
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.


Kubernetes security tools … there are so freaking many of them; with different purposes, scopes and licenses.
33 #Kubernetes #security tools, explained and categorized to help you pick the right ones for your cluster.
Click to tweet
That's why we decided to create this Kubernetes security tools list, including open source projects and commercial platforms from different vendors, to help you choose the ones that look more interesting to you and guide you in the right direction depending on your Kubernetes security needs.
Kubernetes security tools – Categories
To further help you navigate this directory, we have also divided the different tools by their main functionality and scope:
- Kubernetes image scanning and static analysis
- Anchore
- Clair
- Dagda
- KubeXRay
- Snyk
- Trivy
- Kubernetes runtime security
- Falco
- Linux runtime security frameworks
- Sysdig open source
- Kubernetes network security
- Aporeto
- Calico
- Cilium
- Istio
- Tigera
- Trireme
- Image distribution and secrets management
- Grafeas
- In-toto
- Portieris
- Vault
- K8s security audit
- Kube-bench
- Kube-hunter
- Kubeaudit
- Kubesec
- Open Policy Agent
- End-to-end K8s security commercial products
- Aqua Security
- Capsule8
- Cavirin
- Google SCC
- Layered Insight (Qualys)
- Neuvector
- StackRox
- Sysdig Secure
- Tenable Container Security
- Twistlock (Palo Alto)
As our favourite container orchestration platform matures, more and more security tools appear, if you think we missed any, please reach out to us on Twitter @sysdig!Enough talk, here is the security tools directory:
Kubernetes image scanning
Anchore
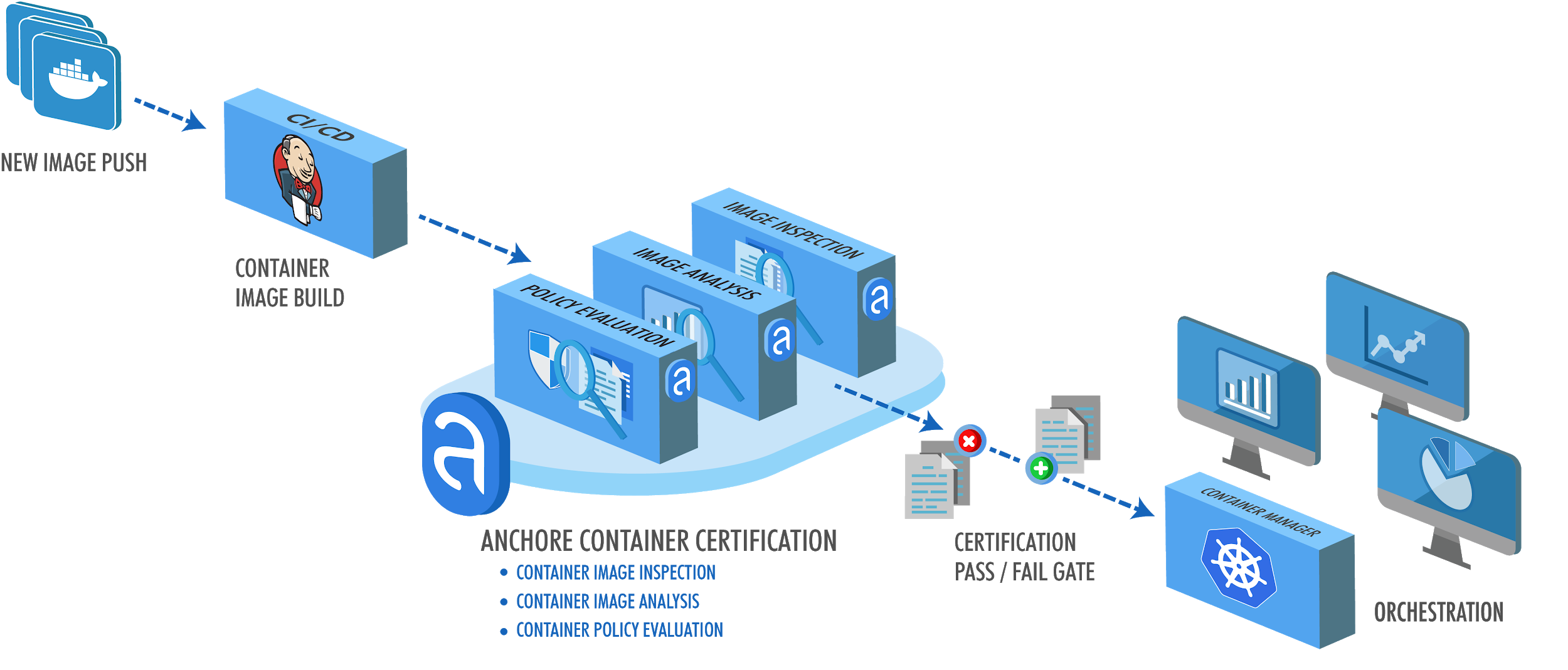
**Home page: **https://anchore.comLicense: Free (Apache) and commercial offeringAnchore engine analyzes container images and applies user-defined policies to implement custom security checks.Apart from the usual container image scanning against known vulnerabilities on the CVE database, there are many additional criteria that you can configure as part as your scanning policy with Anchore: Dockerfile checks, credentials leaking, language specific packages (npm, maven, etc), software licenses and more.
Clair
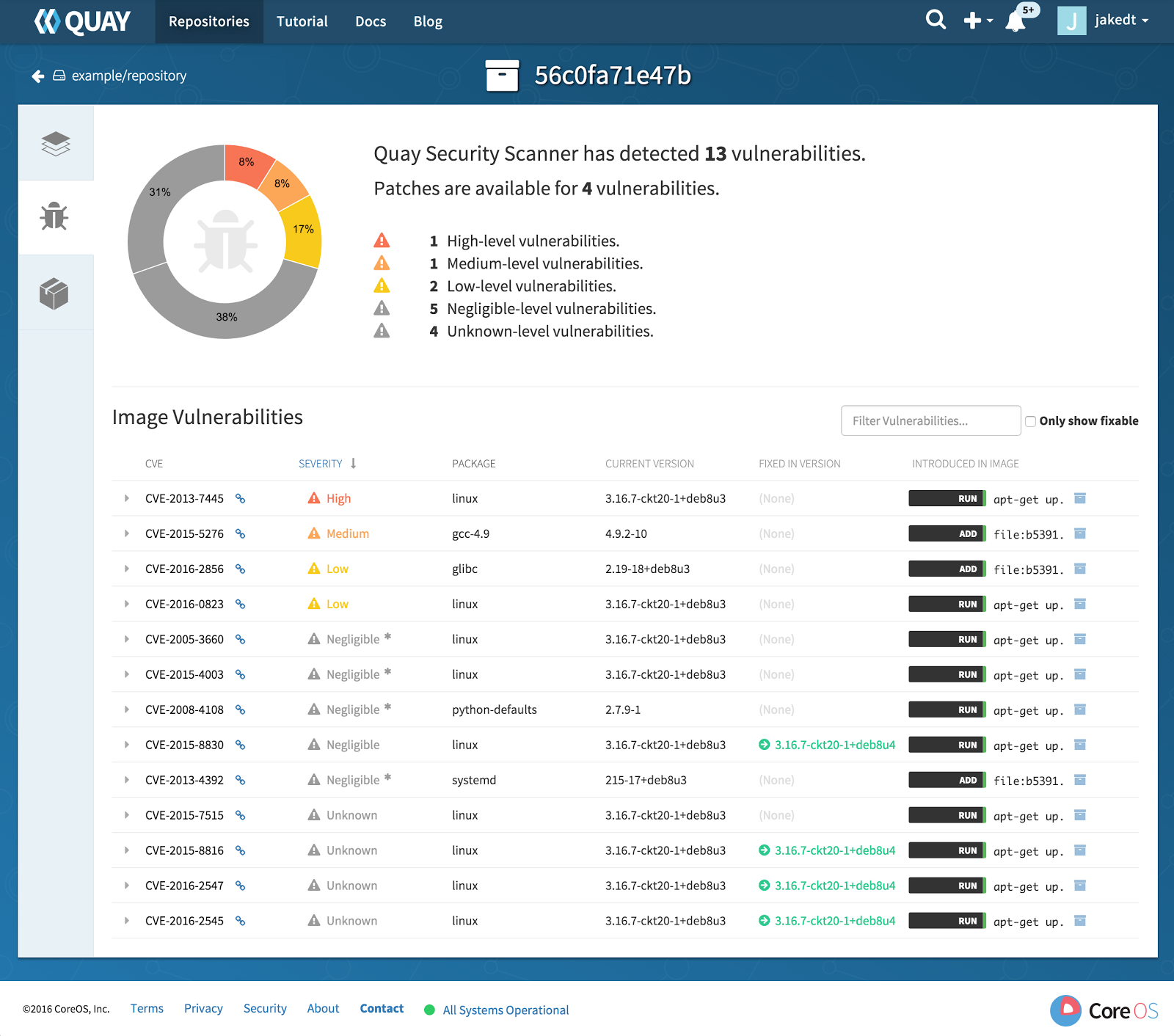
**Home page: **https://coreos.com/clair (now under RedHat umbrella)License: Free (Apache)Clair was one of the first open source image scanning projects, also widely known for being the security scanning engine powering the Quay image registry. Clair is able to pull CVE information from a large number of vulnerability sources, including distro-specific vulnerability lists authored by Debian, RedHat or the Ubuntu security teams.Unlike Anchore, Clair is mostly focused on the vulnerability scanning and CVE matching part, although it provides certain extensibility to its users through the implementation of pluggable drivers.
Dagda
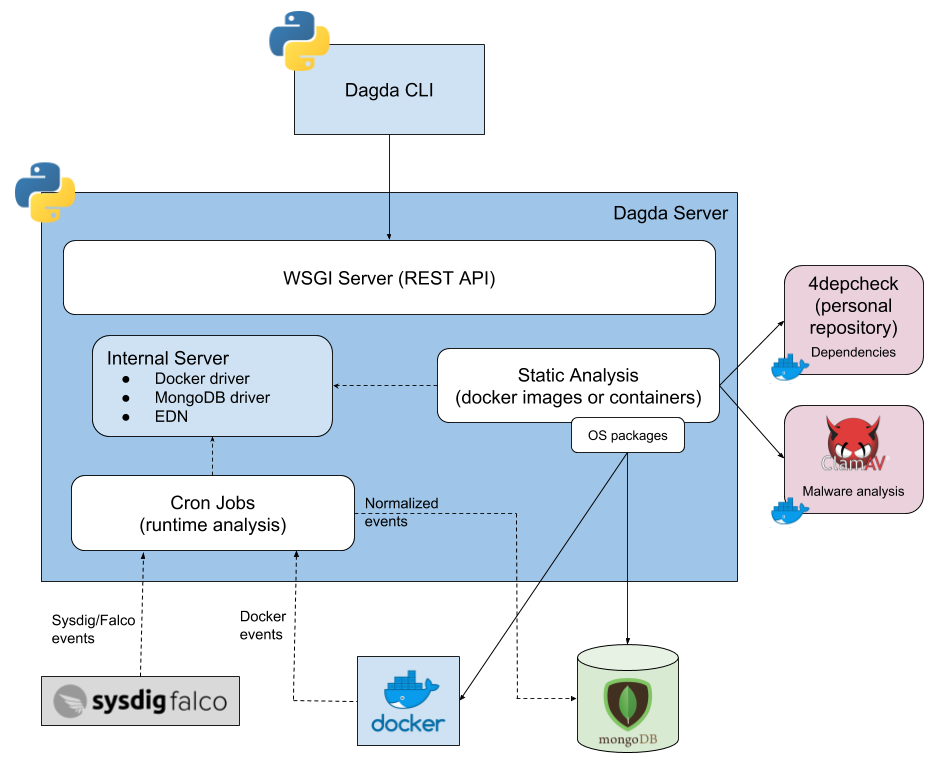
**Home Page: **https://github.com/eliasgranderubio/dagdaLicense: Free (Apache)Dagda performs static analysis of known vulnerabilities, trojans, viruses, malware & other malicious threats present in container images.There are two remarkable features that make Dagda different from similar security tools:
- It natively integrates with ClamAV, doubling down not only as a container image scanner but also antivirus software.
