
Falco Feeds extends the power of Falco by giving open source-focused companies access to expert-written rules that are continuously updated as new threats are discovered.

Among many other features Sysdig Secure version 2.4 introduces a new and improved runtime policy editor, along with a comprehensive library combining out-of-the-box run-time policies from our threat research teams, container-specific compliance standards, Kubernetes security and Falco opensource community rules.This UX overhaul brings three major improvements for every Sysdig Secure user:
- Runtime policies can import any number of security rules and auto-generated image profiles. You can scope the security policy using container, cloud and Kubernetes metadata.
- Tighter Falco integration, directly from the web UI. You will be able to define a new trigger condition or append to the list of forbidden external IPs just clicking on the rule.
- A more structured way to group, classify and lookup rules, following the standard Cloud native procedure: tags and labels.
Let's start taking a quick look at the Rules Library:
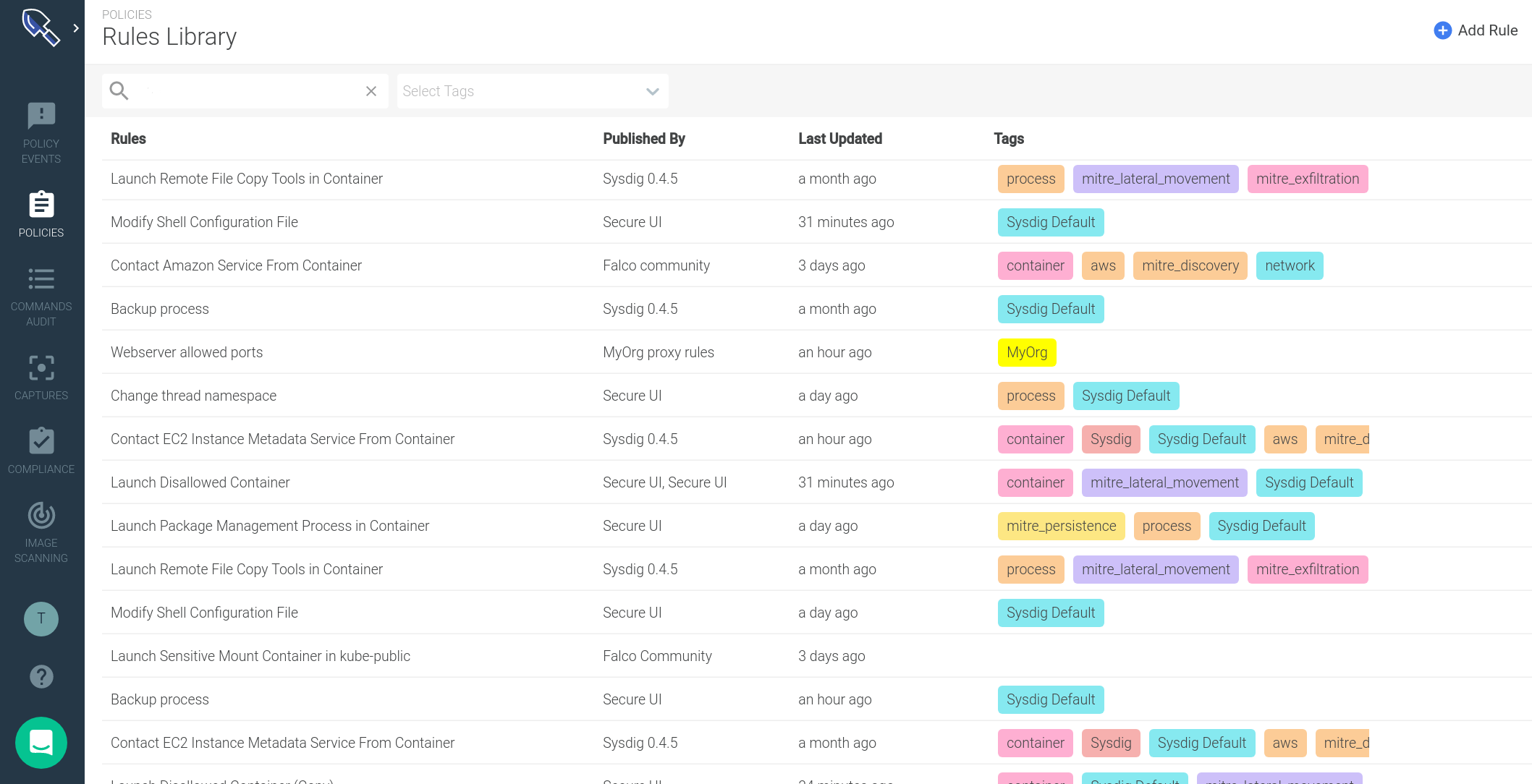
You visualize your runtime rules properties in just a glance:
- **Where this rule comes from **(Published By). The security team can instantly recognize whether a rule came from a specific Sysdig update, from a custom rules file created within the organization or from an external rules source (like the Falco community rules).
- When was the last time it was updated (Last Updated). You can use this information to audit your rules or if you schedule periodic updates, to confirm when last happened.
- Rule tags: An effective method for organizing your rules. You can use these tags to describe the targeted entity (host, k8s, process), the compliance standard it belongs to (MITRE, PCI, CIS Kubernetes) or any other criteria you want to use to annotate your rules.
