
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Containers are a key building block for cloud workloads, offering flexibility, scalability, and speed for deploying applications. But as organizations adopt more and more containers, they encounter a new set of security challenges. Developer, DevOps, platform, and security teams often find themselves struggling to keep up with vulnerabilities, misconfigurations, and threats. This is where runtime insights come in, offering key visibility and intelligence to help detect real risk and cut through noise.
Let's explore what runtime insights are, how it's used from development through production, and why this approach is essential for secure operations.
Staying ahead of container security threats
Container security threats come in many forms. In a dynamic environment orchestrated by Kubernetes and serverless platforms like AWS Fargate with potentially thousands of containers spinning up and down – often within seconds – applying traditional security approaches is typically both frustrating and futile.
Relying solely on pre‑delivery container image vulnerability scanning is not enough. What's needed is a lens into what's actually happening in deployments. Runtime insights provide the container visibility and context needed to provide actionable information that helps not only to detect active threats in your containers but to also prioritize the most impactful risks and problems based on the knowledge of what is running right now.
How runtime insights work
Runtime insights for containers are derived by continuously monitoring containerized workloads in real time. This continuous visibility means security teams can detect unusual behavior as it happens, providing an added layer of security that is attuned to the fast-paced, ephemeral nature of containerized applications.
To get the insights needed to understand critical aspects of containers in production, runtime instrumentation designed for container inspection is essential. Containerized workloads interact with the kernel and with other applications through system calls. Visibility into these system calls at the host-level through technologies like eBPF allows for real-time detection of security events and profiling of container behavior without requiring any modification to your container images.
Use cases and benefits of runtime insights for container security
Runtime insights are a key component of the Sysdig cloud security platform. It enables security teams to effectively identify and prioritize the most important and relevant risks in their environment across several different domains.
Real-time threat detection
Runtime insights improve threat detection for containers by analyzing live behavior instead of relying on periodic snapshot analysis. Because containers can have such short lifespans and are ephemeral, runtime security that captures what is happening while a container runs is critical to identifying the exploits of malicious actors. Runtime insights make it possible to identify active risk and spot anomalies and attack patterns such as unusual network connections and unauthorized data access in real time.
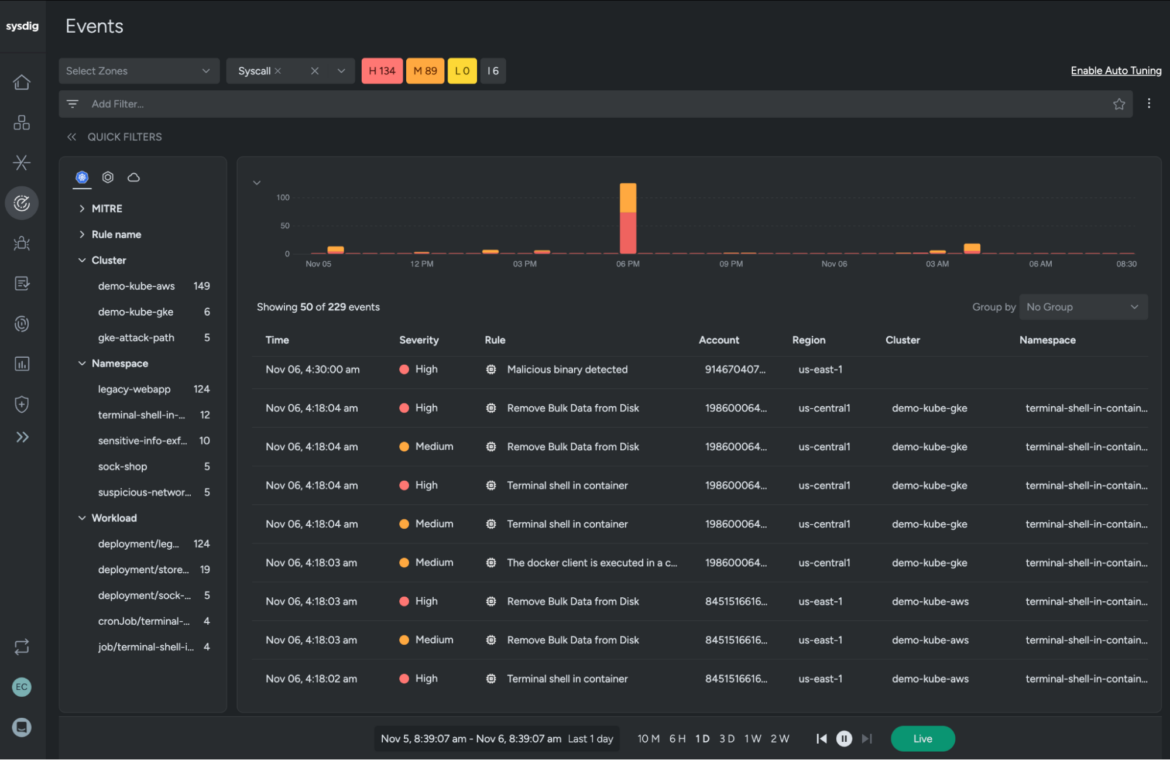
Learn more about real-time cloud-native threat protection with Falco open source.