- Dagda also provides runtime protection features, gathering real time events from the Docker daemon and integrating with CNCF's Falco to collect runtime container security events.
KubeXray
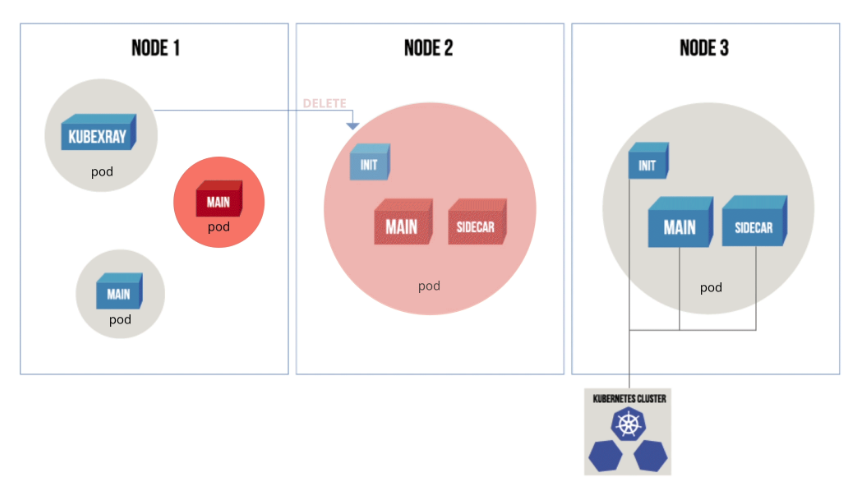
**Home Page: **https://github.com/jfrog/kubexrayLicense: Free (Apache), but needs to retrieve data from JFrog Xray (commercial product)KubeXray listens to Kubernetes API server events, and leverages the metadata from JFrog Xray (commercial product) to ensure that only the pods that comply with your current policy can run on Kubernetes.KubeXray not only audits new or upgraded container deployments (similar to a Kubernetes admission controller), but can also dynamically check the runtime containers against new security policies that you configure, deleting the resource that is pointing to a vulnerable image.
Snyk
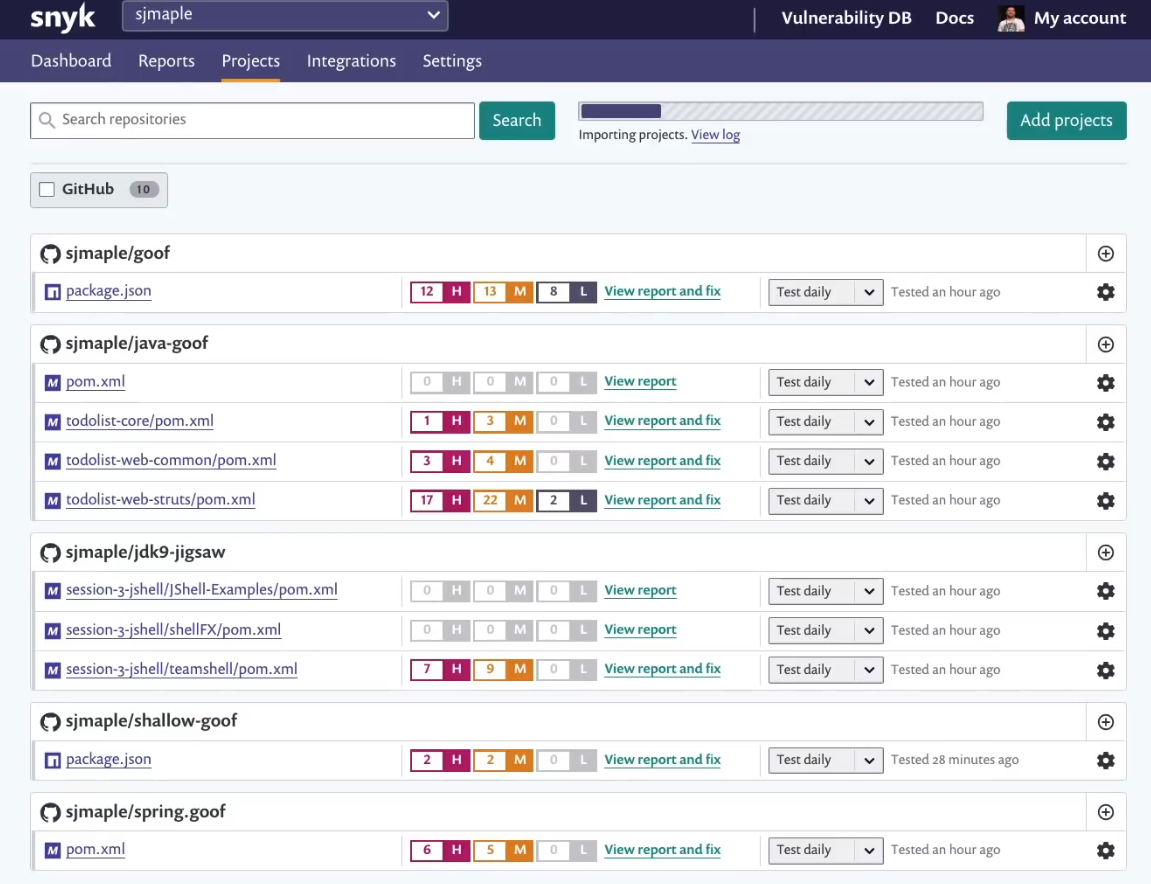
Home page: https://snyk.io/**License: **Free (Apache) and commercial offeringSnyk is a special vulnerability scanner in the sense that is particularly focused on the development workflow and advertises itself as a developer-first solution.Snyk will connect directly to your code repositories, parse the project manifesto and analyze the imported code, together with their direct and indirect library dependencies. Snyk has support for many popular programming languages and can also discover implicit licensing risks.
Trivy
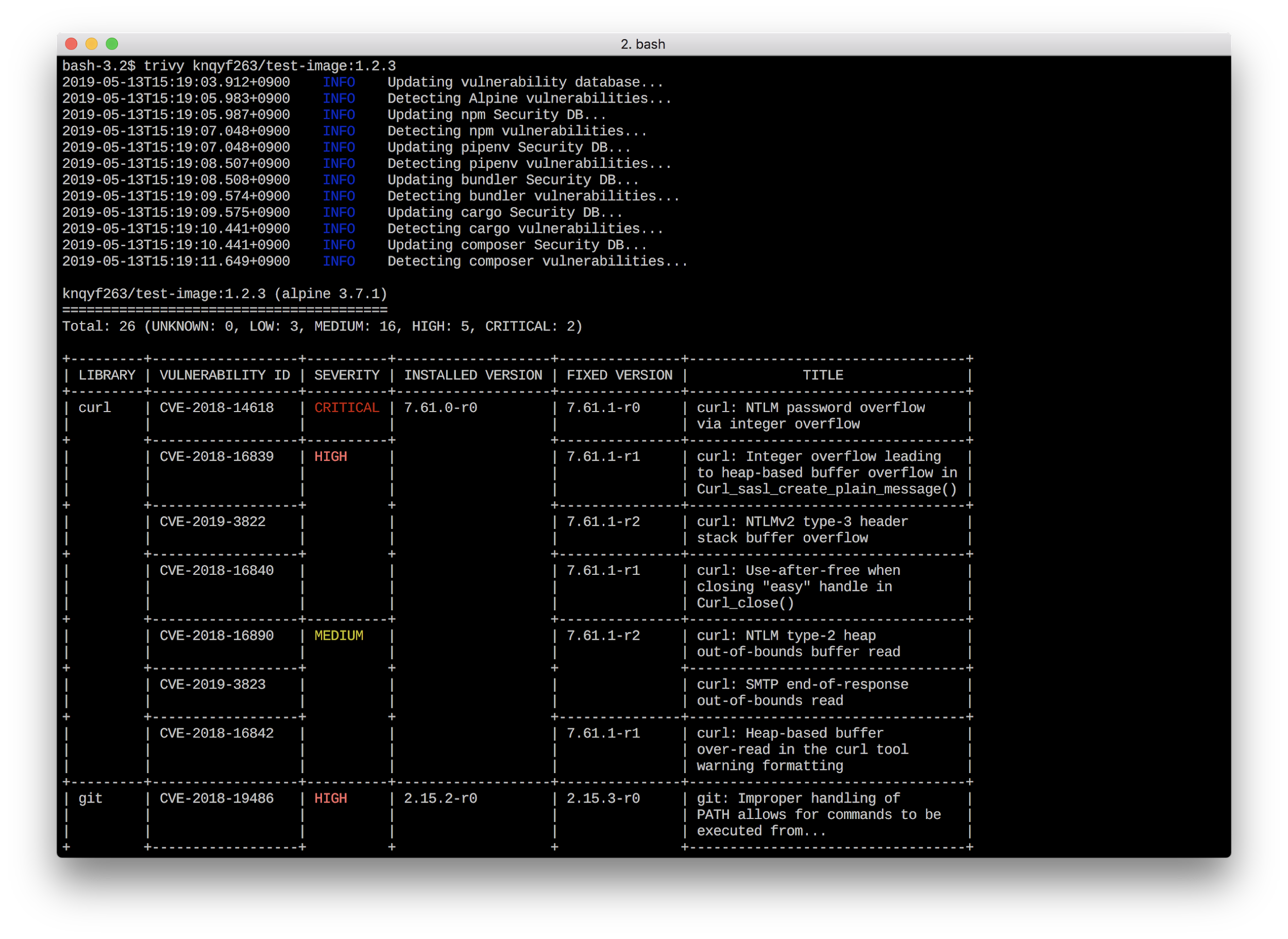
Home Page:https://github.com/knqyf263/trivyLicense: Free (AGPL)Trivy is a simple and comprehensive vulnerability scanner for containers, easy to integrate with your with CI/CD pipeline. One remarkable feature is the simplicity of its installation and operation, using just a single binary file that doesn't require you to install a database or additional libraries.The downside of Trivy's simplicity is that you will need to figure out how to parse and forward the JSON output so it can be leveraged by other security tools.
