What is a CNAPP?
A cloud-native application protection platform (CNAPP) is your all-in-one cloud security solution. It looks after your cloud-based apps and infrastructure, offering centralized controls, threat detection, and incident response capabilities.
Gartner defines CNAPP as “a unified and tightly integrated set of security and compliance capabilities designed to secure and protect cloud-native applications across development and production. CNAPPs consolidate a large number of previously siloed capabilities, including container scanning, cloud security posture management, infrastructure as code scanning, cloud infrastructure entitlement management, runtime cloud workload protection, and runtime vulnerability/configuration scanning.”
Before we delve deeper, let’s take a step back to quickly review the evolution of cloud security, and where CNAPP fits in.
What is a CNAPP?
What you’ll learn
-
What CNAPP is and how it helps consolidate posture, workload protection, identities, and detection & response
-
How to choose the right CNAPP solution for your org + best practices for implementing it
-
How one company uses CNAPP to cut costs, automate more, and improve security
The road to CNAPP
Before CNAPP entered the market, businesses faced a rocky path when it came to securing their cloud operations due to limited and fragmented security resources. Back in the 2000s, as the cloud began to take off, security vendors raced to adapt their traditional security solutions for this new frontier. Tools like firewalls, virtual private networks, and intrusion detection systems were implemented to protect cloud infrastructure against unauthorized access.
But here’s the catch: as cloud computing gained momentum and applications became more complex, this siloed approach to cloud security fell short. Traditional security measures struggled to keep up with the dynamic and distributed nature of cloud environments. This led to visibility blind spots, inconsistent policy enforcement, and an inability to tackle the complete range of cloud security risks.
Likewise, cloud ops security (the day-to-day protection of the applications, software, and workloads in a company’s cloud environment) and development security (protection of an organization’s application code base running in the cloud) were treated as separate security functions. This separation of tool sets made security still more siloed, thereby adding to the challenges organizations faced. As more security tools were added, visibility gaps widened, and organizations struggled to effectively manage the growing number of tools.
By the mid-2010s, two significant developments reshaped the cloud security landscape:
- With the emergence of new visibility gaps, cybercriminals found fresh incentives to target cloud-based infrastructure and services. This led to a surge in cyber attacks within cloud environments — and a surge in companies falling prey to data breaches in the cloud. Because organizations had limited visibility into the cloud surface, breaches could remain undetected for extended periods.
- In response to these breaches, cloud service providers (CSPs) introduced the shared responsibility model. This model divides security responsibilities between the CSP and its customers, outlining areas where a customer is in charge of their own security as they migrate applications, data, containers, and workloads to the cloud.
As cyber threats mounted, and organizations were given greater responsibility to safeguard their own cloud infrastructure, the market witnessed a whirlwind of innovation in cloud security technologies. This frenzy gave birth to CNAPP solutions. CNAPPs combine the functions of what were previously many separate security tools. In this way, they offer an integrated approach to cloud security that empowers organizations to overcome the limitations of traditional security tools.
What problems does a CNAPP solve?
The arrival of CNAPP solutions is a big deal because they simplify cloud security in meaningful ways that are easy for everyone to understand. Let’s break down the problems they solve:
- Tool sprawl
With CNAPP solutions, organizations can say goodbye to the headache of juggling multiple technologies. By offering a single, unified platform, CNAPPs consolidate CSPM, CIEM, IAM, CWPP, data protection, and more in one platform. This means no more scrambling to manage a bunch of different tools — CNAPPs streamline and simplify everything for you. - Lack of end-to-end protection
CNAPP solutions provide rock-solid security to keep your sensitive cloud-stored data safe from prying eyes. How? By beefing up your defenses with robust access controls, encryption, and vigilant monitoring. With a CNAPP, you can breathe easy knowing your data is shielded from unauthorized access and potential breaches. - Compliance challenges
CNAPP solutions make meeting regulatory compliance a breeze by providing tools for continuous monitoring, auditing, and reporting on cloud security controls. - Visibility gaps
To overcome the blind spots in cloud environments, CNAPP solutions step in with robust monitoring and logging features. This enables organizations to get a clear view of network traffic, user activities, and potential security threats. - Developer responsibility in cloud security
CNAPP solutions play a vital role in supporting engineers throughout the development lifecycle with early error detection and comprehensive runtime visibility. By integrating a CNAPP into your workflow, your developers gain the tools they need to proactively address security concerns, ensuring the resilience and reliability of their cloud-native environments.
