
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Amazon EKS Anywhere (EKS-A) on Bare Metal is a new deployment option recently launched for Amazon Elastic Kubernetes Service. Why bare metal? In the age of the cloud it would seem to go against "best practices." On the contrary. While we tend to overuse the term, "hybrid cloud," it is a real thing. Enterprises come in all shapes and sizes — and so do their compute choices and privacy requirements. EKS-A Bare Metal enables you to provision and manage Amazon EKS Distro clusters in your data center on your own bare metal infrastructure.
As a Container Security Competency partner of AWS, Sysdig brings security, visibility, and compliance capabilities for containers and cloud to any EKS environment, now including EKS-A Bare Metal. In this blog, we'll take a look at EKS-A Bare Metal use cases and see how you can use Sysdig Secure and Sysdig Monitor to protect and observe your workloads and infrastructure.
Why run containers on Amazon EKS-A Bare Metal
EKS-A Bare Metal is powered by the Amazon EKS Distro, which runs upstream Kubernetes. This means you can easily migrate your standard Kubernetes applications without refactoring your code. The eksctl-anywhere binary will power on and provision an OS on your bare metal machines, then create a Kubernetes cluster on your bare metal environment. To do this, it takes advantage of Tinkerbell, an open-source bare metal provisioning engine. Tinkerbell stores datacenter hardware inventory information that is used used by the EKS-A CLI for provisioning and cluster creation. Check out the details on getting started in the this AWS post.
Check out this AWS video to learn more about EKS-A on Bare Metal.
Kubernetes on Bare Metal use cases
There may be a number of different reasons you want to run Kubernetes on bare metal. Control and security are often cited as reasons why an organization chooses to go this route. 58% of the respondents in this informal poll by Canonical on LinkedIn chose control and security as their top reason to build on bare metal. Performance is another reason why customers choose to run Kubernetes clusters directly on bare metal. Stripping out the hypervisor enables direct access to the hardware bypassing a good amount of overhead required to run using VMs.
Of course, many organizations have moved to the cloud to get out of the business of managing physical servers. Yet, for some, the use cases for which they want to use bare metal still exist. It's possible to play the middle and take advantage of bare metal services in the cloud or with a colocation vendor like Equinix. Whichever approach is chosen, the fact of the matter is that many businesses have different performance profiles and requirements across different workloads. For example, some of the use cases we've encountered include:
- Performance-sensitive workloads such as databases and analytics
- Compute-heavy apps like AI/ML
- Cloud gaming and streaming
- Edge computing for telco or retail
- Latency-sensitive video streaming
Regardless of the reason you choose bare metal to run Kubernetes, you should carefully consider what's needed for security to reduce risk and safeguard against potential threats and bad actors. We have validated the Sysdig platform with EKS-A Bare Metal to ensure AWS customers have the security and visibility needed to confidently run containers anywhere with EKS.
Using Sysdig to secure and monitor EKS-A on Bare Metal
Sysdig is well suited for securing and monitoring any (or should I say all?) EKS Anywhere environments. Our platform is built on an open-source stack to provide insight into Kubernetes, containers, and cloud. Sysdig's instrumentation inspects and filters Linux syscalls to help you understand the actual behavior of your containerized microservices. It also integrates with the Kubernetes API to provide context for the behavior of your workloads (e.g., which cluster/namespace/pod/container) and alert on suspicious orchestrator activity as reported by your EKS.
If you're using EKS-A Bare Metal along with EKS "classic" (a hybrid-cloud model), you'll be able to observe and secure all of your clusters with a unified view using Sysdig. You can deploy the Sysdig agent instrumentation anywhere you need to implement security and monitoring. Regardless of whether EKS is on VMware vSphere, bare metal, AWS Outposts, or in the AWS Cloud, you can see and manage your entire estate from one place.
There a few ways you can get started. You can run the agent container as a Kubernetes pod – one per node. If you prefer, you can also install using an AWS CloudFormation template.
By using the Kubernetes DaemonSet feature, EKS will deploy a Sysdig agent on each Kubernetes node in your environment. The Sysdig solution will then automatically monitor all of your hosts, apps, pods, and services, and connect to the Kubernetes API server to pull relevant metadata about the environment.