Kubernetes runtime security
Falco
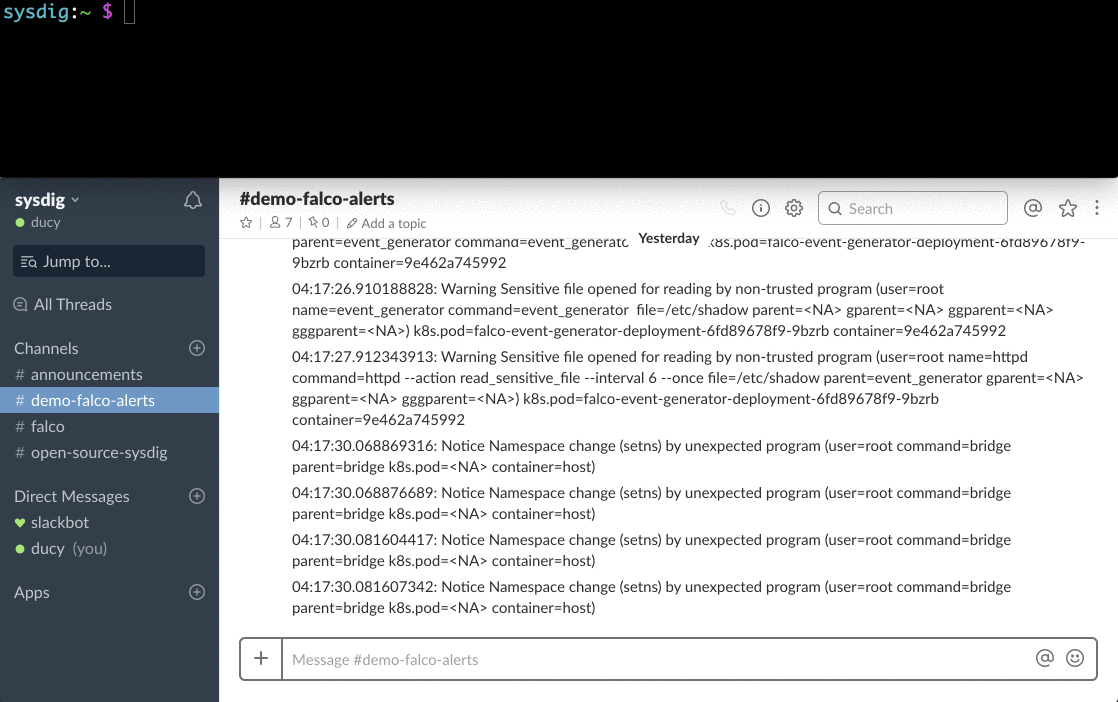
Home Page:https://falco.org/License: Free (Apache)Falco is a cloud-native runtime security toolset, and a proud member of the CNCF family.Leveraging Sysdig's Linux kernel instrumentation and system call profiling, Falco gains deep insight into system behavior. Its runtime rule engine can detect abnormal activity in applications, containers, the underlying host, and the Kubernetes orchestrator.Using Falco you will get full runtime visibility and threat detection deploying a single agent per Kubernetes node, no need to tamper with your containers injecting third-party code or stacking sidecar containers.
Linux runtime security frameworks
These native Linux frameworks are not "security tools" per se, but they are worth mentioning here, since they are part of the runtime security context that can be included in a Kubernetes Pod Security Policy (PSP).AppArmor attaches a security profile to the processes running in your container, defining file system privileges, network access rules, library linking, etc. It's a Mandatory Access Control (or MAC) system, meaning that it will prevent the forbidden action from taking place.Security-Enhanced Linux (SELinux) is a Linux kernel security module, similar in some aspects and often compared to AppArmor. SELinux is more powerful, fine-grained and flexible than AppArmor, at the cost of a steep learning curve and increased complexity.Seccomp and seccomp-bpf allows filtering of system calls, blocking execution of system calls that may be dangerous to the underlying host OS and are not needed for the regular operation of the userland binary. It has some minor similarities with Falco, although seccomp is not container aware.
Sysdig open source
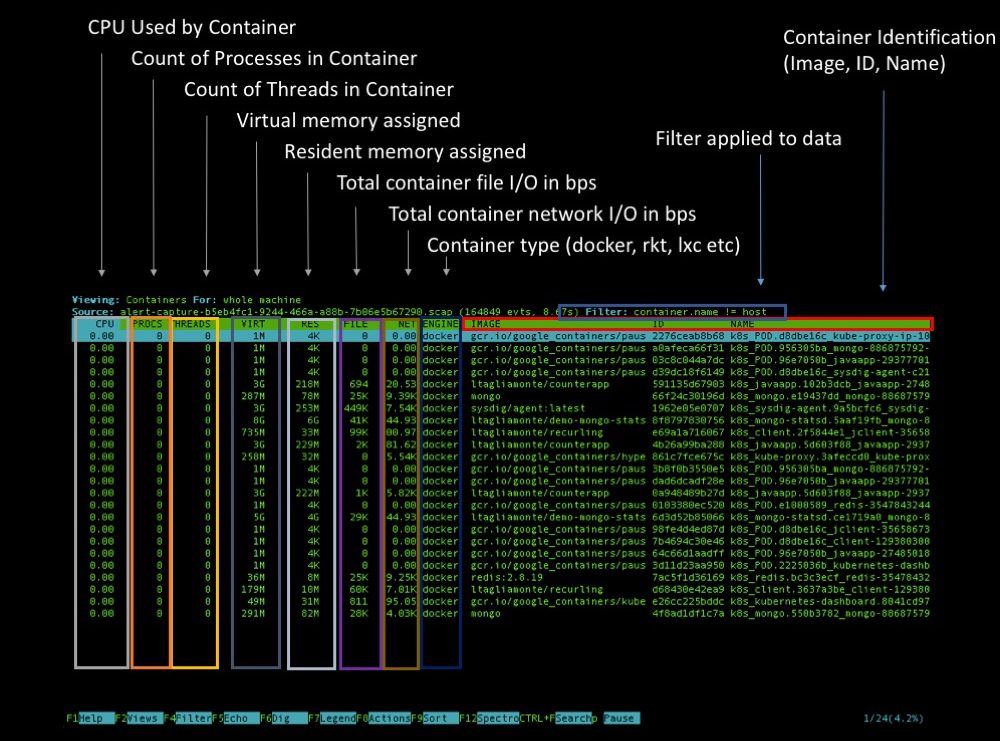
Home Page:https://www.sysdig.com/opensourceLicense: Free (Apache)Sysdig is a full-system exploration, troubleshooting and debugging tool for Linux systems (also works on Windows and Mac OSX, with limited functionality) that can be used to get fine-grained visibility, inspection and forensics for both the hosting OS and any containers running on it.Sysdig also natively supports container runtime and Kubernetes metadata, adding those extra dimensions and labels to any system activity you collect. There are several ways to explore your Kubernetes cluster with Sysdig: you can create a point-in-time capture using kubectl capture or spawn an interactive ncurses interface with the kubectl dig plugin.
Kubernetes network security
Aporeto
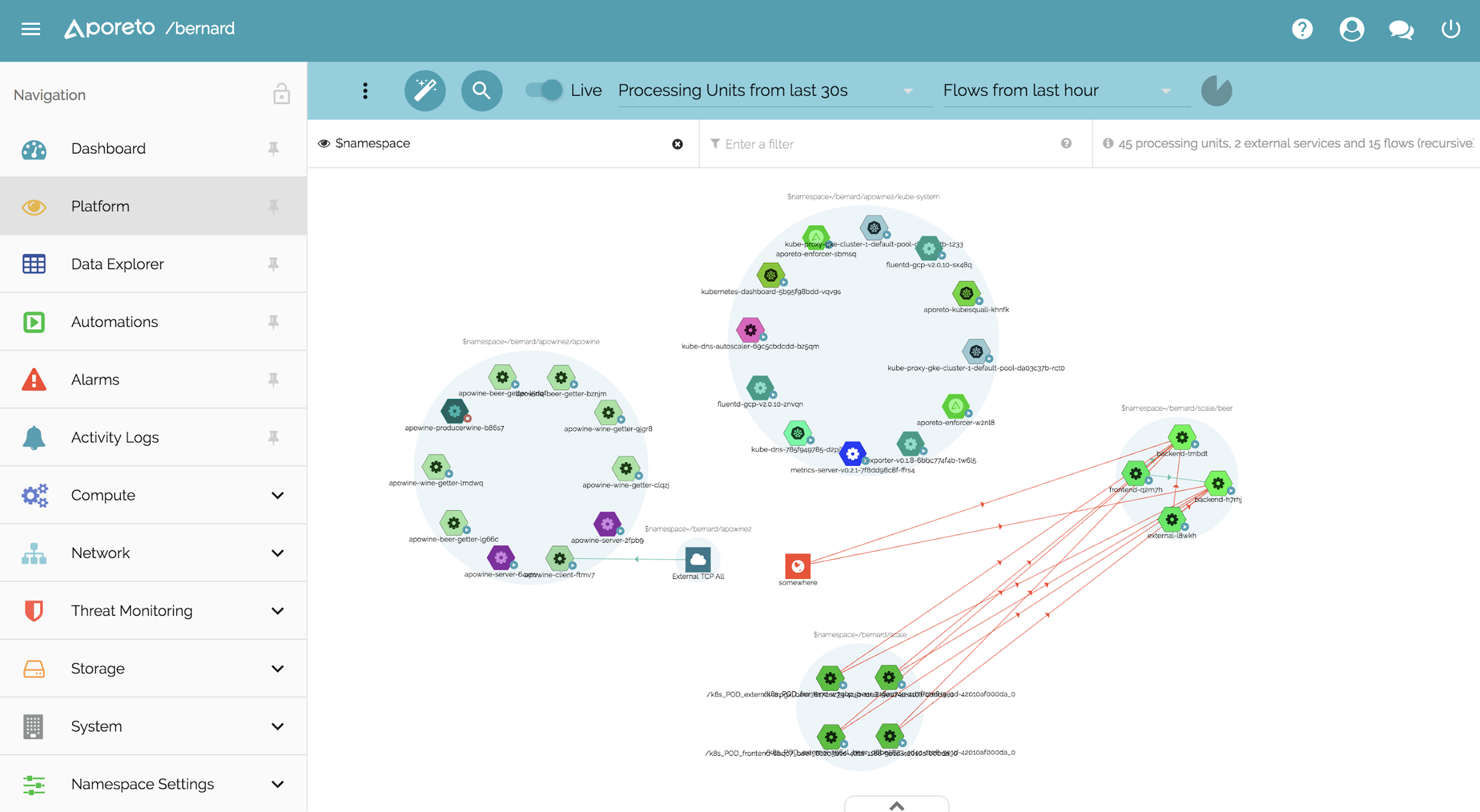
Home Page:https://www.aporeto.com/**License: **CommercialAporeto provides 'Security decoupled from network & Infrastructure'. This means that your Kubernetes services will not only get a local ID (i.e. a Kubernetes ServiceAccount) but also a universal identity/fingerprint that can be used to communicate in a secure and mutually verifiable way with any other service, for example, in an OpenShift cluster.Aporeto can generate a unique identity fingerprint not just for Kubernetes/containers but also for hosts, cloud functions and users. Depending on these identities and the set of network security rules configured by the operator, the communication will be allowed or blocked.
