Cloud Security Compliance
Meet compliance standards (PCI, NIST, GDPR, etc.) for containers and cloud environments with a cloud and container compliance tool like Sysdig Secure.

Cloud and Container Compliance
Ensure cloud and container compliance from source to run with a single solution.
Validate Compliance
Use out-of-the-box controls to meet regulatory standards (PCI, NIST, GDPR, etc.) for cloud and containers across the application life cycle.
Enable Automation
Eliminate manual processes and enforce compliance with controls using policy as code based on OPA.
Pass Audits
Show proof of cloud and container compliance using cloud audit logs and container forensics data.
“With Sysdig, it’s simply night and day as to how quickly and accurately we can manage compliance, as well as avoid costs for being out of compliance.”
– Michal Pazucha, Security Architect at BeekeeperContinuous Compliance
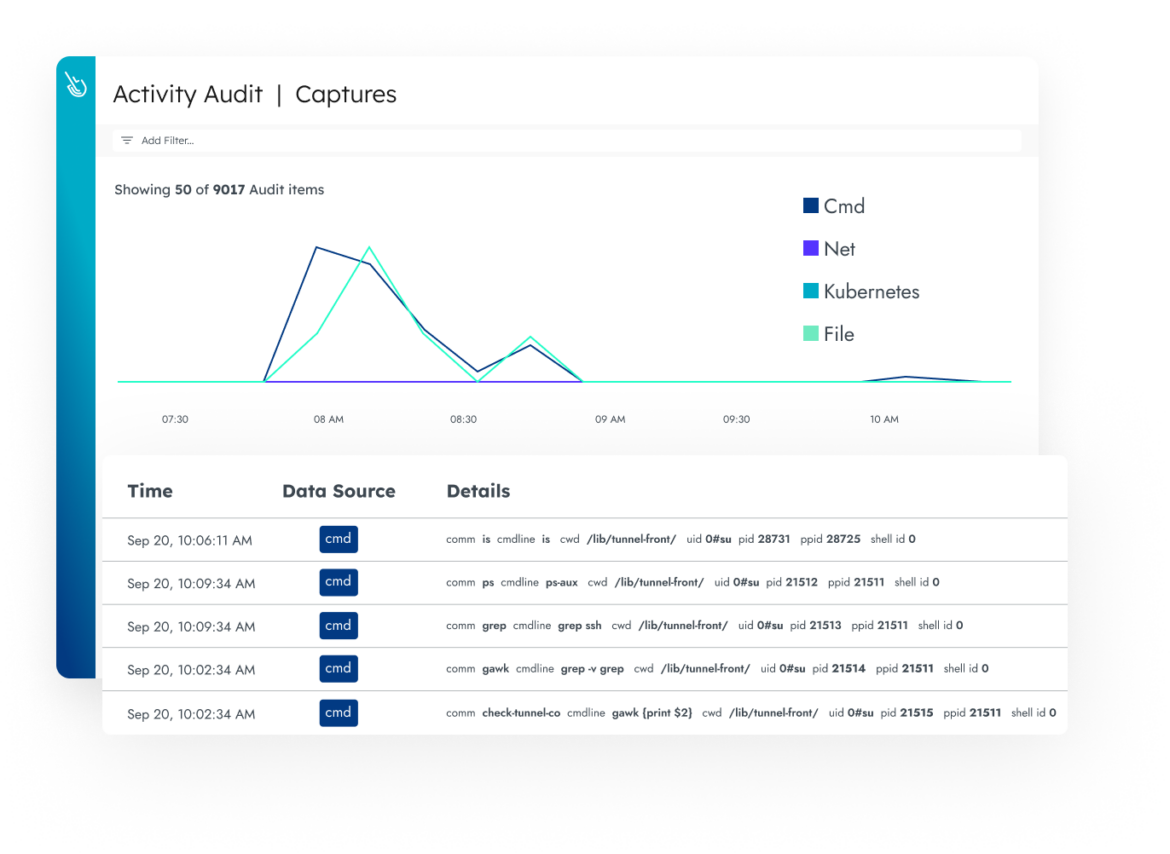
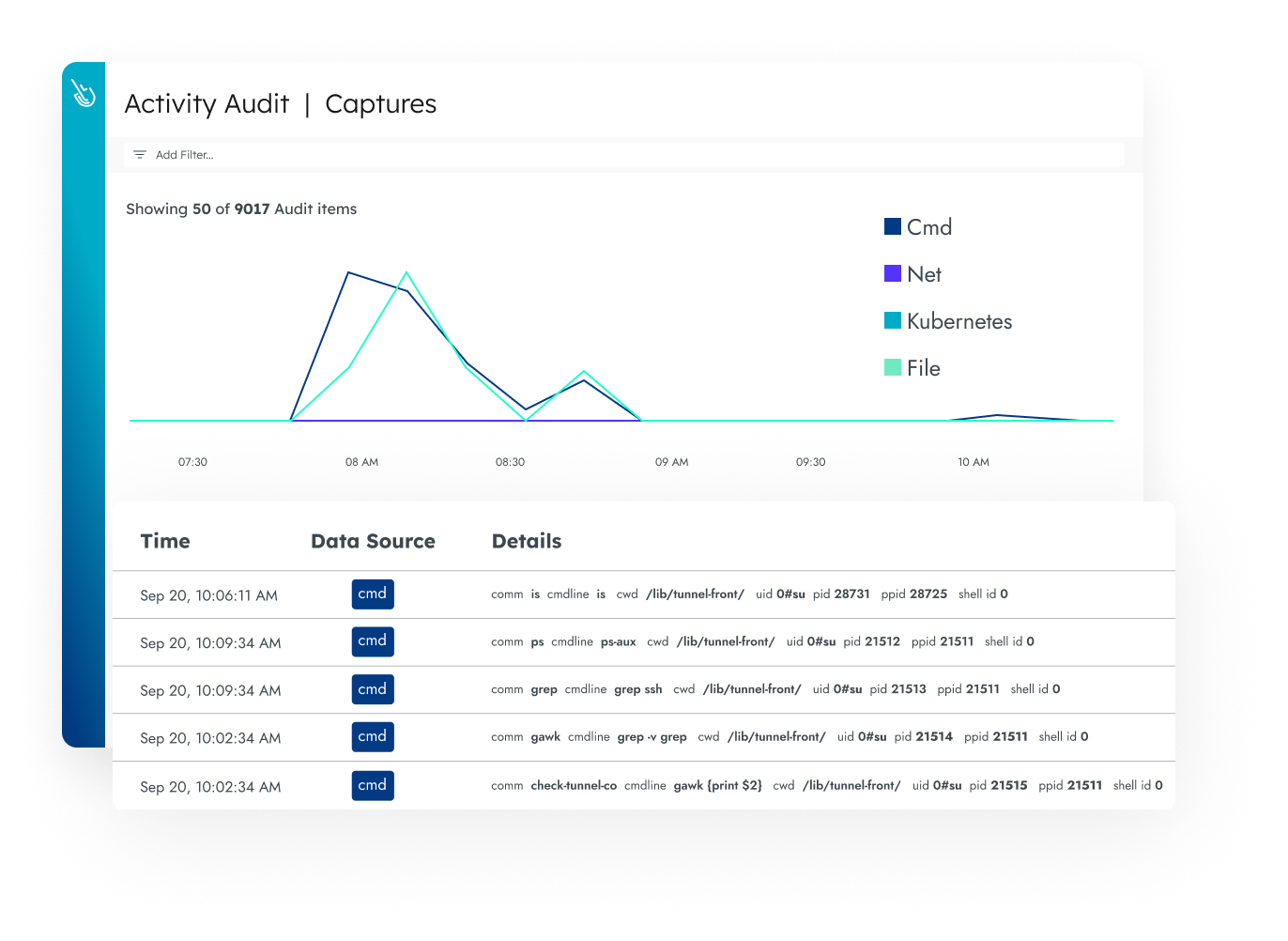
Compliance Auditing
Get detailed audit trails for containers, Kubernetes, and cloud environments. Investigate all suspicious activity performed by a user to see the breadth of impact.