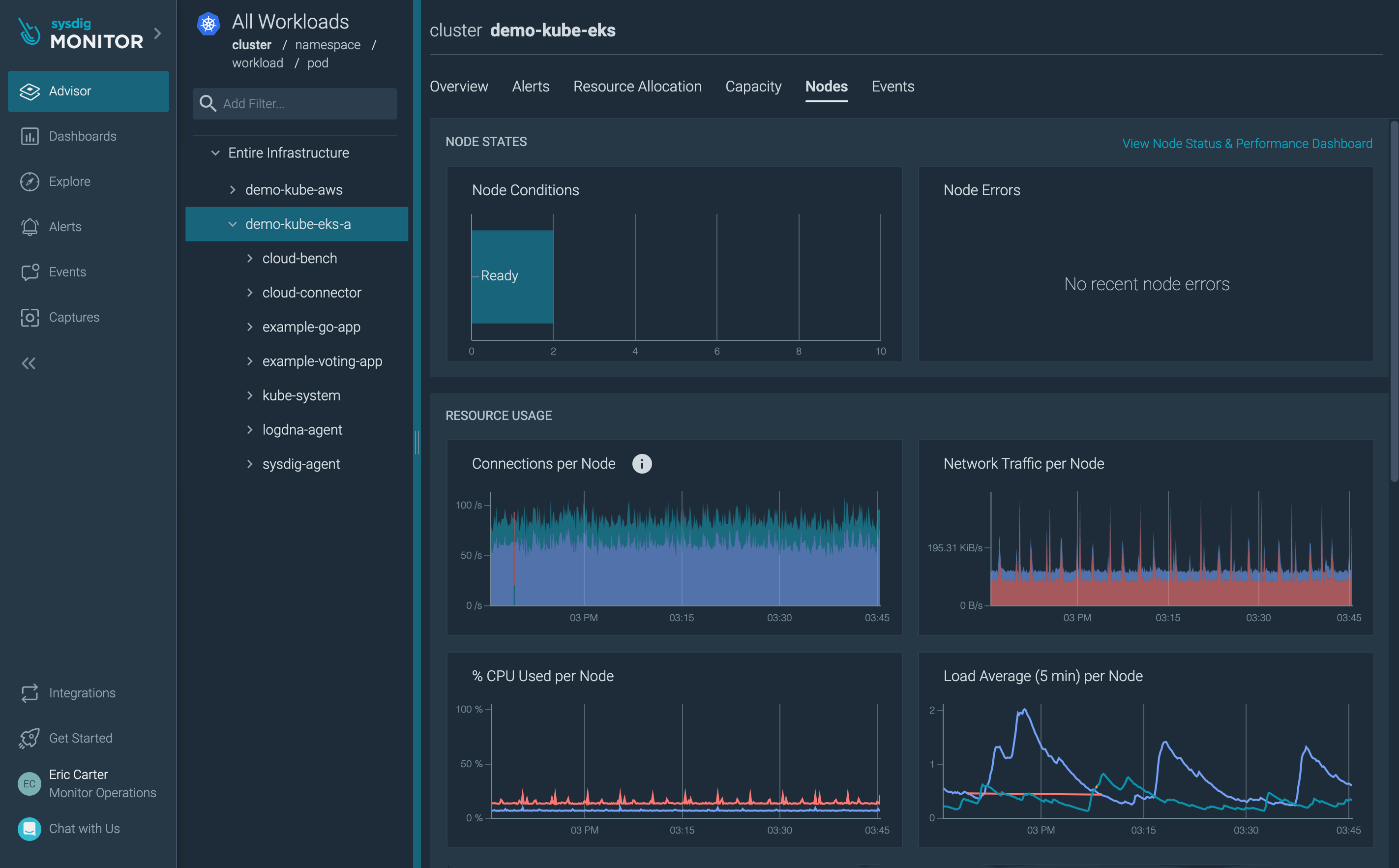
Monitoring an EKS-A Bare Metal environment
Security from source to run for EKS-A Bare Metal
Sysdig Secure is built on a number of open-source projects, including Falco, the cloud-native runtime security project. We've unified a range of security and compliance capabilities that you can apply to your AWS and EKS Anywhere environment – from the time you're building applications through production. This includes, for example:
- Host and image scanning to identify vulnerabilities pre-production and at runtime
- Compliance to control and validate adherence to regulatory standards like PCI and NIST
- Runtime security to detect threats across containers, Kubernetes, and cloud services
- Network security to apply microsegmentation using Kubernetes-native network policies
- Cloud security posture management to flag misconfigurations across EKS and AWS
- Incident response and forensics to investigate security breaches and recover quickly
In the next section, we'll dive deeper into two of these security use cases.