Calico
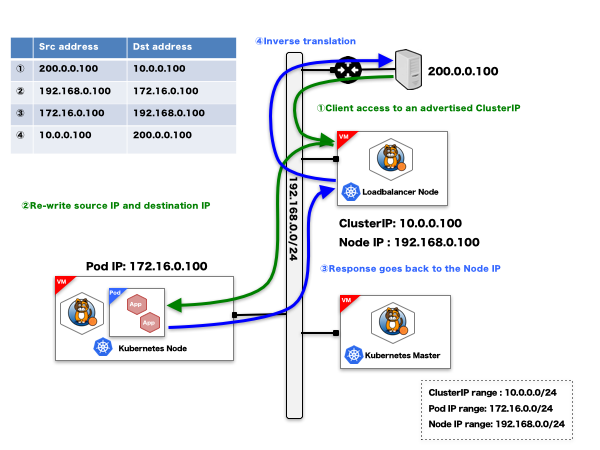
**Home Page: **https://www.projectcalico.org/License: Free (Apache)Calico is often deployed during the installation of your container orchestrator to implement the virtual network that interconnects the containers. On top of this basic network functionality, the Calico project implements the Kubernetes Network Policies specification and its own set of network security profiles implementing endpoint ACLs and annotation-based network security rules for both ingress and egress traffic.
Cilium
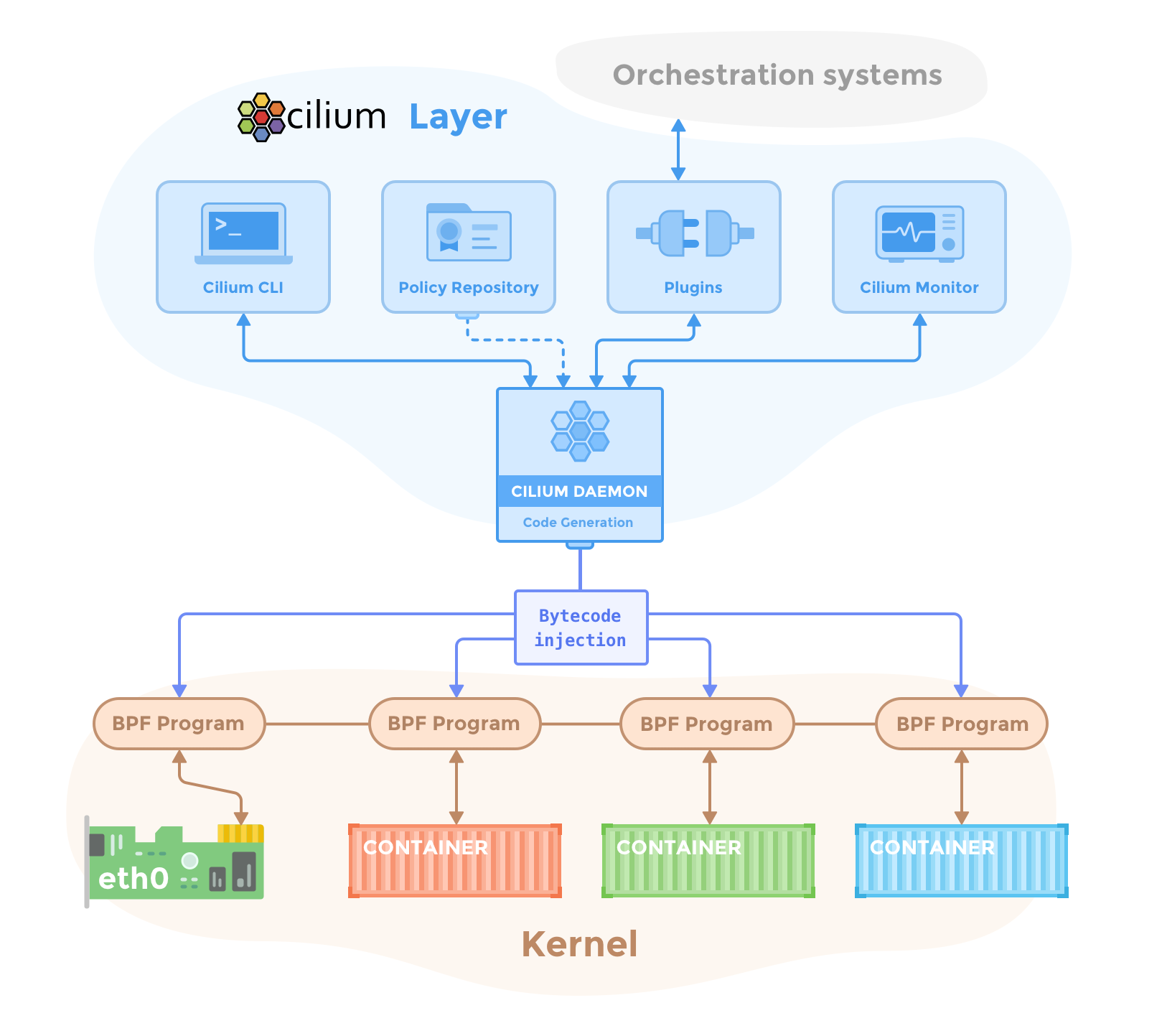
Home Page:https://www.cilium.io/**License: **Free (Apache)Cilium provides container firewall and network security functionality, natively adapted to the Kubernetes and microservices workloads. Cilium leverages a new Linux kernel technology called BPF (Berkeley Packet Filter) to perform core data path filtering, mangling, monitoring and redirection.Cilium can deploy network access policies based on the container identity using Docker or Kubernetes labels and metadata. Cilium can also understand and filter several layer-7 protocols like HTTP or gRPC, allowing you to define the set of REST calls that will be allowed between two given Kubernetes deployments, for instance.
Istio
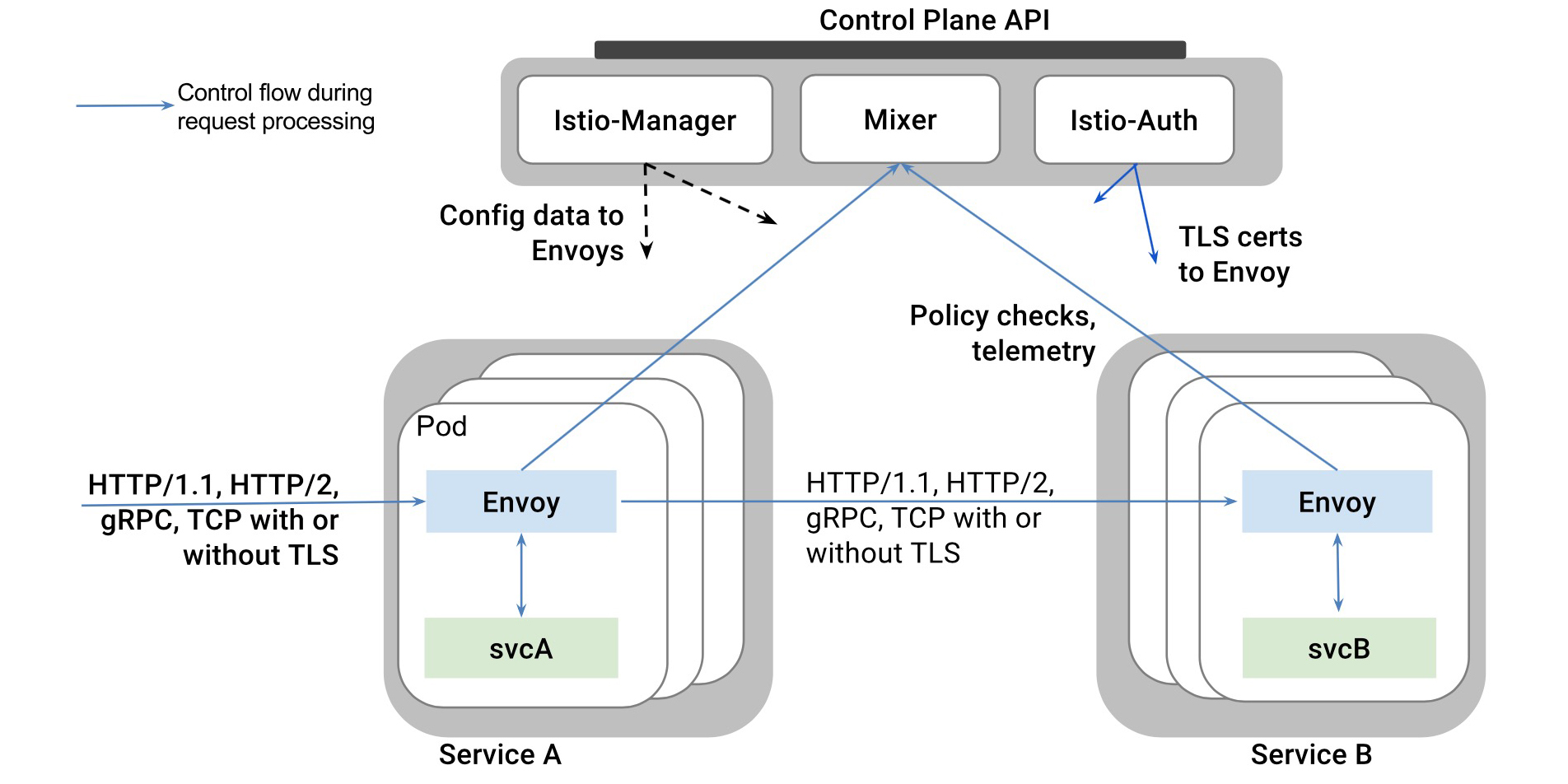
Home Page:https://istio.io/License: Free (Apache)Istio is widely known for implementing the "service mesh" paradigm by deploying a platform-agnostic control plane and rerouting all the managed service traffic through it's dynamically configured Envoy proxies. Istio will take advantage of this vantage view of all your microservices and containers to implement several network security strategies.Istio network security capabilities include: Transparent TLS encryption to automatically upgrade microservices communication to HTTPS and it's own RBAC identity and authorization framework to accept or deny communication between the different workloads in your cluster.
Tigera
Home Page:https://www.tigera.io/License: CommercialThe Tigera "Kubernetes firewall" technology emphasizes a zero-trust approach to your Kubernetes network security.In a similar fashion to other Kubernetes-native network solutions, Tigera leverages the Kubernetes metadata to ID the different services and entities in your cluster, providing runtime detection, continuous compliance checks and network visibility across multi-cloud or hybrid monolithic-containerized infrastructures.
Trireme

Home Page:https://www.aporeto.com/opensource/License: Free (Apache)Trireme-Kubernetes is a simple, straightforward implementation of the Kubernetes Network Policies specification. One of its most remarkable features is that, unlike similar Kubernetes network security solutions, it doesn't require a central control plane to coordinate the mesh, making the solution trivially scalable. Trireme achieves this installing a single agent per node that will directly tap into the TCP/IP stack of the host.