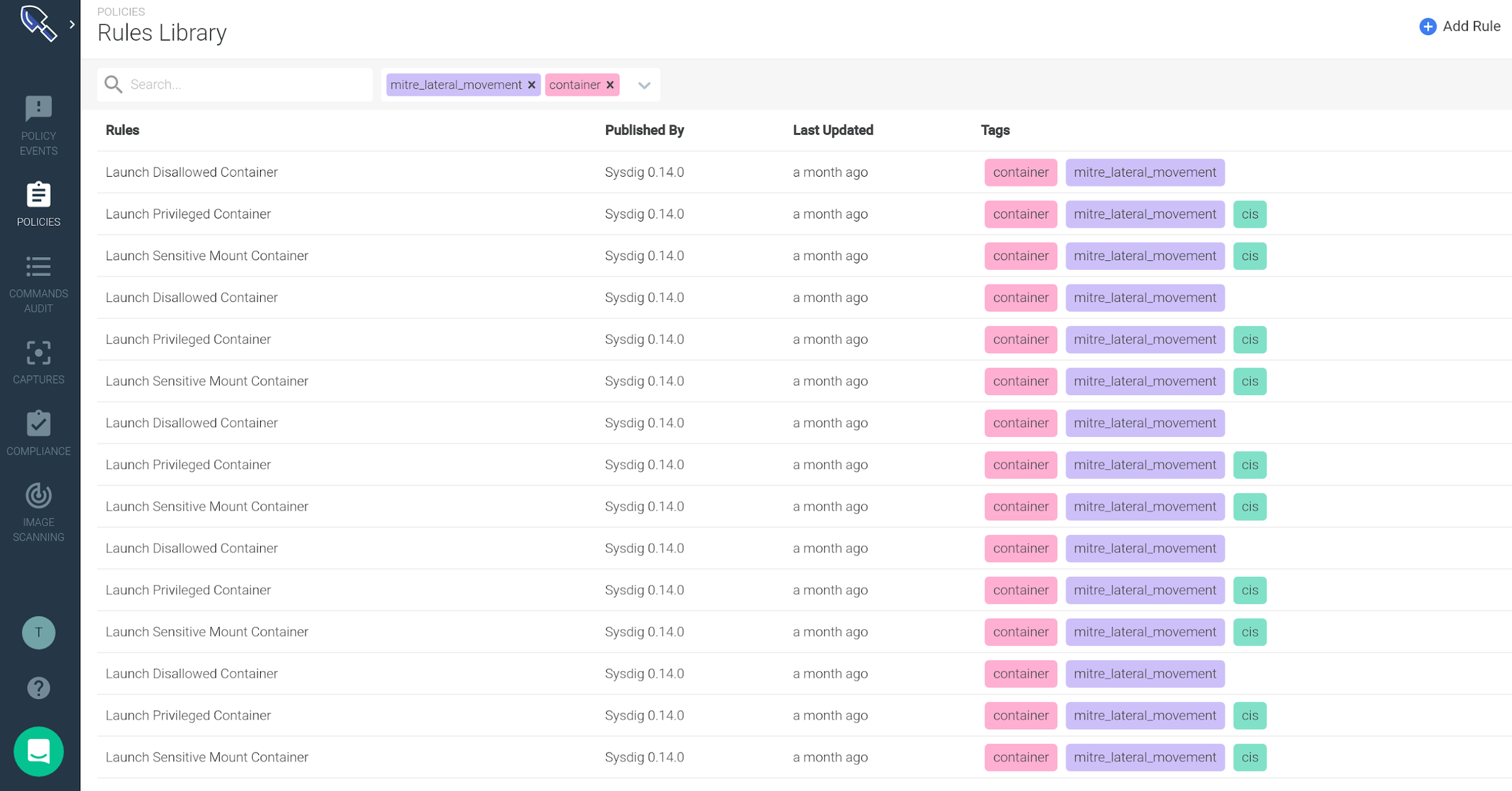
These tags come from the *Tags *attribute of the imported Falco rules, but you can also create or delete them directly from the Secure UI.Using the search panel at the top you can filter by rule name or tags. For example, this is how you get all mitre lateral movement runtime rules associated with containers:
From the library interface itself you can also visualize the rule **syntax and **edit parts of the syntax:
- Falco macro conditions
- List elements
Let me walk you through an example: there is a default runtime security rule that triggers if/when a new privileged container is spawned in your cluster. Suppose that you want to add an exception for a known image that you need to deploy:
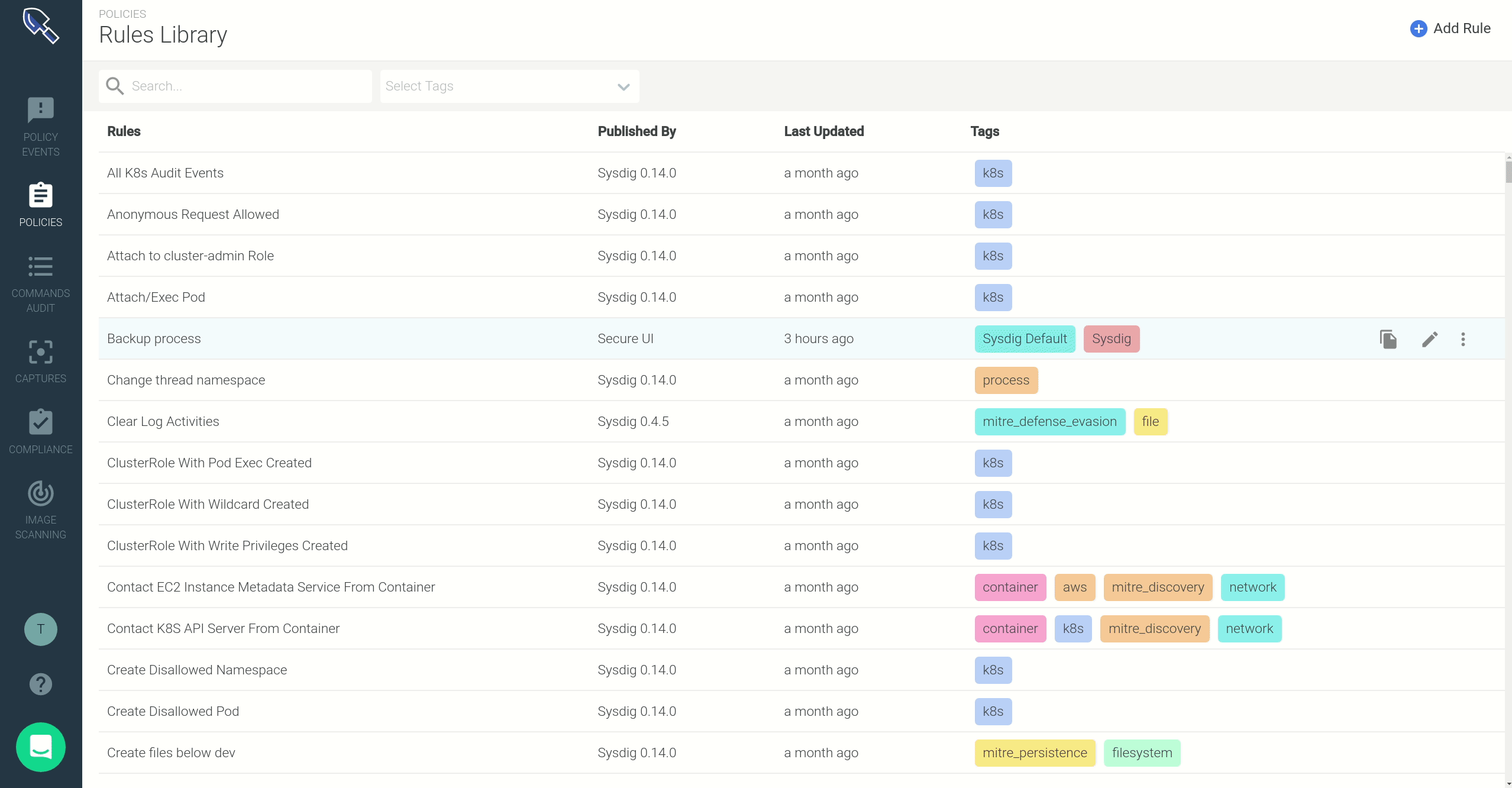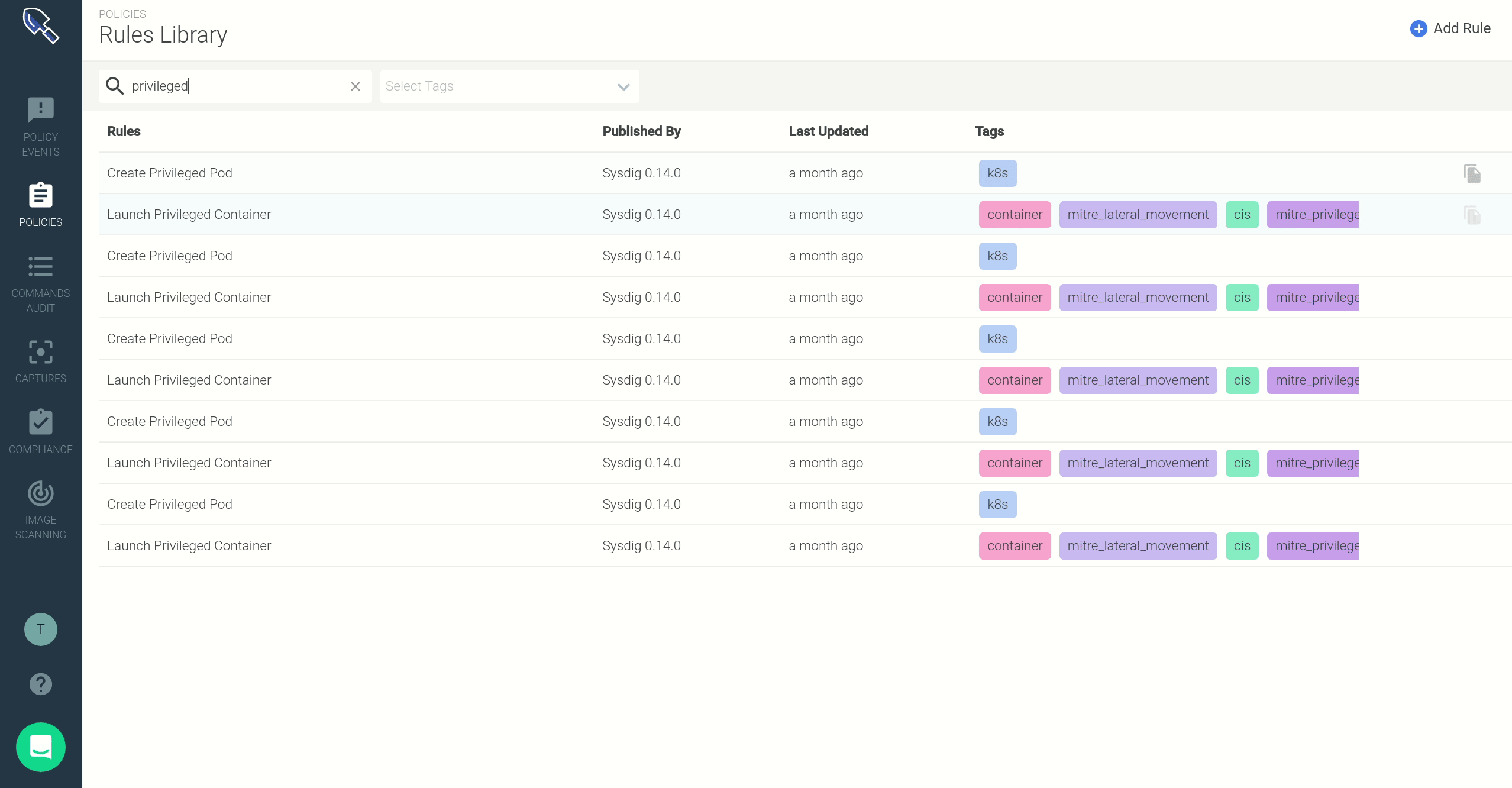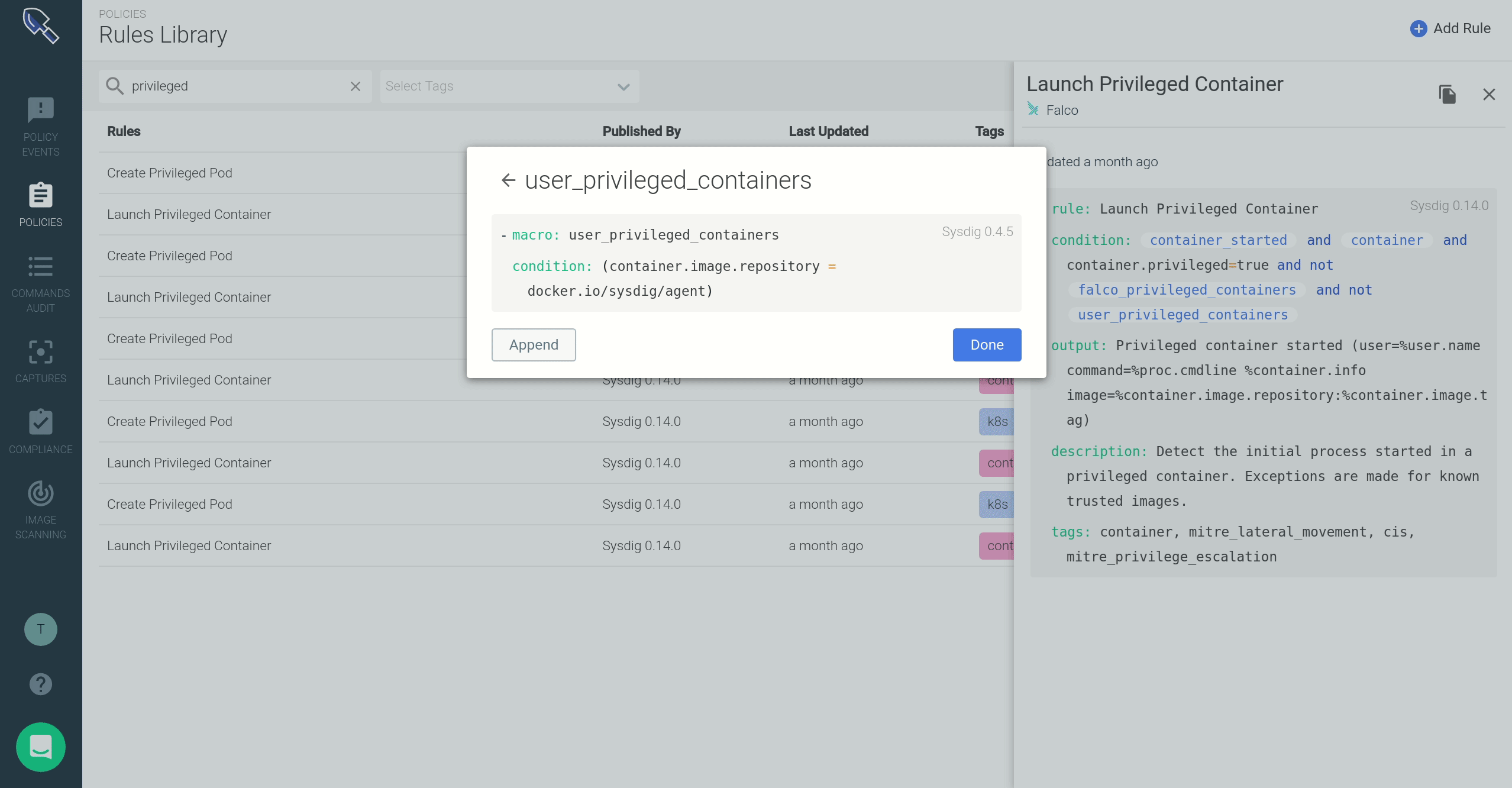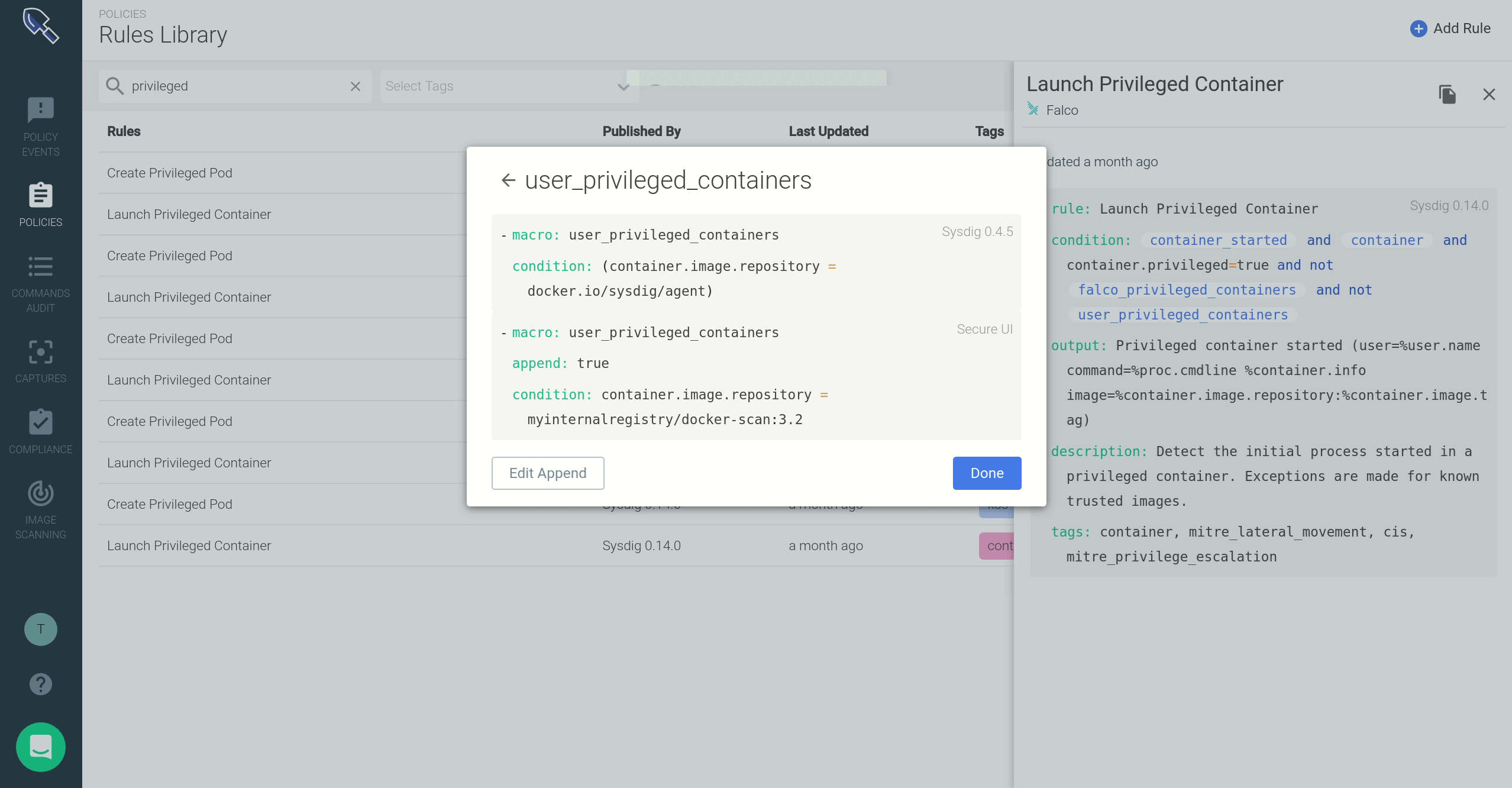
- Click on the rule once to display a side panel containing the Falco rule syntax. This rule uses macros and lists to define desired trigger conditions and exceptions.
- These macros and lists are highlighted, signaling that you can click on them to pop-up an inline editing dialog. Through this form, you can add your container image name to the
user_privileged_containersmacro.
