As cyber threats continue to evolve, the European Union (EU) has introduced two pivotal regulations to enhance cybersecurity: the Digital Operational Resilience Act (DORA) and the Network and Information Security Directive (NIS2), which revises and replaces NIS. These frameworks establish comprehensive standards for compliance, risk management, and incident reporting, aiming to bolster the cybersecurity posture of modern organizations across Europe.
Navigating these regulations can be complex, but Sysdig simplifies the process. As the first Cloud-Native Application Protection Platform (CNAPP) to offer out-of-the-box compliance policies for DORA and NIS2, we assist businesses in aligning with these requirements while enhancing their security measures.
The impact of DORA & NIS2
Previously, cybersecurity compliance audits were conducted periodically — monthly, quarterly, or annually. However, the dynamic nature of cyber risks necessitates more immediate responses. DORA and NIS2 introduce updated reporting requirements to ensure timely action:
- DORA, effective January 17, 2025, mandates that financial entities report major incidents within four hours of classification.
- NIS2, effective October 17, 2024, requires breaches to be reported within 24 hours.
Digital Operational Resilience Act (DORA)
DORA standardizes digital resilience practices across the financial sector, ensuring organizations can withstand, respond to, and recover from Information and Communication Technology (ICT)-related disruptions. It applies to a broad spectrum of financial entities, including:
- Banks and credit institutions
- Investment firms
- Insurance companies
- Asset managers
- Payment service providers
- Crypto-asset service providers
Significantly, DORA extends regulatory oversight to third-party ICT providers, such as cloud services, granting financial regulators the authority to supervise and audit these vendors. The regulation also emphasizes the importance of multi-cloud strategies to enhance resilience, necessitating consistent security controls to manage risks across diverse cloud environments.
Network and Information Systems Directive (NIS2)
NIS2 expands cybersecurity requirements to a wider array of critical sectors beyond the financial industry, including:
- Energy and water supply
- Transportation
- Healthcare
- Digital infrastructure
- Space
- Public administration
The directive introduces stricter security requirements and enhances accountability for organizations within these sectors. Notably, NIS2 mandates that member states impose administrative fines for non-compliance, with penalties reaching up to €10 million or 2% of the organization’s total worldwide annual turnover of the preceding financial year, whichever is higher. This underscores the critical importance of adhering to these enhanced cybersecurity standards.
Sysdig’s role in supporting DORA and NIS2 compliance
Understanding the specifics of these frameworks can be challenging. A practical approach is to break down the complex requirements into fundamental building blocks — which is exactly what we’ll do in the next section.
How Sysdig supports DORA compliance
Sysdig helps organizations comply with DORA by providing comprehensive security controls across:
- Linux environments
- Kubernetes clusters
- Cloud infrastructure
- Identity management
Both DORA and NIS2 introduce technical security requirements for cloud environments.
In the following section, we’ll outline these requirements and demonstrate how Sysdig’s security controls ensure cloud assets remain compliant with DORA standards.
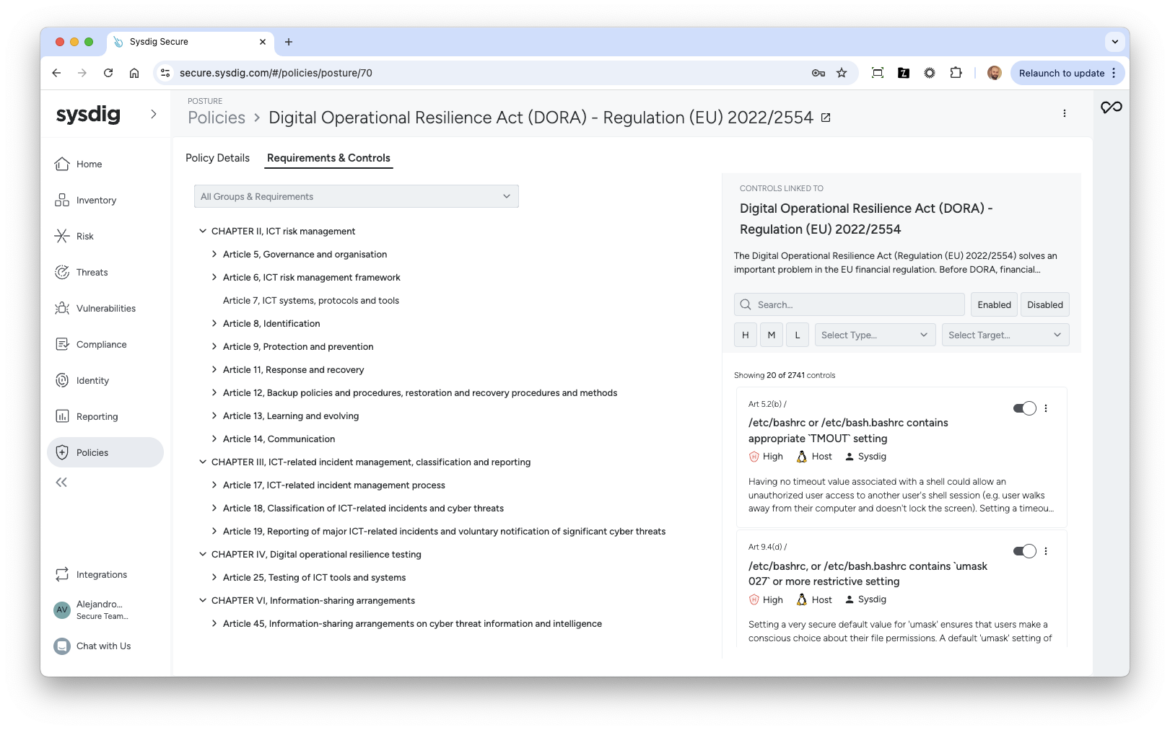