Continuous compliance with EKS-A Bare Metal
Customers in regulated industries, in some cases, have avoided managed services and public cloud in an effort to meet mandates for strict ownership of infrastructure and data. The approach offered by EKS-A Bare Metal lets you keep custody of containers and data locally, but still leverage a consistent AWS management experience.
Sysdig Secure supports your compliance initiatives with compliance-specific policies, as well as checks that you can turn on or off to help you meet requirements for standards such as PCI, NIST, SOC2, and HIPAA.
For example, you can apply image scanning policies built around compliance best practices to help you meet requirements during the build process.
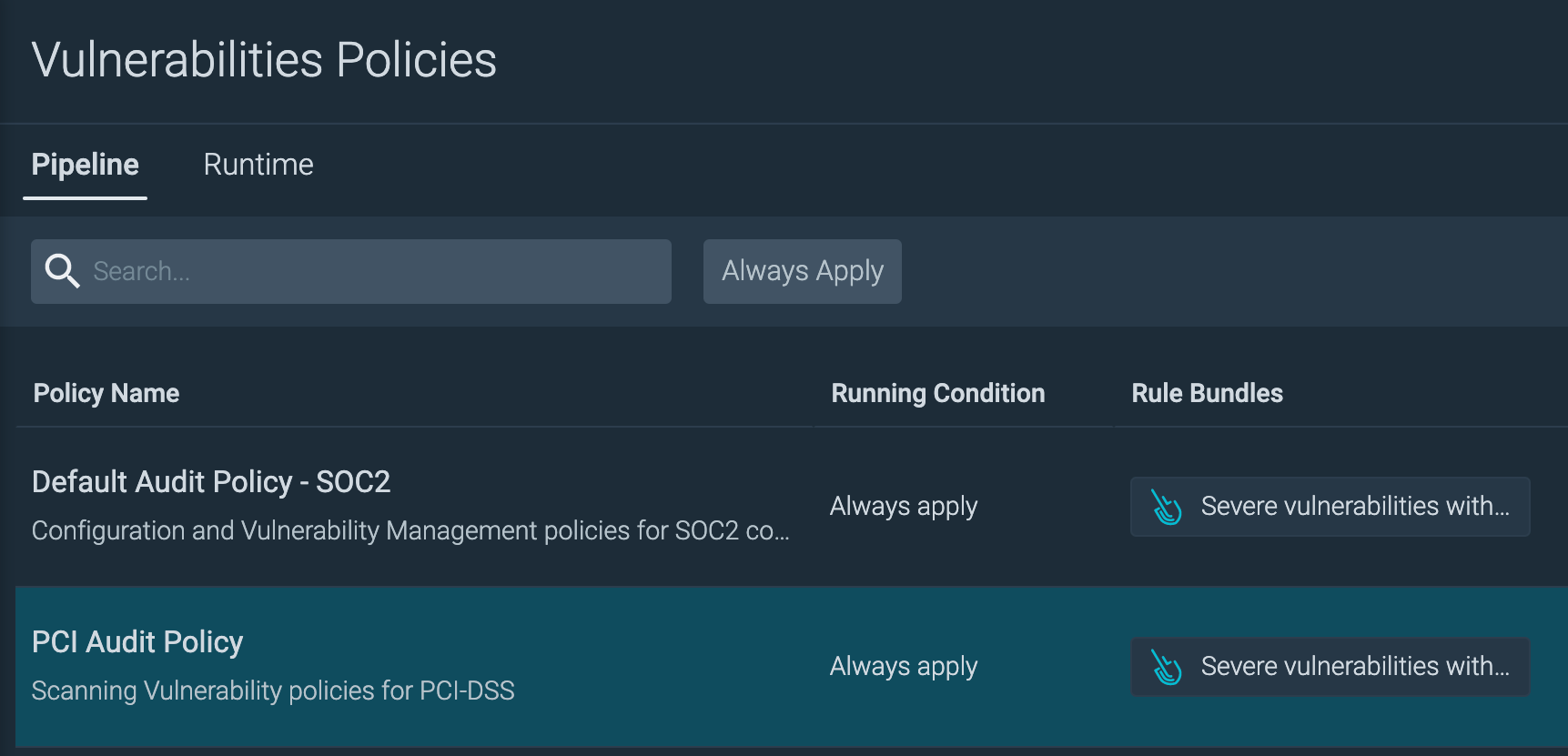
Compliance-focused image scanning policies
You can also validate the compliance posture of your infrastructure and workloads by using CIS benchmarks and other checks designed to help you measure progress against your compliance goals.