Creating a new runtime security rule
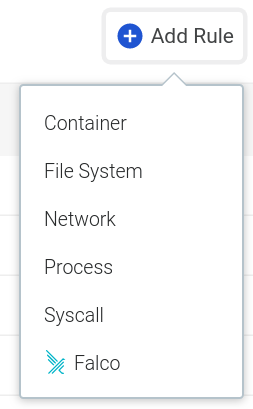
In addition to visualizing and editing existing rules, you can, of course, create new runtime security rules.If your rule needs to whitelist or blacklist a set of:
- Container images
- File system operations (read/write directories, read directories)
- TCP/UDP ports, or inbound / outbound network connections
- Spawned processes
- System calls
You have a quick form that you can access directly from the Add Rule button:
Alternatively, when you need a runtime rule which requires a more advanced set of conditions and logical operators, you can leverage the full-fledged Falco rule syntax, directly from the UI:
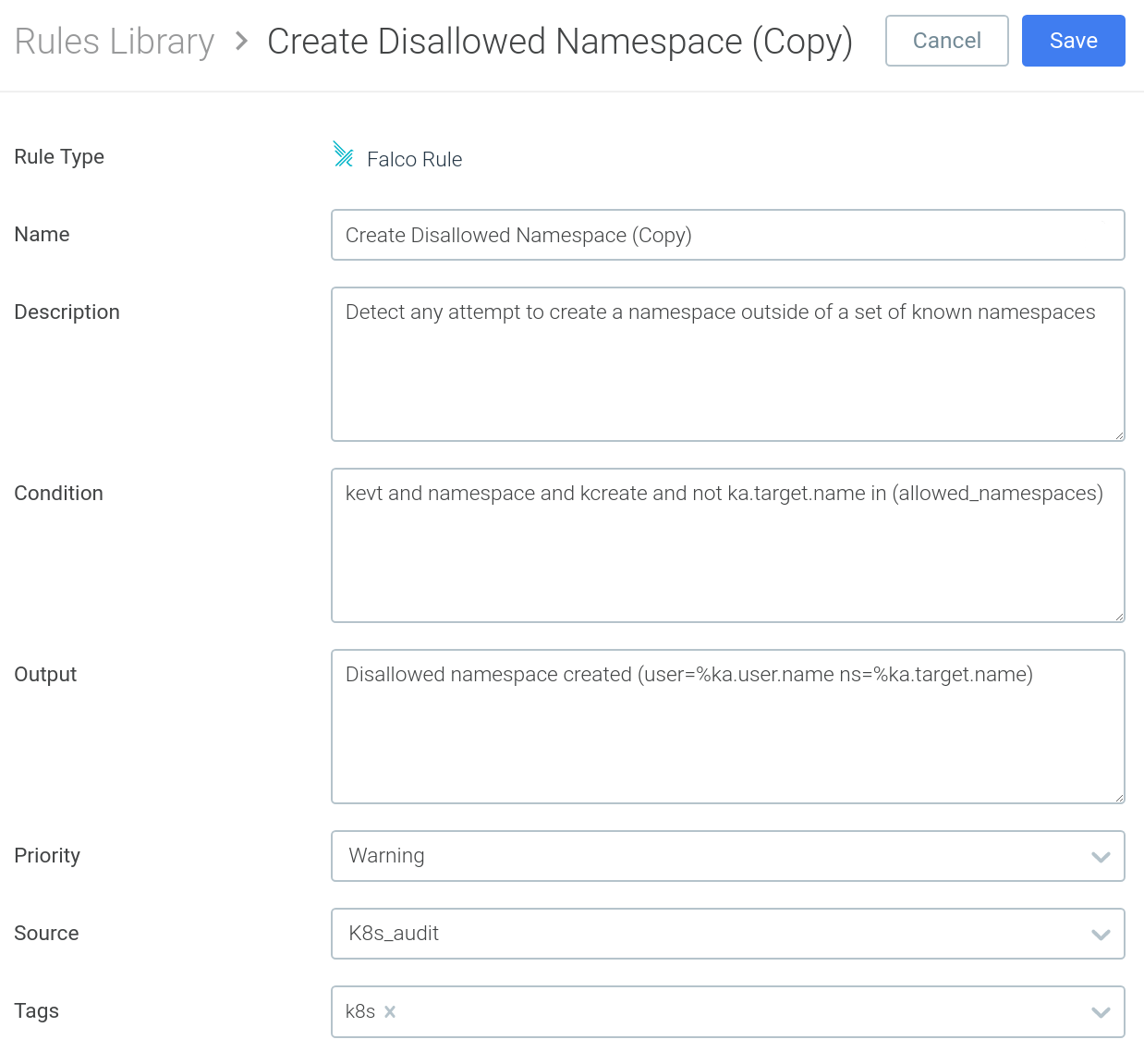
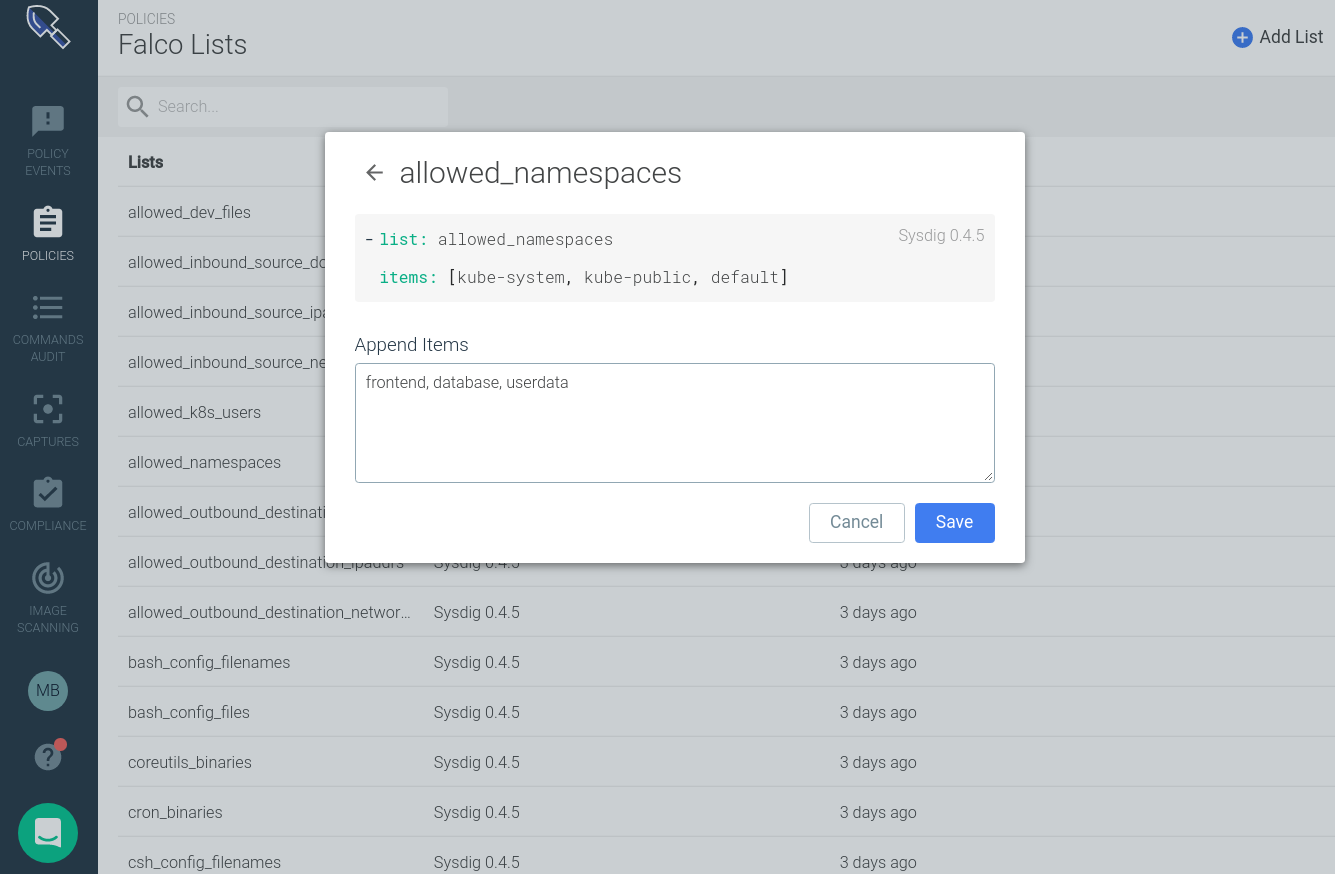
As we mentioned earlier, Falco rules usually reference macros and lists, to improve code reusability and readability. In the Falco rule above, you have the different macros