Image distribution and secrets management
Grafeas
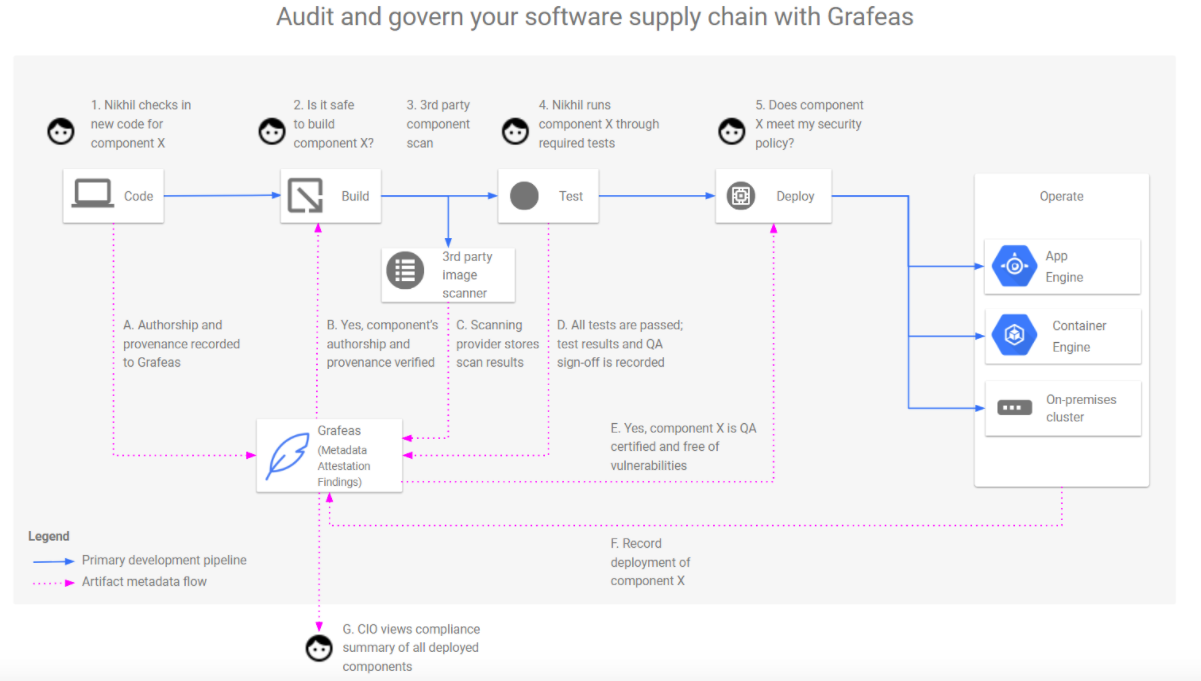
Home Page:https://grafeas.io/License: Free (Apache)Grafeas is an open-source API to audit and govern your software supply chain. On a basic level, Grafeas is a metadata and audit log collection tool that you can use to trace the compliance of security best practices across your organization.This centralized source of truth can help you answer security related questions like:
- Who built and signed a specific container?
- Did it pass all the security scanners and policy checks? When? What was the output for this tools?
- Who deployed it in production? What were the specific parameters used to deploy?
In-toto
Home Page:https://in-toto.github.io/License: Free (Apache)In-toto is a framework designed to provide integrity, authentication and auditability across the entire software supply chain. To roll out in-toto in your infrastructure you will first define a "layout" describing the different steps in your pipeline (repository, CI/CD tools, QA tools, artifact builders, etc) and the users allowed to trigger them (functionaries).In-toto allows you to supervise the layout execution, verifying that each task in the chain is carried out as planned, by authorized personnel only, and that the product is not tampered with in transit.
Portieris
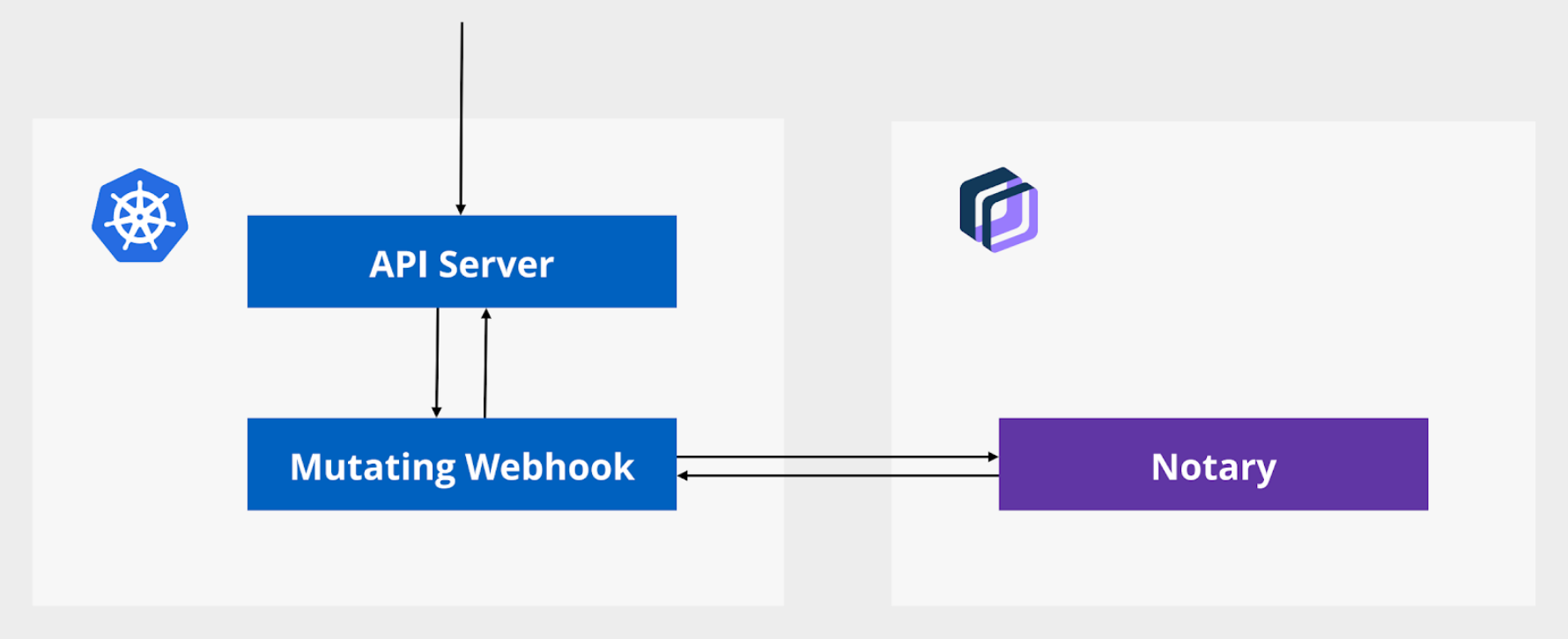
**Home Page: **https://github.com/IBM/portierisLicense: Free (Apache)Portieris is a Kubernetes admission controller used to enforce content trust. It relies on the Notary server as the source of truth for trusted and signed artifacts (i.e. approved container images).Whenever you create or modify a Kubernetes workload, Portieris will pull the signature information and content trust policy for the requested container images and, if required, will modify the API JSON object on the fly to run the signed version of these images instead.
Vault

Home Page:https://www.vaultproject.io/License: Free (MPL)Vault is a high-security storage solution for secrets like passwords, oauth tokens, PKI certs, access credentials, Kubernetes secrets, etc. It supports many advanced features like ephemeral security token leases or orchestrated key rolling.You can deploy vault itself as a new deployment in your Kubernetes cluster using a Helm chart and Consul as its backend storage. It supports Kubernetes native resources like the serviceaccount tokens and can even be configured as your default Kubernetes Secrets store.
Security audit
Kube-bench
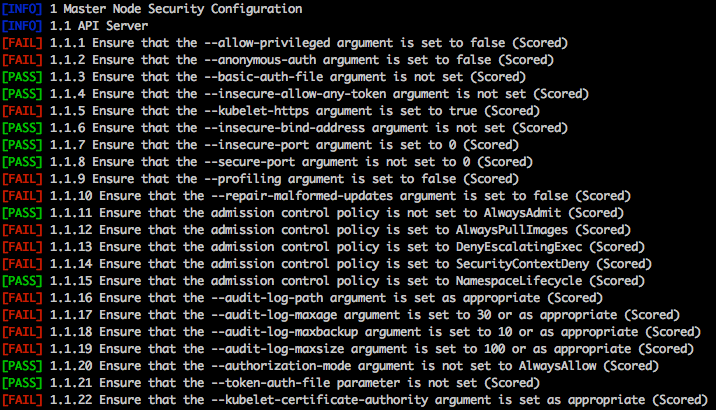
**Home page: **https://github.com/aquasecurity/kube-benchLicense: Free (Apache)kube-bench is a Go application that checks whether Kubernetes is deployed securely by running the checks documented in the CIS Kubernetes Benchmark.Kube-bench will look for insecure configuration parameters on your Kubernetes cluster components (etcd, API, controller manager, etc), sensitive file permissions, insecure accounts or exposed ports, resource quotas, configuration of the APIs rate limiting to protect you against DoS, etc.
Kube-hunter
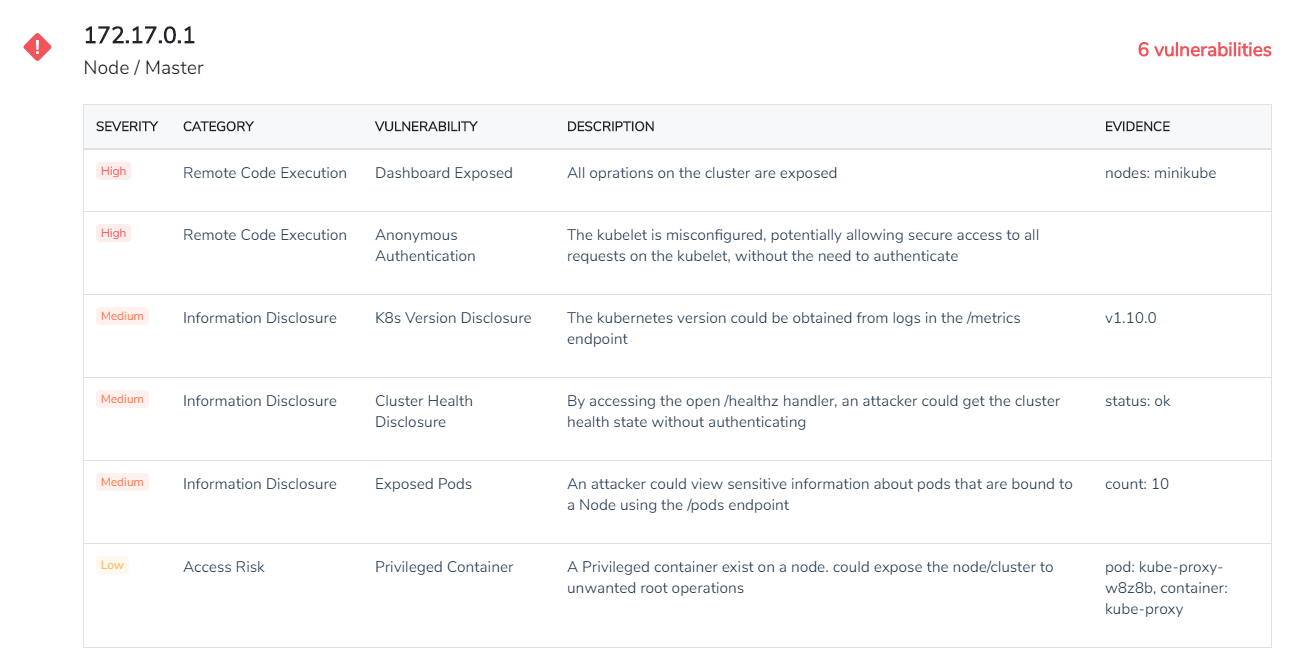
**Homepage: **https://github.com/aquasecurity/kube-hunterLicense: Free (Apache)Kube-hunter hunts for security weaknesses (like remote code execution or information disclosure) in your Kubernetes clusters. You can run kube-hunter as a remote scanner, which will give you the point of view of an external attacker or as a pod inside your Kubernetes cluster.A distinctive feature offered by kube-hunter is that it can be run using "active hunting", this means not only reporting, but actually trying to exploit the vulnerabilities found in the target Kubernetes, which can be potentially harmful to the cluster's operations. Handle with care :).