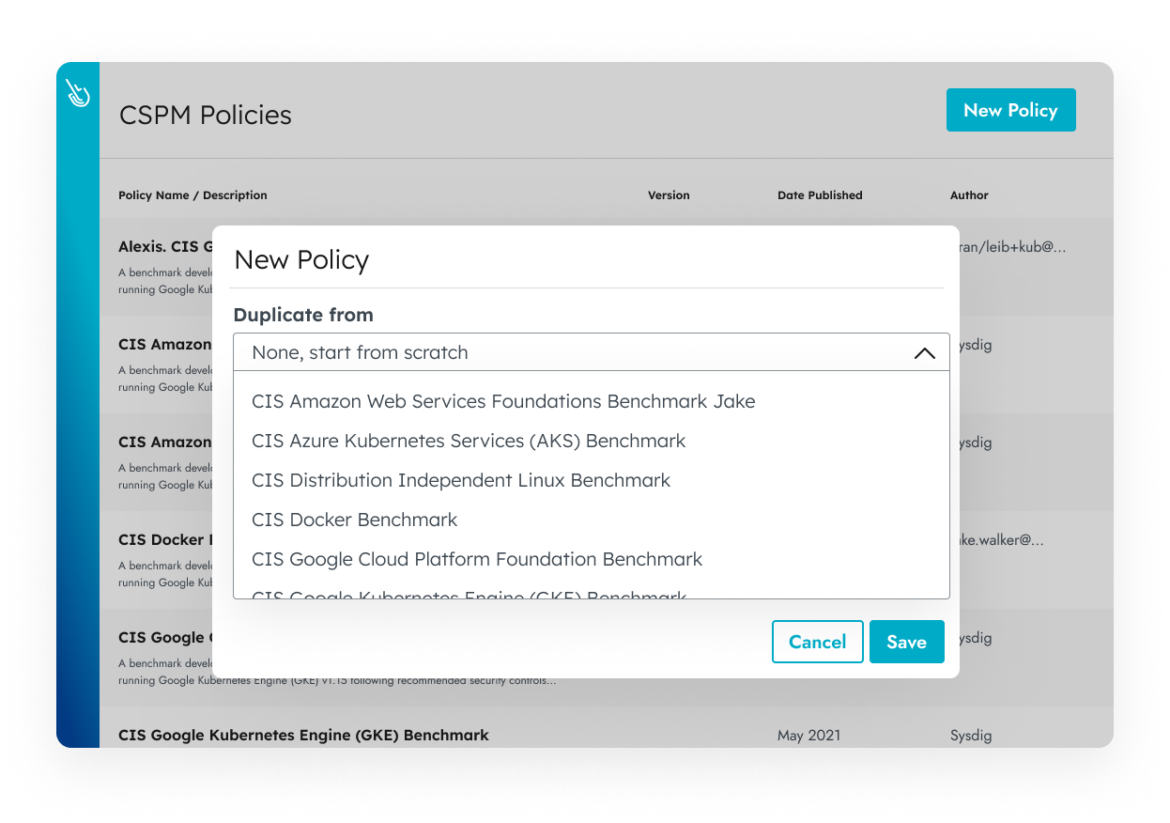
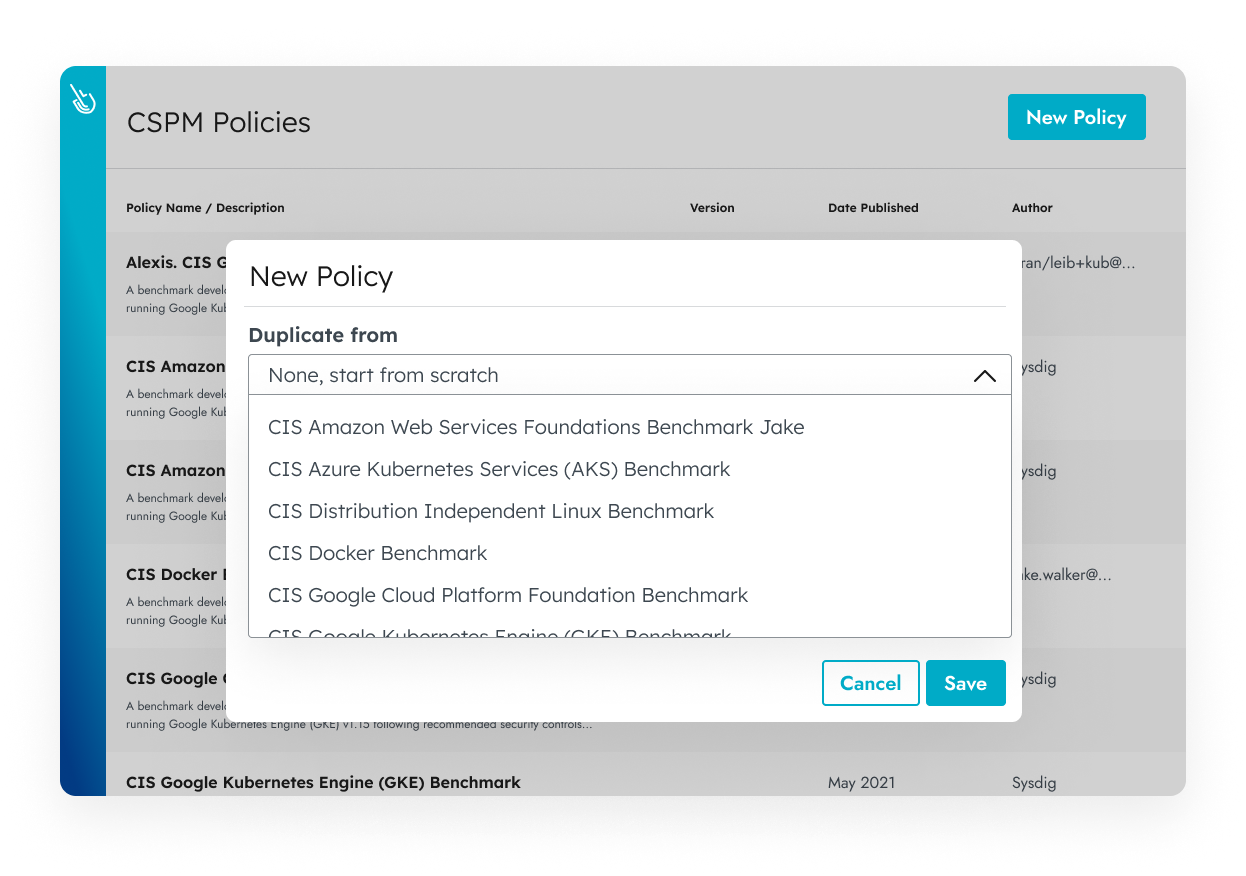
Custom Policies
Create customized security policies that better align