Benefits
Beyond addressing legacy cloud security challenges, a CNAPP solution offers a range of crucial advantages. Let’s explore how CNAPPs transform cloud security, empowering teams to reach their objectives:
- Increased efficiency
CNAPPs simplify security operations by replacing multiple point products and providing a unified view of risk. This streamlines the process, freeing teams from the burden of mastering various tools and managing alerts from different sources. By consolidating security functions into a single platform, CNAPPs enable teams to streamline their workflows, boosting productivity and efficiency. - Comprehensive visibility
CNAPPs provide a unified view for your teams to swiftly pinpoint issues, events, and potential attack paths. Through user-friendly visual layouts, alerts, suggestions, and guidance for remedial actions, you can make informed decisions and proactively safeguard against threats. - Enhanced cloud security
CNAPPs offer an end-to-end solution, ensuring consistent threat detection and visibility across any workload, cloud, or service. By leveraging techniques such as machine learning and threat feeds, CNAPPs enable organizations to effectively identify and respond to threats, reducing the attack surface in cloud-native environments. - Multi-cloud security coverage
CNAPPs give you a clear view of all your resources across different clouds, like where you’re storing things (your infrastructure as a service) and what platforms you’re using (your platforms as a service). They check out everything from virtual machines to containers and even your dev setups. This helps catch and fix problems early, making sure your security covers everything. - Shift left
Through seamless integration with current development and DevOps tools, CNAPPs improve the software development lifecycle. By embracing both “shift left” and “shield right” security principles, CNAPPs offer a robust and comprehensive security strategy across the application lifecycle. This approach enables early detection and swift response to security incidents.
How a CNAPP works
CNAPPs make cloud security simple by bringing together visibility into runtime risks, cloud risks, and development artifacts all in one place. To achieve this, CNAPPs typically use two different methods: agent-based and agentless.
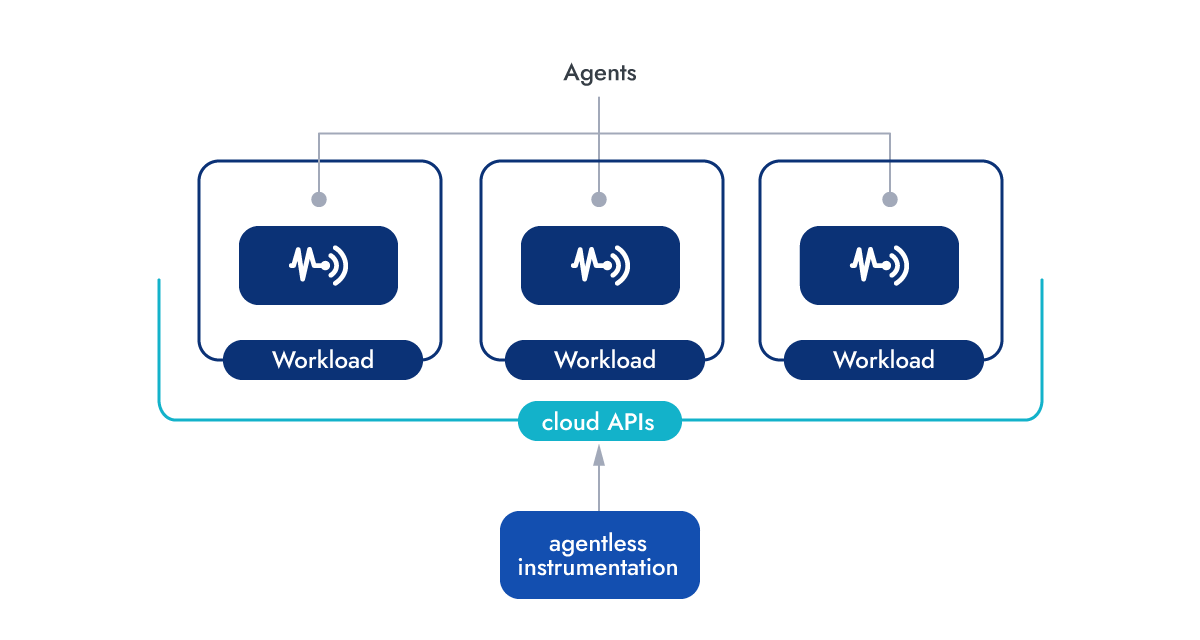
- Agent-based approaches stay close to the workloads. They require an agent (often called sensor or probe) executing alongside the workloads on the instrumented machine. Being on the same host grants real-time visibility into runtime assets and allows access to system-level context information, something that is not available otherwise.
