
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Cloud security teams are often faced with an onslaught of noise from their detection tooling, making it nearly impossible to distinguish truly malicious threats from benign behaviors. Many threats will go uninvestigated simply because there aren’t enough analysts for the sheer amount of alerts, leaving organizations exposed to potential breaches.
Stepping back and evaluating the situation, we can confidently say ignoring this problem isn’t just an operational inefficiency — it’s a risk multiplier. Security teams need a way to rapidly detect, contextualize, and respond to threats.
Enter Sysdig Threat Management, designed to give analysts a much-needed break from alert fatigue and untangle cloud complexities shadowing modern cloud environments. Removing these barriers, Sysdig Threat Management helps security teams focus on what matters most, accelerating response times and bolstering defense strategies in cloud-native environments to reduce risk.
Challenges facing cloud security teams: Alert fatigue and complexity
It’s generally understood that modern cloud-native infrastructure — from Kubernetes clusters to containerized workloads — has revolutionized application development and deployment, enabling rapidly scaling organizational innovation. But the benefits of speed and agility come with a cost: Attackers are gaining the same advantages in speed and scale, all in a vastly expanded and complex attack surface.
Critical challenges from complex and broad attack surfaces include:
- Alert fatigue: Detection tools can generate thousands to millions of alerts daily, many of which are low-confidence, redundant, or even benign. Analysts are left scrambling to differentiate and correlate behaviors across harmless anomalies and genuine threats, pulling them away from deeper analysis.
- Fragmented view of threats: Connecting the dots between related malicious activities — such as privilege escalation, lateral movement, and data exfiltration — can be difficult without adequate context and correlation capabilities. Without adequate correlation, individual behaviors of an attack can be viewed as isolated events. These context and correlation deficiencies turn understanding the scope of an attack into a high-stakes guessing game.
- Slow response times: Without clear prioritization, actionable context, or streamlined workflows, response times lag. Meanwhile, attackers exploit this delay and leverage cloud speed to further their impact, leaving security teams playing a burdensome game of catch-up.
The stakes are high. A single missed detection can lead to a devastating breach, as malicious actors need less than 10 minutes on average to execute an attack. These attacks can expose sensitive data, erode customer trust, and disrupt business operations. Security teams need capabilities to not only simplify threat detection and correlation, but also enhance their ability to respond effectively.
How Sysdig Threat Management cuts through the noise
Sysdig Threat Management takes a unique approach to addressing these challenges. By correlating related detection events into a single, actionable threat, the Sysdig Secure platform provides clarity in the chaos. Instead of bombarding teams with disconnected alerts, Sysdig Threat Management offers a streamlined, contextualized view of malicious activity.

How Sysdig Threat Management delivers value on day one
Context-driven correlation
Sysdig Threat Management doesn’t just group events — it intelligently correlates events based on shared context. Whether it’s a Kubernetes workload, cloud identity, or attack phase, related events are consolidated into a single threat. Take these examples:
- An unauthorized API call that escalates privileges
- Lateral movement within a Kubernetes cluster
- Outbound traffic to a known malicious IP
Instead of handling these as separate incidents, Sysdig Threat Management descriptively labels the activity under a unified threat; e.g., “Privilege Escalation and Exfiltration Attempt.” This empowers teams to quickly grasp the attack’s scope and criticality.
Sysdig Sage: Advanced AI-powered insights
At the heart of Sysdig Threat Management is Sysdig SageTM, a generative AI security analyst. Sysdig Sage enriches threats with easy to understand summaries and high-fidelity context, granting teams the situational awareness they need to take definitive action faster. Sysdig Sage enables analysts to quickly identify the most pressing threats to focus their attention on.
Streamlined workflows
With Sysdig, analysts spend 99% less time managing alerts and can focus on resolving them.
Sysdig Threat Management isn’t just about detection — it’s designed to enhance every stage of the response process. With inline management features like status changes, rule tuning, enhanced investigation, and response actions, teams can seamlessly manage their security workflows without switching tools or duplicating efforts.