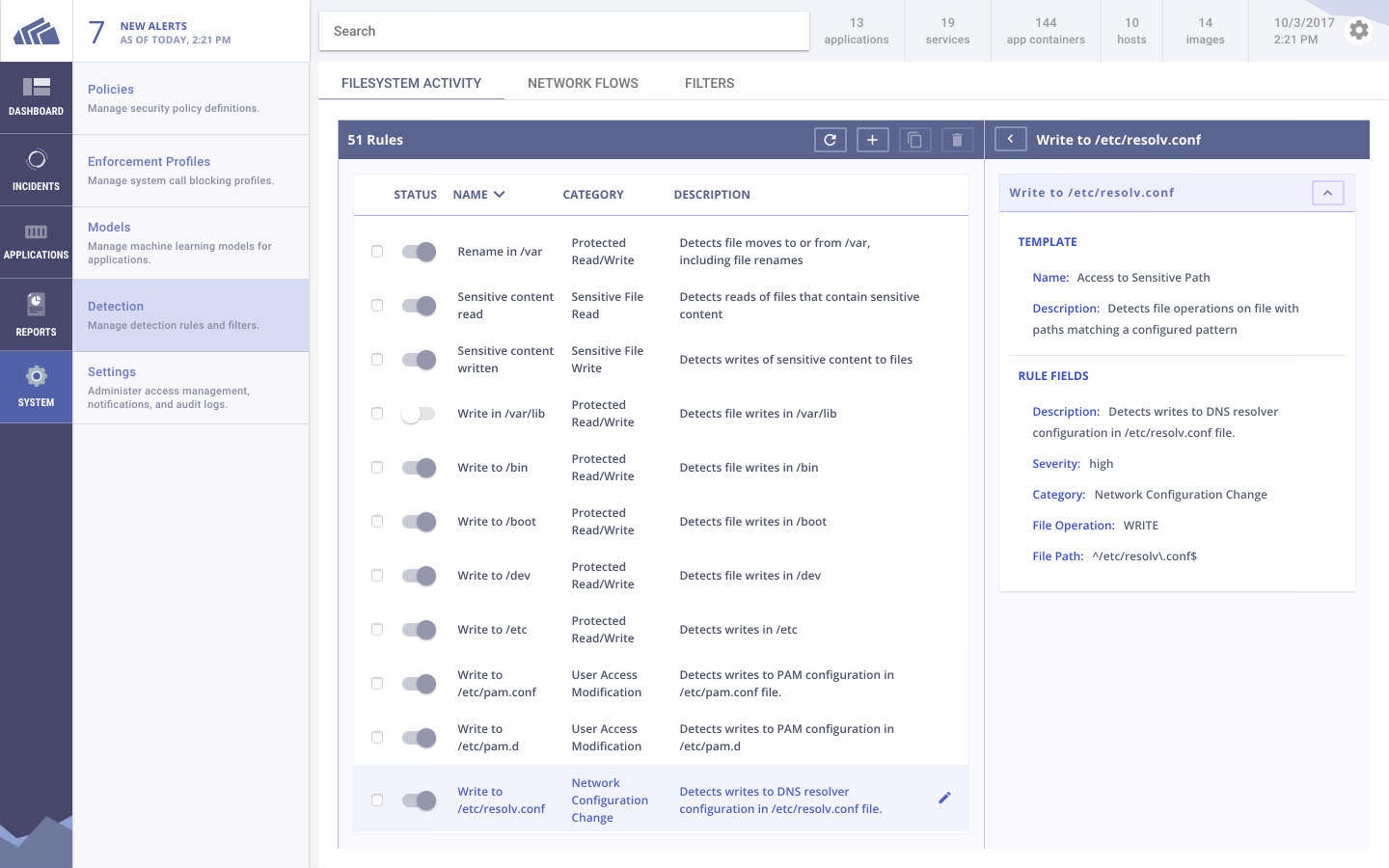
Kubeaudit
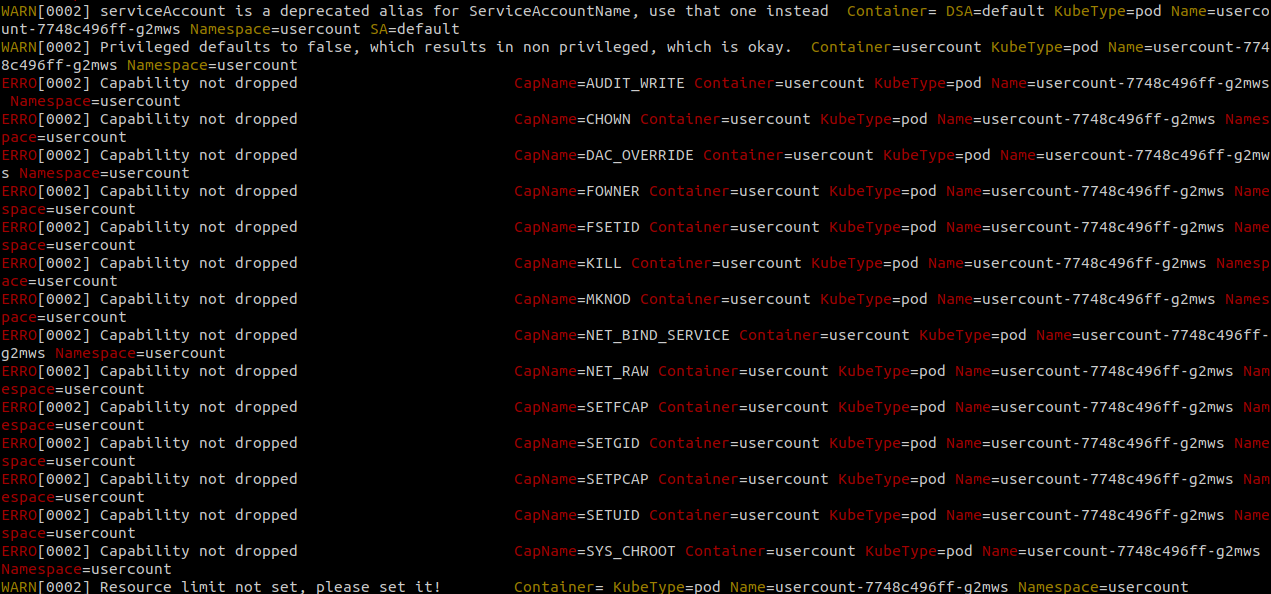
**Home page: **https://github.com/Shopify/kubeauditLicense: Free (MIT)Kubeaudit is a free command line tool originally created at Shopify to audit Kubernetes configuration for various different security concerns. You can spot container images running without limits, running as root, using privileged capabilities or the default serviceaccount, to name a few.Kubeaudit does have several other noteworthy features, for example, it can process your local YAML files to detect configuration flaws that will lead to any of the security issues covered by this tool, automatically fixing them for you.
Kubesec
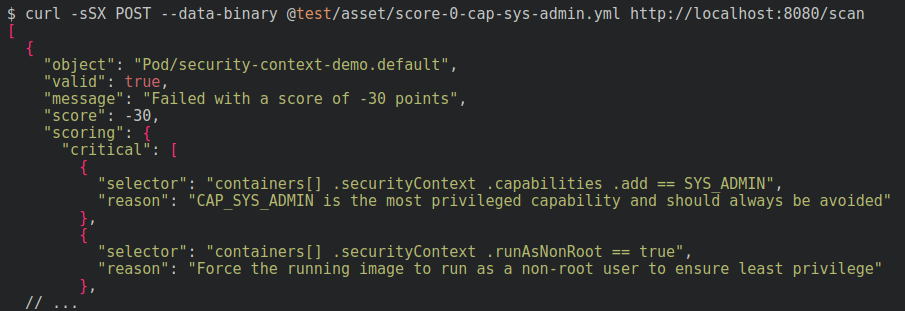
**Home page: **https://kubesec.io/License: Free (Apache)Kubesec is a rather special security tool in the sense that it will directly scan the YAML files where you declare your Kubernetes resources to find weak security parameters.It can detect, for example, excessive capabilities and permissions granted to a pod, using root as the default container user, attaching to the host network namespace, or dangerous mounts like host /proc or the docker socket. Another nice feature of Kubesec is their online demo linter, you can just post a YAML there and start trying it right away.
Open Policy Agent
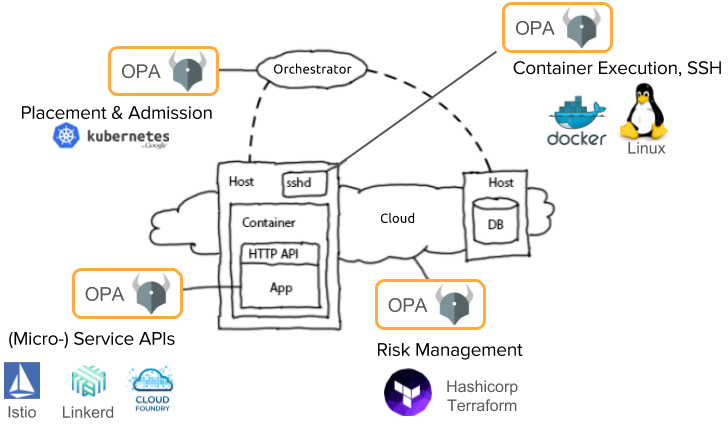
Home Page:https://www.openpolicyagent.orgLicense: Free (Apache)The vision of OPA (Open Policy Agent) is to decouple your security policies and security best practices from your specific runtime platform: Docker, Kubernetes, Mesosphere, Openshift or any combination of them.You can, for instance, deploy OPA as the backend for a Kubernetes admission controller, delegating the security decisions so the OPA agent that can validate, deny or even modify requests on the fly to enforce you custom security constraints. OPA Security policies are written using Rego, its domain specific language.