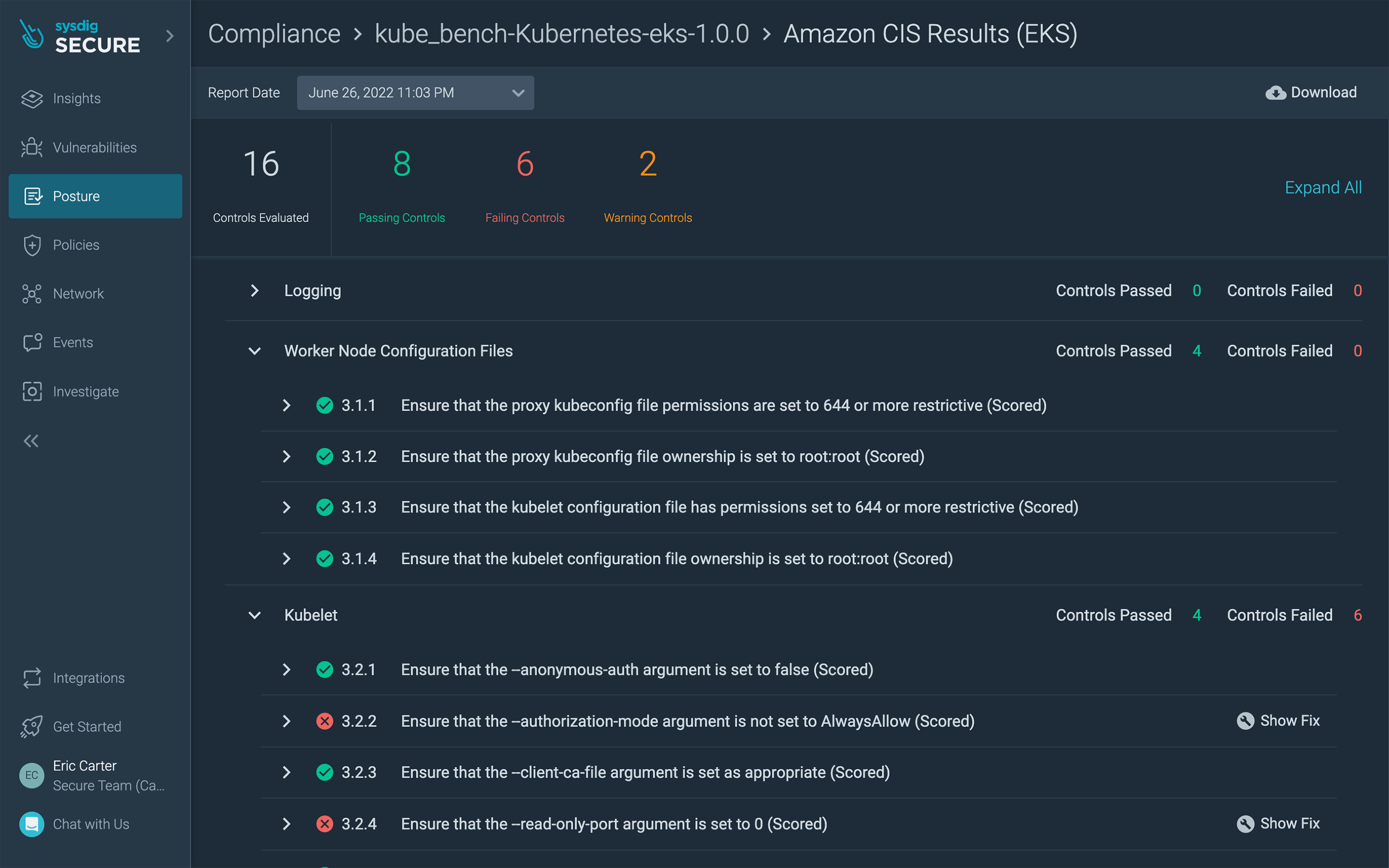
CIS benchmark for EKS
Sysdig detection rules, based on Falco, are mapped to compliance frameworks to help you implement the appropriate controls. Using this capability, you can, for instance, address File Integrity Monitoring (FIM) requirements to meet compliance standards, such as PCI DSS.