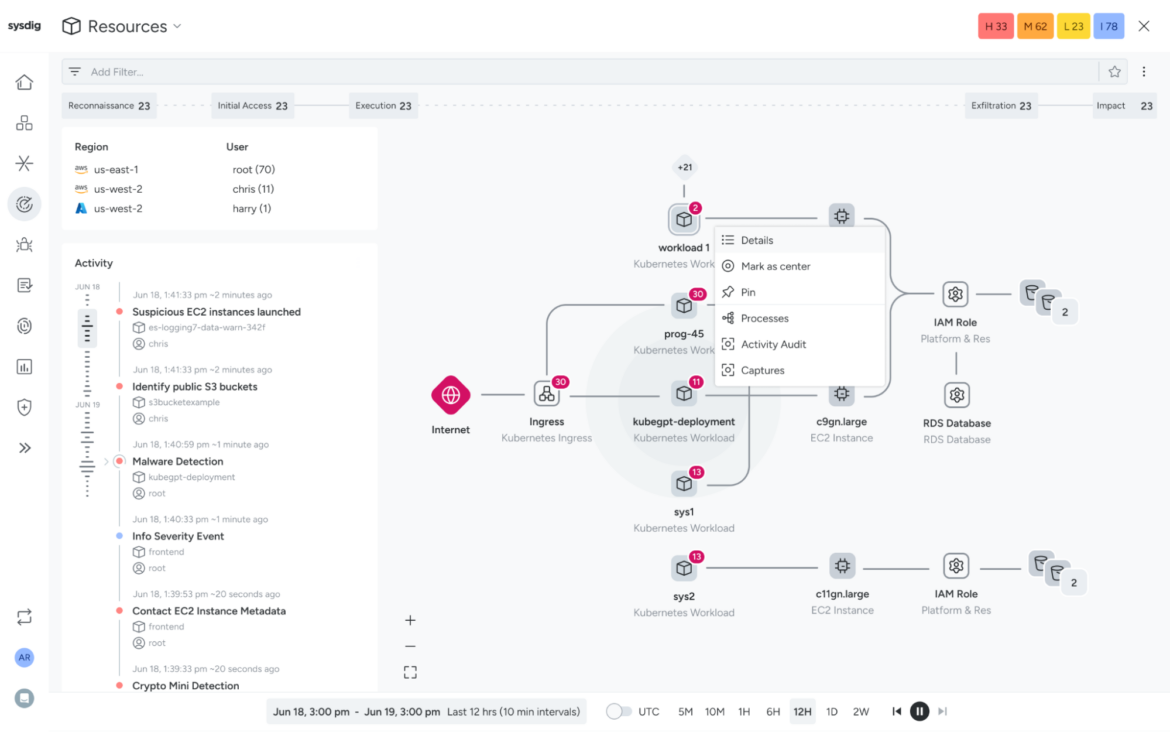
The result? Analysts spend 99% less time managing alerts and can focus on resolving them.
How Sysdig Threat Management works
Sysdig Threat Management brings clarity to even the most complex attack patterns by combining real-time detection with advanced correlation capabilities.
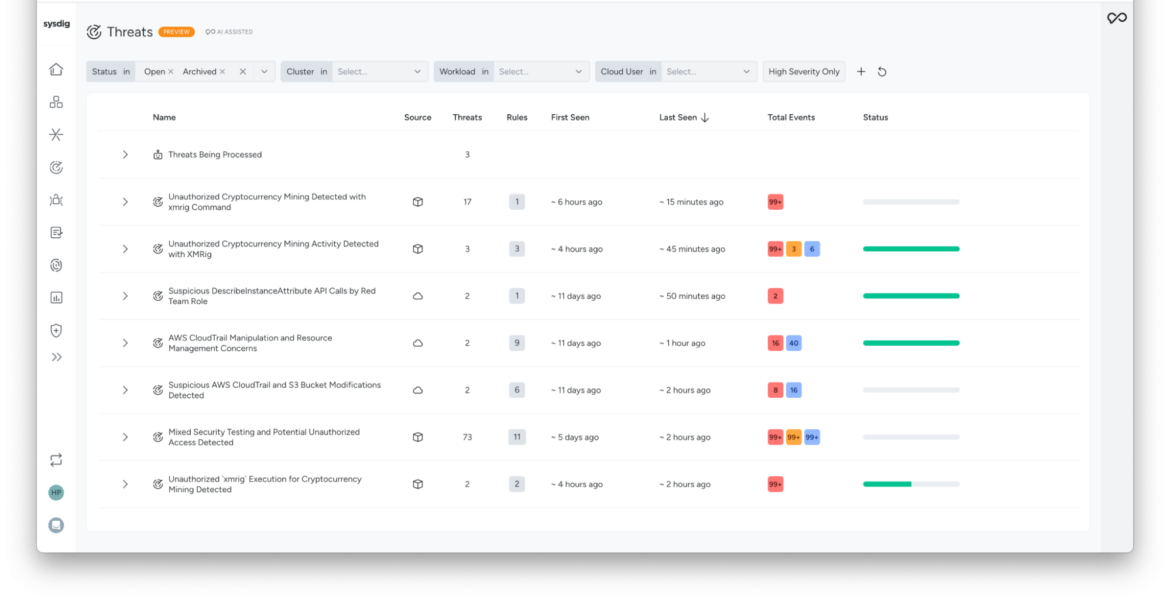
Here’s how it works:
Runtime detection in real time: Malicious events — such as unauthorized API calls or outbound connections to command-and-control servers — are identified as they occur.