Container vulnerability management and prioritization
One of the realities of container images is that they often include libraries, packages and other files not required for a given deployment. This creates noise when interpreting vulnerability scan reports resulting in wasted time as developers try to determine what to fix first.
Runtime insights help organizations improve "shift-left" security practices by focusing on container vulnerabilities in packages that are actually in use, rather than spending resources on fixing vulnerable packages that are dormant. This targeted approach delivers a more efficient process for vulnerability remediation by directing attention to high-priority risks.
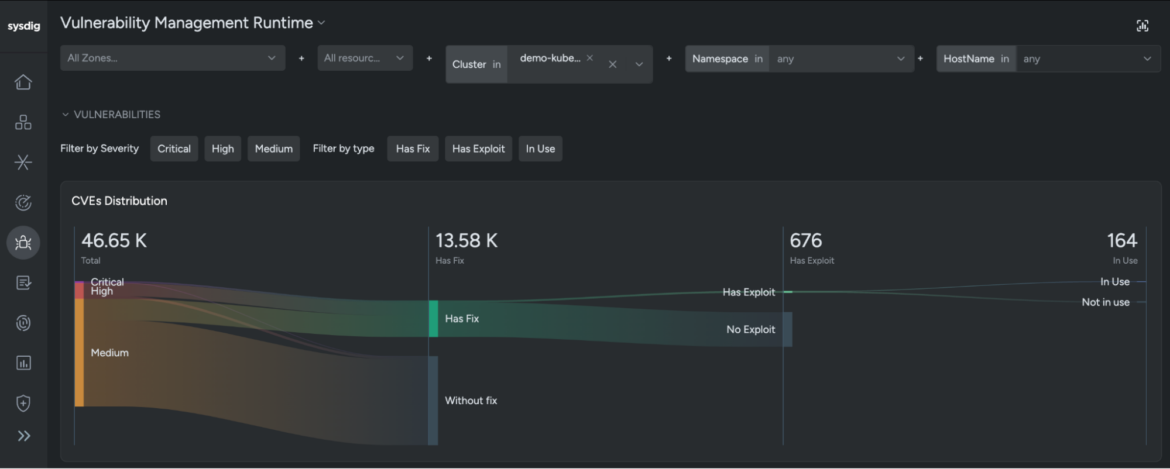
Read more about runtime insight integration with leading AppSec tools: Checkmarx, Docker Scout, Mend.io, ServiceNow, and Snyk.
Container Incident Response
When a threat is detected, runtime insights provide the context needed for quick, informed responses. Knowing exactly what happened in real time—who accessed what, when, and from where—enables security teams to respond effectively. This reduces incident response times and limits potential damage.
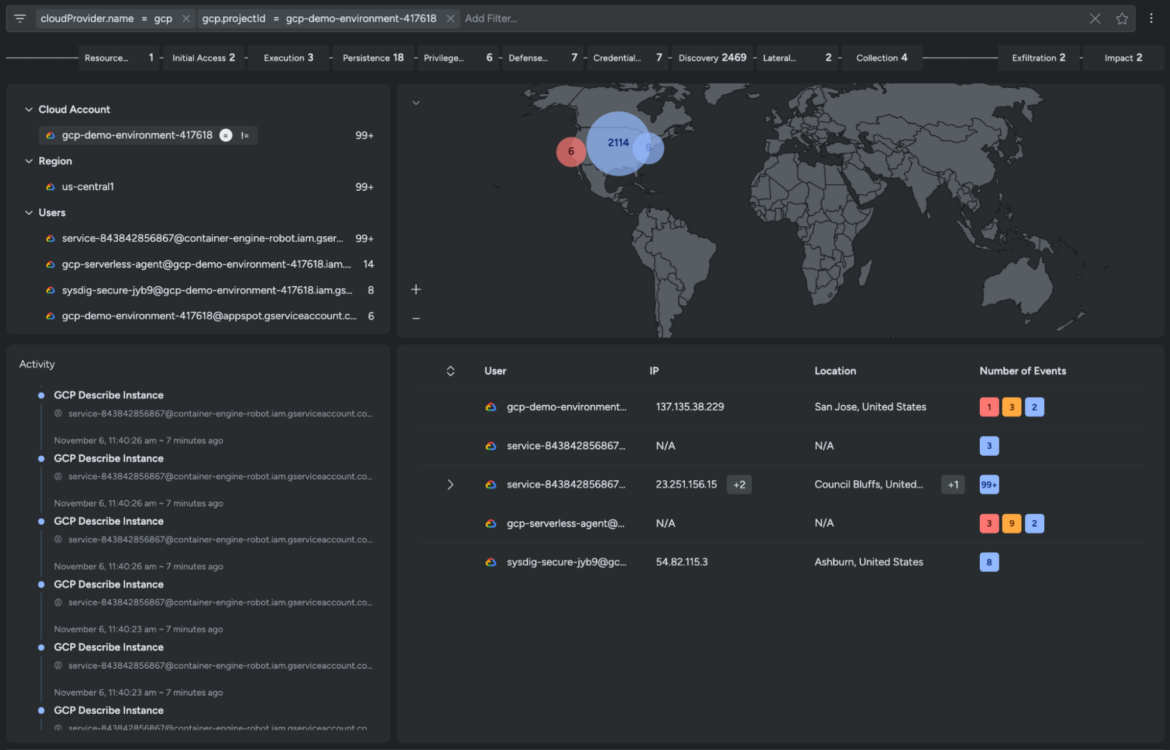
Learn about the 555 benchmark for cloud detection and response.
