Cloud Detection and Response
Detect, investigate, and respond to threats fast
Cloud attacks happen fast. When you have minutes to detect and respond to threats, you need visibility, context, and insights from cloud-native services to stay ahead of attackers. Secure your cloud with end-to-end detection, cloud-native context with multi-domain correlation, and definitive response actions.
How Sysdig helps
Secure your cloud in real time with speed and precision
In the cloud, you only have 5 seconds to detect, 5 minutes to investigate, and 5 minutes to initiate a response to a threat. Traditional endpoint detection and response (EDR) solutions lack the critical capabilities to safeguard against cloud attacks.
-
Detect known and unknown threats across your cloud estate
Do you know when an attacker is in your cloud estate? Within 5 seconds, you must be able to detect malicious process, file, network and user activity in real time. Built on Falco, the standard for threat detection, Sysdig comes with out-of-box detection for the latest threats, across serverless, containers, Kubernetes, cloud logs and trails.
-
Investigate threats in 5 minutes
Siloed and limited data forces teams to manually collect and correlate findings across tools, drastically slowing down investigation times. Sysdig delivers comprehensive forensic data correlated across activity audits, syscall captures, process trees, and beyond. This speeds up cloud-native investigations by automating correlation across environments between resources, events, identities, posture, and vulnerability data making it possible for teams to perform 5-minute investigations and respond at cloud speed.
-
Respond to threats fast
Cloud resources are an increasingly attractive target for threat actors to leverage cryptominers and botnets. Sysdig stops common and emerging threats in cloud and container environments, such as backdoors and C&C in compromised images, and cryptojacking. Respond with powerful automated and manual response actions.

Free resource
Can you detect and respond to threats in under 10 minutes?
According to our latest threat research, it only takes 10 minutes for bad actors to execute an attack in the cloud. The 555 benchmark establishes 5 seconds to detect, 5 minutes to correlate, and 5 minutes to initiate a response to a threat. Security teams must strive to meet this benchmark to stay ahead of modern cloud threat actors.
FAQ
Cloud detection and response (CDR) enables security teams to protect their cloud applications and infrastructure at runtime and post runtime. CDR capabilities should enable continuous monitoring with real time detections of potential threats, deep context and correlation for investigation, and response countermeasures to eradicate threats.
EDR solutions are great at protecting endpoint assets, like laptops, desktops, and mobile devices, but they’re not built for the cloud. EDR simply can’t deliver the context, correlation, and continuity needed to stay ahead of attackers in the cloud. Cloud-native CDR solutions are purpose built for the complexities of distributed, immutable, and ephemeral multi-cloud environments.
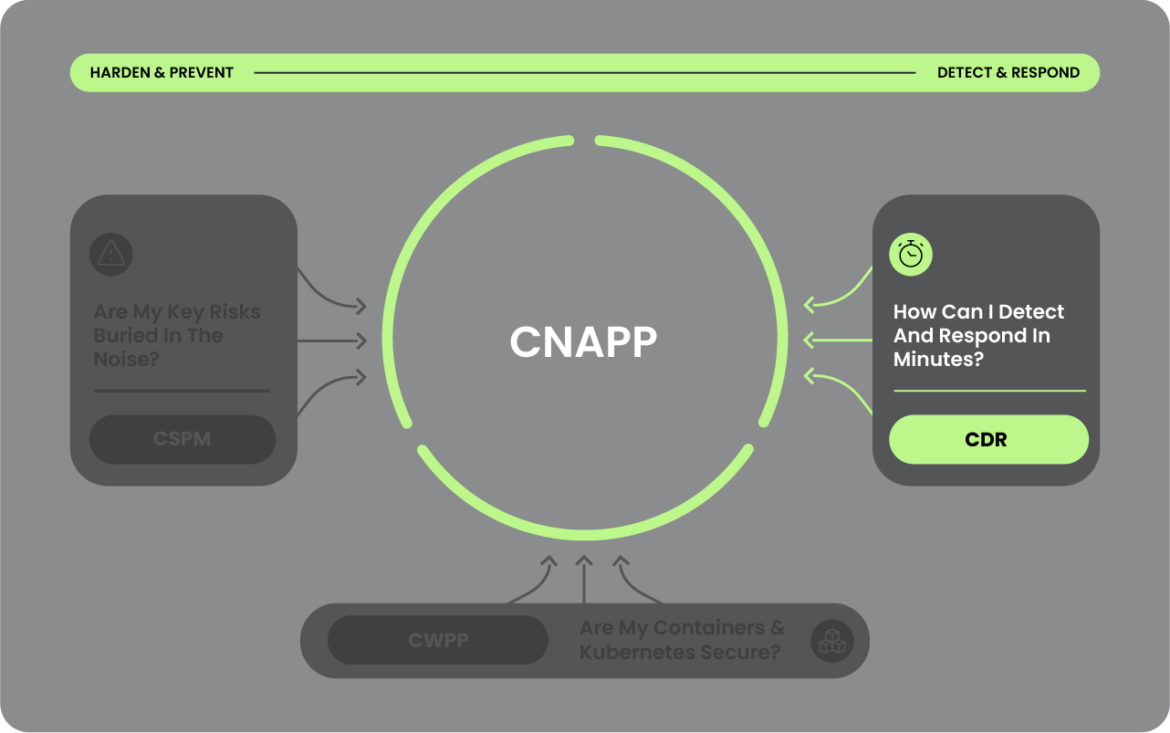
CDR pairs well with CSPM. Whereas CSPM helps to proactively reduce cloud risk in pre-runtime (what can happen), CDR ensures you have the ability to detect, investigate, and respond to cloud attacker activity in runtime (what is happening right now) and post runtime (what has happened). CSPM is not a replacement for CDR.
Numbers don't lie
How cloud detection & response can helpReduce the risk of breaches, speed time to detect & respond, and accelerate innovation. Unlock the full potential with a unified cloud security platform, like Sysdig CNAPP.
Learn More
Start your cloud security journey
Accelerate Cloud Threat Detection & Response From Days to Minutes
Detect attack patterns across containers, Kubernetes and cloud. Protect workloads against runtime threats.
See Sysdig in Action
From prevention to defense, Sysdig helps you prioritize critical risks and stop attacks in real time.