Contextual correlation: Events are grouped into a single threat based on shared context. For instance, a compromised workload might involve the following actions:
- Access production workloads – Attackers can manipulate Kubernetes clusters, VMs, or containers.
- Modify or exfiltrate sensitive data – Attackers gain access to S3 buckets, databases, or customer records.
- Escalate privileges across accounts – Attackers move laterally through cloud environments, assuming more powerful roles.
- Deploy persistence mechanisms – Attackers create rogue IAM roles, generate API keys, or spin up backdoor workloads.
Easy to consume summarization: Sysdig Sage analyzes correlated security events, signals, and context to generate threat insights, accelerating analyst response by automatically providing an intuitive summary, a timeline of activity, and a clear narrative of attacks to understand the who, what, where, when, and why
This approach drastically reduces noise and eliminates the guesswork in understanding multi-stage attacks.
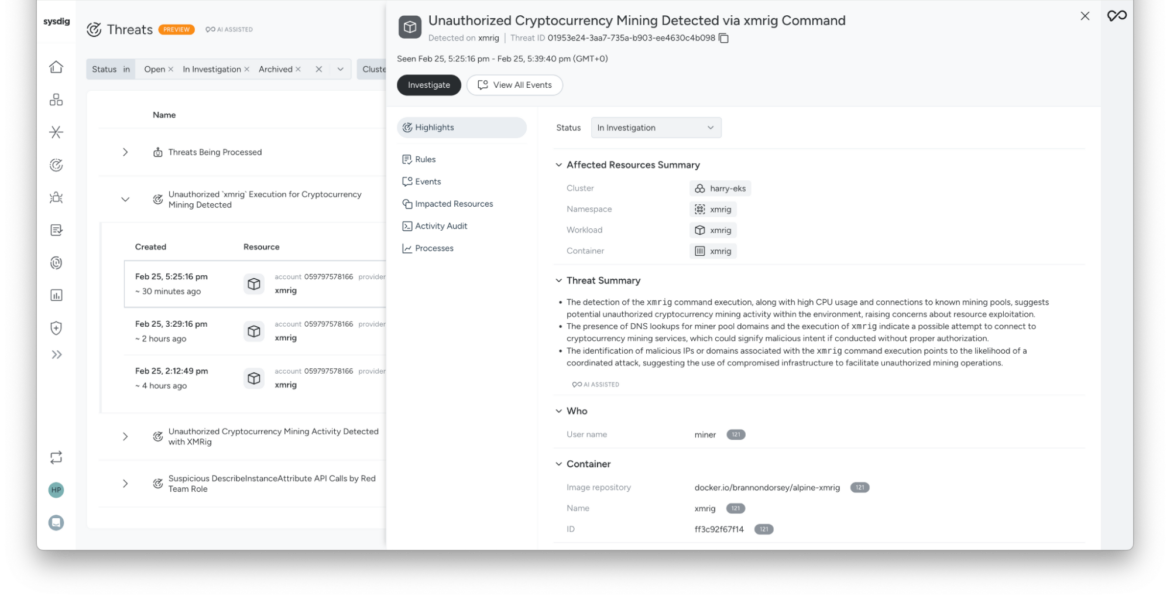
The business impact of Sysdig Threat Management
For security teams, the benefits of Sysdig Threat Management are transformative:
- Noise reduction: By consolidating alerts into actionable threats, the platform reduces the volume of alerts analysts must process by 99%, drastically impacting alert fatigue.
