective October 17, 2024, requires breaches to be reported within 24 hours.
Digital Operational Resilience Act (DORA)
DORA standardizes digital resilience practices across the financial sector, ensuring organizations can withstand, respond to, and recover from Information and Communication Technology (ICT)-related disruptions. It applies to a broad spectrum of financial entities, including:
- Banks and credit institutions
- Investment firms
- Insurance companies
- Asset managers
- Payment service providers
- Crypto-asset service providers
Significantly, DORA extends regulatory oversight to third-party ICT providers, such as cloud services, granting financial regulators the authority to supervise and audit these vendors. The regulation also emphasizes the importance of multi-cloud strategies to enhance resilience, necessitating consistent security controls to manage risks across diverse cloud environments.
Network and Information Systems Directive (NIS2)
NIS2 expands cybersecurity requirements to a wider array of critical sectors beyond the financial industry, including:
- Energy and water supply
- Transportation
- Healthcare
- Digital infrastructure
- Space
- Public administration
The directive introduces stricter security requirements and enhances accountability for organizations within these sectors. Notably, NIS2 mandates that member states impose administrative fines for non-compliance, with penalties reaching up to €10 million or 2% of the organization's total worldwide annual turnover of the preceding financial year, whichever is higher. This underscores the critical importance of adhering to these enhanced cybersecurity standards.
Sysdig's role in supporting DORA and NIS2 compliance
Understanding the specifics of these frameworks can be challenging. A practical approach is to break down the complex requirements into fundamental building blocks — which is exactly what we'll do in the next section.
How Sysdig supports DORA compliance
Sysdig helps organizations comply with DORA by providing comprehensive security controls across:
- Linux environments
- Kubernetes clusters
- Cloud infrastructure
- Identity management
Both DORA and NIS2 introduce technical security requirements for cloud environments.
In the following section, we'll outline these requirements and demonstrate how Sysdig's security controls ensure cloud assets remain compliant with DORA standards.
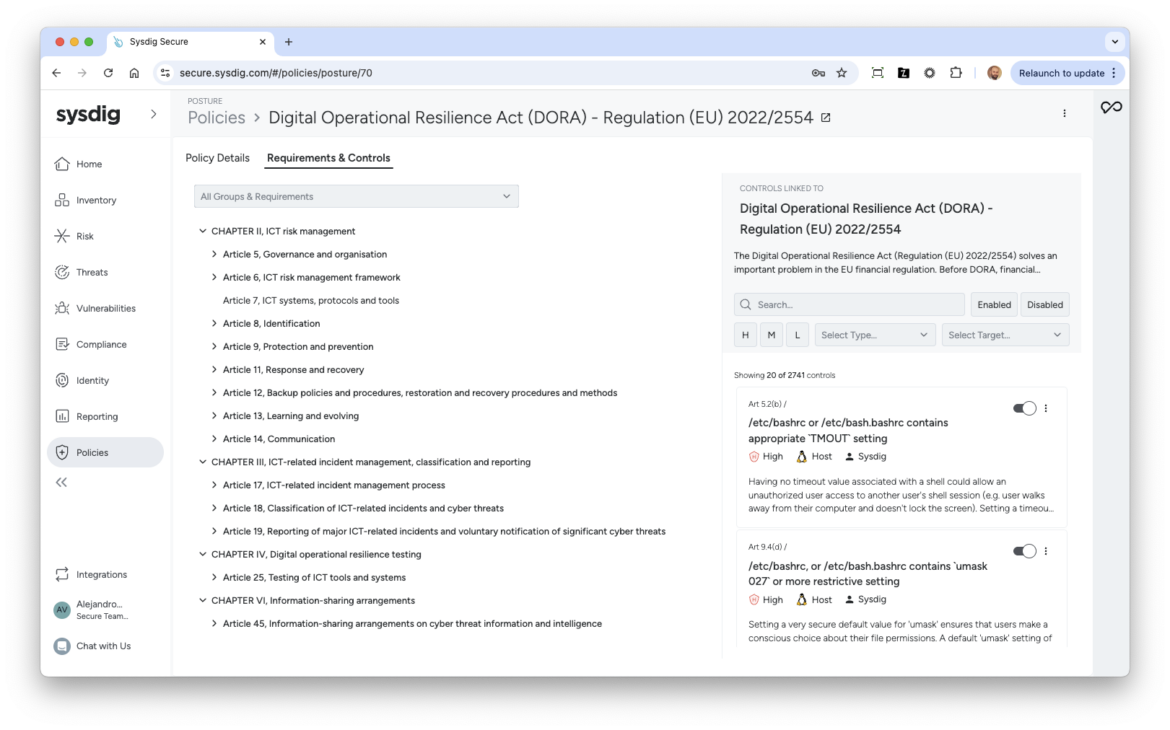
These are just some examples of the technical requirements of DORA. Our comprehensive policy extends beyond these examples.