End-to-end commercial security tools
We decided to create a separate category for the commercial security platforms, as they usually cover several security areas. You can check the table below to get an overall picture:
*Advanced forensics and post mortem analysis providing a complete syscall capture
Aqua Security
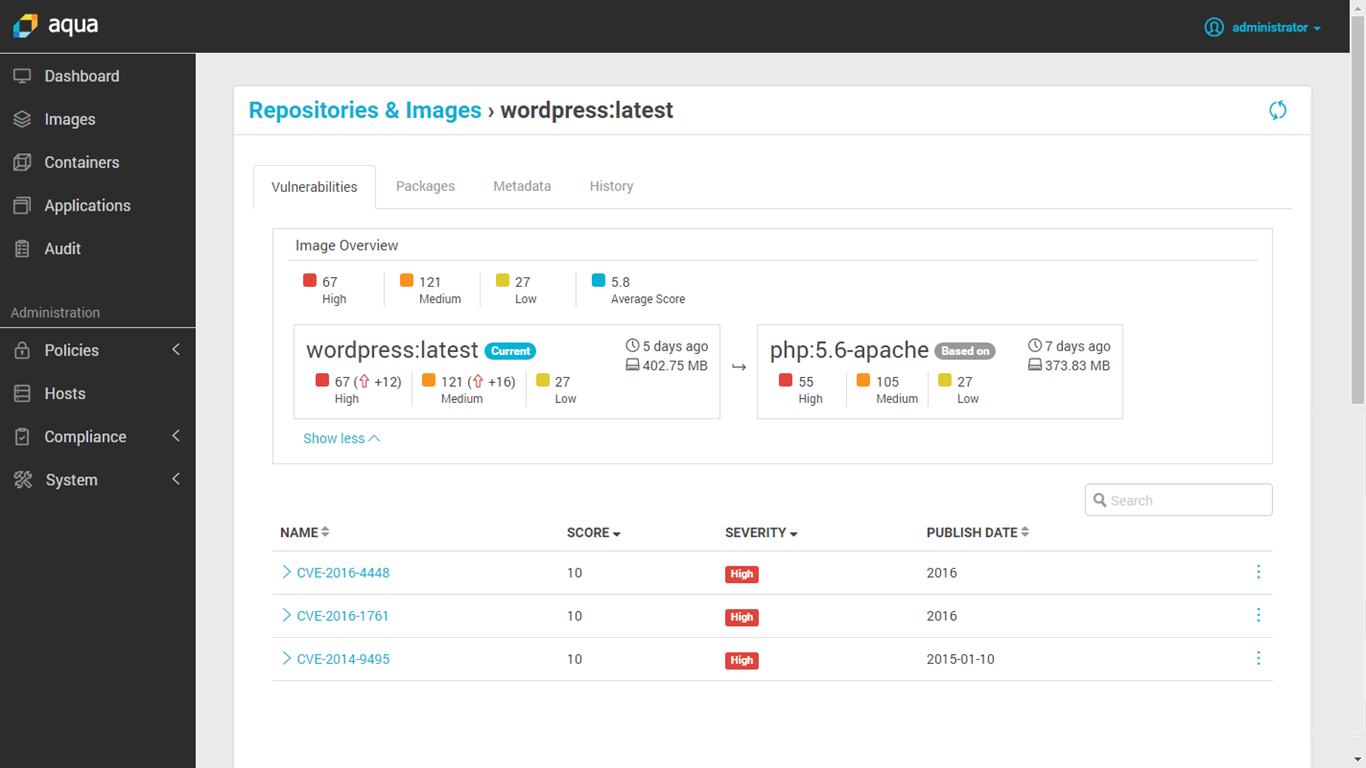
**Home Page: **https://www.aquasec.com/License: CommercialAquaSec is a commercial security tool aimed at containers and cloud workloads, including:
- Image scanning, integrated with your container registry or CI/CD pipeline
- Runtime protection to detect container modifications or suspicious activity
- Container-native application firewall
- Serverless security for cloud services
- Compliance and audit reporting, integrated with event logging
Capsule8

Home Page:https://capsule8.com/License: CommercialCapsule8 integrates with your infrastructure deploying a sensor on your on-prem or cloud Kubernetes cluster. This sensor will collect host and network telemetry, matching this activity against different attack patterns.The Capsule8 team is in charge of detecting and disrupting 0-day attacks before they manage to advance through your systems. Their security operations team can push targeted rules to your sensors as a response to recently discovered threats of software vulnerabilities.
Cavirin
**Home Page: **https://www.cavirin.com/License: CommercialThe Cavirin solution is focused on providing an enterprise counterpart to the different security standardization bodies. Apart from its image scanning capabilities, it can integrate with your CI/CD pipeline, blocking non-compliant images before they get pushed to your private repositories.Cavirin security suite uses machine learning to provide a credit-like scoring of your cybersecurity state, offering remediation tips to improve your security posture or security standards compliance.
Google Cloud Security Command Center
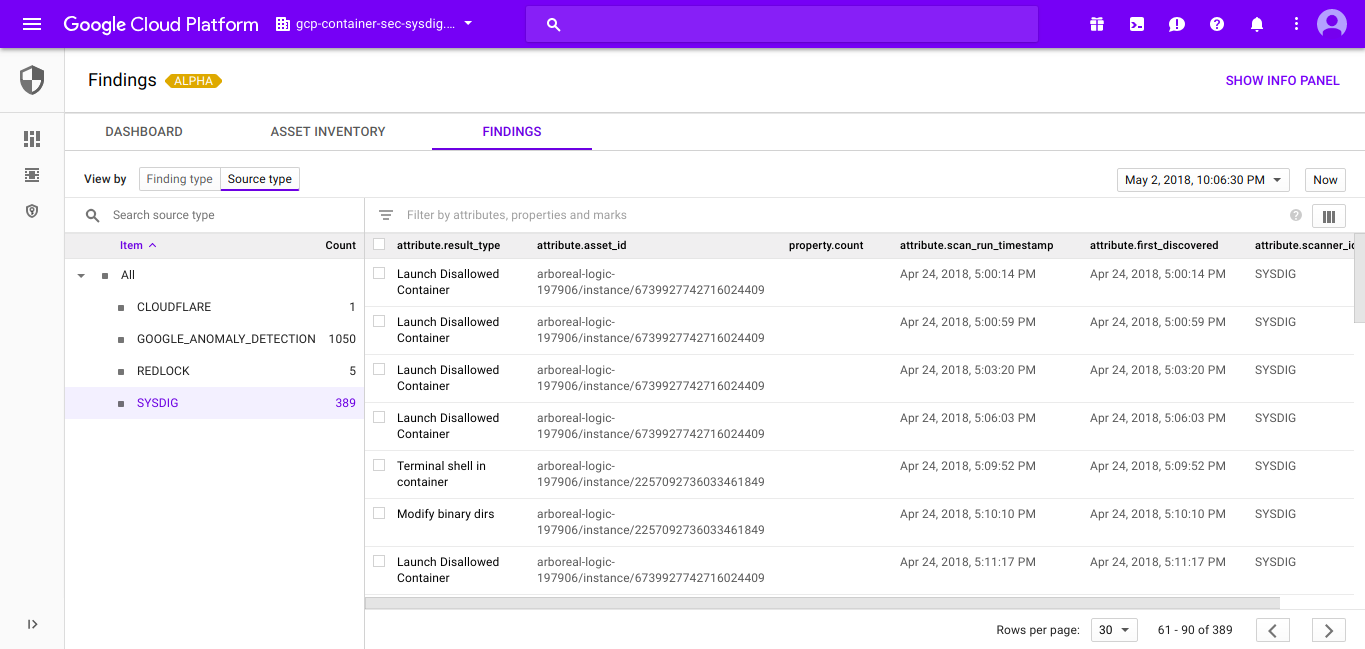
**Home Page: **https://cloud.google.com/security-command-center/**License: **CommercialCloud Security Command Center helps security teams gather data, identify threats, and act on them before they result in business damage or loss.The Google Cloud SCC is, as its name suggests, a unified control panel where you can integrate your different security reports, asset inventories and third party security engines, all from a single, centralized dashboard.The interoperable API provided by Google Cloud SCC facilitates integration of security events coming from different sources like: Sysdig Secure (Container security for Cloud-Native applications) or Falco (Opensource runtime security engine).
Layered Insight (Qualys)
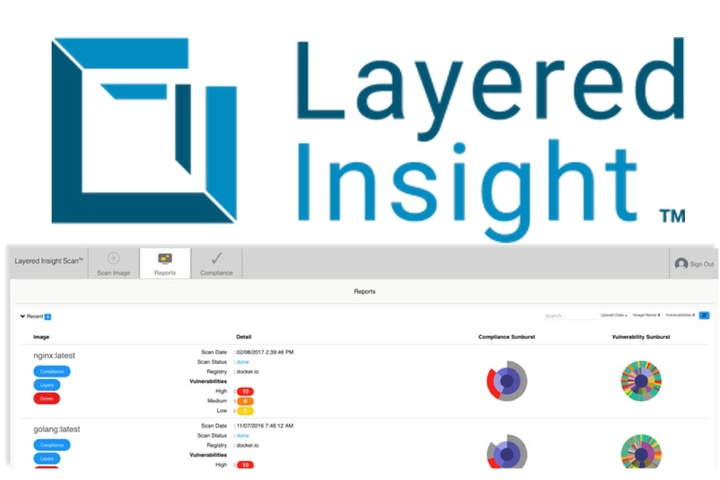
**Home Page: **https://layeredinsight.com/License: CommercialLayered Insight (now part of qualys) is designed around the concept of "embedded security". Once the original image is scanned for vulnerabilities using static analysis techniques, and passes the CVE checks, Layered Insight replaces it with an instrumented image by injecting a binary agent.This binary include runtime security probes for the container network traffic, I/O streams and application activity, in addition to any custom security check provided by the infrastructure operator or DevOps teams.
NeuVector
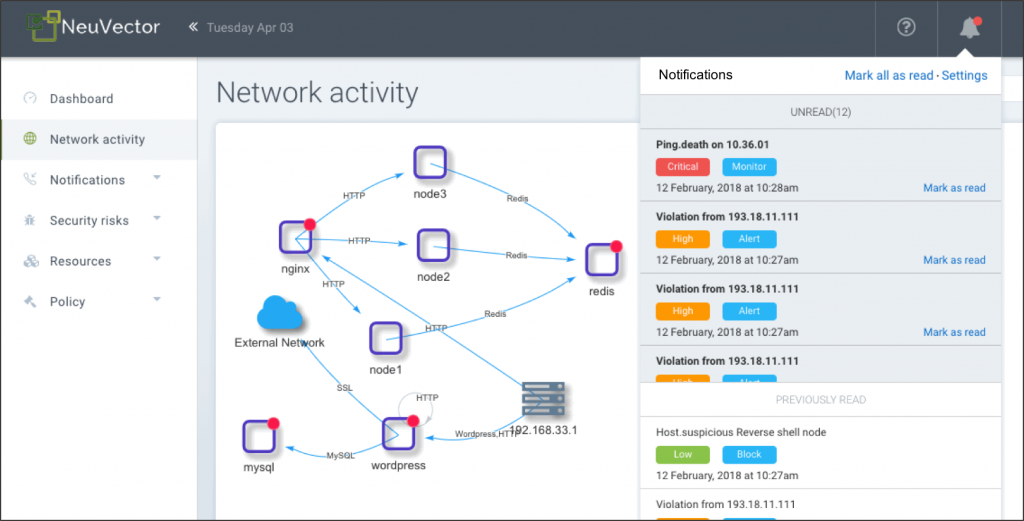
Home Page:https://neuvector.com/**License: **CommercialNeuVector performs container security baselining and runtime protection by analyzing the network activity and application behaviour to create a tailored security profile per image. It can also proactively block threats, isolating suspicious activity by modifying the local network firewall.NeuVector's network integration, labelled as "Security Mesh", is able to perform deep packet inspection and layer7 filtering of all network connections in your service mesh.
StackRox
**Home Page: **https://www.stackrox.com/License: CommercialStackRox container security platform aims to cover the entire lifecycle of the Kubernetes applications in your cluster. Like other commercial container security platforms in this list, it generates a runtime profile based on observed container behaviour and will automatically alert on any abnormality.The StackRox platform will also evaluate Kubernetes configurations using the CIS Kubernetes benchmark, among other container compliance benchmarks.