- Agentless approaches use cloud provider APIs to gather relevant context without needing an agent running along the workloads. These solutions often take snapshots to defer the security scans on a point-in-time copy, leaving the original workload unaltered. While this approach lacks the deep runtime insights that an agent provides, it offers a frictionless solution for tackling issues that do not need to rely on real-time data, like building an asset inventory, or identifying known vulnerabilities and anomalous behavior in audit logs.
For a strong CNAPP solution, it’s important to use both approaches to get the best results. Agent-based methods help you see what’s happening in real time and give you lots of detail about how your system works. On the other hand, agentless approaches are great for finding known vulnerabilities and spotting anomalous activity in your logs.
Choosing a CNAPP
Now that we’ve explored the benefits that CNAPPs offer and their inner workings, it’s time to delve into the process of selecting the right one for your organization. What factors should you consider when planning to adopt a solution? Here’s a highlight of the key components and capabilities that a CNAPP should offer to empower your organization’s security posture.
Key components
An effective CNAPP consolidates multiple solutions:
- Cloud security posture management (CSPM)
CSPM allows you to monitor, identify, alert on, and remediate compliance risks and misconfigurations within your cloud environments. It’s your watchdog for ensuring your cloud infrastructure remains compliant and secure. - Cloud detection and response (CDR)
CDR plays a vital role in a CNAPP by providing advanced threat detection, incident response, and continuous monitoring capabilities specifically designed for cloud environments. CDR within a CNAPP leverages cloud-native security controls to gain real-time visibility into cloud assets, configurations, and activities. - Cloud infrastructure entitlement management (CIEM)
CIEM is your shield against data breaches in public clouds. By continuously monitoring permissions and activities, it helps mitigate the risk of unauthorized access to sensitive data. - Data protection
Safeguarding your critical data is paramount. With data protection capabilities, a CNAPP can monitor, classify, and inspect data to prevent its exfiltration due to phishing attempts, insider threats, or other cyber threats. - Identity and access management (IAM)
IAM ensures that the right people have the right access to your organization’s resources. By controlling access to internal systems and data, IAM helps prevent unauthorized access and data breaches. - Cloud workload protection platforms (CWPP)
CWPPs offer visibility and control over various workloads, including physical machines, virtual machines, containers, and serverless environments. It’s your comprehensive solution for securing workloads across hybrid, multi-cloud, and data center environments.
Key capabilities
When it comes to figuring out the key capabilities of CNAPPs, Gartner’s Market Guide for CNAPP Platforms is a handy resource. Here’s a breakdown of Gartner’s suggested capabilities:
Core capabilities
- Runtime visibility into virtual machine (VM) and container workloads
- Cloud security posture management, including all leading hyperscale providers and their managed Kubernetes offerings (Kubernetes security posture management or KSPM)
- Infrastructure as code (IaC) scanning, including for major IaC scripting languages and YAML/Helm for Kubernetes
- Cloud infrastructure entitlement management
- Network connectivity mapping
- Scanning of containers and container registries for risk
- Software composition analysis, including software bill of materials (SBOM) creation
Recommended capabilities
- Real-time workload visibility from the inside for critical VMs and containers, including workload detection/response
- API discovery and scanning for correct configuration in development
- API discovery in development and monitoring at runtime
- Scanning of unstructured IaaS data repositories for risk
- Network monitoring capabilities
- Workload detection and response
- Expanded cloud detection and response (CDR) capabilities beyond workload monitoring (for example, looking at event logs, network logs, and DNS lookups)
- Drift detection from expected state
- Support for other common clouds like Oracle, IBM, Alibaba Cloud, or Tencent
- Scanning of other application artifacts for risk
- VMs
- Serverless functions
Questions to ask your vendor
As you start looking for a CNAPP solution, it’s important to get a good understanding of what each vendor offers. Here are some questions you can ask to help you figure out which CNAPP solution is right for your organization:
- Does your CNAPP include consolidated components such as CSPM, CIEM, CWPP, IAM, and data protection?
- Can you provide a demo, and do you offer a trial of your CNAPP solution?
- Can your CNAPP apply runtime insights to provide a prioritized and contextual view of risk?
- How does your CNAPP provide unified security and risk dashboards across cloud, containers, and Kubernetes environments?
- Does your CNAPP support both an agentless and agent-based approach?
- Is your CNAPP an enterprise-grade platform that integrates and aligns with API use, scripting, and automation functionality?
- Can you provide customer references and testimonials?
- What is the vendor onboarding process like, and what level of ongoing support do you provide?
Real-world example
One fraud detection software company offers a real-world example of how they streamlined their cloud security solutions and updated their approach by implementing a CNAPP.
After their team rapidly grew from five to 250 engineers, this company was ready to shift security responsibilities to the engineering team and build it into their development processes.
