Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Minimizing the time to detect, investigate and respond to threats is crucial in stopping cloud attacks. In fact, this might be the biggest understatement in cloud security today. Modern threat actors are escalating their tactics, making attacks faster, more aggressive, and increasingly difficult to stop. Cloud attacks occur at lightning speeds, leveraging automation to access sensitive data and resources before security teams can react. This leaves defenders feeling like they are playing an impossible game of 3D chess against attackers. With attackers needing less than 10 minutes to go from identifying an exploit to fully executing an attack, the value of rapid detection and response can't be overstated.
Furthermore, advancements in AI have equipped malicious actors with new and unknown techniques that are difficult to anticipate. Threat actors are using AI to write malicious code, create malware, conduct highly targeted social engineering or phishing campaigns, and even generate realistic videos and voice recordings. These AI-driven techniques increase the speed, efficacy, and scale of attacks, thereby reducing barriers to entry, chipping away at the basic foundations of identity in security, and enabling threat actors to bypass initial defenses.
Operating in this changed landscape requires a new mindset of tracking active risks from security teams. Prevention alone is no longer enough. As threat actors evolve and develop new attack vectors, defenders must prioritize detecting and stopping unknown attacks in real time. Identity and access management, vulnerability management, and other preventive controls are important for building a robust defense. However, no organization can effectively defend against zero-day exploits without a purpose-built cloud detection and response (CDR) solution.
What security teams are missing
Many modern attackers exploit the vastness and complexity of cloud infrastructure to evade defenses. They behave like the queen on a chessboard, effortlessly traversing public clouds, workloads, and on-premises infrastructure, making it difficult for security teams to track their actions in real time. To defend against attacks, security practitioners must quickly read into the attacker's moves, and create a cohesive narrative from tangled details like where the attack started, which identities and permissions were exploited, and the attack's targets and goals.
Legacy EDR and XDR tools struggle with adequate cloud visibility, leaving teams with incomplete and siloed data that lacks cloud context. Without the ability to correlate findings across identity behavior, workload activity, and cloud resources, security teams can't see the full picture of an attack. Detection and response needs to occur in minutes — which means this process needs to be automated and conducted in real time.
Recent attack patterns highlight three key areas where security teams need help in addressing unknown attacks.
Lack of insights around identities and their behavior
Credentials are the primary attack vector used to launch attacks in the cloud, yet insights into identities and their early-stage behavior remain limited. Identity has become one of the most overlooked risks in cloud security, with many major breaches in recent years involving overly permissive credentials and some form of lateral movement or privilege escalation. According to the Verizon 2024 Data Breach Investigations Report, exploited credentials are the most common initial access vector, used in almost 40% of breaches.
Attackers can move across machines in the cloud, decoupling identity behavior from workload activity and making it difficult to reconstruct the full history of an attack even after initial detection. The explosion of non-human/machine identities adds even more complexity, as cloud infrastructure has expanded to encompass a vast array of identities and roles. With thousands of users, permissions, and logs to analyze, EDR/XDR tools fall short in providing visibility into user activity around cloud identities, especially across multi-cloud and hybrid cloud environments.
Gaps in coverage due to the complex nature of the cloud
Like a game of chess, the battleground for today's cloud defenders is multidimensional in its complexity, diversity, and vastness. It's challenging to cover the diversity of workloads across public, private, and hybrid cloud environments. Exploits manifest on workloads and services across the cloud expanse, but the forensics patterns are typically visible across the associated compromised identities much earlier. Too many gaps exist, as current tools lack deep visibility into #3 diverse cloud-native constructs such as containers, Kubernetes clusters, microservices, serverless, and more.
Commonly used EDR/XDR tools fail to provide full visibility and recognize malicious forensic patterns when it comes to cloud-native infrastructure. XDR agents lack the necessary visibility and context for cloud workloads.
On the other hand, cloud security posture management (CSPM) vendors take a purely agentless approach that lacks true real-time coverage. To rectify this, several CSPM-focused vendors have also released immature security agents. But these agents are riddled with issues such as high resource consumption, slow response times, and cumbersome installation processes. These coverage and visibility gaps leave cloud defenders blind and often result in delayed threat detection, higher operational costs, and an increased risk of breaches.