Sysdig Secure
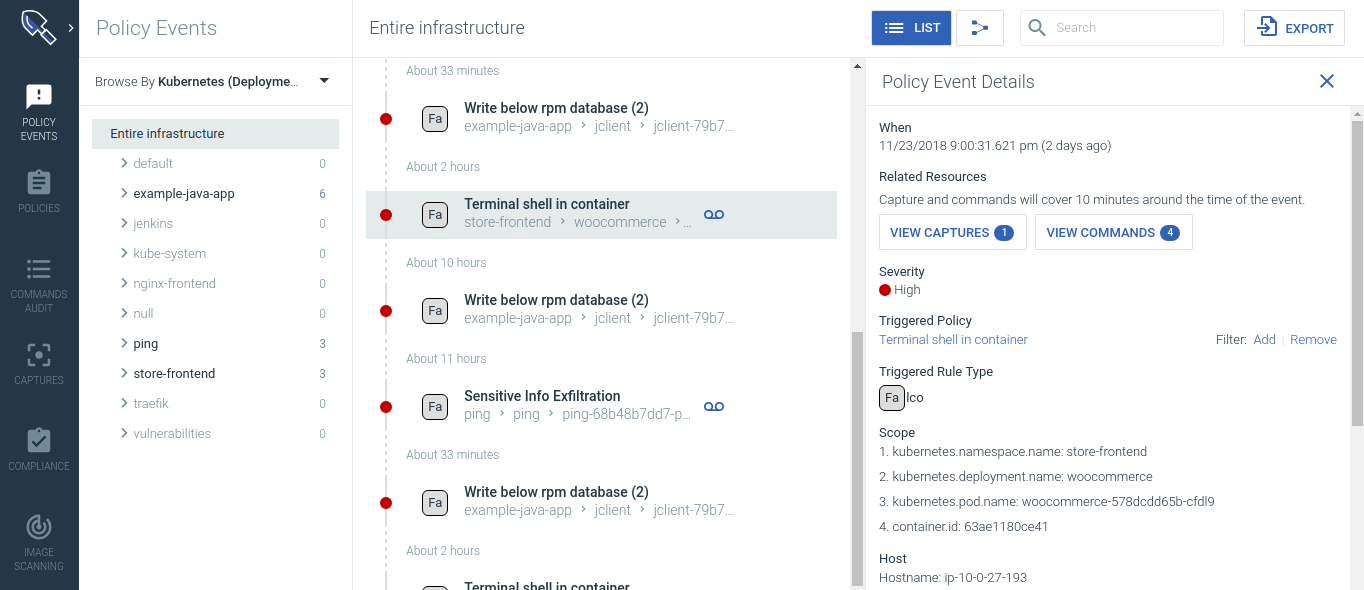
Home Page:https://sysdig.com/products/secure/License: CommercialSysdig Secure protects your applications across the Kubernetes and container lifecycle securing both the CICD pipeline and production environments. It provides image scanning, ML based runtime protection, and forensics to identify vulnerabilities, enforce compliance, and block threats across your microservices. Sysdig Secure integrates with CICD tools like Jenkins and also secures images pulled from Docker registries to prevent risky images from being pushed to production. It also provides comprehensive runtime security including:
- ML based runtime profiling and anomaly detection
- Runtime policies based on system events, K8s-audit API, community (FIM, cryptojacking) and MITRE ATT&CK framework
- Incident remediation and response
Tenable Container Security
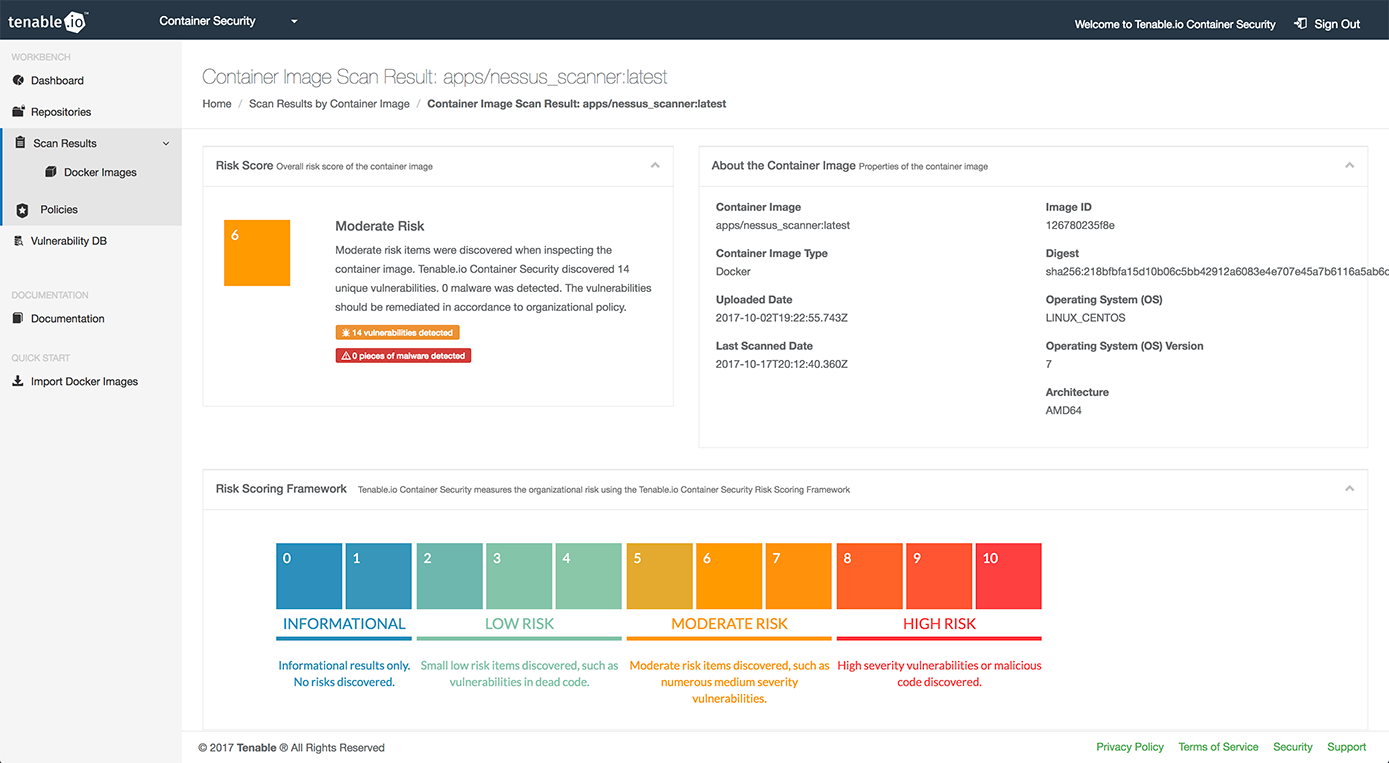
**Home Page: **https://www.tenable.com/products/tenable-io/container-securityLicense: CommercialTenable was widely known in the security industry before the advent of containers as the company behind Nessus, a popular vulnerability scanning and security auditory tool.'Tenable container security' leverages their experience in the computer security field to integrate your CI/CD pipeline with vulnerabilities databases, specialized malware detection engines and security threat remediation advice.
Twistlock (Palo Alto Networks)
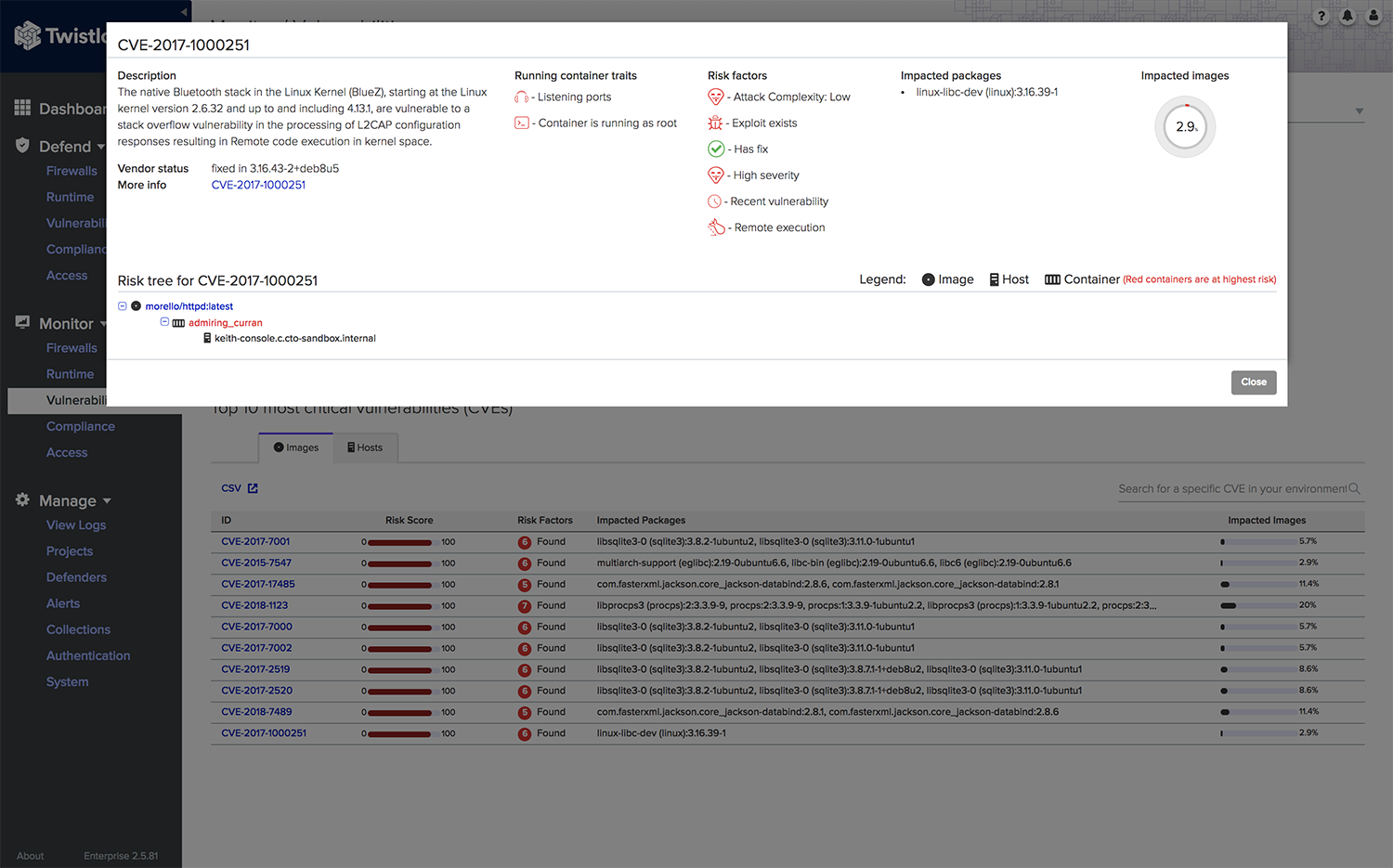
**Home Page: **https://www.twistlock.com/License: CommercialTwistlock advertises itself as a cloud-first, container-first platform, providing specific integrations with cloud providers (AWS, Azure, GCP), container orchestrators (Kubernetes, Mesospehere, Openshift, Docker), serverless runtimes, mesh frameworks and CI/CD tools.Apart from the usual container security enterprise features like CI/CD pipeline integration or image scanning, Twistlock uses machine-learning techniques to generate behavioural patterns and container-aware network rules.Twistlock was acquired by Palo Alto Networks, also owner of the Evident.io and Redlock security solutions. TBD how these three platforms integrate into Palo Alto's PRISMA.
Help us build the best security tools directory!
We strive to make this page the go-to directory for security tools, but we cannot do it alone! Do you know of cool security tools that should be included in this list? Did you spot any mistakes or outdated information?If this article was interesting to you, don't hesitate to join us for a live online session "Choosing Security Tools for your Organization", July 30th.If you want to keep up with the security projects and news, subscribe to our container newsletter, a monthly email with the coolest stuff happening in the cloud-native ecosystem.