These are just some examples of the technical requirements of DORA. Our comprehensive policy extends beyond these examples.
| CHAPTER II, ICT risk management Article 5, Governance and organization Financial entities shall have in place an internal governance and control framework that ensures an effective and prudent management of ICT risk, in accordance with Article 6(4), in order to achieve a high level of digital operational resilience. | Sysdig provides around 300 controls to ensure availability, authenticity, integrity, and confidentiality of data under this article. Here are some examples: API Server: – Defined tls-cert-file and tls-private-key-file IAM: – Appropriate Service Accounts Access Key Rotation Storage: – S3 – Blocked Public Access (Account-wise) Networking: – Disabled Endpoint Public Access in Existing Clusters Linux Security: – /etc/bashrc, or /etc/bash.bashrc contains appropriate `TMOUT` setting |
| CHAPTER II, ICT risk management Article 6, ICT risk management framework, Art 6.2 The ICT risk management framework must encompass comprehensive strategies, policies, procedures, and tools designed to safeguard all information and ICT assets. This includes software, hardware, servers, physical components, and more. | Sysdig supports these requirements through 190 controls and a multi-layered security approach that includes: Identity security: – IAM – No Multiple Access Keys Workload protection: – Workload mounting ServiceAccount Token |
| CHAPTER II, ICT risk management Article 7, ICT systems, protocols, and tools This section of DORA is all about utilizing and keeping up-to-date ICT systems, protocols, and tools that are scalable, reliable, resilient, and high-performance. | Sysdig aids financial entities in meeting these requirements by providing: Workload security: – Container running as privileged Kubernetes: – Kubelet – Defined streaming-connection-idle-timeout – Kubelet – Disabled hostname-override – Kubelet – Disabled read-only-port – Kubelet – Enabled make-iptables-util-chains – Kubelet – Enabled protect-kernel-defaults Audit Log: – Audit Log Events – file system mounts – Audit Log Events – kernel module loading and unloading |
| CHAPTER II, ICT risk management Article 9, Protection and prevention, Art 9.3 This Article emphasizes that financial entities must employ ICT solutions and processes that ensure data transfer security, minimize risks such as data corruption, unauthorized access, and technical issues, and prevent data availability, authenticity, integrity, confidentiality breaches, and data loss. These measures must also protect data from management-related risks, including administrative errors, processing hazards, and human mistakes. | Sysdig achieves this by means of controls like: API Server: – Defined strong cryptographic ciphers Compute: – Disabled connection to serial ports Firewall Configuration: – IPv4 – firewall rules – Networking – disallowed default network |
How Sysdig supports NIS2 compliance
While NIS2 shares many similarities with DORA, its scope is broader, covering all critical infrastructure sectors. This includes not only healthcare, utilities, and telecom providers but also digital service providers. Entities are classified as either essential or important, with varying levels of security controls, monitoring requirements, and attestation obligations.
Sysdig supports compliance with all 14 technical requirements of NIS2, implementing 2,905 security controls to help organizations meet these standards.
Most of these technical requirements fall under Article 21, titled “Cybersecurity Risk-Management Measures”, within Chapter IV: Cybersecurity Risk-Management and Reporting Obligations. Below, we’ll explore key technical requirements in more detail.