Silos prevent teams from collaborating to harden defenses
Detection activities for the cloud are viewed by security teams as separate from cloud posture use cases such as cloud identity and entitlements management. This prevents sharing of identity insights across the spectrum, even though most cloud attacks in recent years have had a link between compromised identities, workloads, and cloud resources.
There is an urgent need to connect the dots across detection and prevention activities. Ideally, learnings from the detection and response teams need to be passed on and integrated into posture strategy to ensure robust defenses for the cloud.
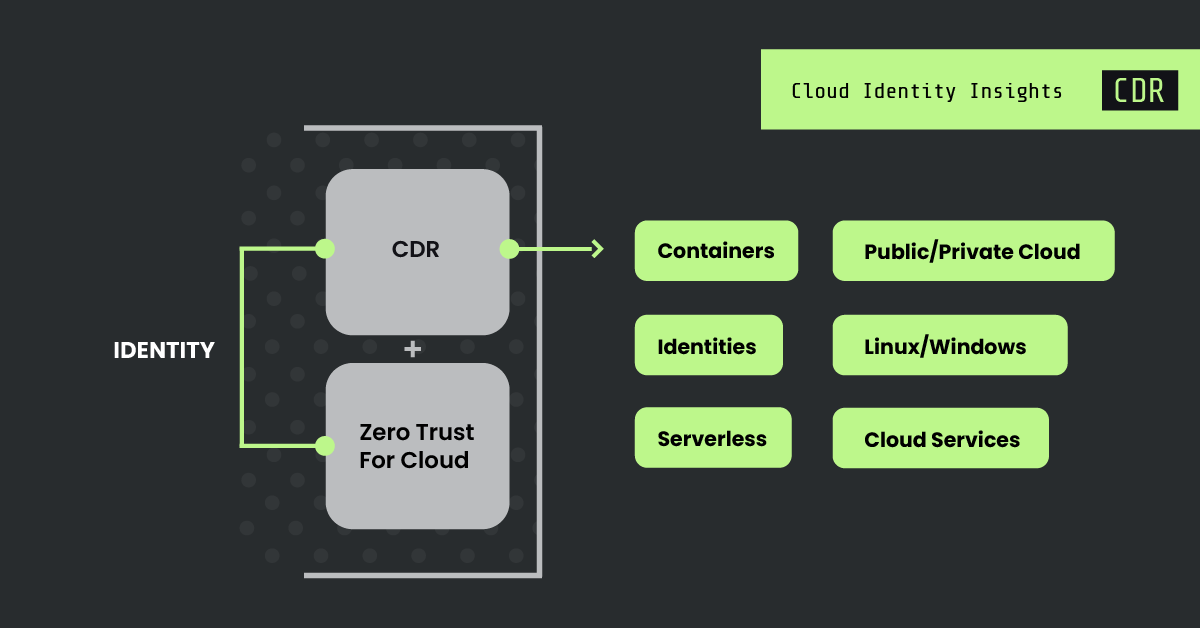
True CDR: Identity behavior + coverage
The limitations of EDR and XDR tools, which cannot provide insights into cloud identities or comprehensive coverage of cloud workloads, make them fundamentally unsuited for cloud security. To effectively thwart attacks in motion, a purpose-built CDR solution is necessary — one that offers full visibility into cloud infrastructure and encompasses identities, workloads, and cloud resources.
Detection and prevention cannot be viewed as silos. To anticipate threat actors' intentions and stay ahead of attacks, defenders need a tool that correlates identity behavior with workload activity to get the full picture in real time. Identity context is central to a zero trust for cloud strategy, but must also be integrated into detection and response workflows.
By incorporating identity context, security teams can respond to threats as soon as they detect identity-based actions, such as privileged user creation, which often represent the initial steps of the attack chain. This integration of identity context, bolstered with extensive workload coverage, empowers security teams to stop attacks at the first sign of compromise, effectively shutting down threat actors before they get off the ground.To stop cloud threats early in the attack chain, you need security solutions built for the cloud. Once you can meet the 555 Benchmark for cloud detection and response, you can confidently safeguard your entire cloud estate and unlock its true value.