With six solutions already in place – AWS GuardDuty, AWS Security Hub, AWS Config, Tenable, SentinelOne, and Lacework – the company seized the opportunity to consolidate its cloud security tools. The objective was to manage vulnerability, security posture, and compliance, and to protect against intrusions in all cloud environments across workloads and cloud services with a single platform.
Their new CNAPP provided a comprehensive approach to cloud security, and improved overall security posture by focusing on the vulnerabilities, misconfigurations, and compliance gaps that create the greatest risk. With this CNAPP, the company can detect threats in real time, prioritize the vulnerabilities that matter, and fix them fast with context. Consolidating six tools into one also netted the company an overall cost savings of more than 20%.
The future of CNAPP
The adoption of microservices built on containers and Kubernetes are driving an explosion in data volume. And so CNAPPs are tasked with ingesting and analyzing a flood of data sources. This surge in data leads to a growing number of high- and low-fidelity signals. CNAPPs that apply runtime insights help you focus on the most crucial risks in your cloud infrastructure.That’s why, as the volume of signals continues to grow, runtime insights will become a foundational feature for any CNAPP solution.
Runtime insights give you visibility into what’s running right now, which can help you shrink down the list of things that need urgent attention. Simply put, knowledge of what’s currently running gives you the necessary context to take action on the most critical risks first. Ultimately, this context can be fed back into the development lifecycle to improve your “shift left” use cases with actionable prioritization.
FAQs
As we wrap up our CNAPP deep dive and you get ready to head off into your CNAPP explorations, we’d like to leave you with summary answers to some of the most frequently asked questions on the topic.
CNAPP stands for Cloud-Native Application Protection Platform. It is a comprehensive solution designed to secure your cloud applications and infrastructure by providing advanced threat detection, access controls, and security measures specifically designed for cloud environments.
CNAPP is designed for businesses and organizations looking to secure their cloud-native applications in today’s digital landscape, regardless of industry or size.
A CNAPP typically includes features such as threat detection, prevention, and response capabilities, along with real-time monitoring and alerting functionalities. And don’t forget the essential runtime insights capability to help you prioritize security risk.
Yes, a CNAPP can seamlessly integrate with your current security tools and systems, making it easy to leverage your existing investments in infrastructure and applications.
The short answer: CSPM (short for cloud security posture management) is a capability within CNAPP solutions. CSPM uses automation to help businesses establish a secure posture against threats in cloud environments, as well as ensuring compliance with industry regulation. While it can exist as a standalone solution, CSPM is also one of the solutions included within CNAPP. By enhancing cloud security with speed, efficiency, and adaptability to different types of cloud workloads, CSPM serves as a fundamental component of any comprehensive cloud security strategy.
CWPPs protect cloud workloads, including containers, servers, and serverless workloads. They provide visibility across hybrid and multicloud environments, scan for risk in the development pipeline, and safeguard workloads from attack at runtime.
CWPPs can be adopted as a stand-alone solution, and it’s also a capability included within CNAPP. With so many tools working in silos, it gets difficult to prioritize risk within cloud-native applications and associated infrastructure. CNAPP’s offerings are bringing together multiple disparate security and protection capabilities into a single platform. CNAPP encompasses CWPP as part of its broader security strategy, ensuring that both applications and workloads in the cloud are protected.
A CNAPP helps with compliance by providing robust security controls specifically designed for cloud environments. CNAPPs offer comprehensive capabilities such as data encryption, access controls, identity management, and logging mechanisms that are essential for meeting regulatory standards. For instance, regulations like the EU’s Digital Operational Resilience Act (DORA) and Network and Information Systems Directive (NIS2) require organizations to secure their cloud resources and maintain audit trails of activities. Also, many CNAPPs include out-of-the-box compliance policies tailored to these regulations, which streamlines and simplifies your compliance efforts.
The cost of implementing a CNAPP solution varies depending on several factors, such as the size of your organization and the specific features and capabilities of the CNAPP. Generally, CNAPP solutions are subscription-based and priced according to the number of protected applications, the level of support required, and the amount of traffic processed. Costs can range from several thousand to tens of thousands of dollars annually with additional expenses for professional services, training, and any necessary infrastructure upgrades.
Many CNAPP tools are designed with ease of deployment in mind, offering predefined security policies and configurations that streamline the setup process. CNAPPs consolidate various security solutions into a single platform, simplifying deployment and management processes by providing a unified interface and workflow for security operations. This consolidation not only streamlines the initial setup, but also simplifies your ongoing management, as it reduces the complexity of maintaining and updating your security measures across separate tools.