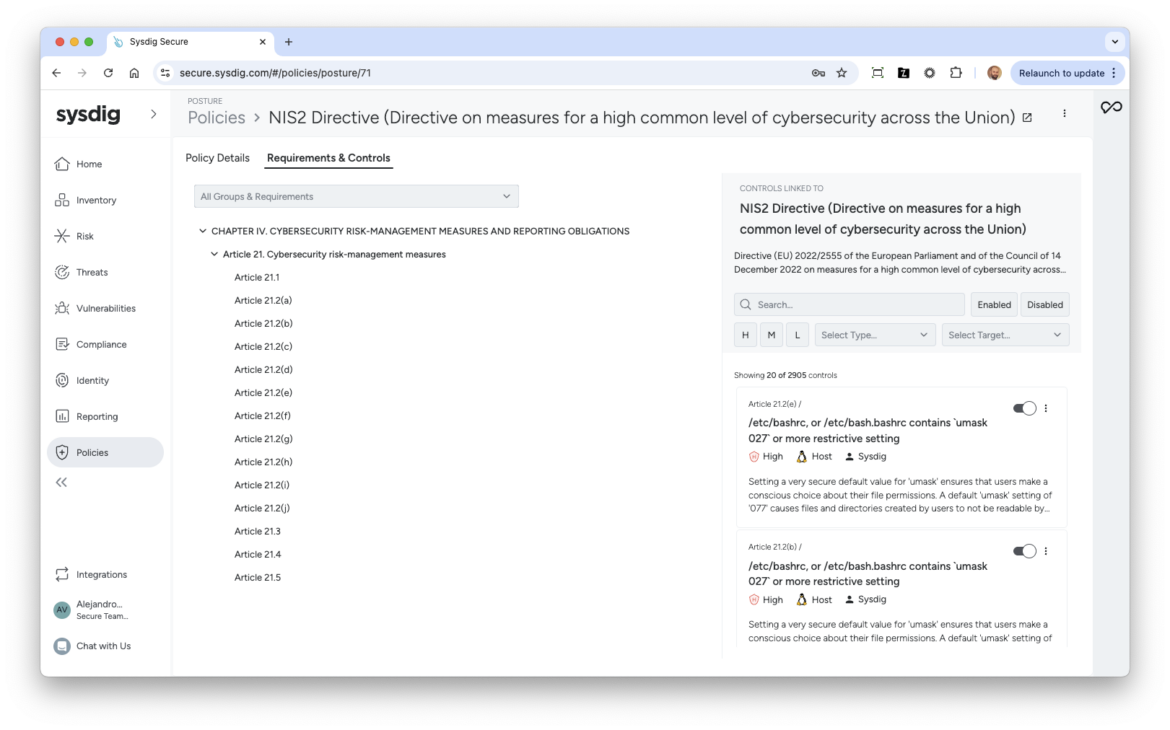
These are just some examples of the technical requirements of NIS2. Our comprehensive policy extends beyond these examples.
| Article 21, Cybersecurity risk-management measures NIS2 requires entities to adopt suitable measures across technical, operational, and organizational domains to manage security risks for their network and information systems, aiming to reduce the impact of incidents. These measures should align with the latest standards and be cost-effective, reflecting the entity’s risk exposure, size, and potential incident impacts. | Sysdig addresses this through over 200 controls. Here are some examples: – Compute – Installed latest OS patches – Container permitting root – Logging – Enabled Cluster Logging AKS/EKS – SQL Server – Enabled periodic recurring scans – SSH Server Configuration Permissions – public host key files |
| Article 21.2(d) The key focus is on securing the supply chain, which involves addressing security aspects in the relationships between entities and their direct suppliers or service providers. | Sysdig can facilitate compliance with this requirement through over 200 controls, and here are some examples: Secure SDLC: – Registry – Enabled Vulnerability Scanning – Registry – Read-only access Logging: – Logging – Enabled cclusterl logging Access control: – Over-permissive access to resource types in group Secret: – Secrets Management |
Conclusion
The NIS2 directive and DORA regulations represent key advancements in the European Union’s efforts to enhance cybersecurity and operational resilience across many critical sectors, with particular prioritization of the financial industry. Now in effect, these frameworks require organizations to implement comprehensive security measures to safeguard their networks and information systems against evolving cyber threats.
Sysdig is uniquely positioned to support organizations in meeting these requirements not just as a security tool to check the box, but as a strategic partner. With Sysdig, businesses can confidently streamline compliance, strengthen security, and adapt to the ever-evolving regulatory landscape.