with your internal security mandates. Simply duplicate an existing security policy and turn on/off controls or create a new one from scratch.
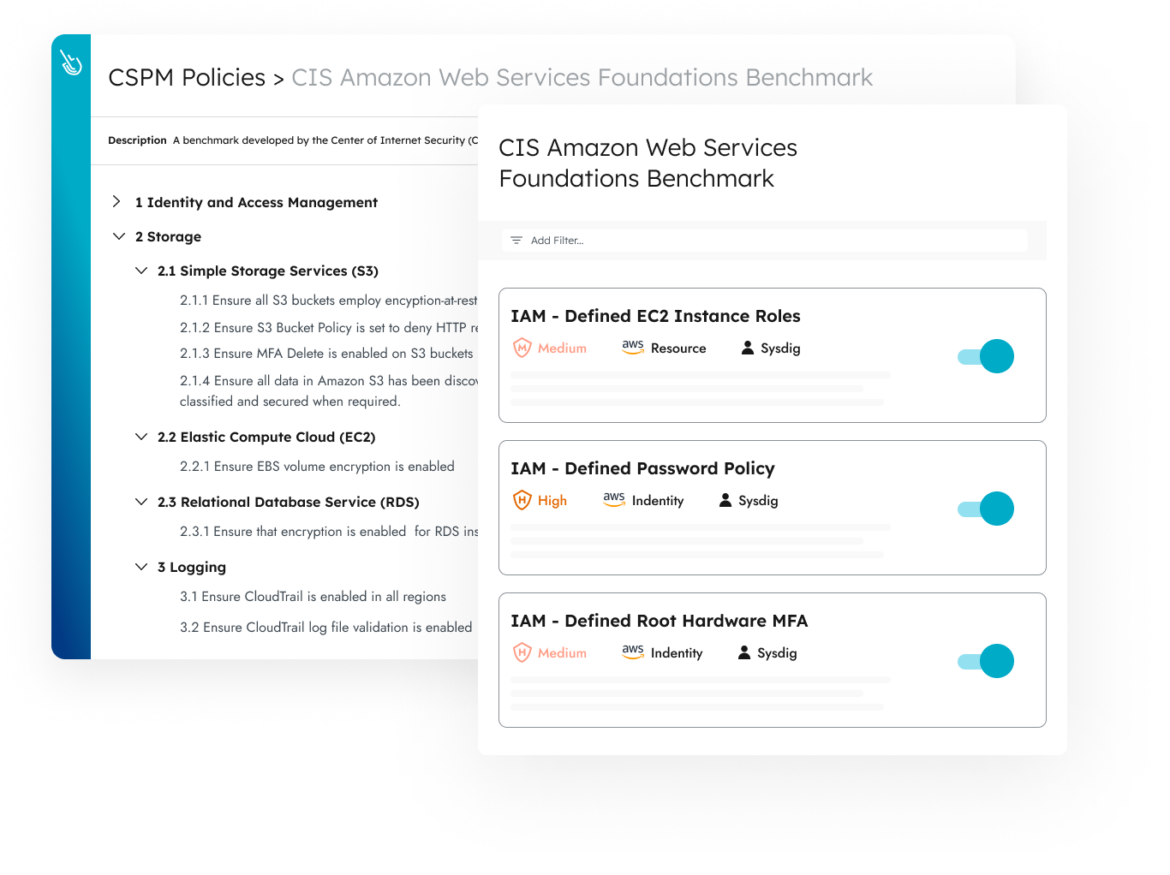
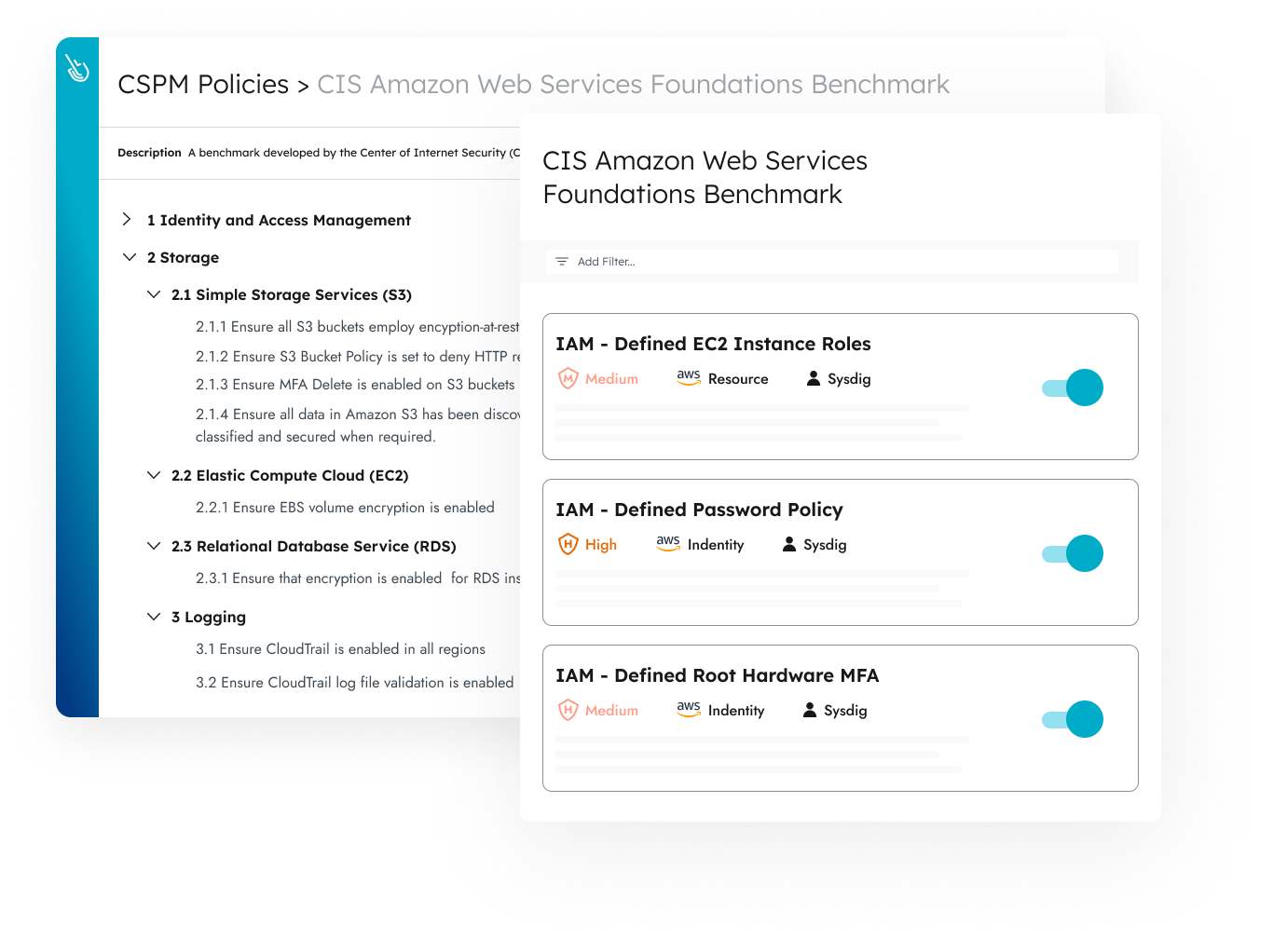
Out-of-the-Box Controls
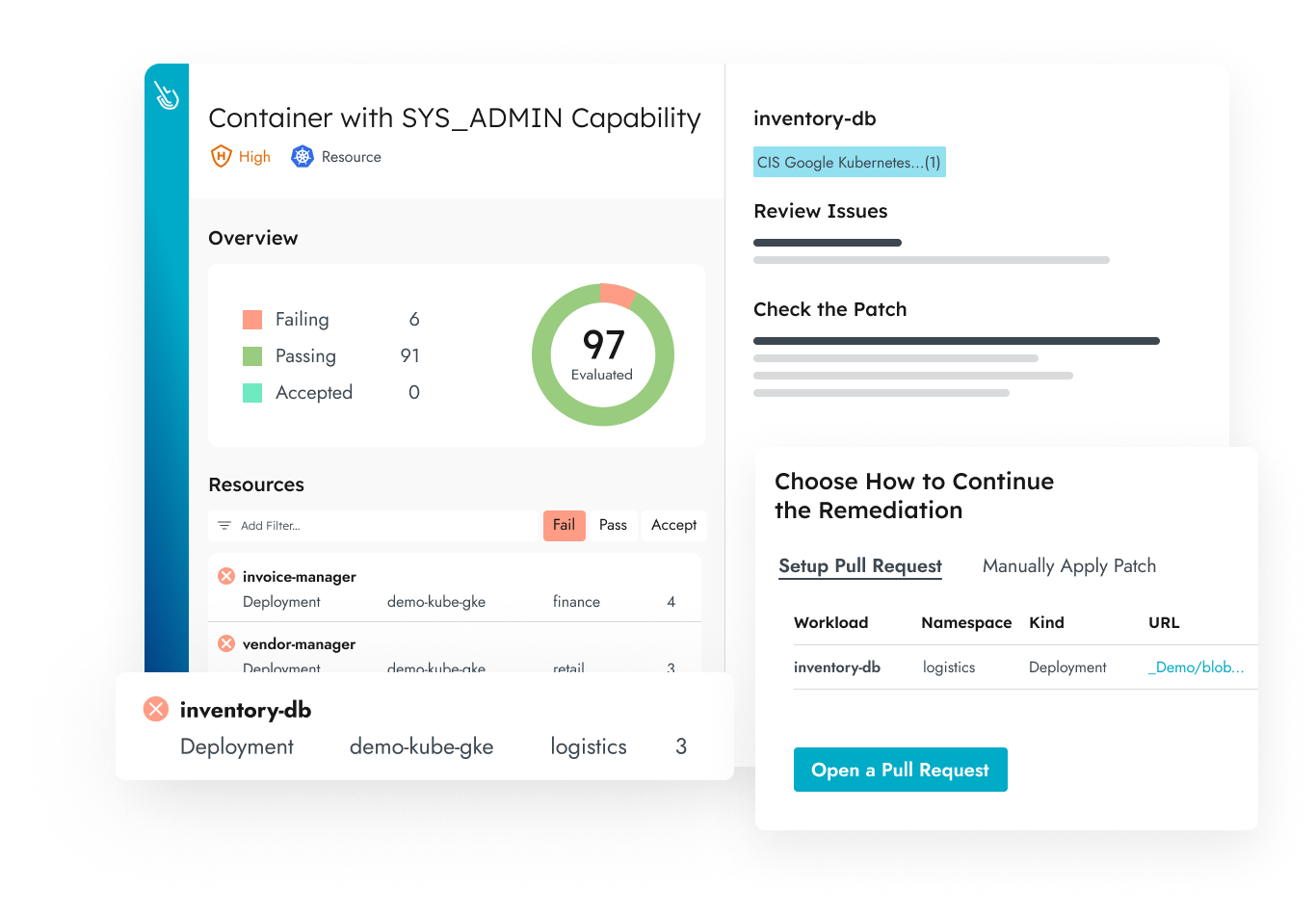
Use out-of-the-box compliance controls to verify cloud and container compliance. With almost a thousand controls and guided remediation, teams can start working from day one.