Container compliance
Many regulatory standards require continuous monitoring of workloads. In the EU, for instance, the Digital Operational Resilience Act (DORA) and the Network and Information Systems Directive (NIS2) establish regulations and objectives to raise the level of cybersecurity and require aggressive time to disclosure of security events in industries including financial services.
Runtime insights help achieve compliance by constantly assessing container security posture, delivering automated alerts, and capturing audit trails that simplify meeting standards to help organizations meet continuous alignment with regulatory requirements.
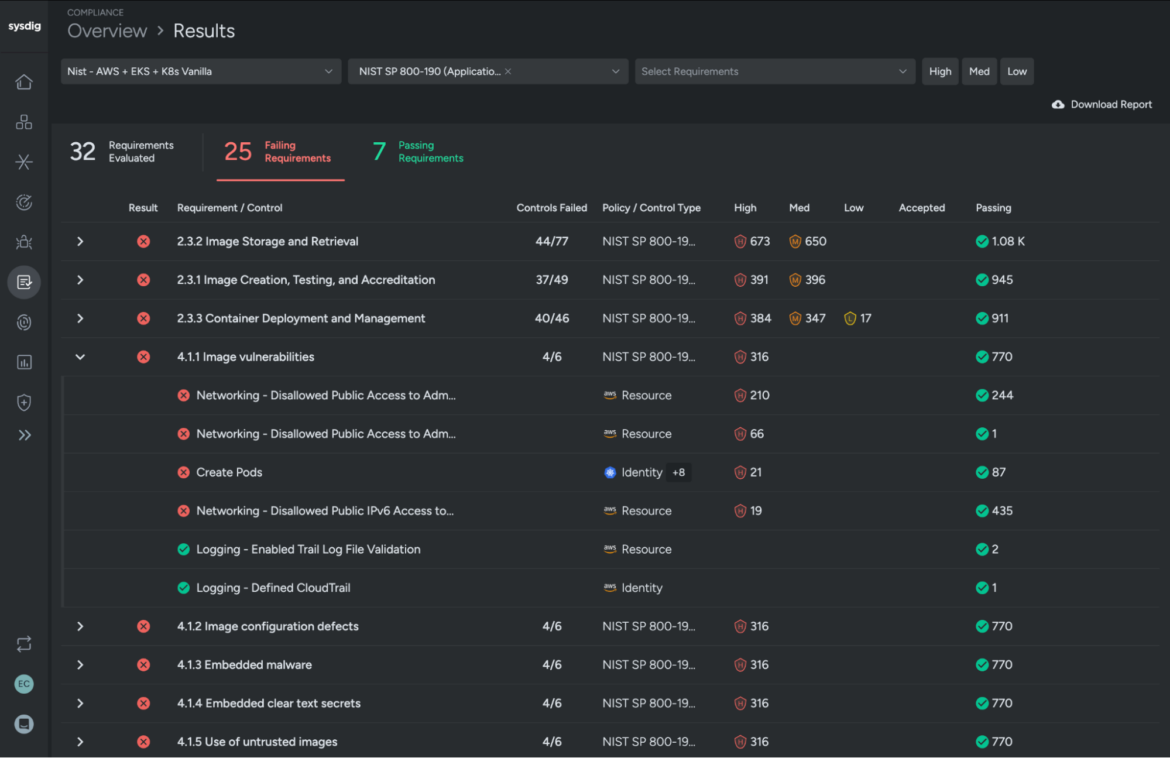
Get the scoop on container security best practices.
Conclusion
Runtime insights provide a unique, powerful approach to improving security practices for containerized applications. Security in containerized environments is a shared responsibility across teams. By integrating runtime insights with DevSecOps practices, development, operations, platform and security teams can better collaborate to improve response to emerging threats.
By leveraging live data and behavioral analysis, runtime insights fill the gaps left by traditional, static security approaches. This helps organizations adapt to the unique needs of containers, removing security as a bottleneck to cloud-native innovation.