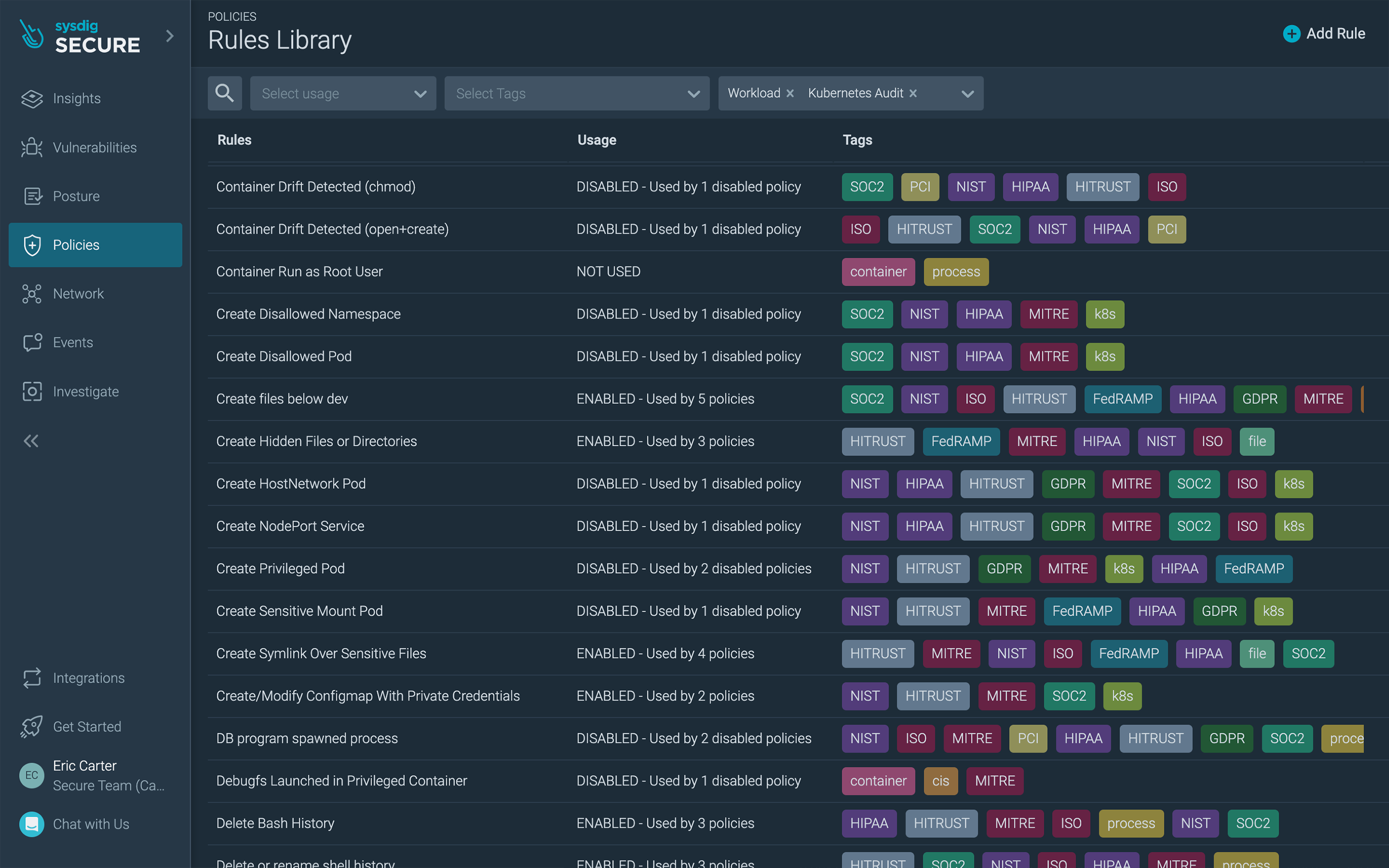
Runtime security rules tagged for compliance standards
Runtime security with EKS-A Bare Metal
Sysdig's runtime security based on Falco provides container-level and cloud activity visibility, leveraging syscalls, k8s audit logs, and cloud logs to help you understand the behavior of your container applications and cloud infrastructure.