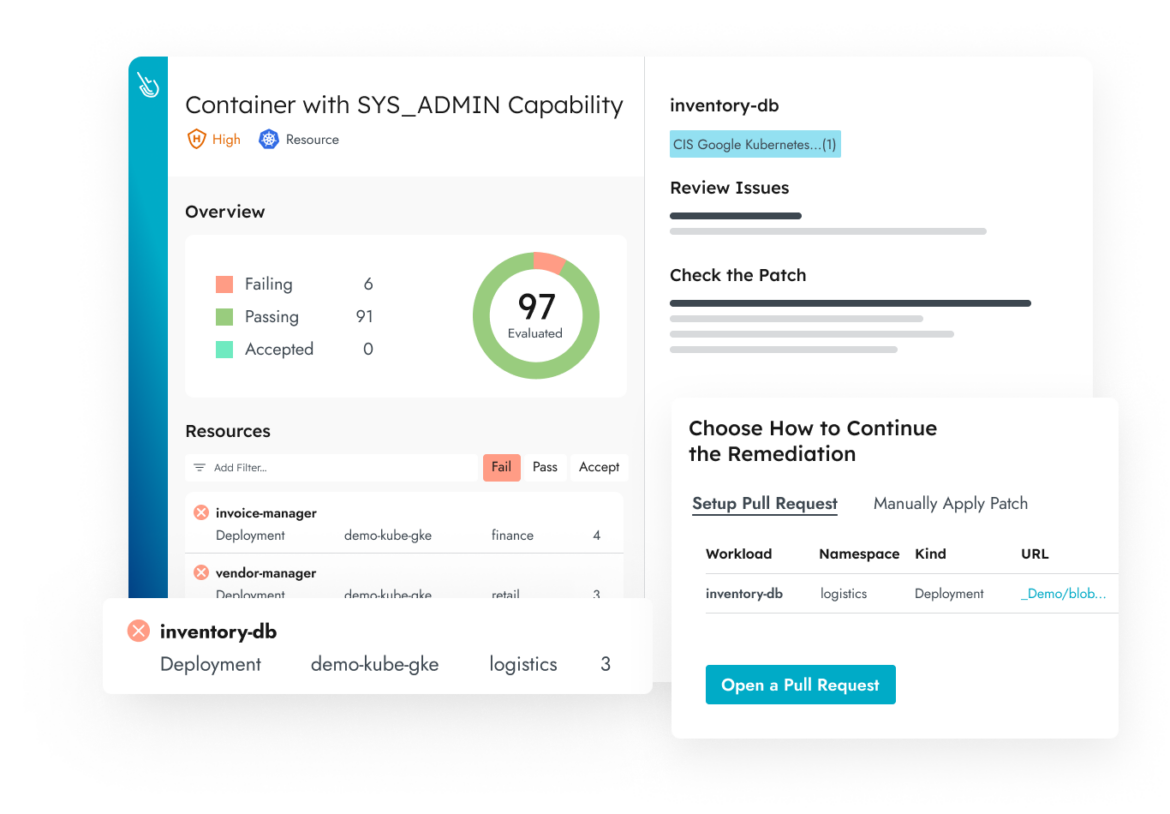
Automated Remediation
Map misconfigurations in production to infrastructure as code (IaC) manifests. Fix violations simply opening a pull request to the source file using Sysdig’s Git integration.
Take the Next Step!
See how you can secure every second in the cloud.