that compose the condition (kevt, namespace, kcreate) and a list of allowed_namespaces.Updating the list of allowed / forbidden elements related with a security rule is an extremely common task (i.e. adding a new valid namespace).This new version of the interface also allows you to create and edit Falco Lists and Falco Macros, making these kind of iterative updates a breeze:
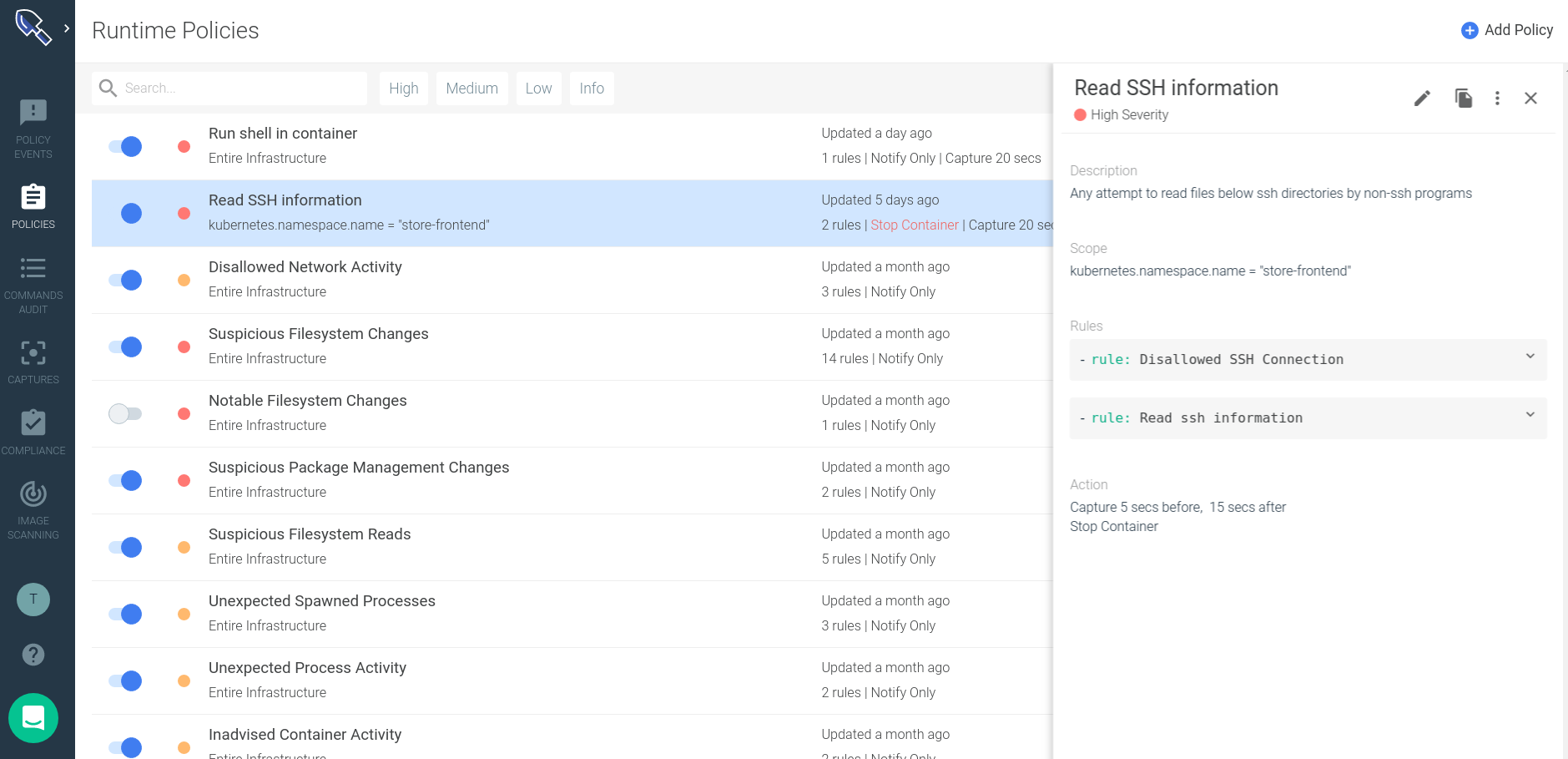
The new Sysdig Secure policy editor
Rules need to be included as part of a policy to become an actionable item. These policies can be listed, created or edited from the new Sysdig Secure policy interface:
Using the new Secure policy editor interface you can:
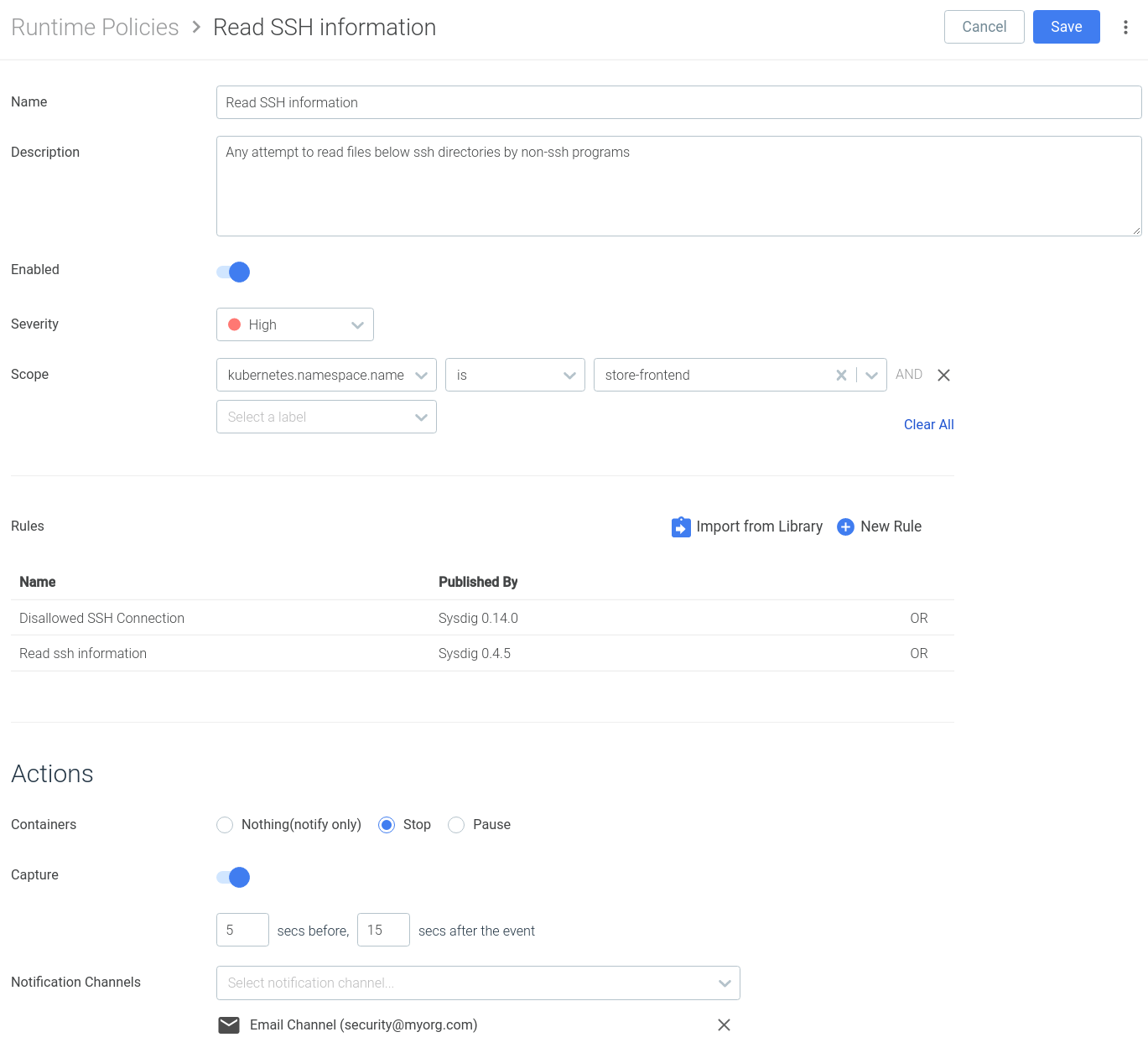
- Import one or several rules that will trigger this policy, directly from the Rules Library or creating new rules from this interface.
- **Scope the policy **using labels and tags. Enforcing this rule over a Kubernetes namespace or the hosts in a specific availability zone, to give you an example.
- Configure automated remediation actions: stop the container, create a capture to enable advanced container forensics or forward the event to a SIEM platform.
This new workflow allows you to create groups of runtime security rules that you can easily reuse for your different environments, applying the relevant modifications for each case.
Wrapping up
The policy editor overhaul released in Sysdig Secure 2.4 goes beyond the productivity and usability improvements, enabling a new set of features for you:
- Falco rules, macros and lists, tightly integrated with the interface.
- Out of the box runtime compliance standards, tagged using the different sections of the standard.
- Multiple runtime rules and image profiles per runtime policy.
If you don't want to miss the many other features being released for Sysdig Secure version 2.4, you can read the full story here.