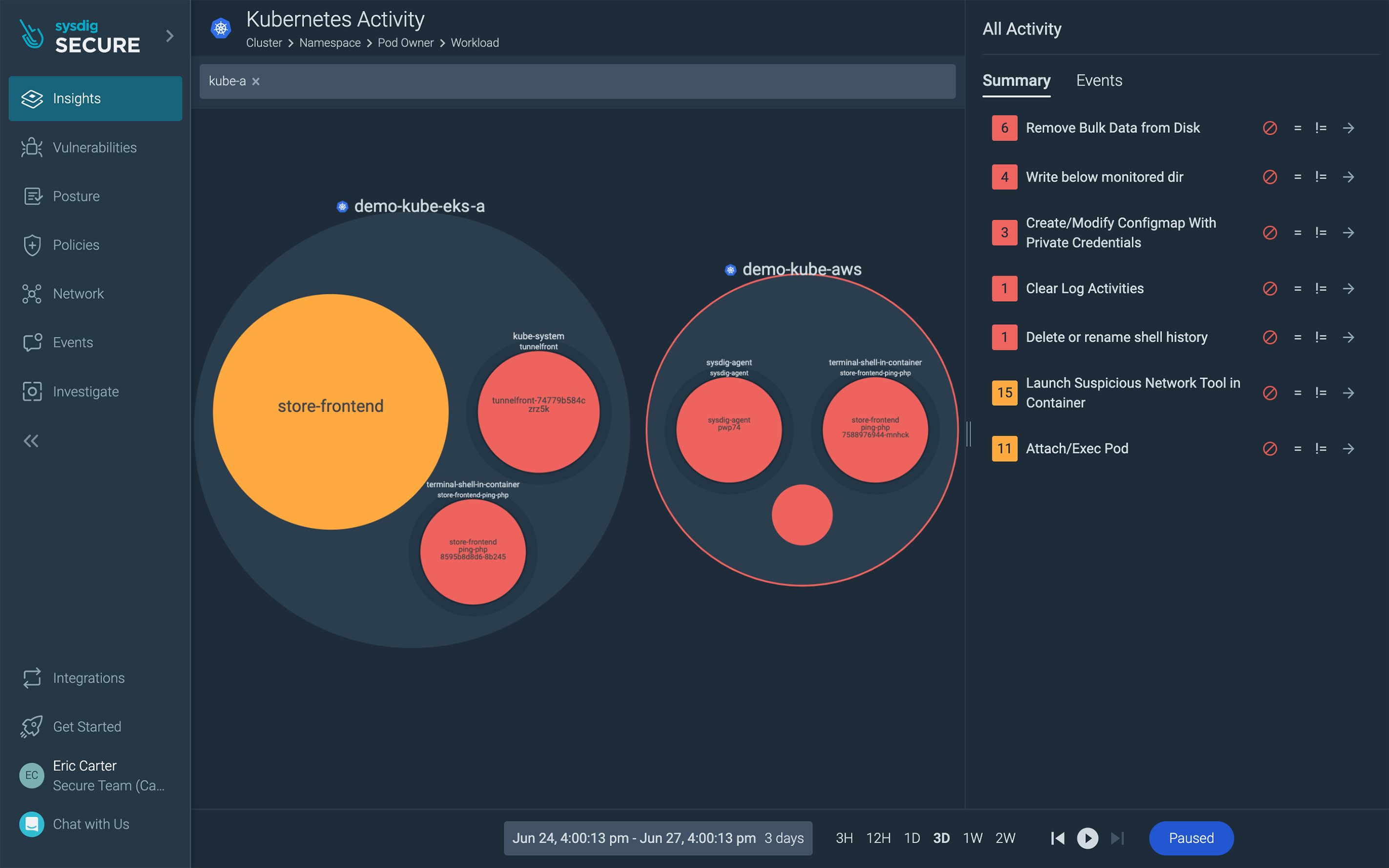
Visibility into container, Kubernetes, and cloud activity
Out-of-the-box policies and the comprehensive rules library shown above let you dial in detections and alert you to threats across your environments. With it, you can, for instance, spot an intrusion into sensitive data via a container running on EKS-A Bare Metal. You can see which cluster, which node, and understand down to a container and process level what was taking place.