How Sysdig supports NIS2 compliance
While NIS2 shares many similarities with DORA, its scope is broader, covering all critical infrastructure sectors. This includes not only healthcare, utilities, and telecom providers but also digital service providers. Entities are classified as either essential or important, with varying levels of security controls, monitoring requirements, and attestation obligations.
Sysdig supports compliance with all 14 technical requirements of NIS2, implementing 2,905 security controls to help organizations meet these standards.
Most of these technical requirements fall under Article 21, titled "Cybersecurity Risk-Management Measures", within Chapter IV: Cybersecurity Risk-Management and Reporting Obligations. Below, we'll explore key technical requirements in more detail.
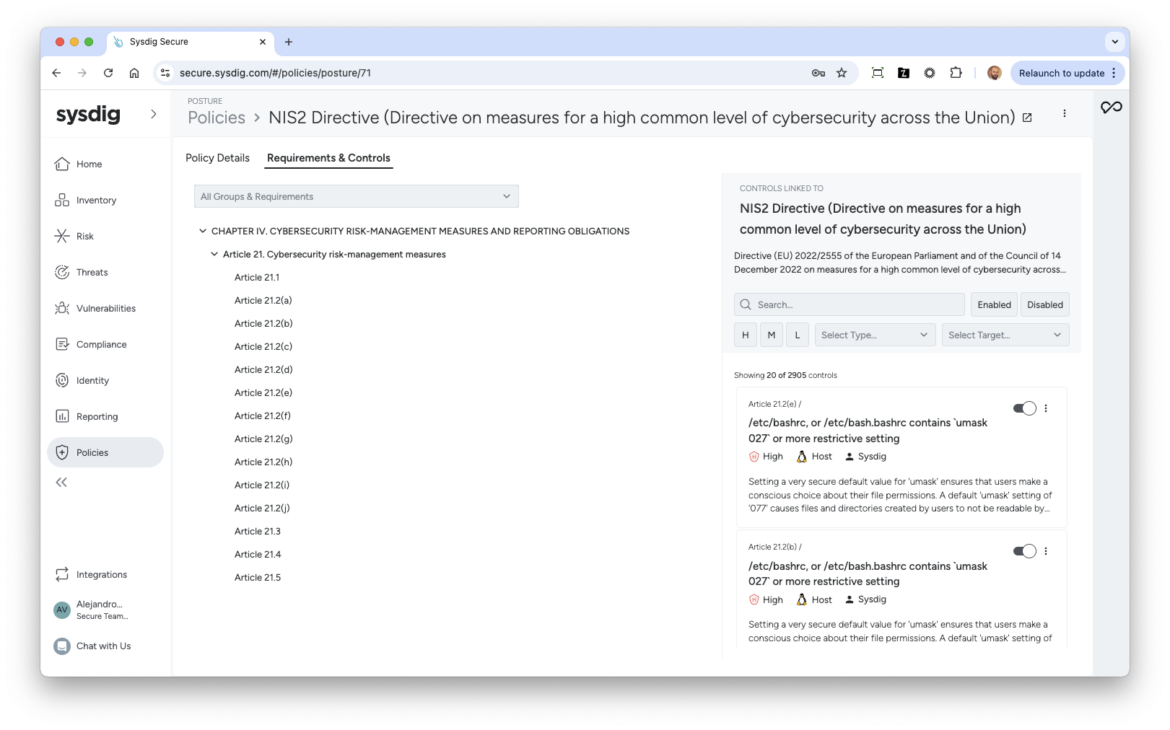
These are just some examples of the technical requirements of NIS2. Our comprehensive policy extends beyond these examples.
Conclusion
The NIS2 directive and DORA regulations represent key advancements in the European Union's efforts to enhance cybersecurity and operational resilience across many critical sectors, with particular prioritization of the financial industry. Now in effect, these frameworks require organizations to implement comprehensive security measures to safeguard their networks and information systems against evolving cyber threats.
Sysdig is uniquely positioned to support organizations in meeting these requirements not just as a security tool to check the box, but as a strategic partner. With Sysdig, businesses can confidently streamline compliance, strengthen security, and adapt to the ever-evolving regulatory landscape.