- Improved efficiency: Analysts can focus on critical issues without wading through a sea of low-priority alerts. With streamlined workflows, triage processes become faster and more efficient.
- Faster mean time to respond (MTTR): The single-pane-of-glass interface provided by Sysdig Threat Management, in addition to the enriched context from Sysdig Sage, allows analysts to see a significant decrease in the time it takes to investigate and resolve incidents.
- Proactive security posture: With fewer false positives and clearer insights, teams can dedicate more resources to proactive measures, strengthening overall security.
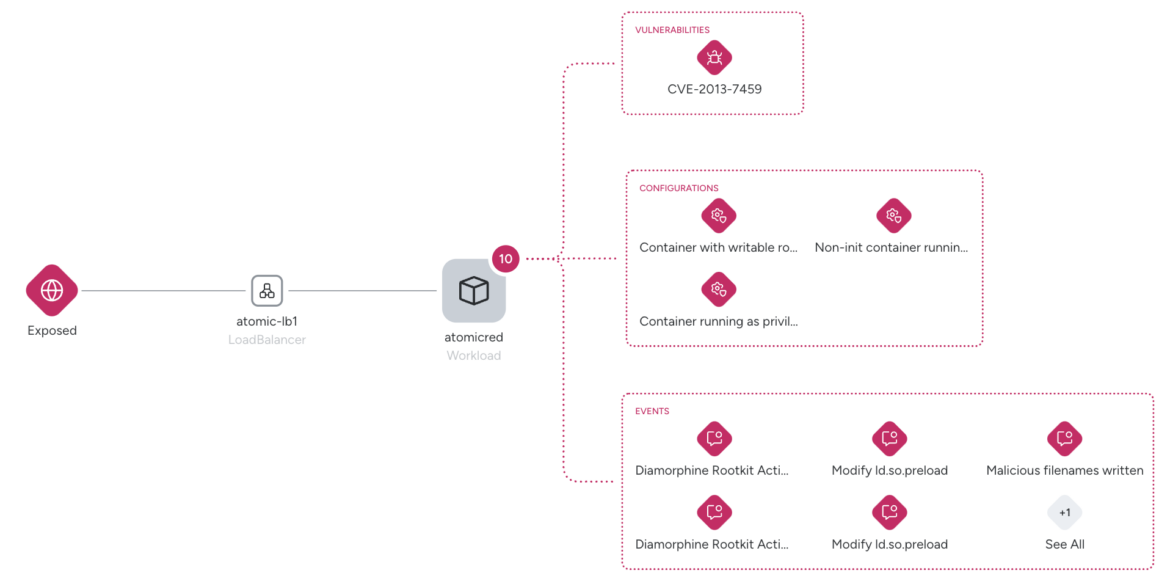
Real-world use case
Consider this scenario: A security team detects unusual outbound traffic from a Kubernetes cluster to a suspicious IP.
Using traditional tools, analysts would face the challenging task of manually investigating and piecing together whether this event is correlated with any of the hundreds to thousands other events scattered across fragmented insights. Would they be able to connect high-risk behaviors such as privilege escalation or lateral movement before the threat has executed?
With Sysdig Threat Management, the entire chain of events is consolidated within a single threat. Analysts are able to immediately understand that this isn’t just an isolated anomaly — it’s a live, multistaged, and coordinated attack. Enriched by Sysdig Sage, the escalated threat includes a timeline and intuitive summary, enabling the team to act decisively and contain the attack.
Conclusion
The modern cloud-native environment demands a modern approach to threat detection and response. Sysdig Threat Management delivers that approach by cutting through the noise, reducing alert fatigue, and enabling faster, more effective responses.
For CISOs and analysts looking to empower their teams and fortify their defenses, Sysdig Threat Management isn’t just a tool — it’s a force multiplier. With its unique combination of Sysdig Sage, contextual correlation, and streamlined workflows, Sysdig Threat Management ensures that your team is not buried in the noise, has complete visibility, and can accelerate meaningful response to outpace even the most advanced threats.
Ready to see how Sysdig can help you go from visibility to action?
👉 Request a demo to see how Sysdig works.