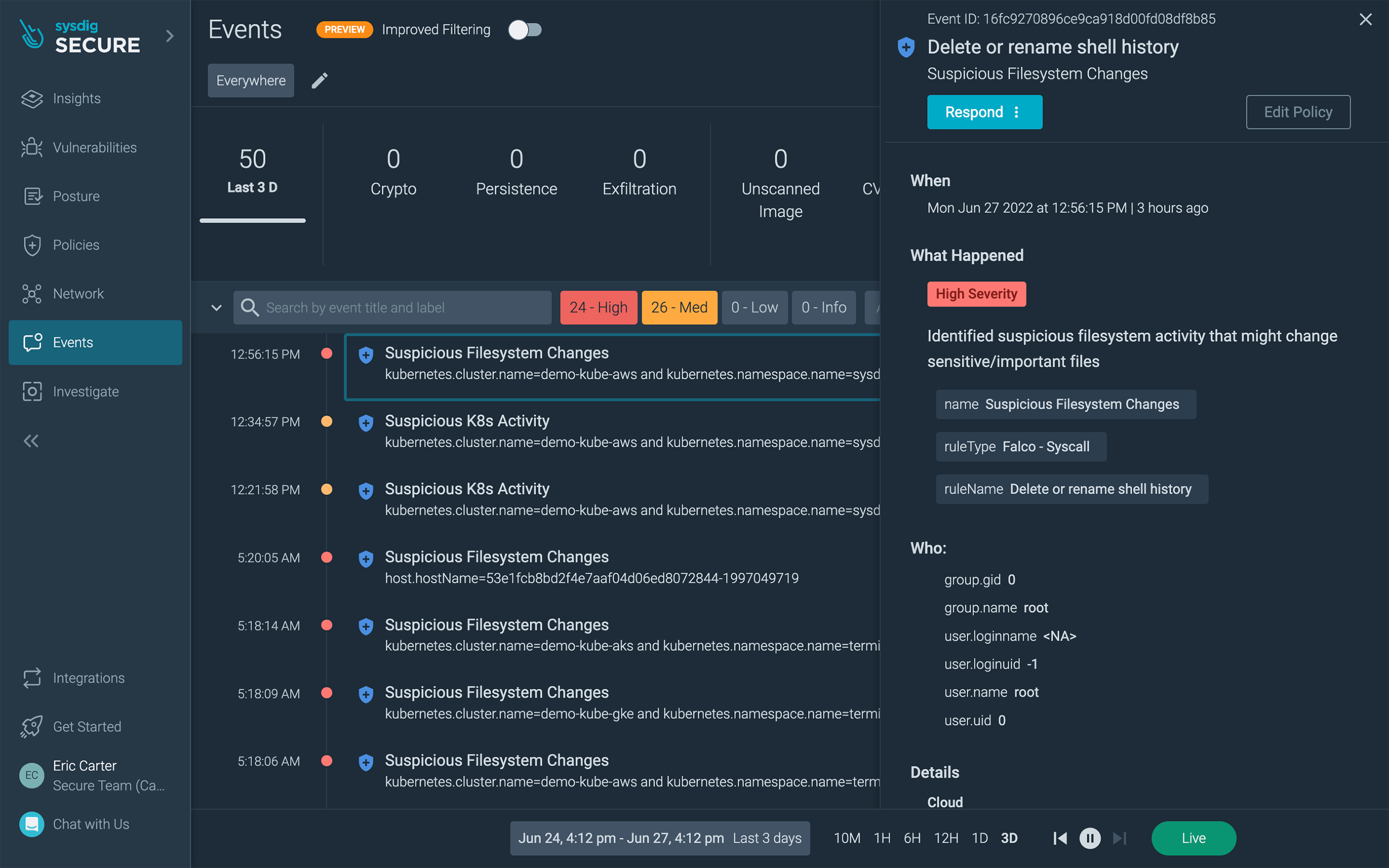
Security event investigation
One of the key values for EKS Anywhere is to provide consistent operations for cloud and on-prem so customers can free themselves from disparate operational models. Similarly, Sysdig can help to alleviate the need to support different security and monitoring tools. Correlating a broader set of telemetry and event information with Kubernetes and cloud context makes the triage of incidents far more effective and less time-consuming.
Read more about Kubernetes security best practices in our Kubernetes Security Guide.
Conclusion
With EKS-A Bare Metal, AWS is continuing its quest to help customers expand their application infrastructure beyond the public cloud. EKS-A brings a consistent AWS management experience to your data center. Both within the cloud and in your own data center, security is something that should be carefully planned and executed. Together with AWS, Sysdig is here to help ensure your success with Kubernetes.
Ready to get started? Check out Sysdig on the AWS Marketplace.


